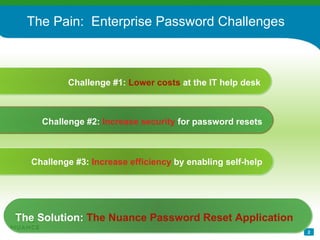
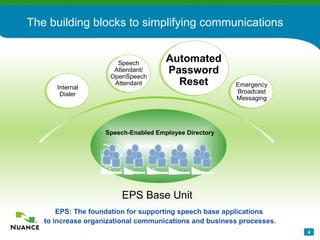
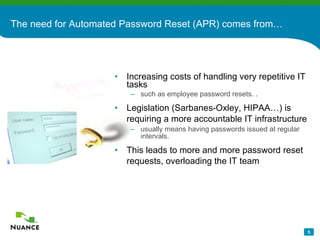
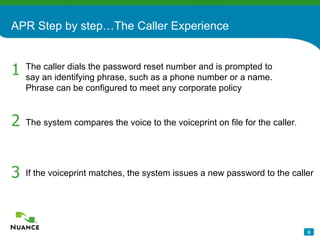
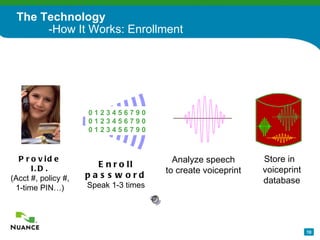
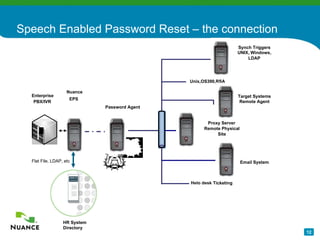
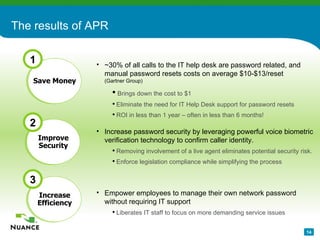
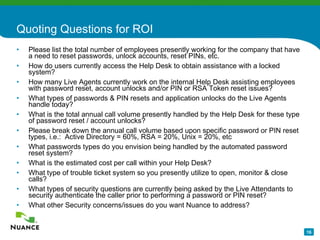
The document discusses an automatic password reset solution called Nuance Password Reset Application. It would help address challenges around reducing IT help desk costs, increasing security for password resets, and improving efficiency. The solution uses voice biometrics to securely authenticate users and allow them to reset their own passwords without involving IT support staff. This is estimated to save organizations over $10 per password reset on average by automating the process.