Embed presentation
Downloaded 48 times

















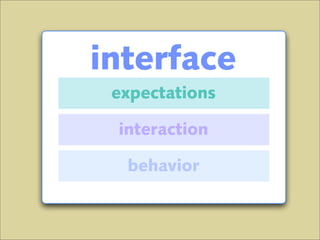
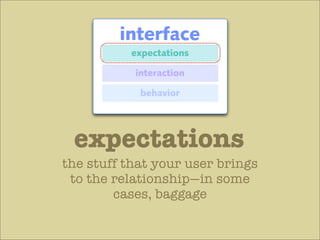
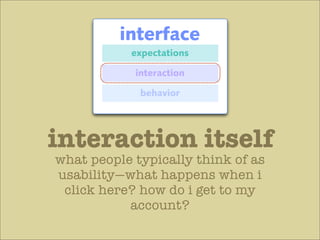
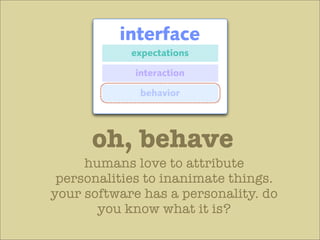


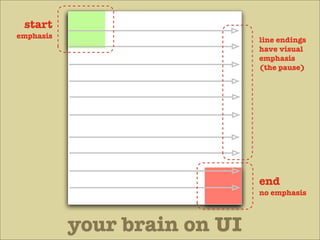

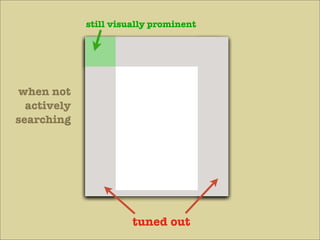


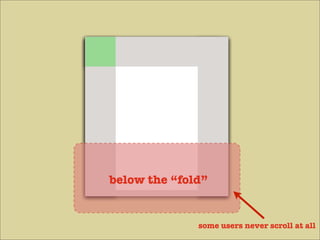
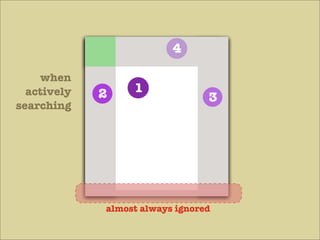





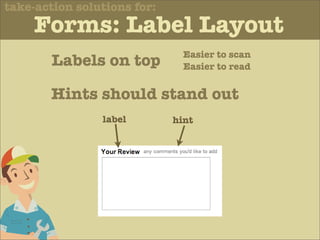

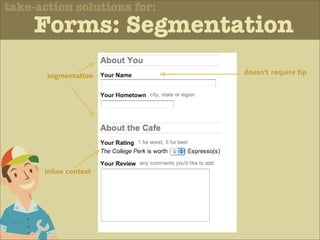
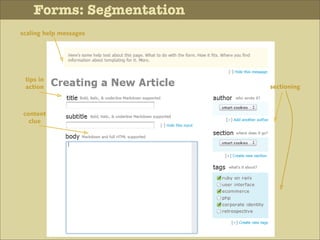

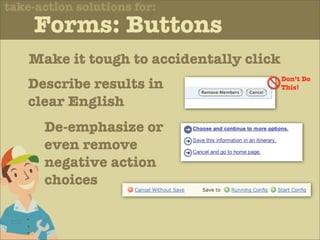
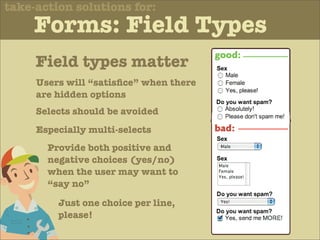
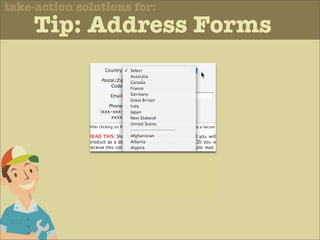
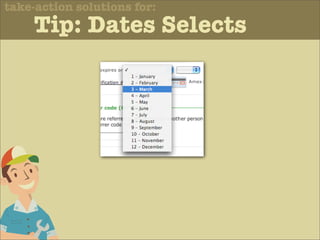
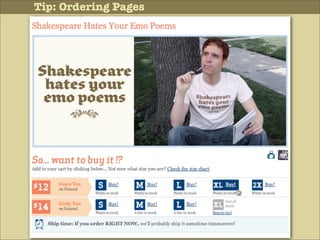





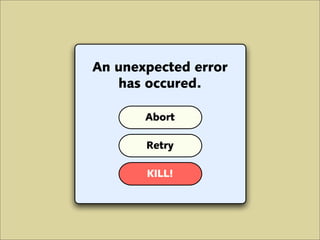
The document discusses various principles of interface design that can improve usability and the user experience. It covers topics like literacy levels of users, how users scan pages and ignore certain elements, the importance of clear labels, segmentation, and field types. The document provides specific solutions like keeping text simple, using headings and lists, putting labels above fields with hints, breaking up forms into logical sections, and ensuring buttons are clear in what they will do. The overall message is that interface design impacts users and good design can improve effectiveness and revenue.





















































