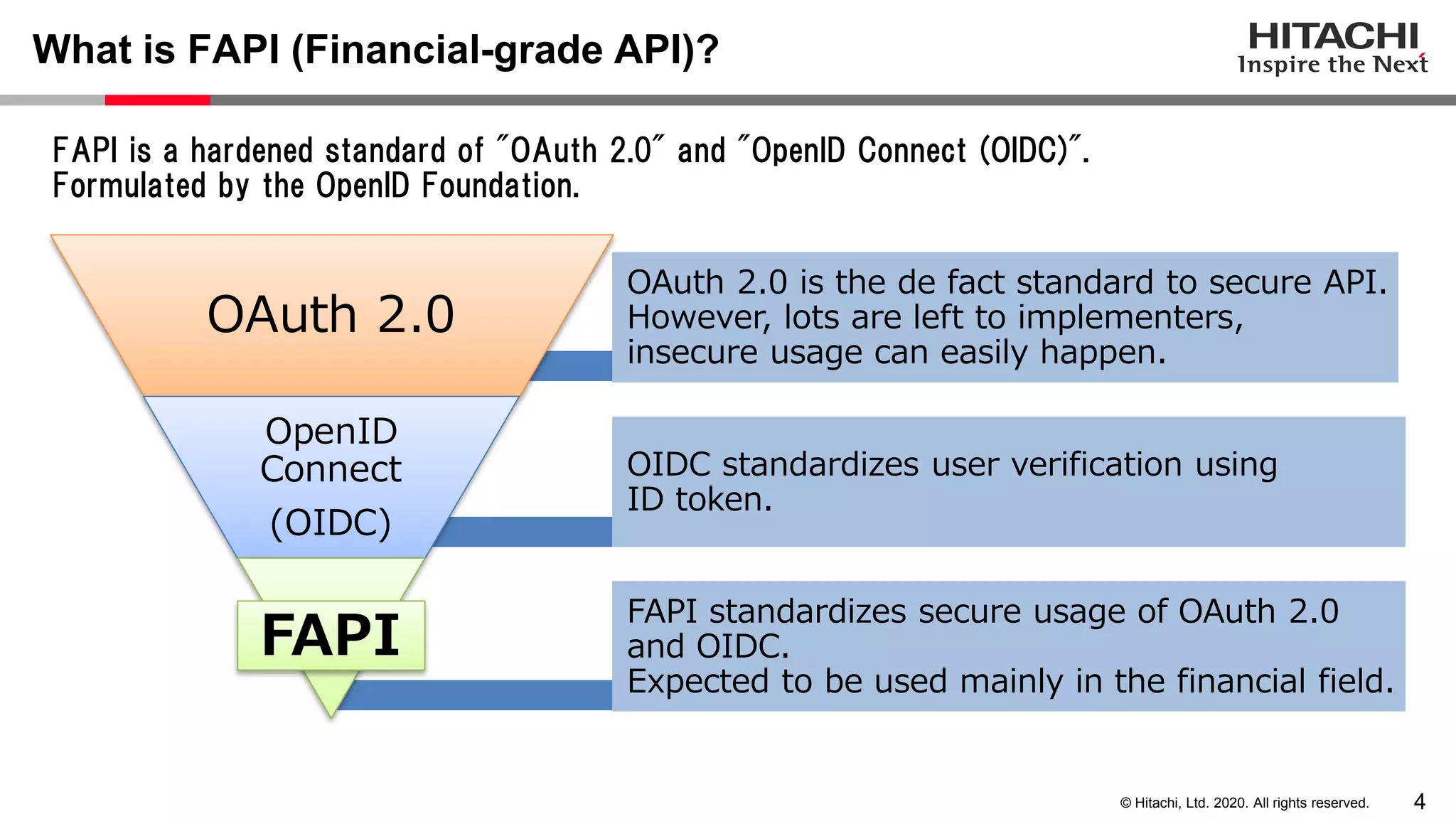
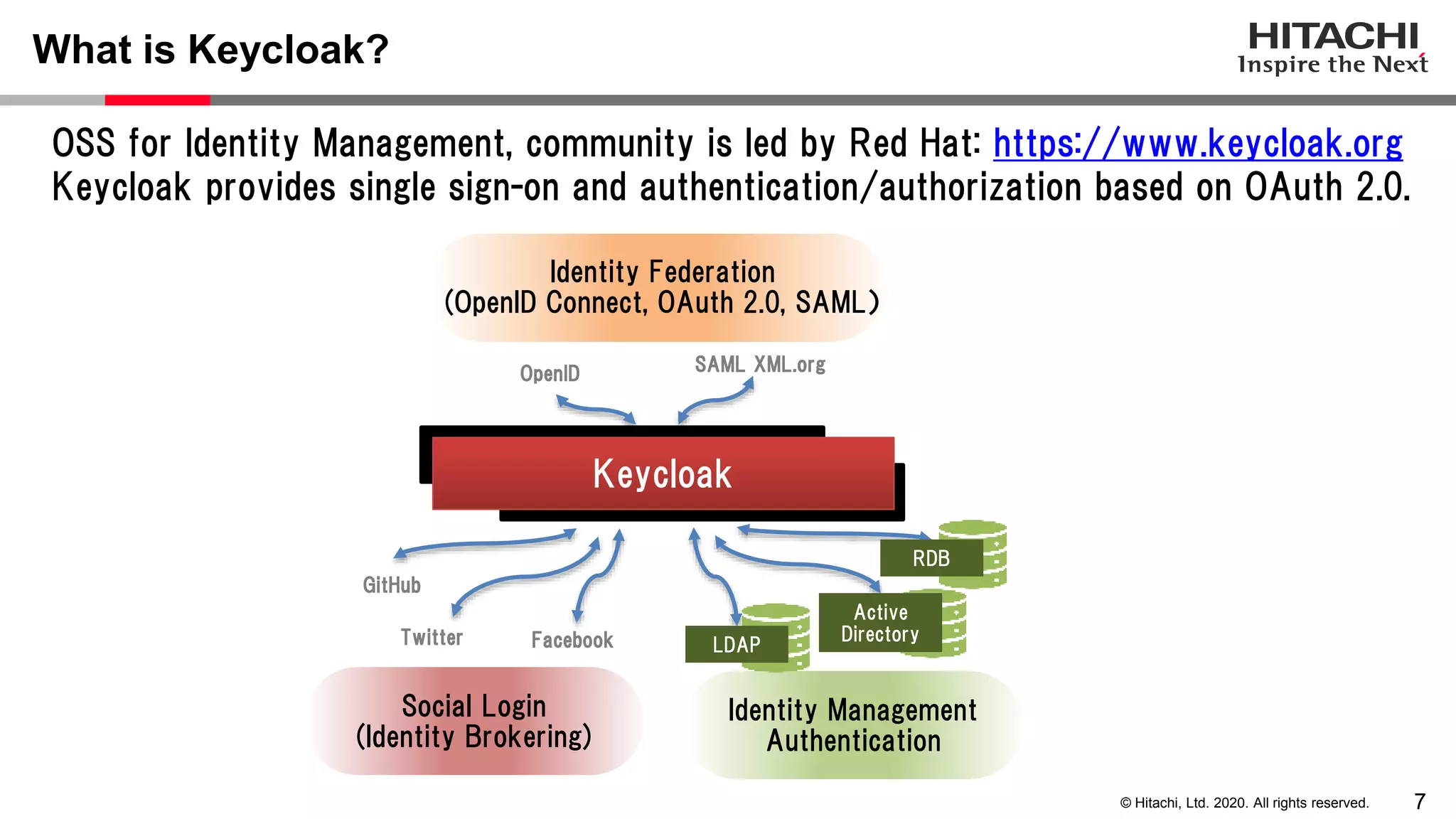
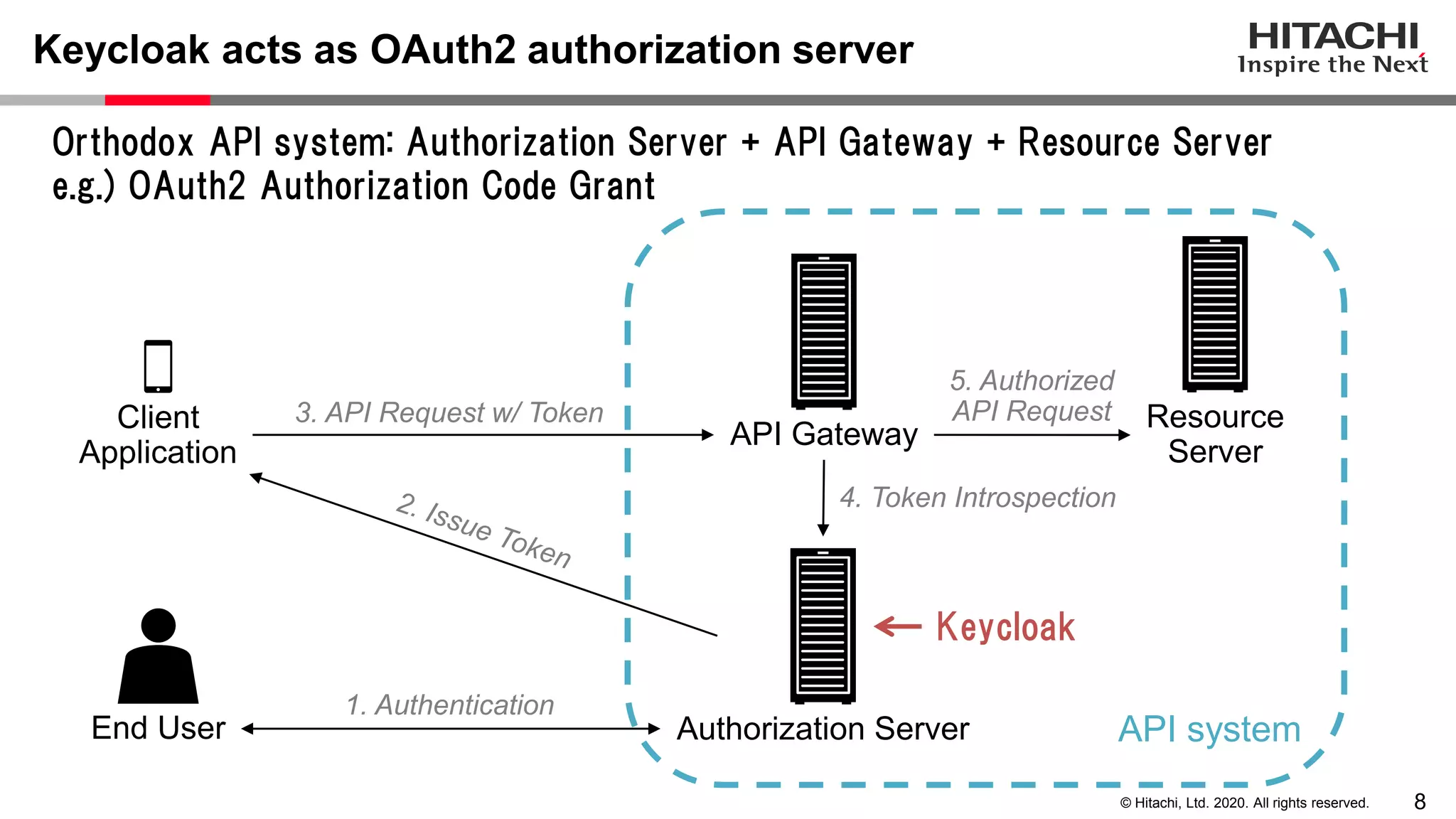
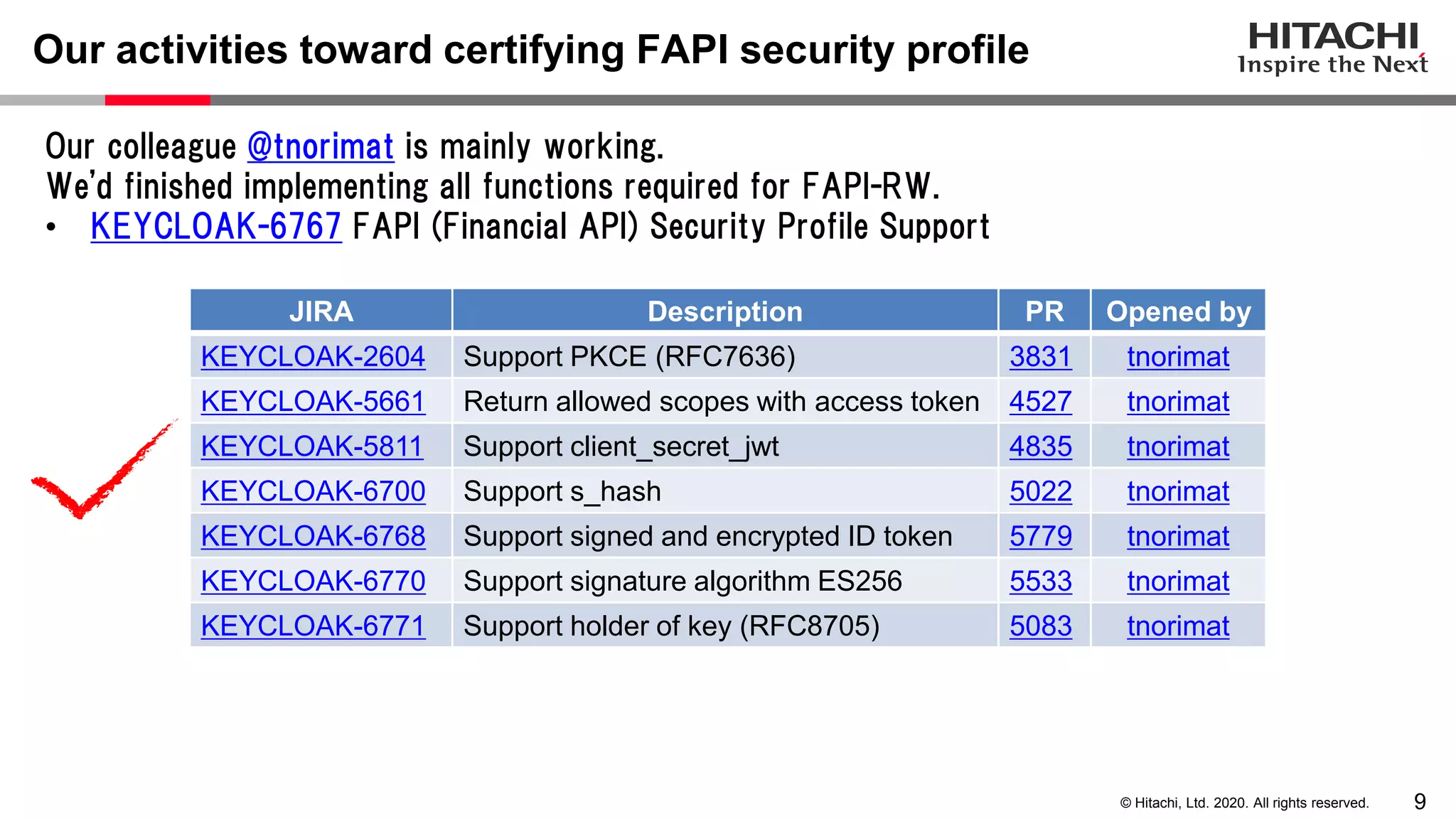
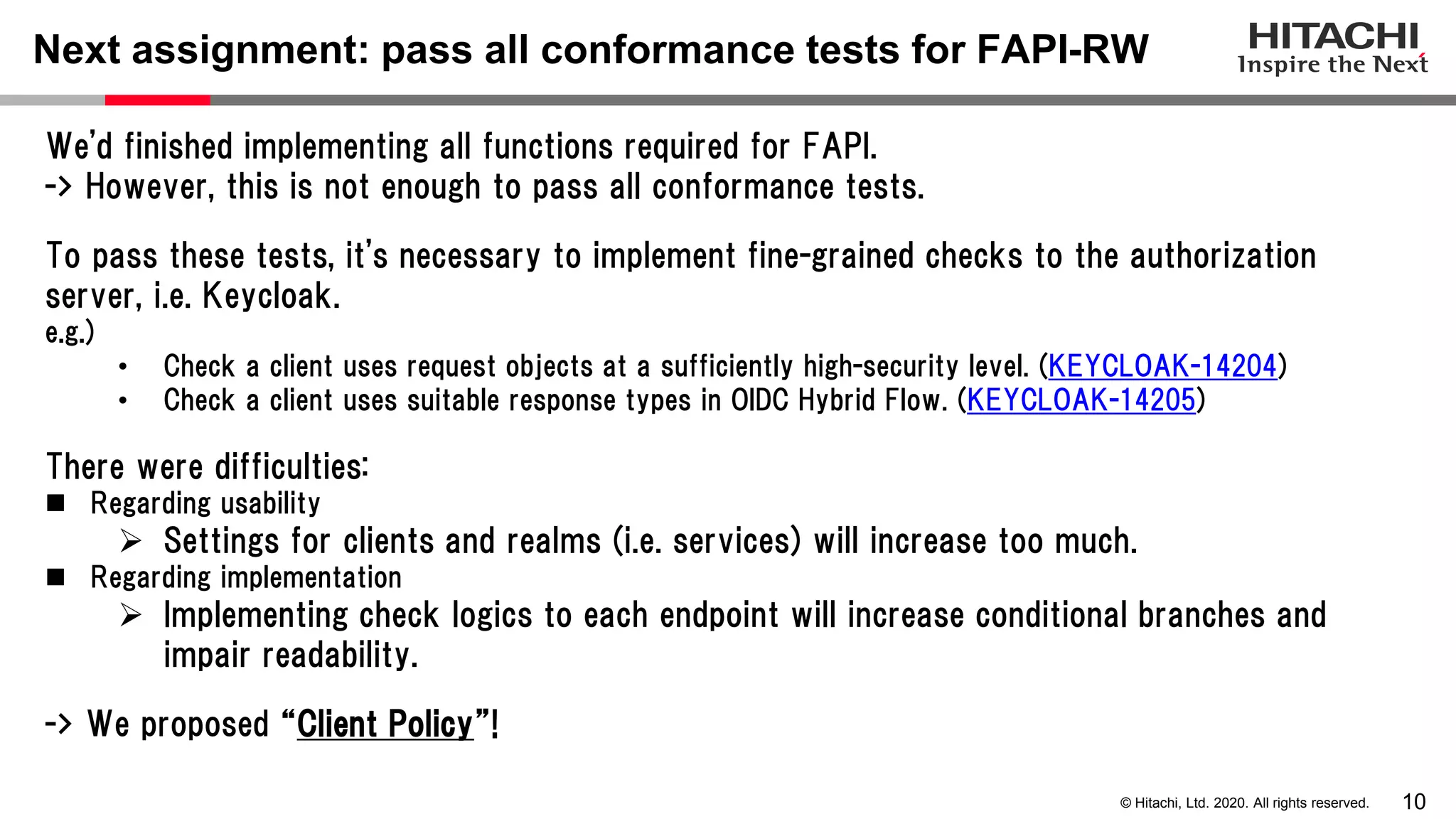
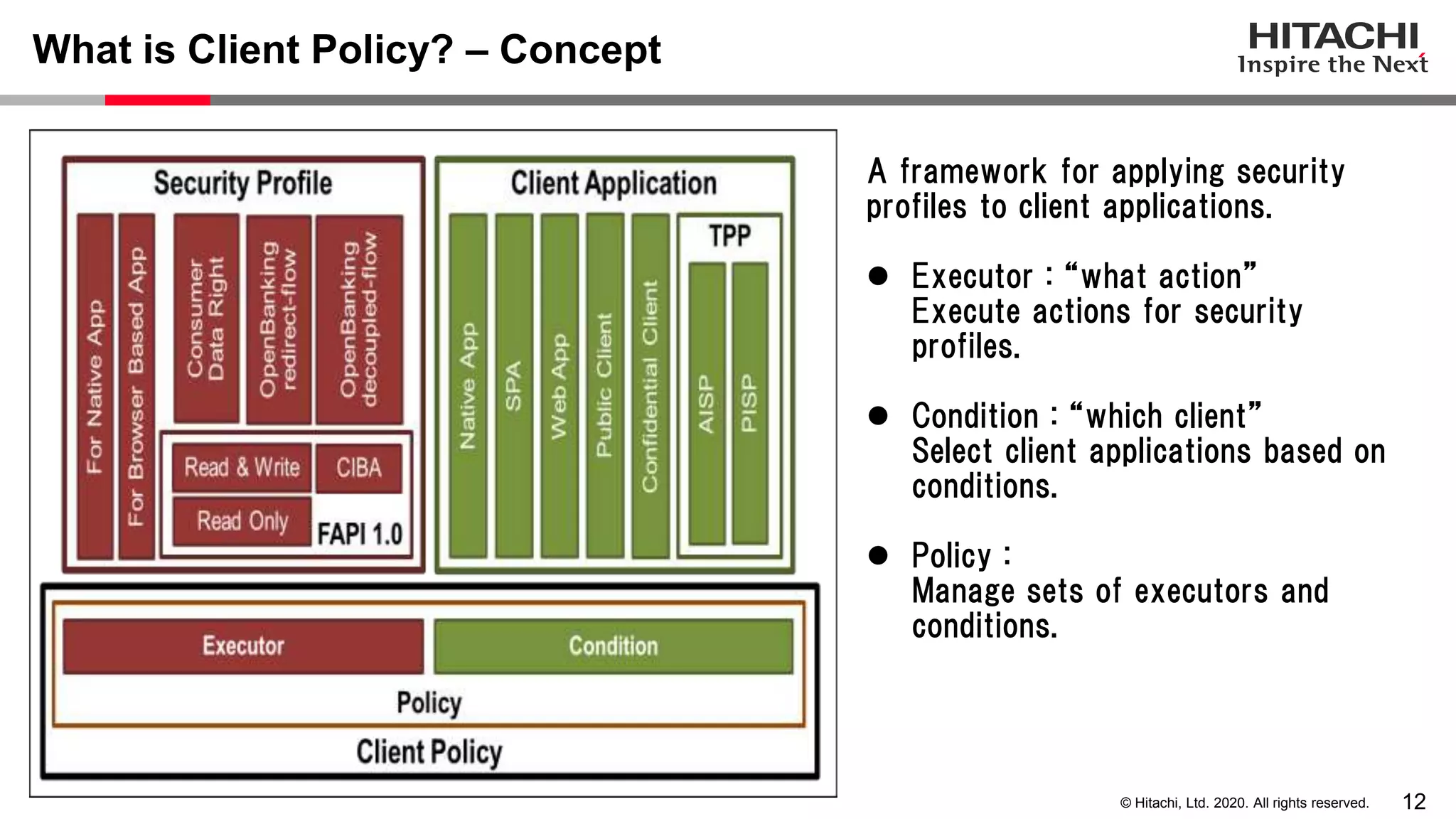
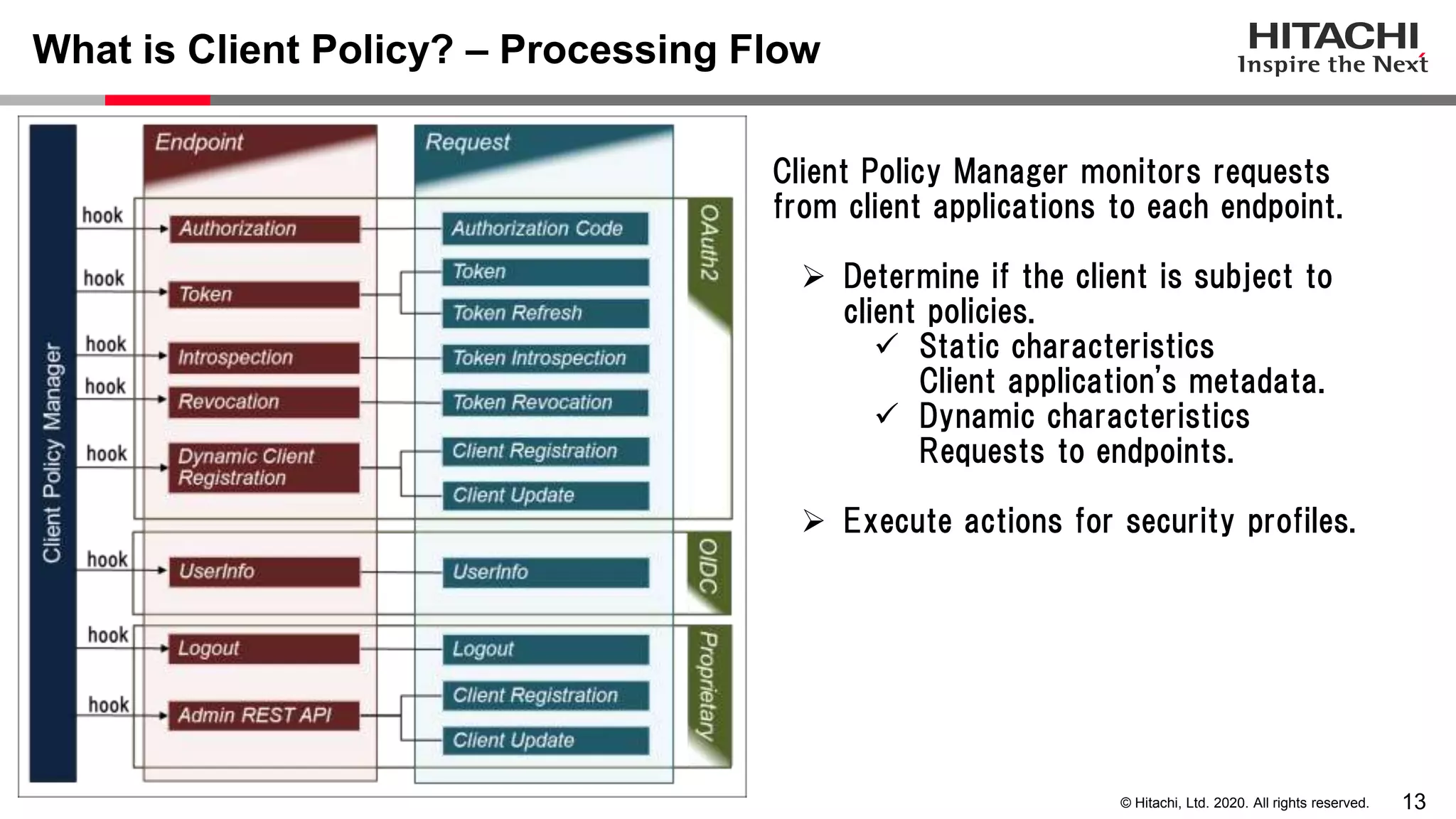
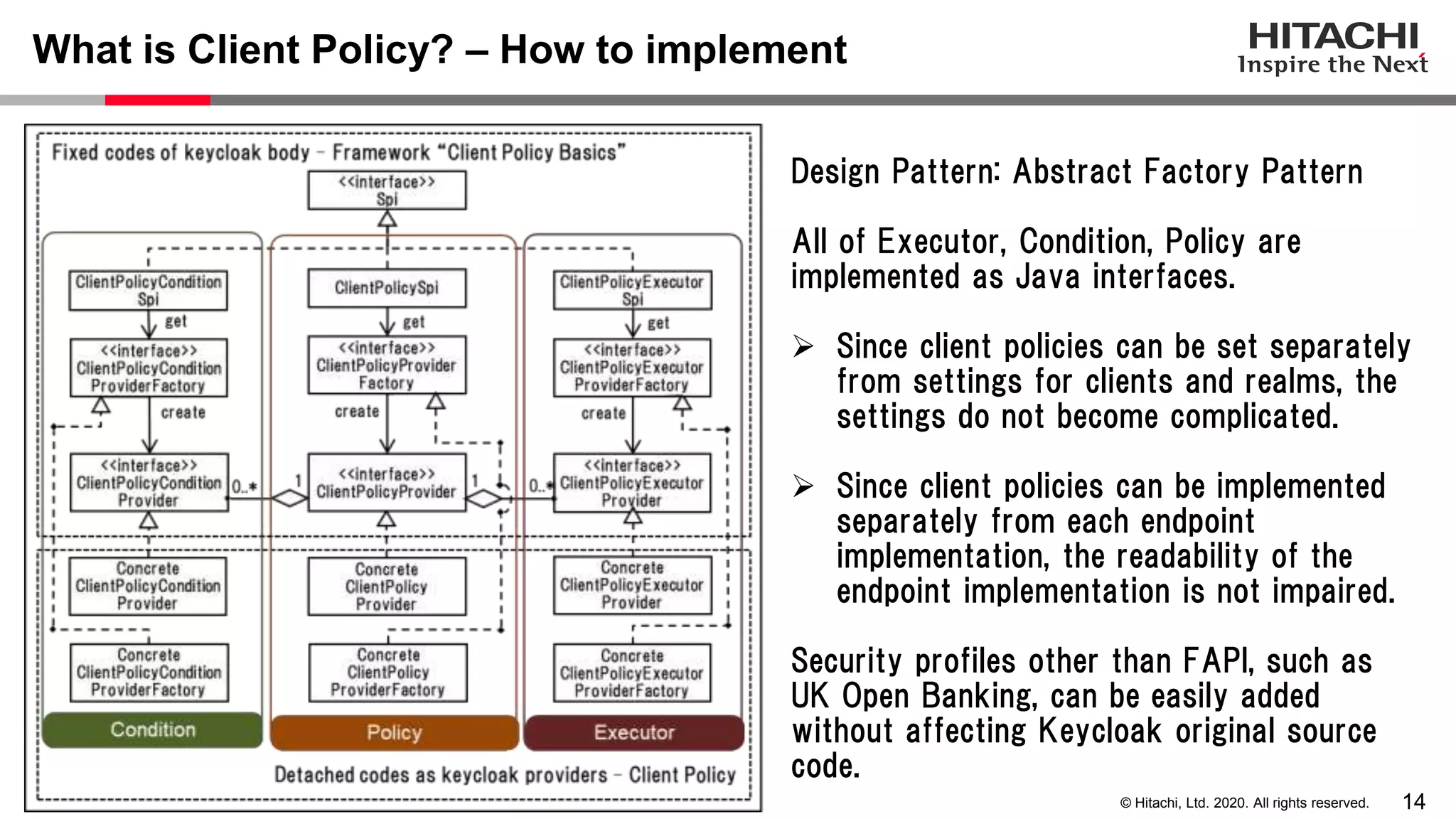
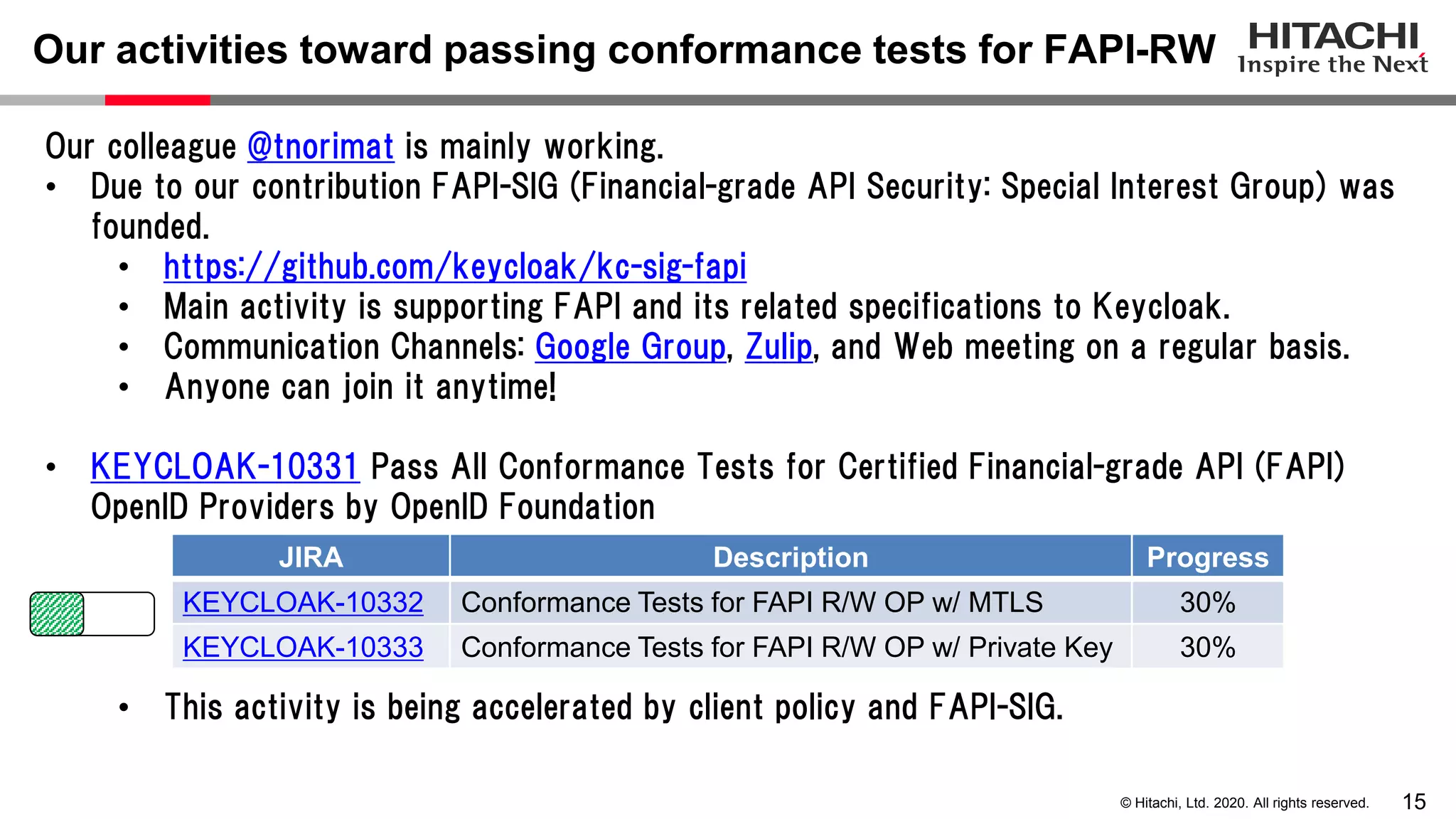
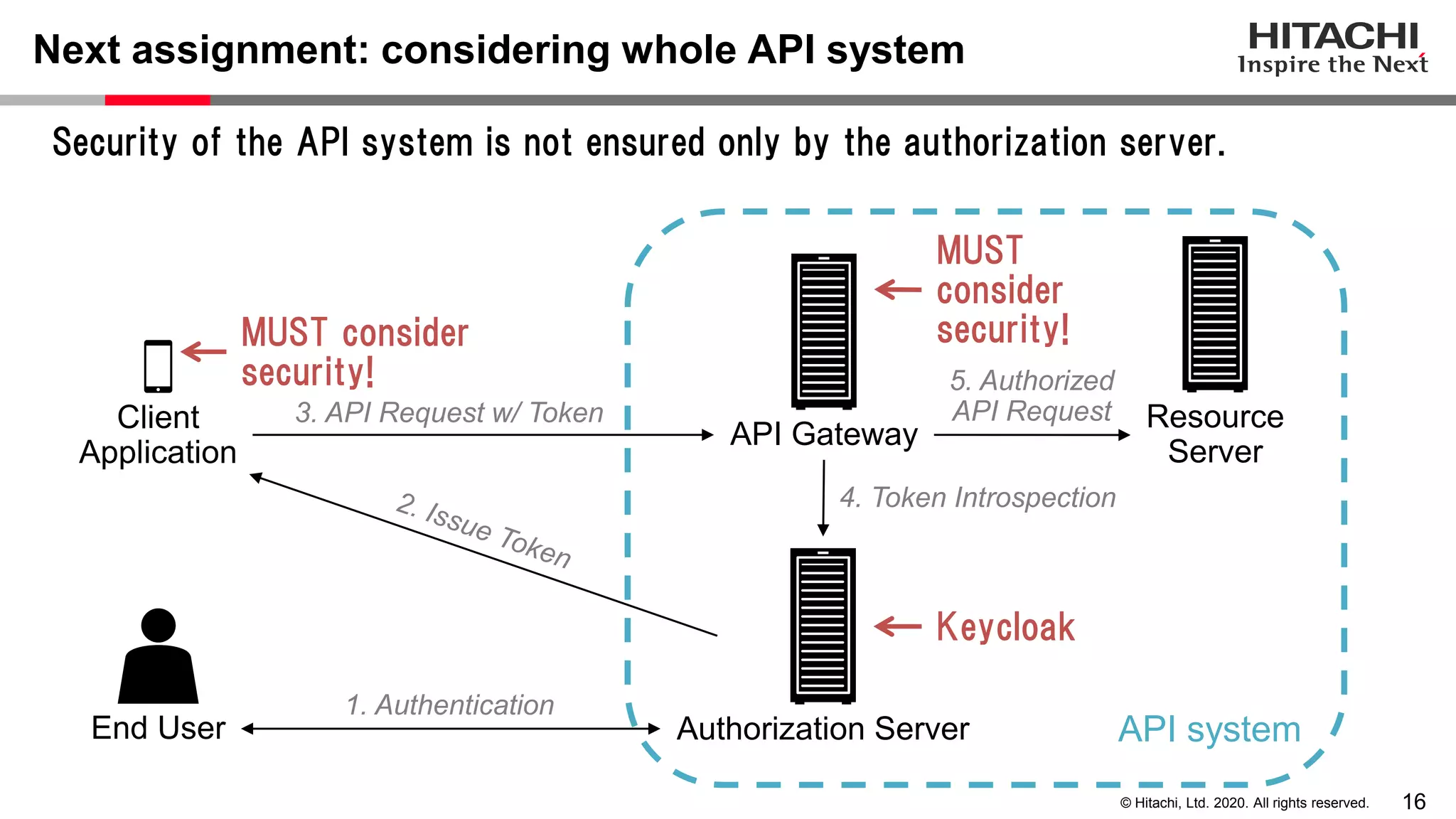
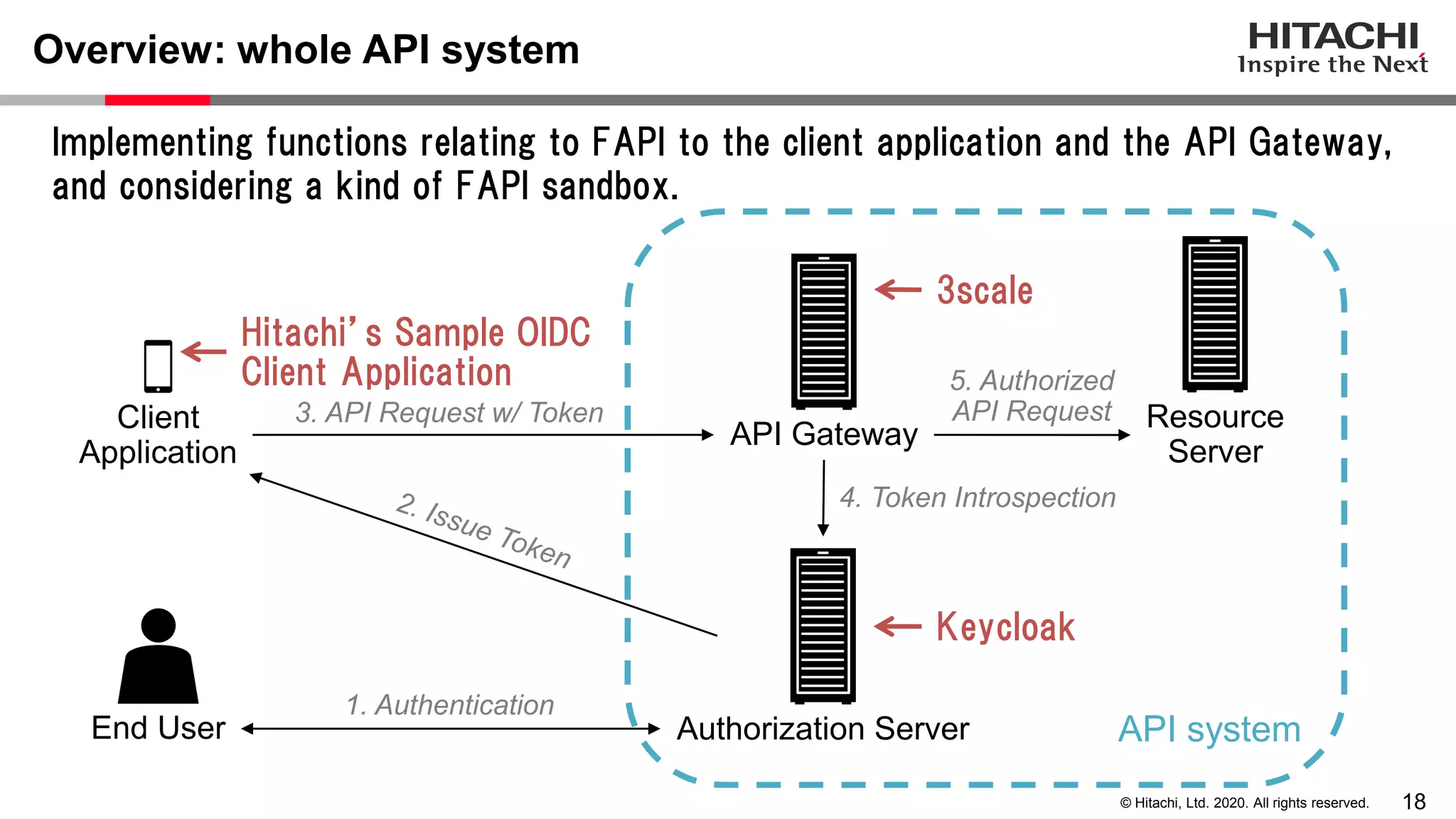
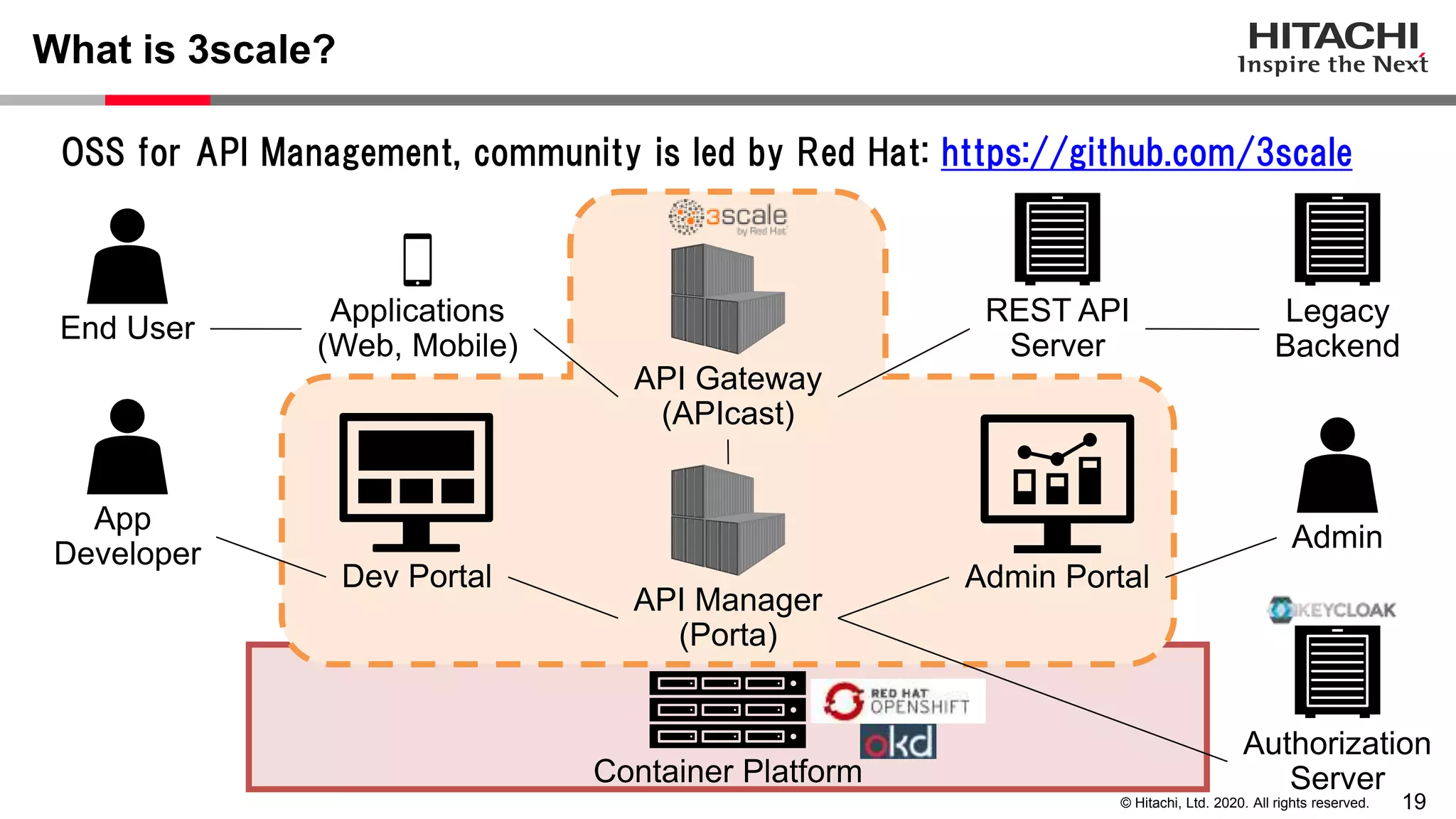
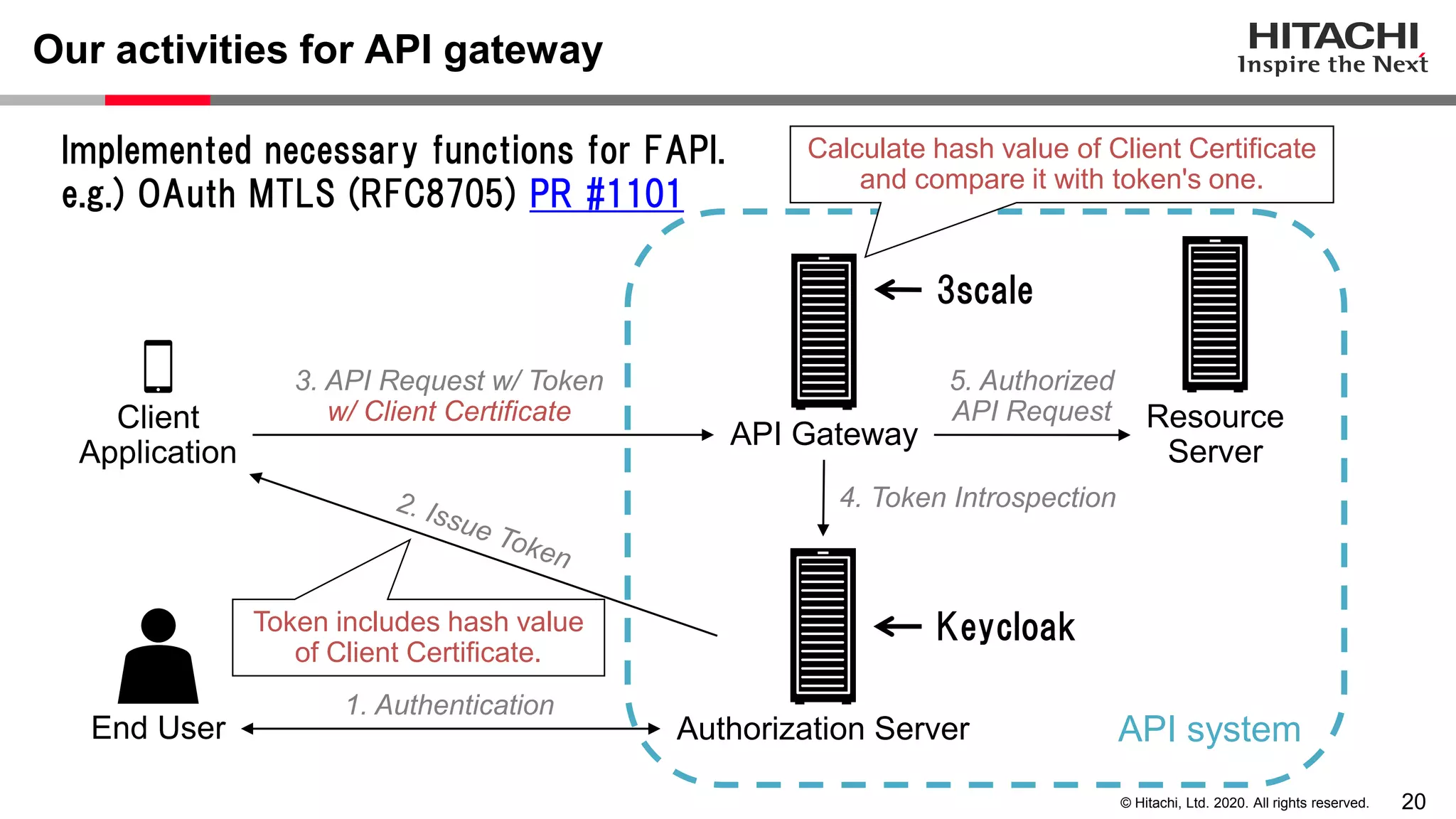
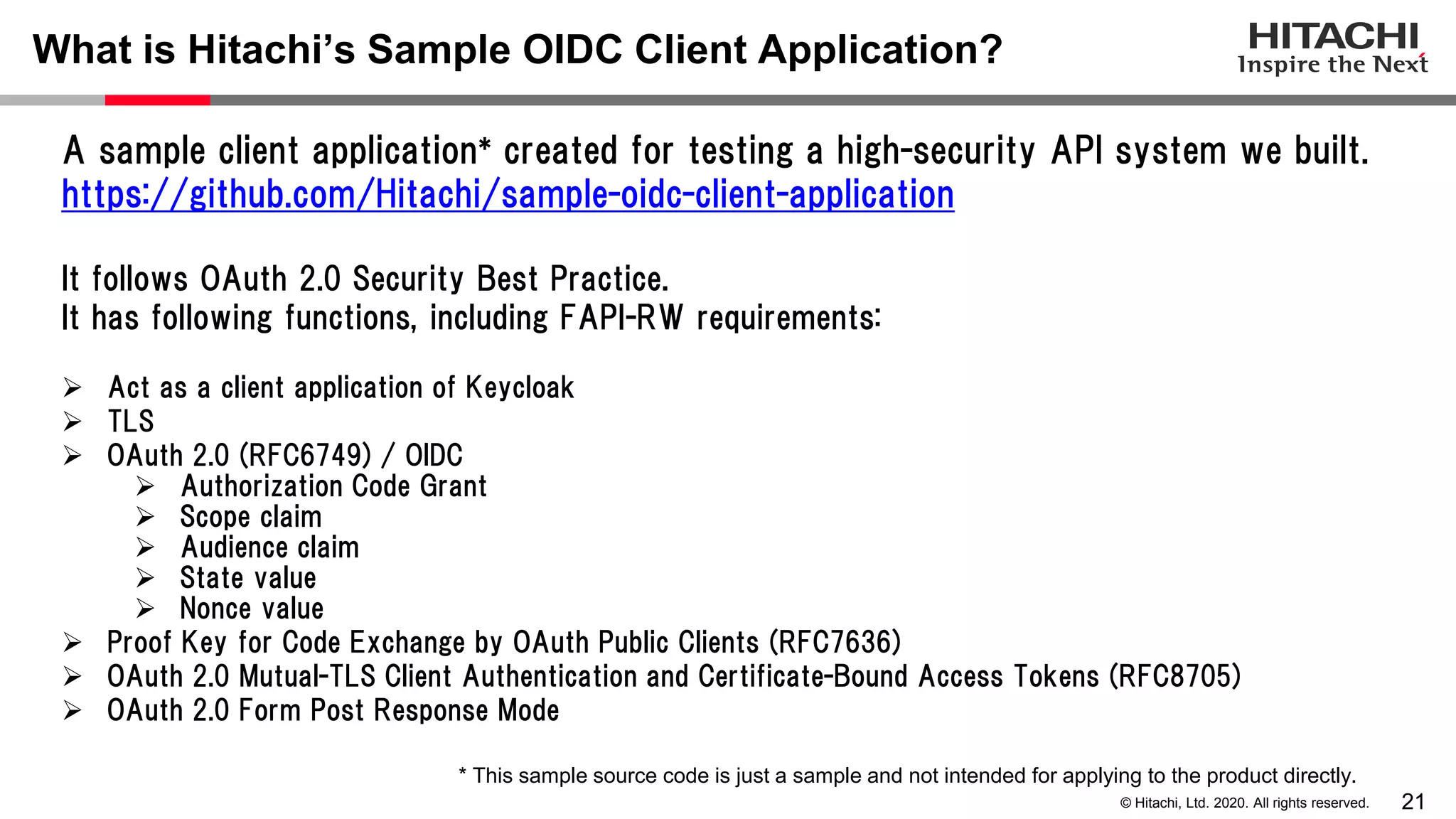
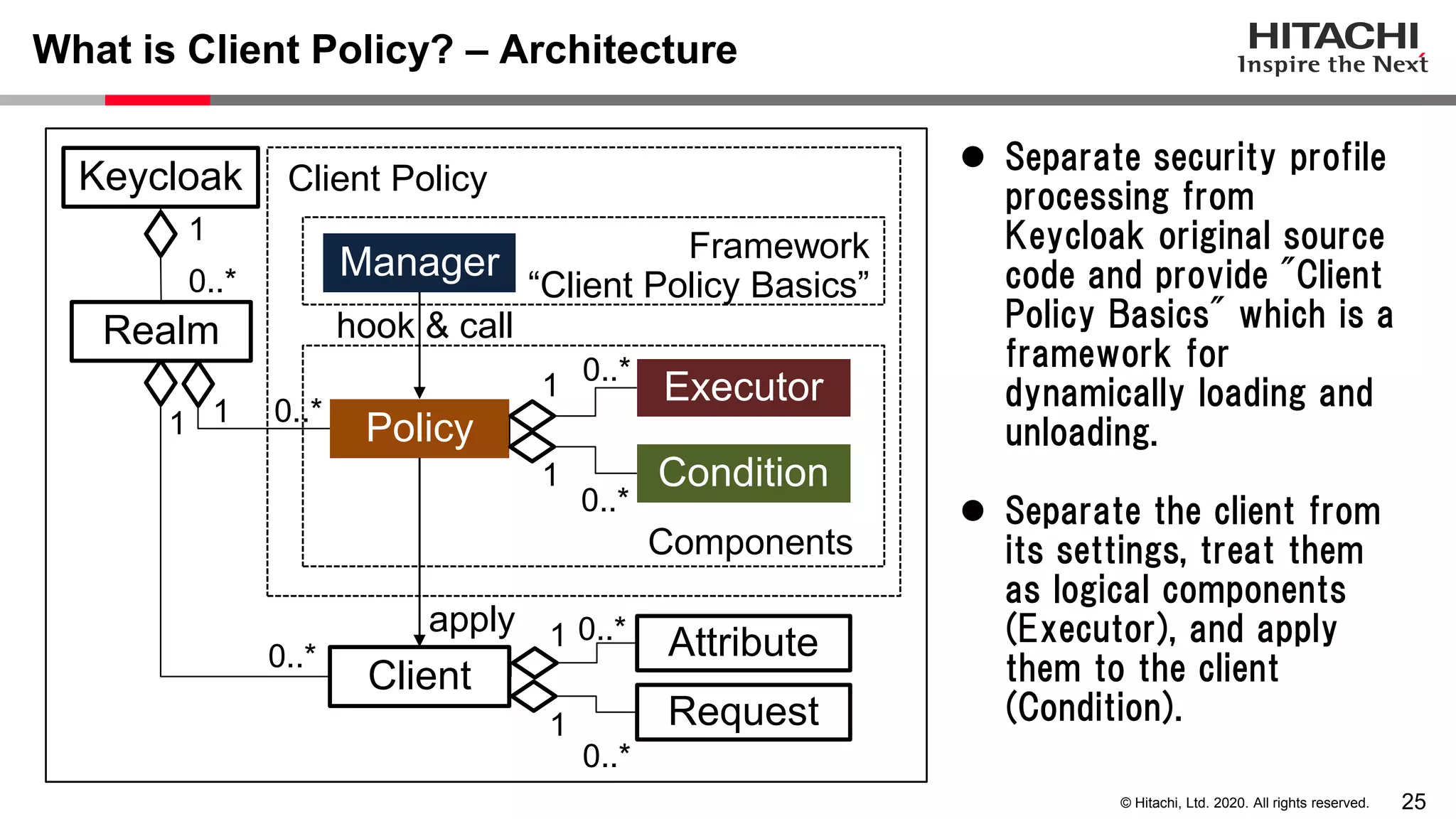
The document discusses Keycloak and its capabilities for satisfying the Financial-grade API (FAPI) security profile. It introduces Keycloak and describes how the proposed "Client Policy" feature allows Keycloak to easily meet the FAPI requirements by applying security profiles to client applications based on configurable conditions and executors. It also outlines other efforts like the FAPI-SIG group and implementation of FAPI requirements in the 3scale API gateway to help build fully FAPI-compliant systems.