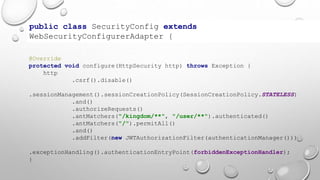
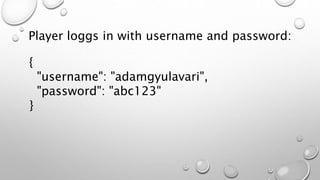
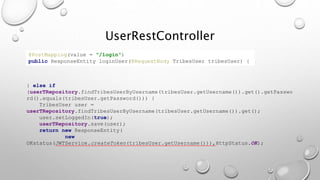
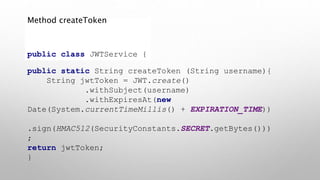
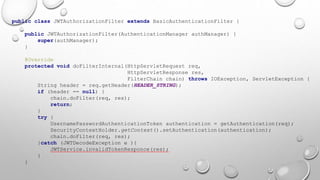
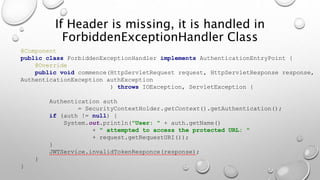
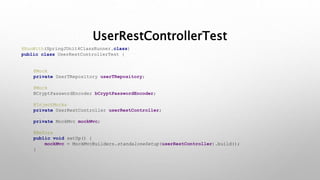
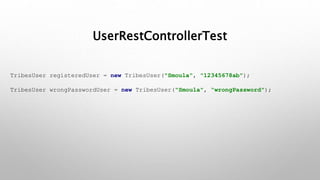
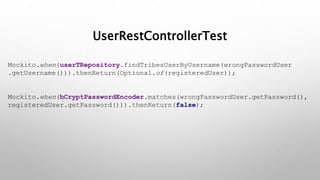
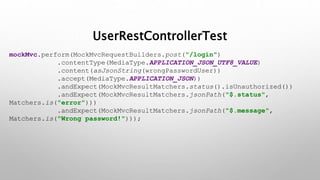
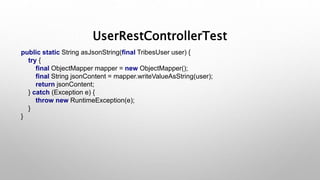
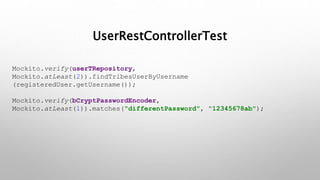
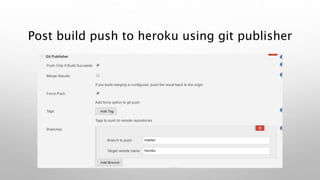
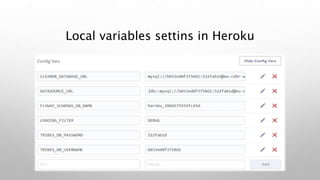
This document introduces the Vulpes Tribes backend team project at GFA/Húli. It introduces the four team members and their GitHub and LinkedIn profiles. It provides an overview of the Java Spring Boot RESTful web application being created, which simulates an MMO strategic game similar to Travian. It describes how the game works with kingdoms, buildings, armies. It lists the technologies used in the project like Spring Boot, Hibernate, MySQL, Flyway, JWT authentication. It provides the URL and GitHub repo for the app and outlines what each team member will present on in more detail - security with JWT tokens, testing with JUnit/Mockito, database migration with Flyway, and continuous integration with