The document discusses the necessity and methodology of web mining, which involves the discovery and analysis of useful information from the World Wide Web. It outlines various aspects such as web content mining, web structure mining, and web usage mining, while also addressing the challenges posed by the diverse and dynamic nature of web data. Additionally, it proposes an integrated system to enhance web usability analysis through automated tools and techniques from various disciplines.



![Page 4
systems and the languages for the exchange of
information rather than data. Many challenges are
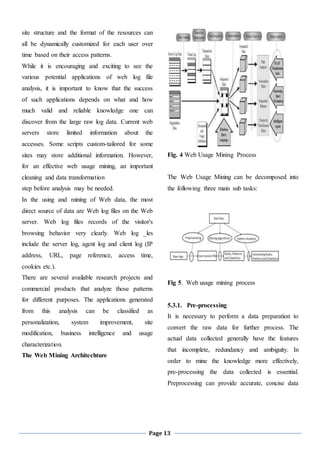
in the area of knowledge representation, discovery
and engineering. They include the extraction of
knowledge from data and its representation in a
form understandable by arbitrary parties, the
intelligent questioning and the delivery of answers
to problems as opposed to conventional queries
and the exploitation of formerly extracted
knowledge in this process.
2. WEB MINING
Web mining is the integration of information
gathered by traditional data mining methodologies
and techniques with information gathered over the
World Wide Web.
Data mining is also called knowledge discovery
and data mining (KDD). It is the extraction of
useful patterns from data sources, e.g.databases,
texts, web, images, etc. Patterns must be valid,
novel, potentially useful, understandable.Classic
data mining tasks
Classification: mining patterns that can
classify future (new) data into known
classes.
Association rule mining: mining any rule
of the form X ® Y, where X and Y are sets
of data items. E.g.,Cheese, Milk® Bread
[sup =5%, confid=80%]
Clustering: identifying a set of similarity
groups in the data
Sequential pattern mining: A sequential
rule: A® B, says that event A will be
immediately followed by event B with a
certain confidence
Fig .1 The Data Mining (KDD) Process
Just as data mining aims at discovering valuable
information that is hidden in conventional
databases, the emerging field of web mining aims
at finding and extracting relevant information that
is hidden in Web-related data, in particular hyper-
text documents published on the Web. Web
Mining is the extraction of interesting and
potentially useful patterns and implicit
information from artifacts or activity related to the
World Wide Web. There are roughly three
knowledge discovery domains that pertain to web
mining: Web Content Mining, Web Structure
Mining, and Web Usage Mining. Web content
mining is the process of extracting knowledge
from the content of documents or their
descriptions. Web document text mining, resource
discovery based on concepts indexing or agent
based technology may also fall in this category.](https://image.slidesharecdn.com/webddoc1-200709133442/85/Web-Mining-4-320.jpg)
![Page 5
Web structure mining is the process of inferring
knowledge from the World Wide Web
organization and links between references and
referents in the Web. Finally, web usage mining,
also known as Web Log Mining, is the process of
extracting interesting patterns in web access logs.
Web is a collection of inter-related files on one or
more Web servers. Web mining is a multi-
disciplinary effort that draws techniques from
fields like information retrieval, statistics,
machine learning, natural language processing,
and others. Web mining has new character
compared with the traditional data mining. First,
the objects of Web mining are a large number of
Web documents which are heterogeneously
distributed and each data source are
heterogeneous; second, the Web document itself is
semi-structured or unstructured and lack the
semantics the machine can understand.
3. HISTORY
The term “Web Mining” first used in [E1996],
defined in a ‘task oriented’ manner. Alternate
‘data oriented’ definition given in [CMS1997]. Its
First panel discussion at ICTAI 1997 [SM1997]. It
is a continuing forum.
WebKDD workshops with ACM
SIGKDD, 1999, 2000, 2001, 2002, … ; 60
–90 attendees
SIAM Web analytics workshop 2001,
2002, …
Special issues of DMKD journal,
SIGKDD Explorations
Papers in various data mining conferences
& journals
Surveys [MBNL 1999, BL 1999,
KB2000]
This area of research is so huge today due to the
tremendous growth of information sources
available on the Web and the recent interest in e-
commerce. Web mining is used to understand
customer behavior, evaluate the effectiveness of a
particular Web site, and help quantify the success
of a marketing campaign.
3.1.web mining subtasks
Web mining can be decomposed into the subtasks,
namely:
1. Resource finding: the task of retrieving
intended Web documents. By resource
finding we mean the process of retrieving
the data that is either online or offline from
the text sources available on the web such
as electronic newsletters, electronic
newswire, the text contents of HTML
documents obtained by removing HTML
tags, and also the manual selection of Web
resources.
2. Information selection and pre-
processing: automatically selecting and
pre-processing specific information from
retrieved Web resources. It is a kind of
transformation processes of the original
data retrieved in the IR process. These
transformations could be either a kind of
pre-processing that are mentioned above](https://image.slidesharecdn.com/webddoc1-200709133442/85/Web-Mining-5-320.jpg)

![Page 7
When attempting to detect web robots from a
stream it is desirable to monitor both the Web
server log and activity on the client-side. What we
are looking for is to distinguish single Web
sessions from each other. A Web session is a
series of requests to web pages, i.e. visits to web
pages. Since the navigation patterns of web robots
differs from the navigation patterns of human
users the contribution from web robots has to be
eliminated before proceeding with any further data
mining, i.e. when we are looking into web usage
behaviour of real users.
One problem with identifying web robots is
that they might hide their identity behind a facade
looking a lot like conventional web browsers.
Standard approaches to robot detection will fail to
detect camouflaged web robots. As web robots are
used for tasks like website indexing, e.g. by
Google, or detection of broken links they have to
exist. There is a special file on every domain
called “robot.txt” which, according to the Robot
Exclusion Standard [M. Koster, 1994], will be
examined by the robot in order to prevent the
robot from visiting certain pages of no interest.
Evil web robots however aren’t guaranteed to
follow the advice from robot.txt.
The classes chosen for evaluation are Temporal
Features, Page Features, Communication Features
and Path Features. It is desirable to be able to
detect the presence of a web robot after as few
requests as possible, this is ofcourse a tradeoff
between computational effort and result accuracy.
A simple decision model for determining the class
of a visitor is to first check if the visitor requested
robots.txt, then it will be labeled as robot, second
the visitor will be matched against a list of former
known robots. Third the referer “-” is searched
for, since robots seldom assign any value to the
referer fields this is a rewarding place to look. If a
robot is found, the list of known robots is updated
with the new one.
3.1.2 Avoiding Mislabeled Sessions To avoid
mislabeling of sessions an ensemble filtering
approach [C. Brodley et al., 1999] is used, where
the idea is to instead of just one model for
classification, build several models which are used
to find classification errors via finding single
mislabeled sessions.
The set of models acquired are used to classify all
sessions respectively. For each session, the
amount of false negative and false positive
classifications are counted. A large value of false
positive classifications imply that the session is
currently assigned to be a non-robot despite being
predicted to be a robot in most of the models. A
large value of false negative classifications imply
that the session might be a non-robot but has the
robot classifier.
4.2 Mining Issue](https://image.slidesharecdn.com/webddoc1-200709133442/85/Web-Mining-7-320.jpg)

![Page 9
Web Content Mining deals with discovering
useful information or knowledge from web page
contents. Web content mining analyzes the
content of Web resources. Content data is the
collection of facts that are contained in a web
page. It consists of unstructured data such as free
texts, images, audio, video, semi-structured data
such as HTML documents, and a more structured
data such as data in tables or database generated
HTML pages. The primary Web resources that are
mined in Web content mining are individual
pages. They can be used to group, categorize,
analyze, and retrieve documents. Web content
mining could be differentiated from two points of
view:
5.1.1. Agent-Based Approach
This approach aims to assist or to improve the
information finding and filtering the information
to the users. This could be placed into the
following three categories:
a. Intelligent Search Agents: These agents
search for relevant information using
domain characteristics and user profiles to
organize and interpret the discovered
information.
b. Information Filtering/ Categorization:
These agents use information retrieval
techniques and characteristics of open
hypertext Web documents to automatically
retrieve, filter, and categorize them.
c. Personalized Web Agents: These agents
learn user preferences and discover Web
information based on these preferences,
and preferences of other users with similar
interest.
1. Intelligent Search Agents:
Several intelligent Web agents have been
developed that search for relevant information
using domain characteristics and user profiles
to organize and interpret the discovered
information. Agents such as Harvest , FAQ
Finder , Information Manifold , OCCAM , and
ParaSite rely either on pre-specified domain
information about particular types of
documents, or on hard coded models of the
information sources to retrieve and interpret
documents. Agents such as ShopBot and ILA
(Internet Learning Agent) interact with and
learn the structure of unfamiliar information
sources. ShopBot retrieves product
information from a variety of vendor sites
using only general information about the
product domain. ILA learns models of various
information sources and translates these into
its own concept hierarchy.
2.InformationFialtering/Categorization:
A number of Web agents use various information
retrieval techniques and characteristics of open
hypertext Web documents to automatically
retrieve, alter, and categorize them, BO
(Bookmark Organizer) 34] combines hierarchical
clustering techniques and user interaction to](https://image.slidesharecdn.com/webddoc1-200709133442/85/Web-Mining-9-320.jpg)













![Page 24
and there is no strong rule against the usage of
such algorithms with such attributes. This process
could result in denial of service or a privilege to
an individual based on his race, religion or sexual
orientation, right now this situation can be avoided
by the high ethical standards maintained by the
data mining company. The collected data is being
made anonymous so that, the obtained data and
the obtained patterns cannot be traced back to an
individual. It might look as if this poses no threat
to one’s privacy, actually many extra information
can be inferred by the application by combining
two separate unscrupulous data from the user.
9. CONCLUSION
The term Web mining has been used to refer to
techniques that encompass a broad range of issues.
However, while meaningful and attractive, this
very broadness has caused Web mining to mean
different things to different people, and there is a
need to develop a common vocabulary. Towards
this goal we proposed a definition of Web mining,
and developed taxonomy of the various ongoing
efforts related to it. Next, presented a survey of
the research in this area and concentrated on Web
usage mining.The provided a detailed survey of
the e orts in this area, even though the survey is
short because of the area's newness. To provided a
general architecture of a system to do Web usage
mining, and identified the issues and problems in
this area that require further research and
development.
As the Web and its usage continue to grow, so
does the opportunity to analyze Web data and
extract all manner of useful knowledge from it.
The past few years have seen the emergence of
Web mining as a rapidly growing area, due to the
efforts of the research community as well as
various organizations that are practicing. The key
component of web mining is the mining process
itself. Here described the key computer science
contributions made in this field, including the
overview of web mining, taxonomy of web
mining, the prominent successful applications, and
outlined some promising areas of future research.
10.REFERENCE
[1] http://en.wikipedia.org/wiki/Web mining
[2] http://www.galeas.de/webimining.html
[3] Jaideep srivastava, Robert Cooley, Mukund
Deshpande, Pan-Ning Tan, Web Usage Mining:
Discovery and Applications of Usage Patterns
from Web Data, SIGKDD Explorations, ACM
SIGKDD,Jan 2000.
[4] Miguel Gomes da Costa Jnior,Zhiguo Gong,
Web Structure Mining: An Introduction,
Proceedings of the 2005 IEEE International
Conference on Information Acquisition
[5] R. Cooley, B. Mobasher, and J.
Srivastava,Web Mining: Information and Pattern
Discovery on the World Wide Web, ICTAI97
[6] Brijendra Singh, Hemant Kumar Singh, WEB
DATA MINING RE- SEARCH: A SURVEY,
2010 IEEE](https://image.slidesharecdn.com/webddoc1-200709133442/85/Web-Mining-24-320.jpg)
![Page 25
[7] Mining the Web: discovering knowledge from
hypertext data, Part 2 By Soumen Chakrabarti,
2003 edition
[8] Web mining: applications and techniques By
Anthony Scime
[9] . R. Agrawal and R. Srikant. Fast algorithms
for mining association rules.
[10] S. Agrawal, R. Agrawal, P.M. Deshpande, A.
Gupta, J. Naughton, R. Ramakrishna, and S.
Sarawagi. On the computation of
multidimensional aggregates.
[11] R. Armstrong, D. Freitag, T. Joachims, and
T. Mitchell. Webwatcher: A learning apprentice
for the world wide web.
[12] M. Balabanovic, Yoav Shoham, and Y. Yun.
An adaptive agent for automated web browsing.
Journal of Visual Communication and Image
Representation,
[13] A. Z. Broder, S. C. Glassman, M. S.
Manasse, and G Zweig. Syntactic clustering of the
web.](https://image.slidesharecdn.com/webddoc1-200709133442/85/Web-Mining-25-320.jpg)