Embed presentation
Download to read offline


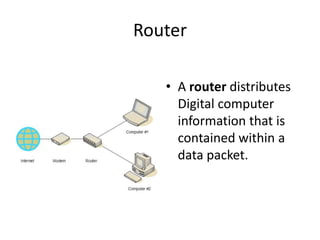



Encryption provides security across central servers, routers, firewalls, and VPNs. Central servers encrypt files to protect them from being read or changed. Routers distribute encrypted data packets. Firewalls are certified to slow the spread of fire and contain information. VPNs encrypt links, often across private networks and the Internet.





