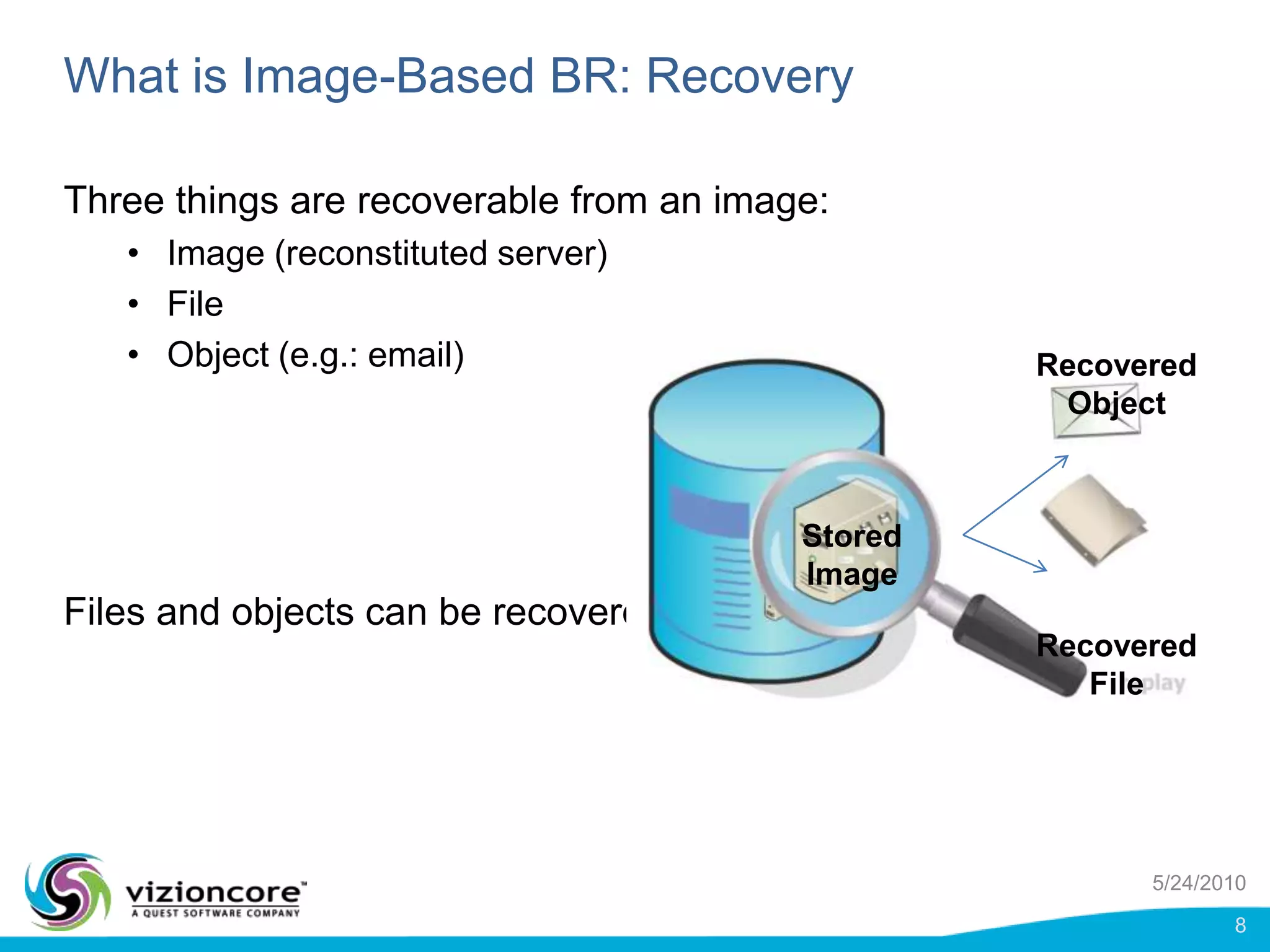
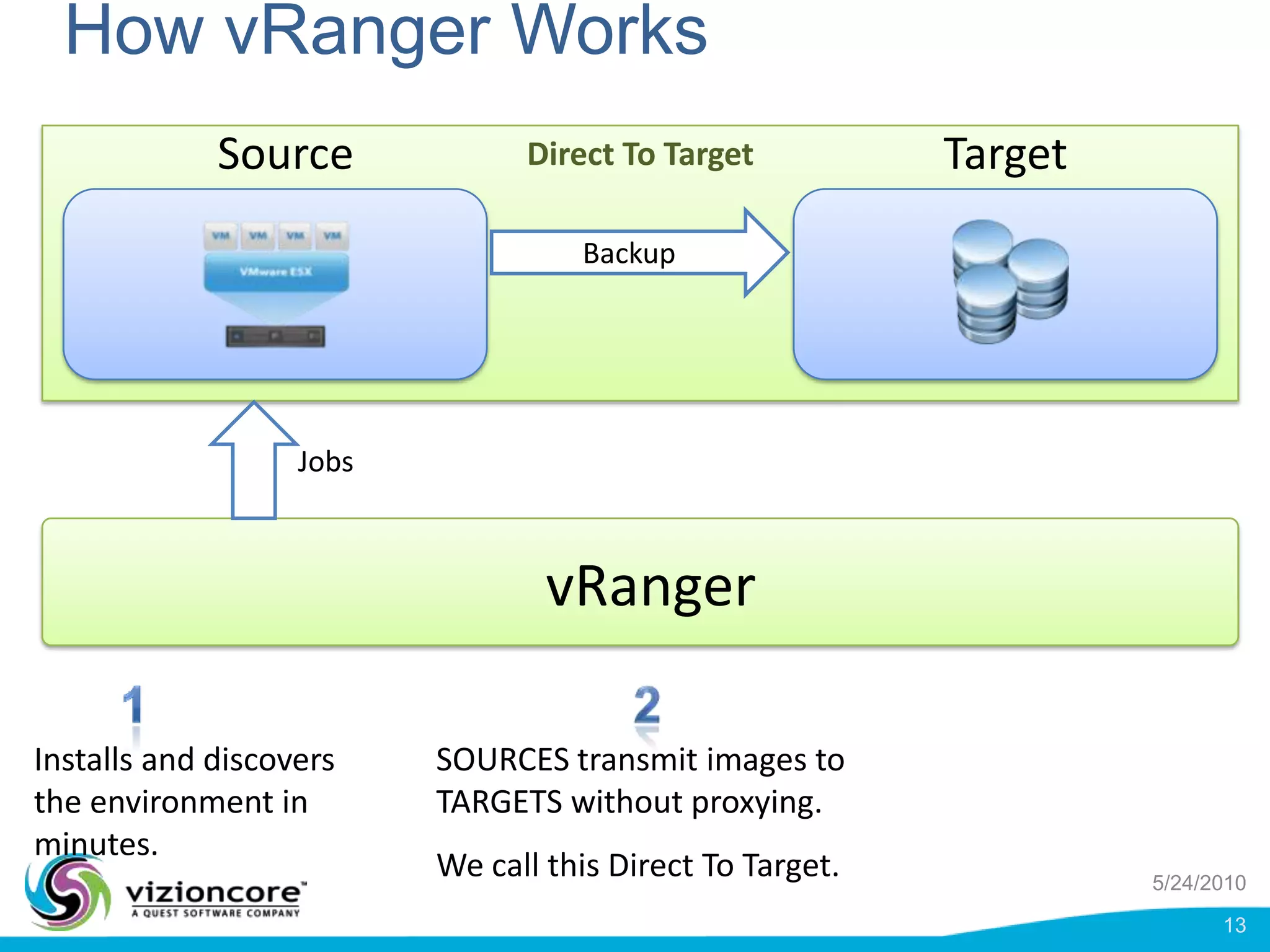
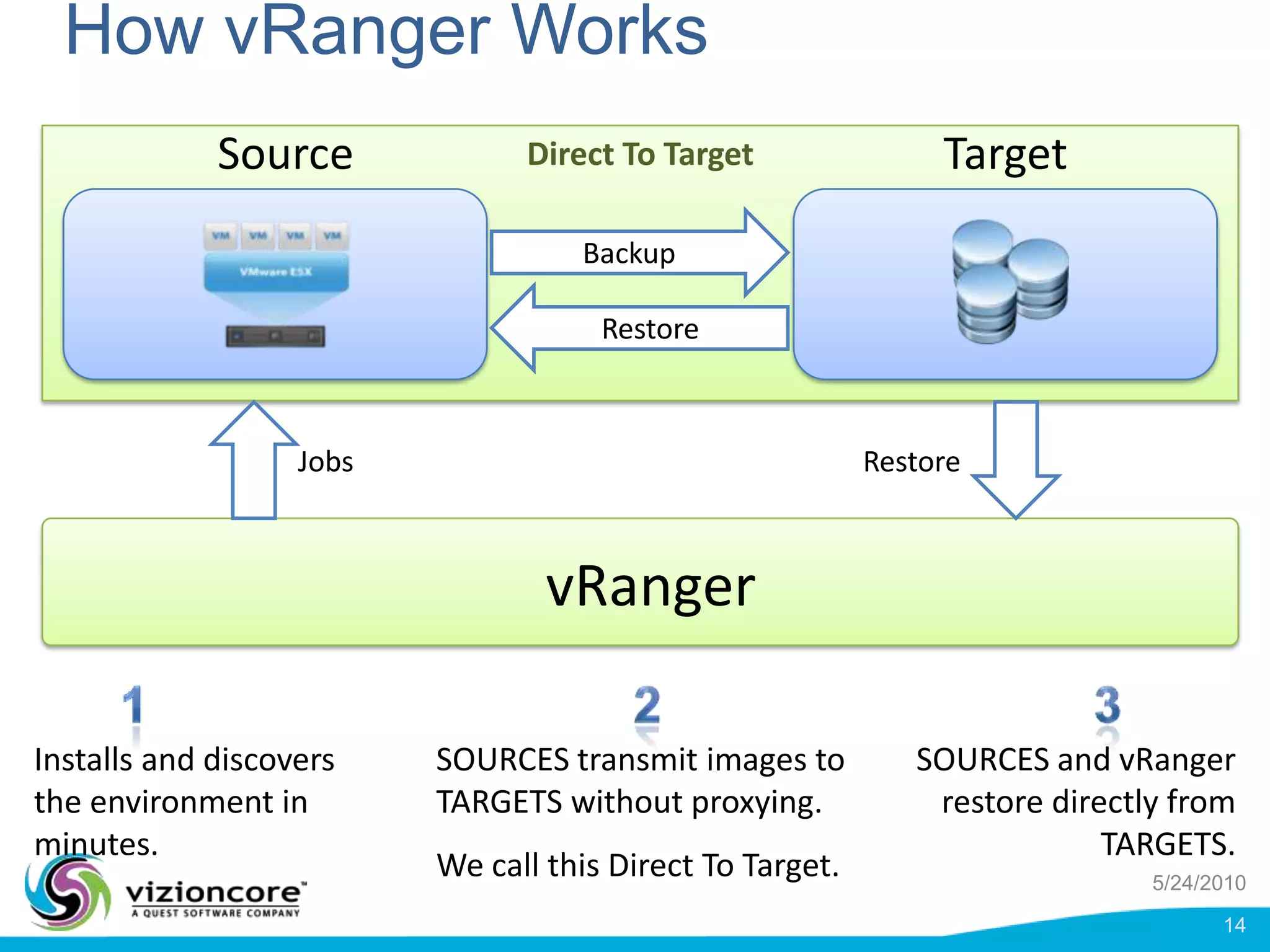
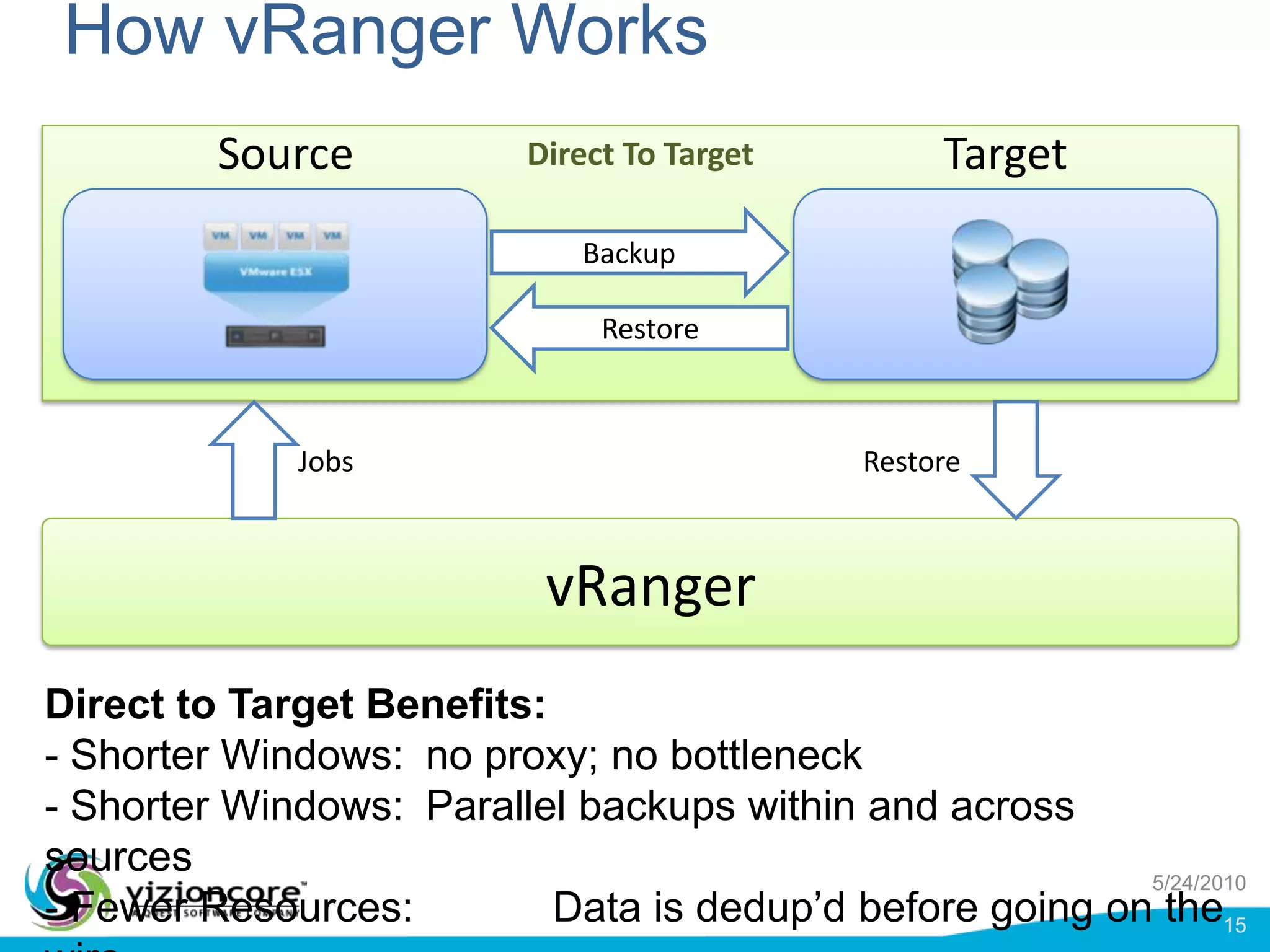
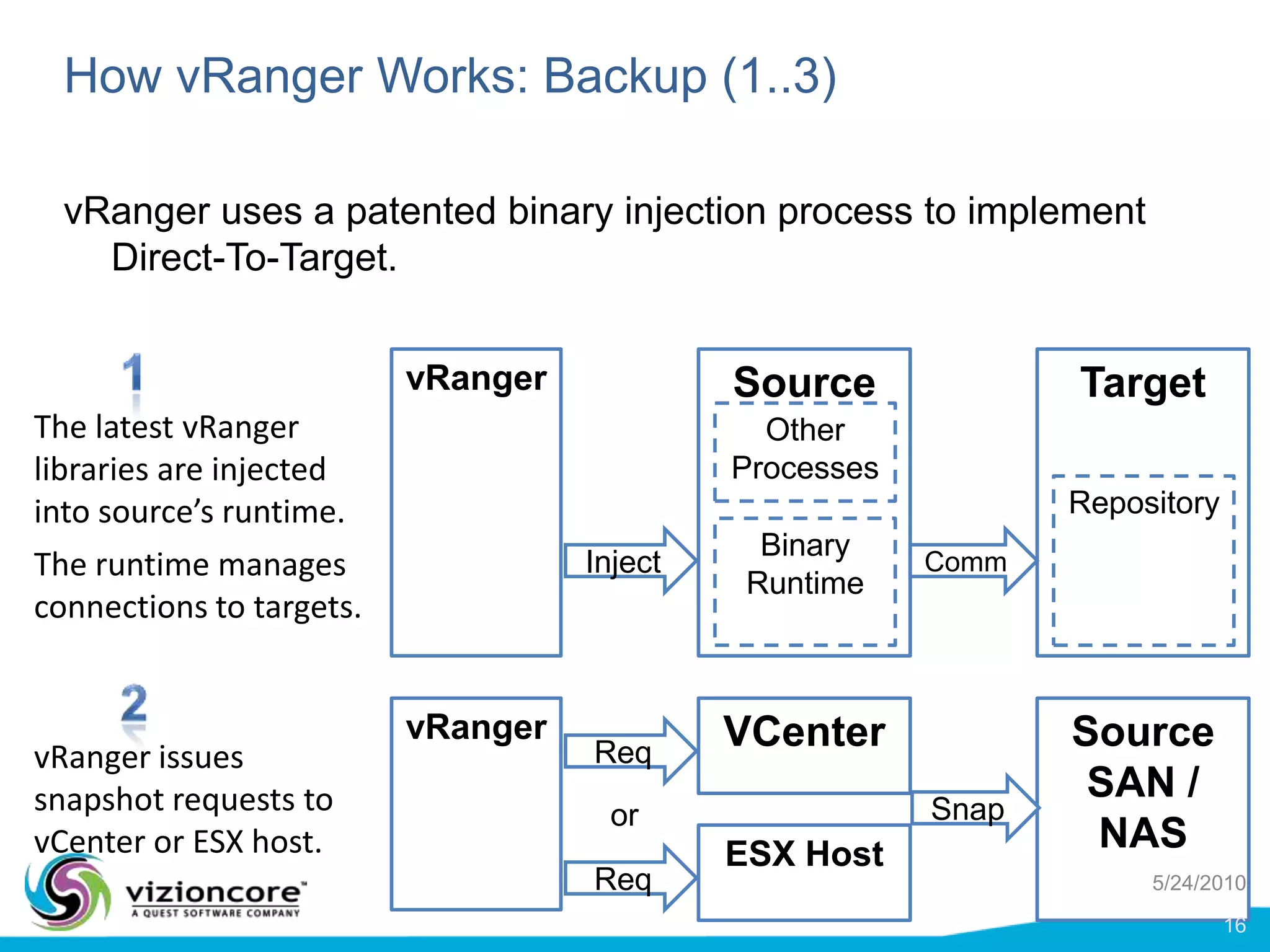
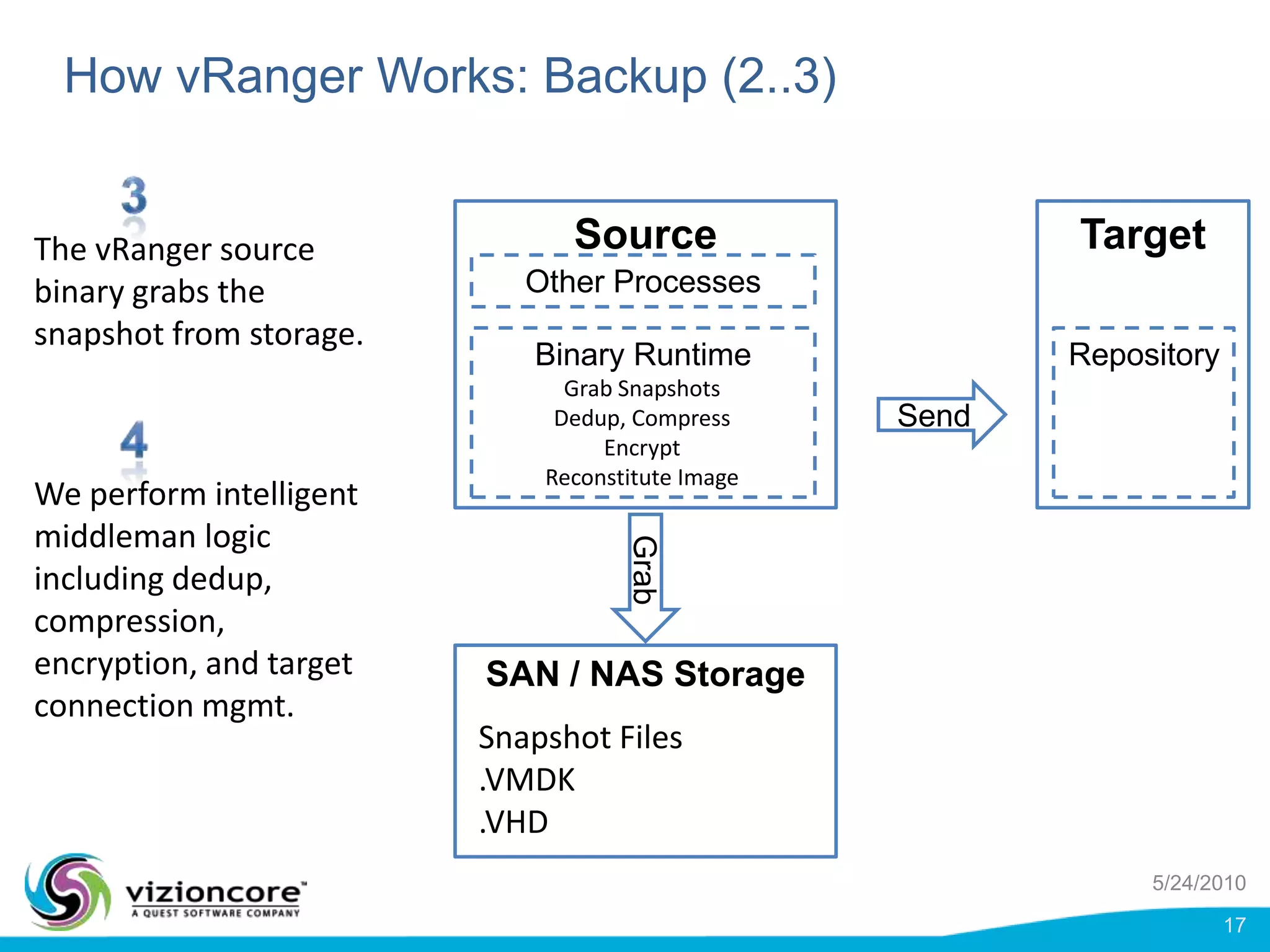
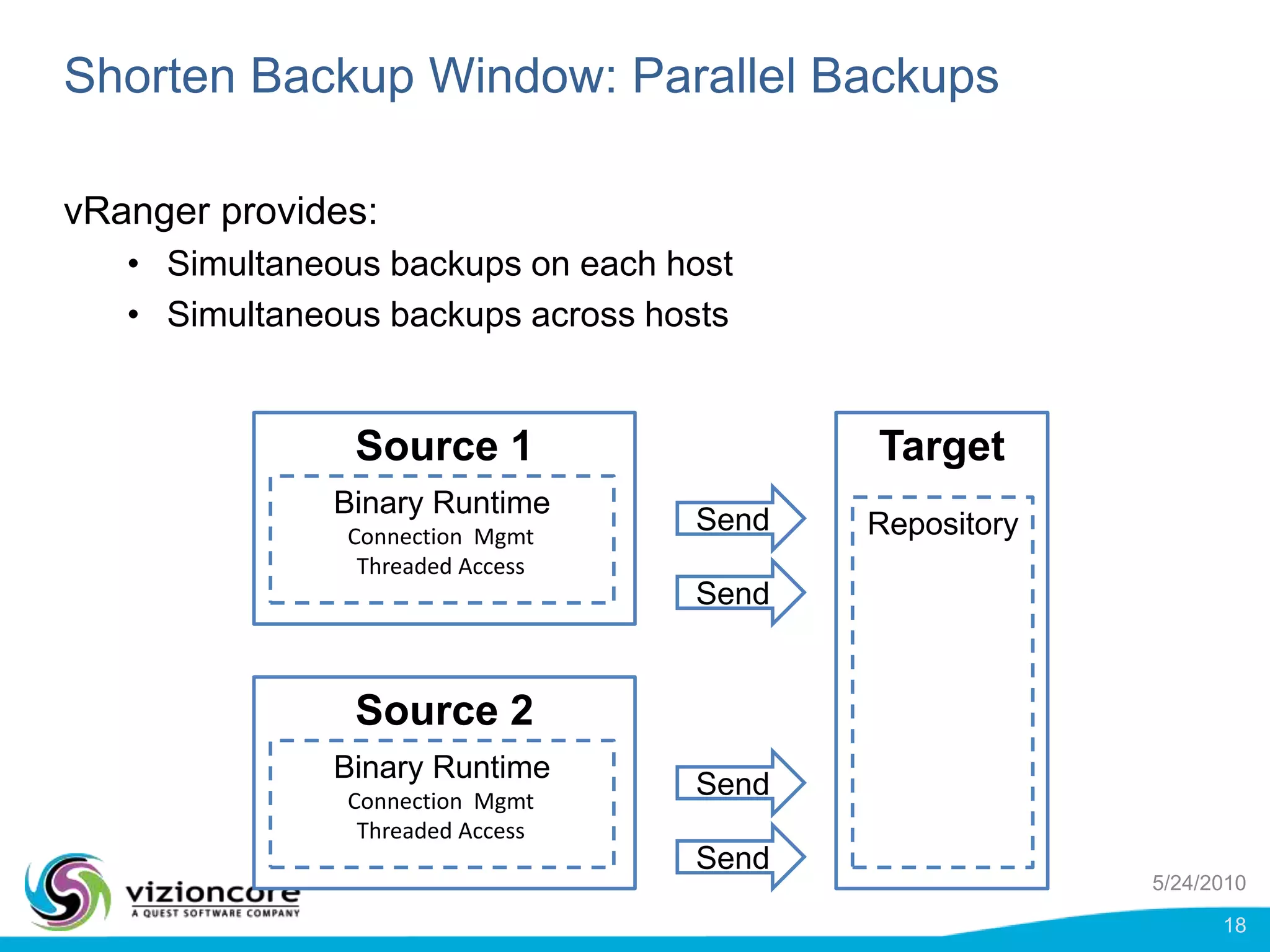
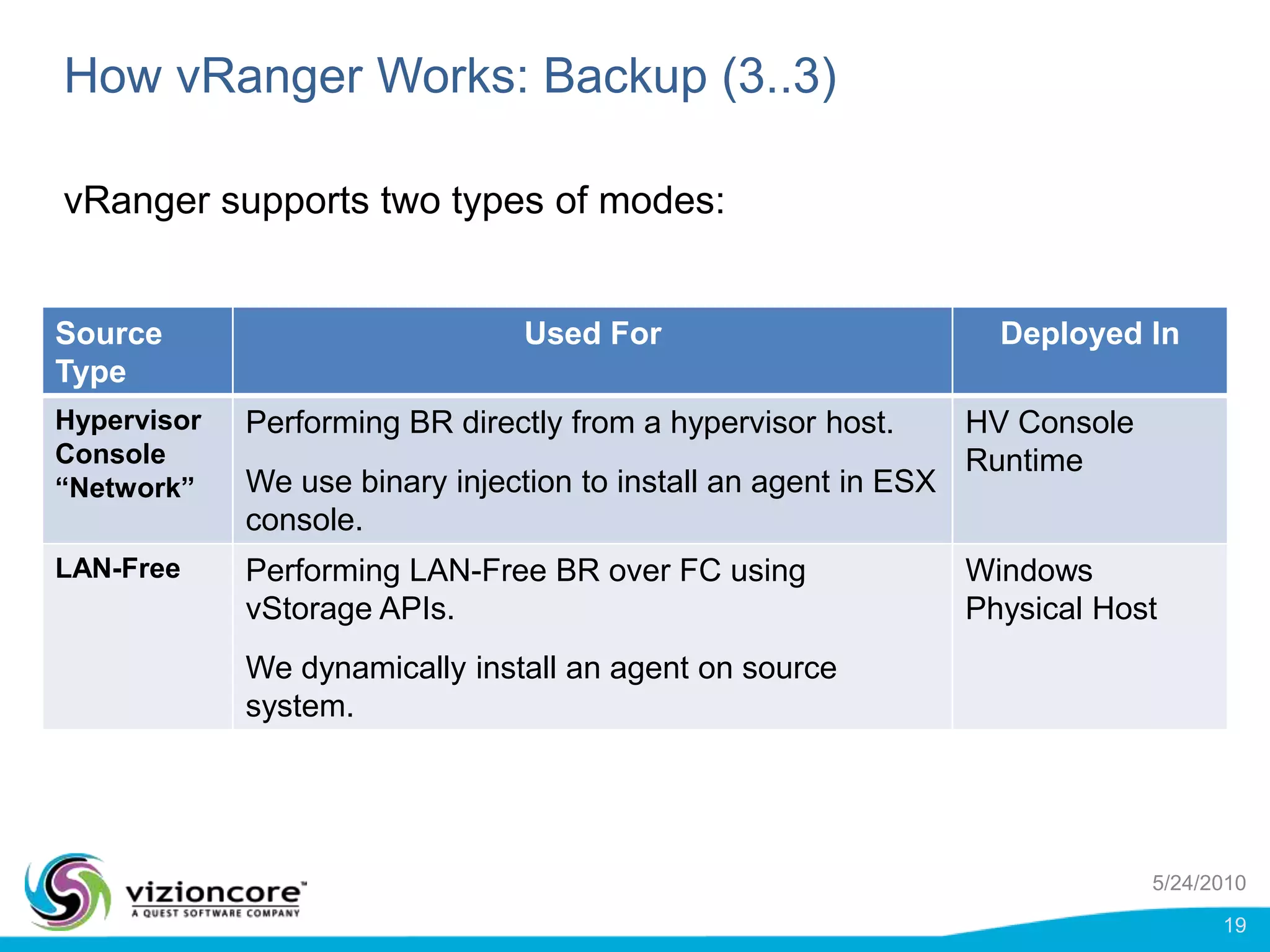
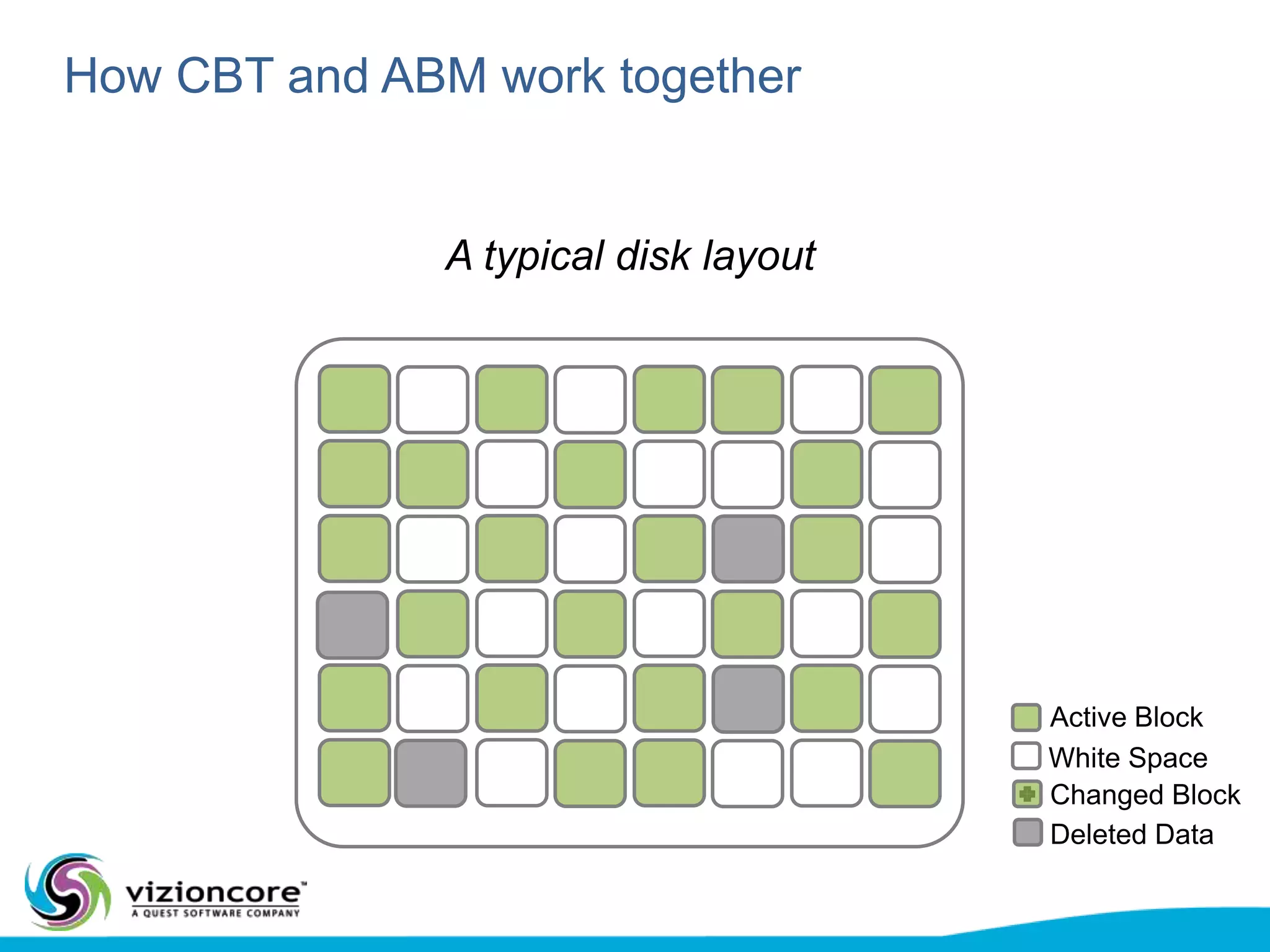
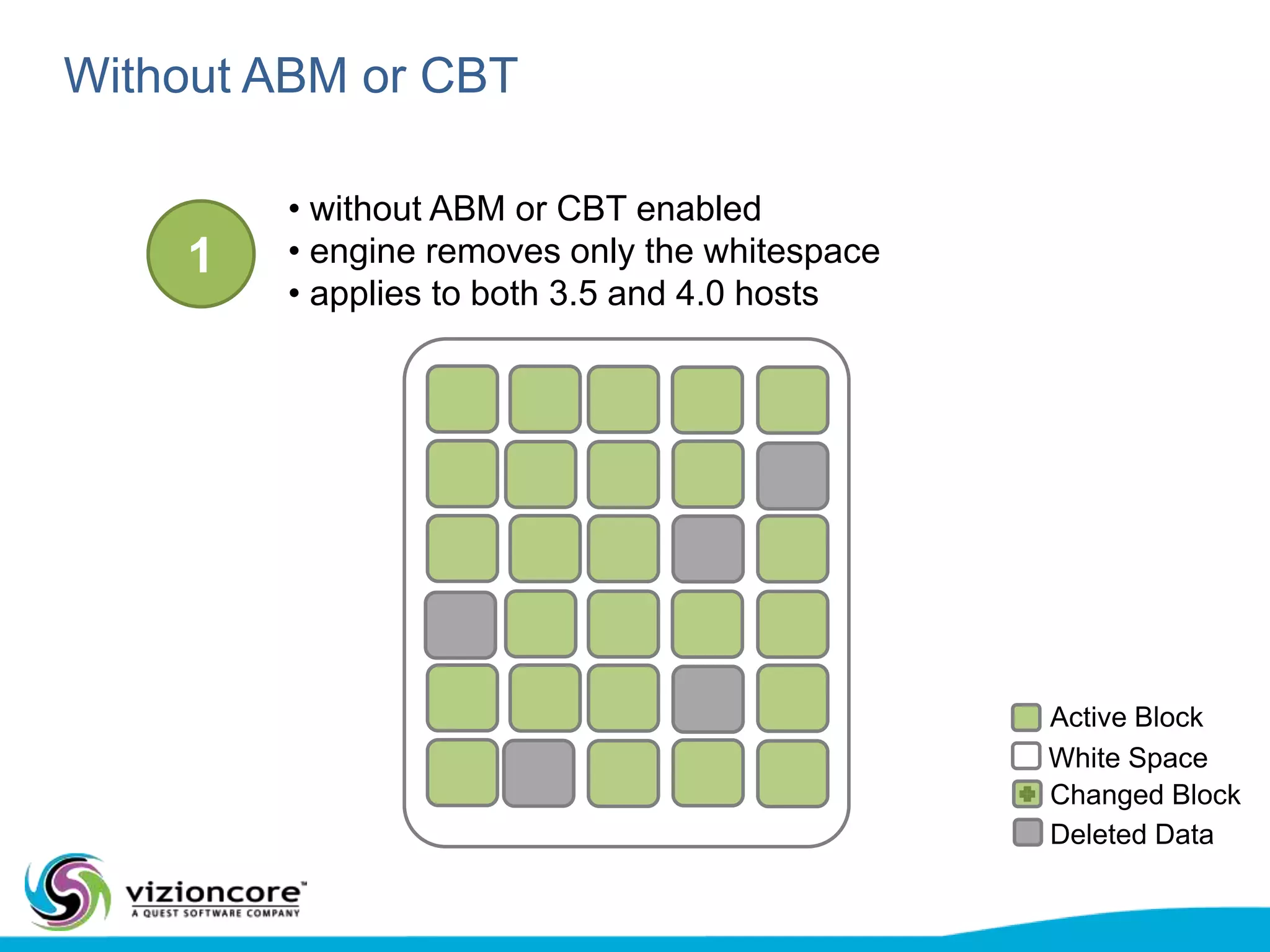
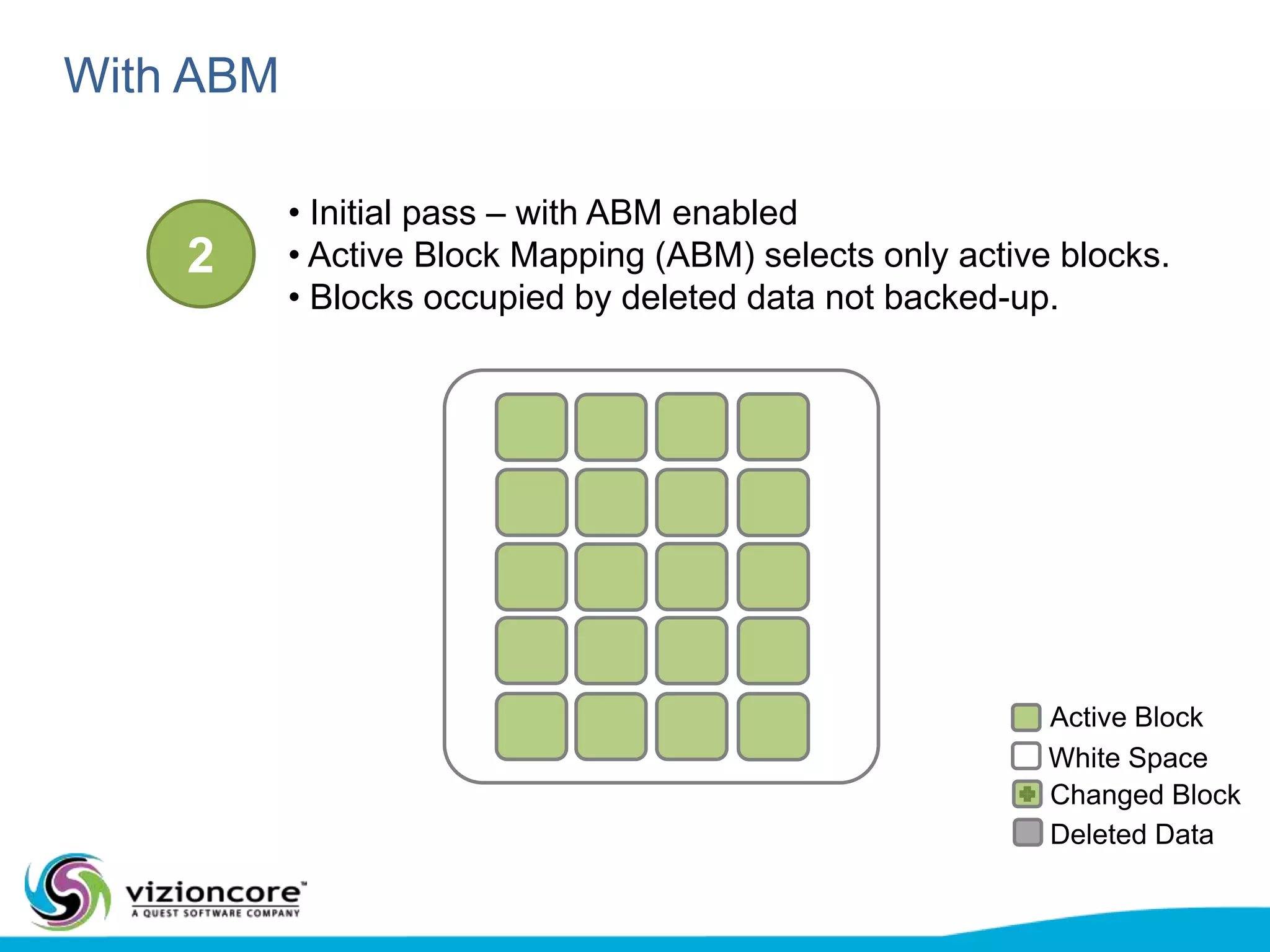
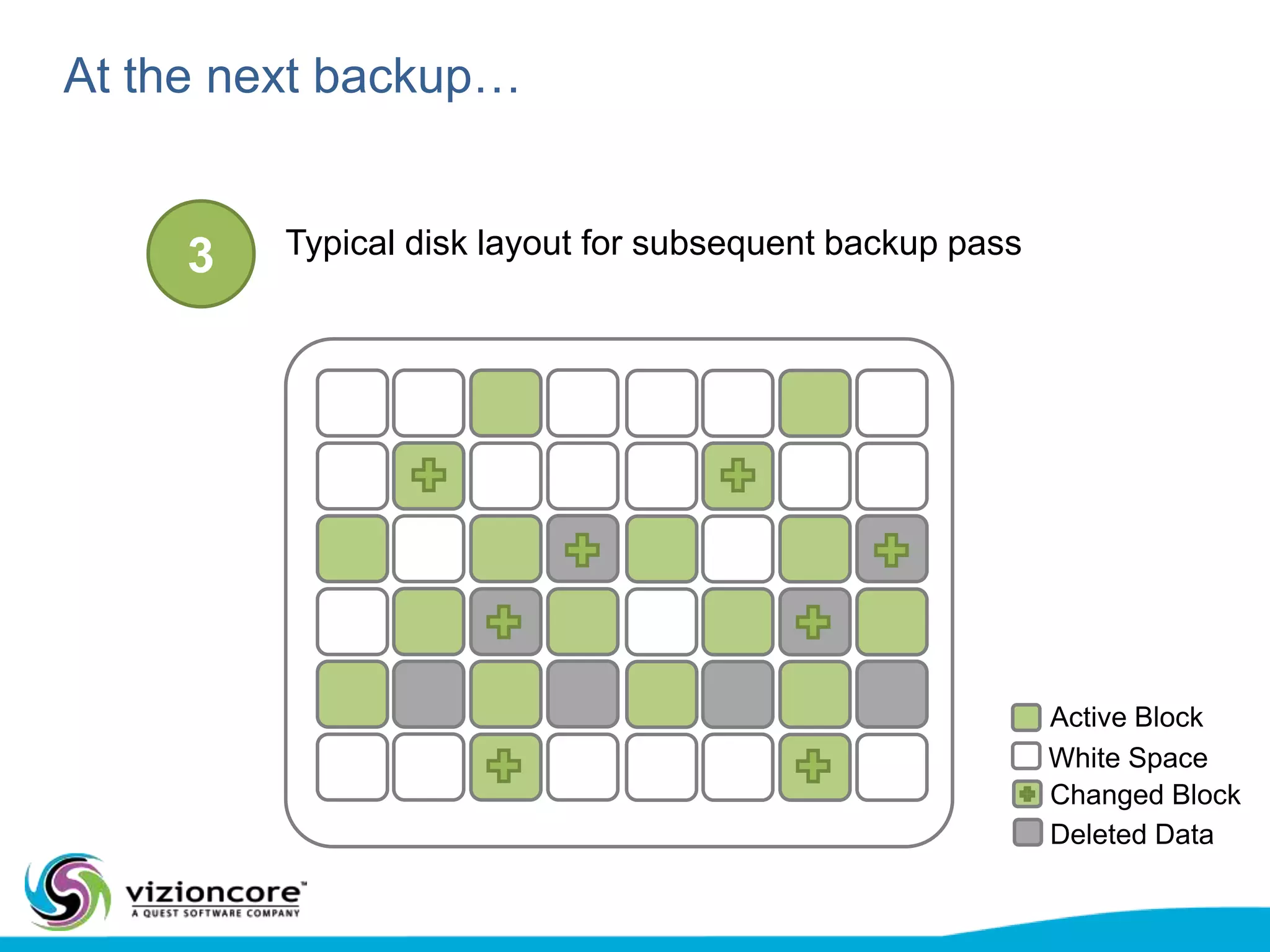
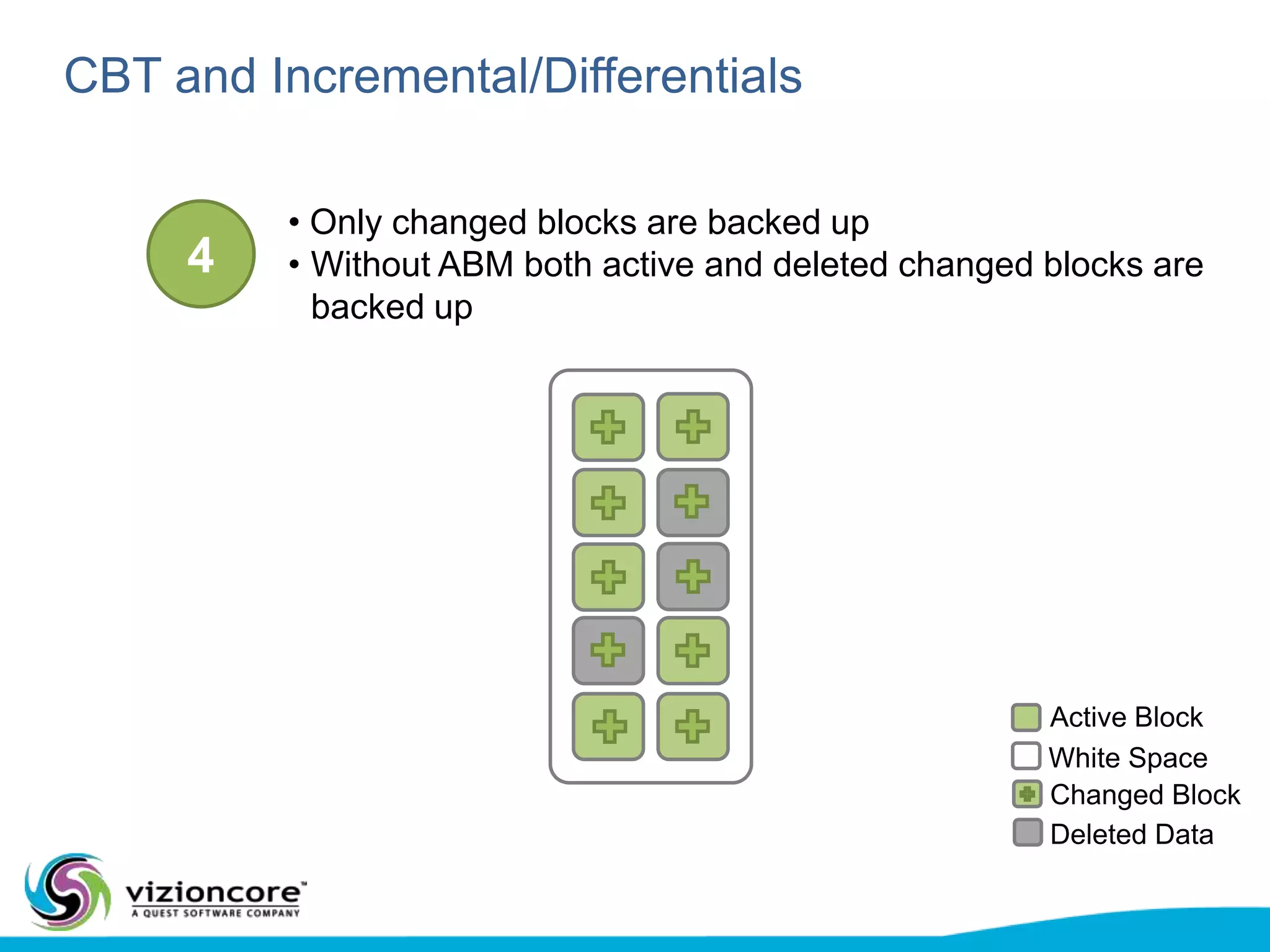
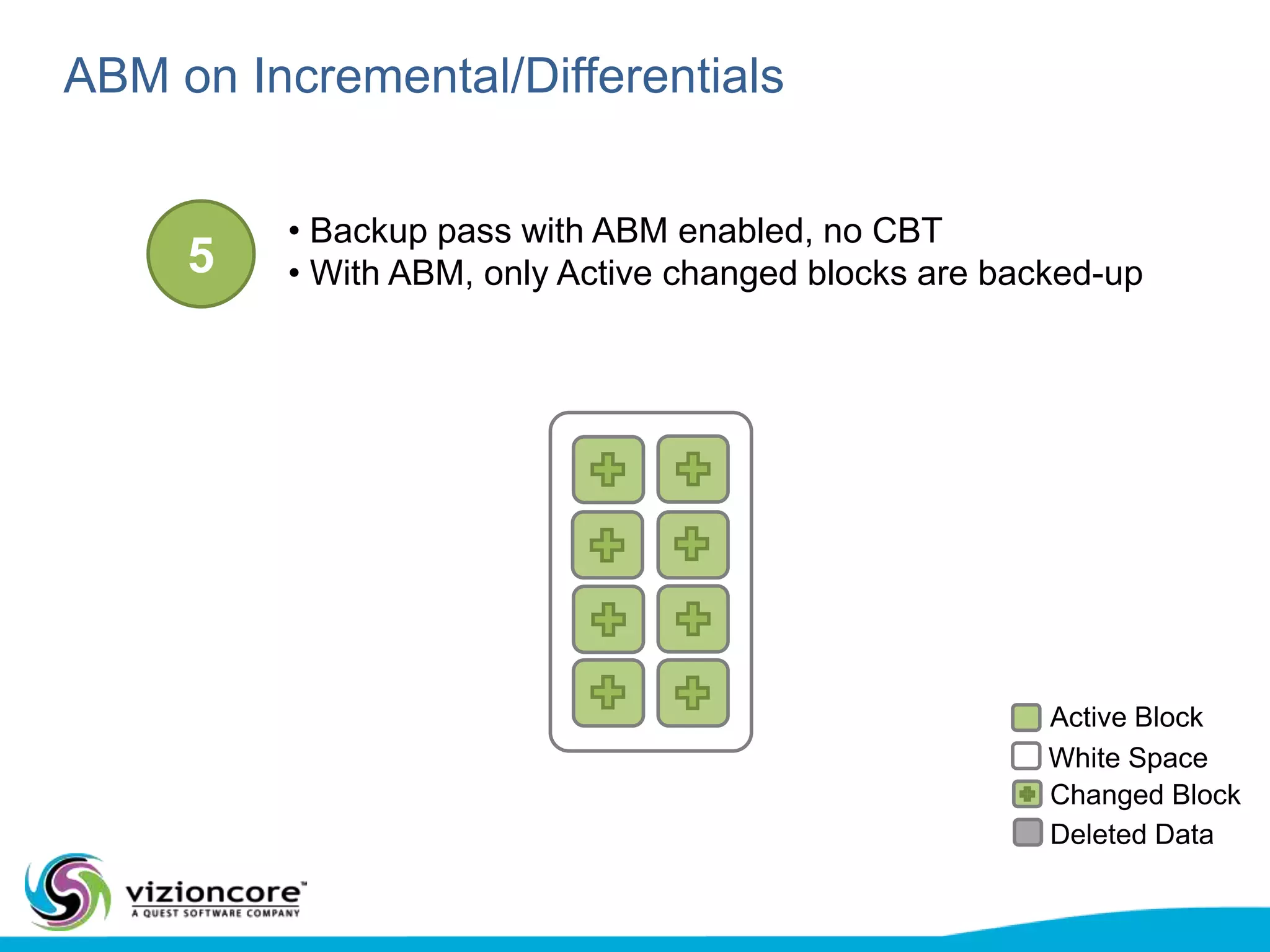
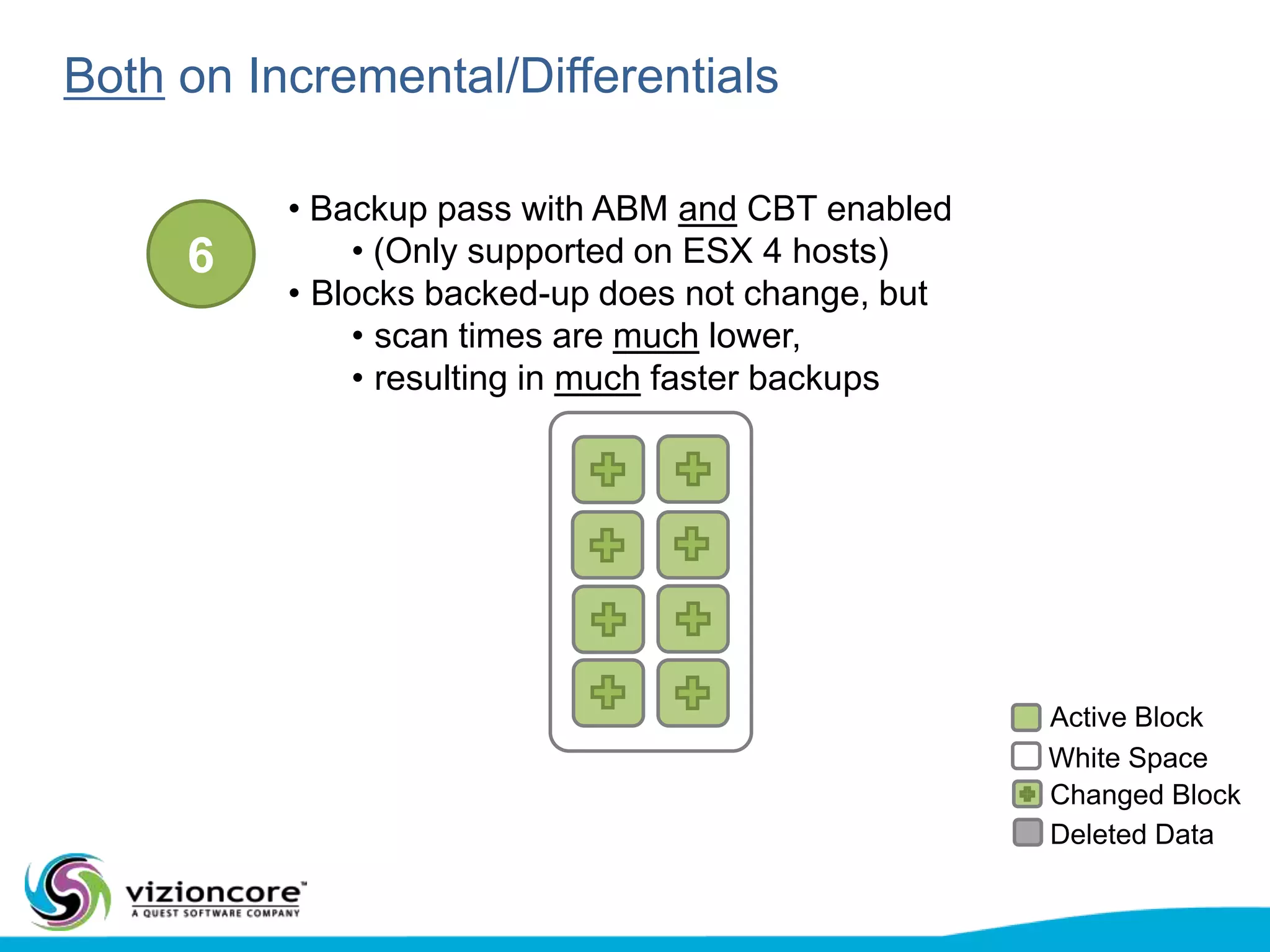
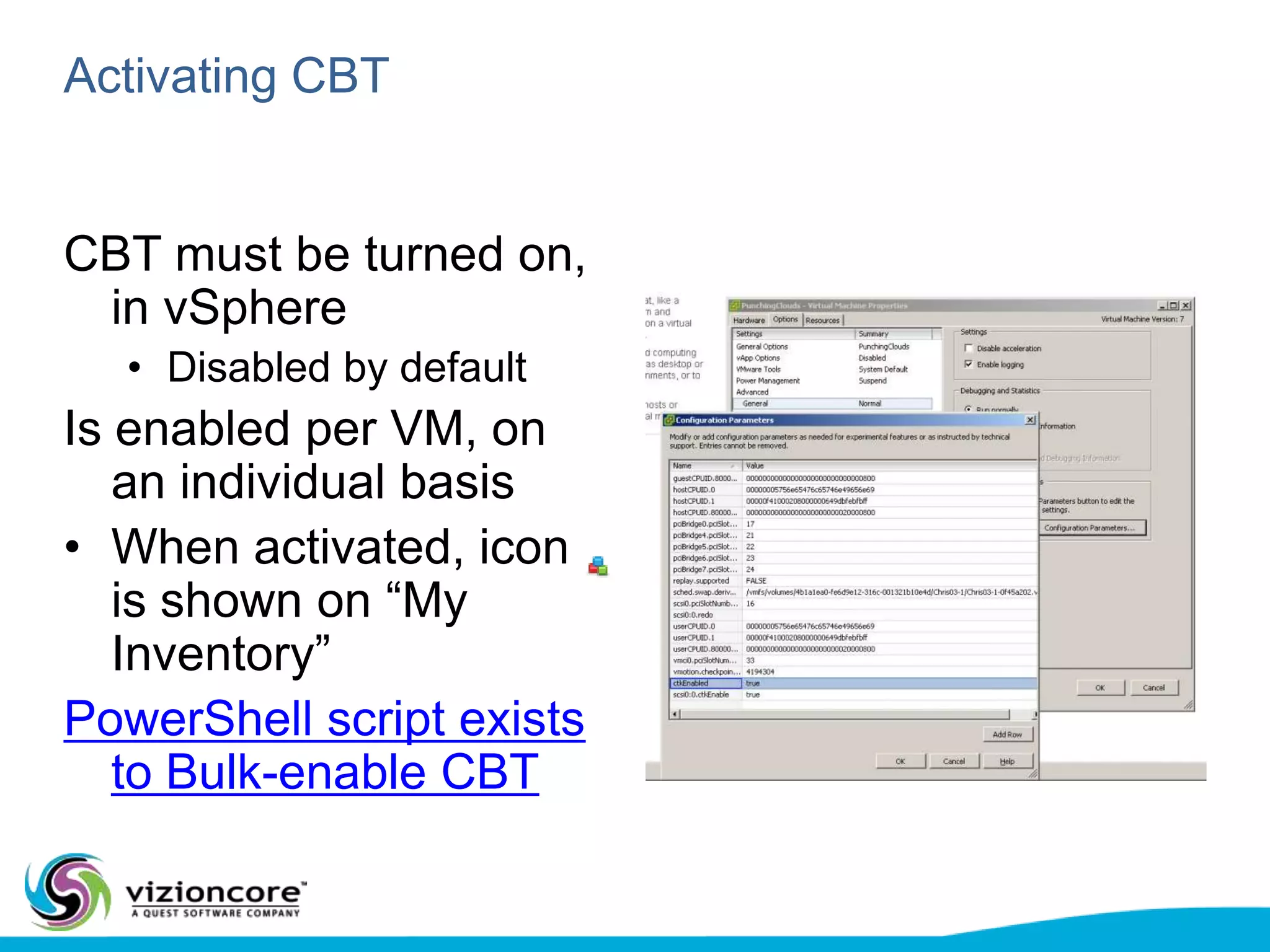
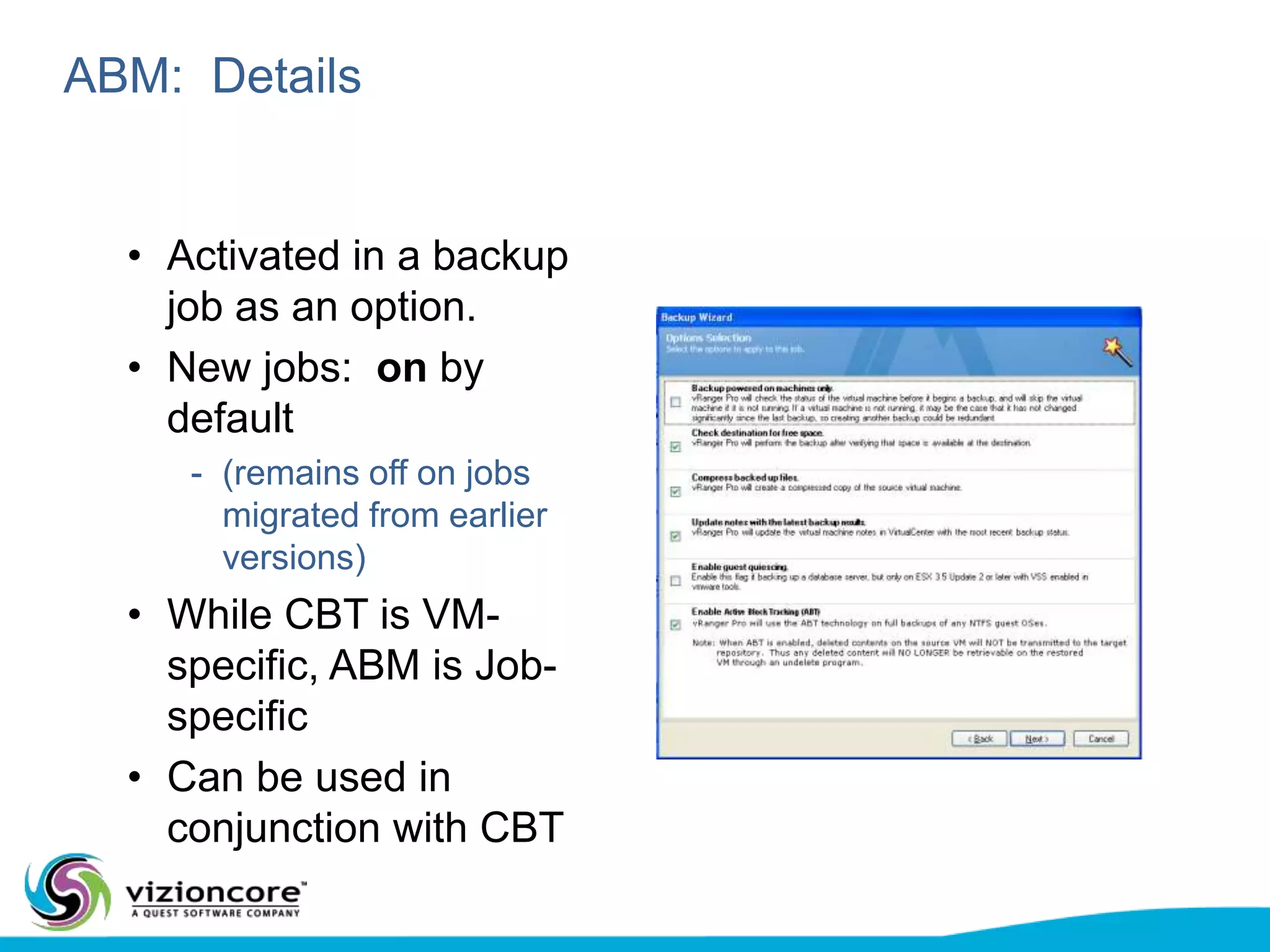
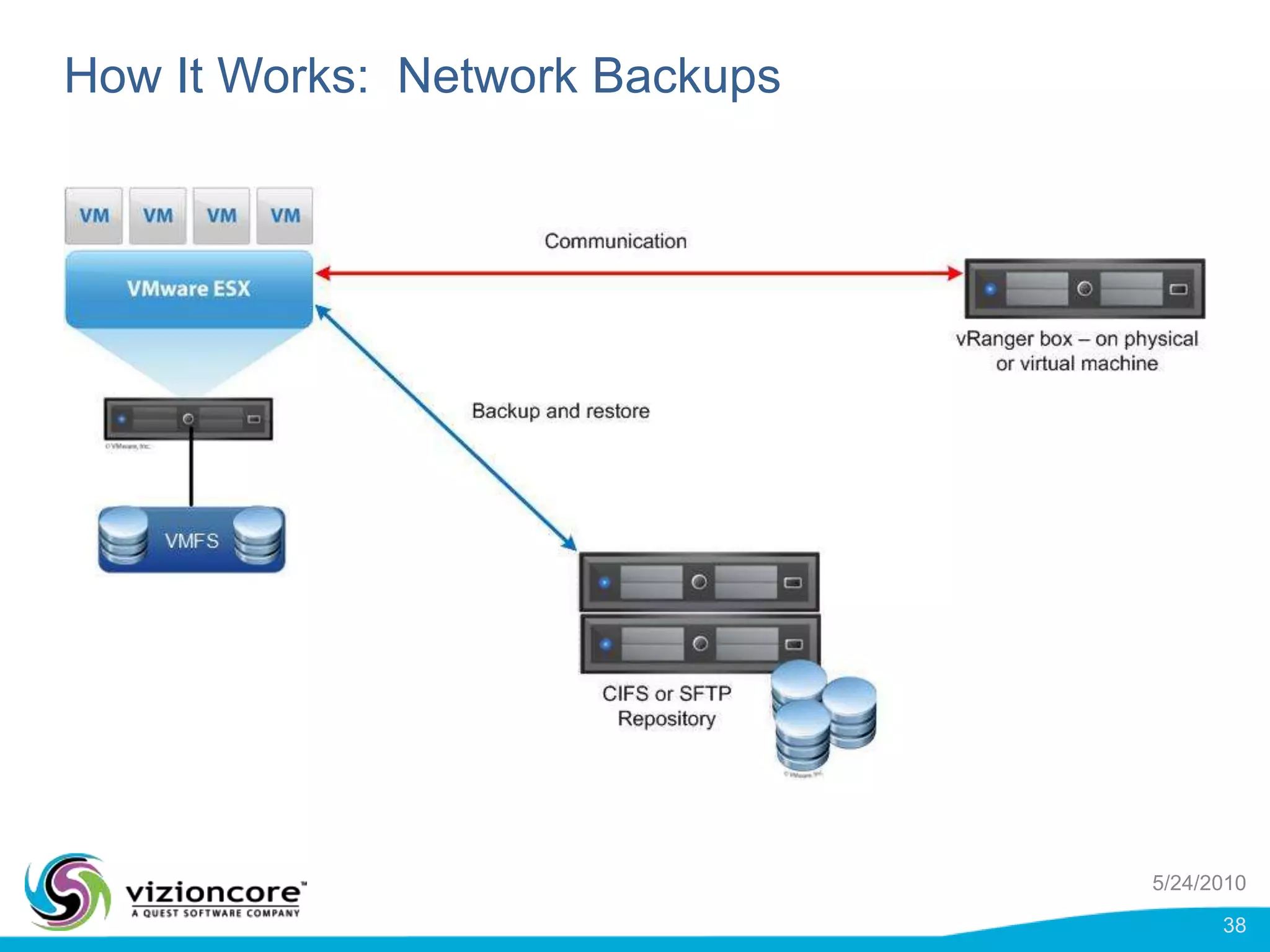
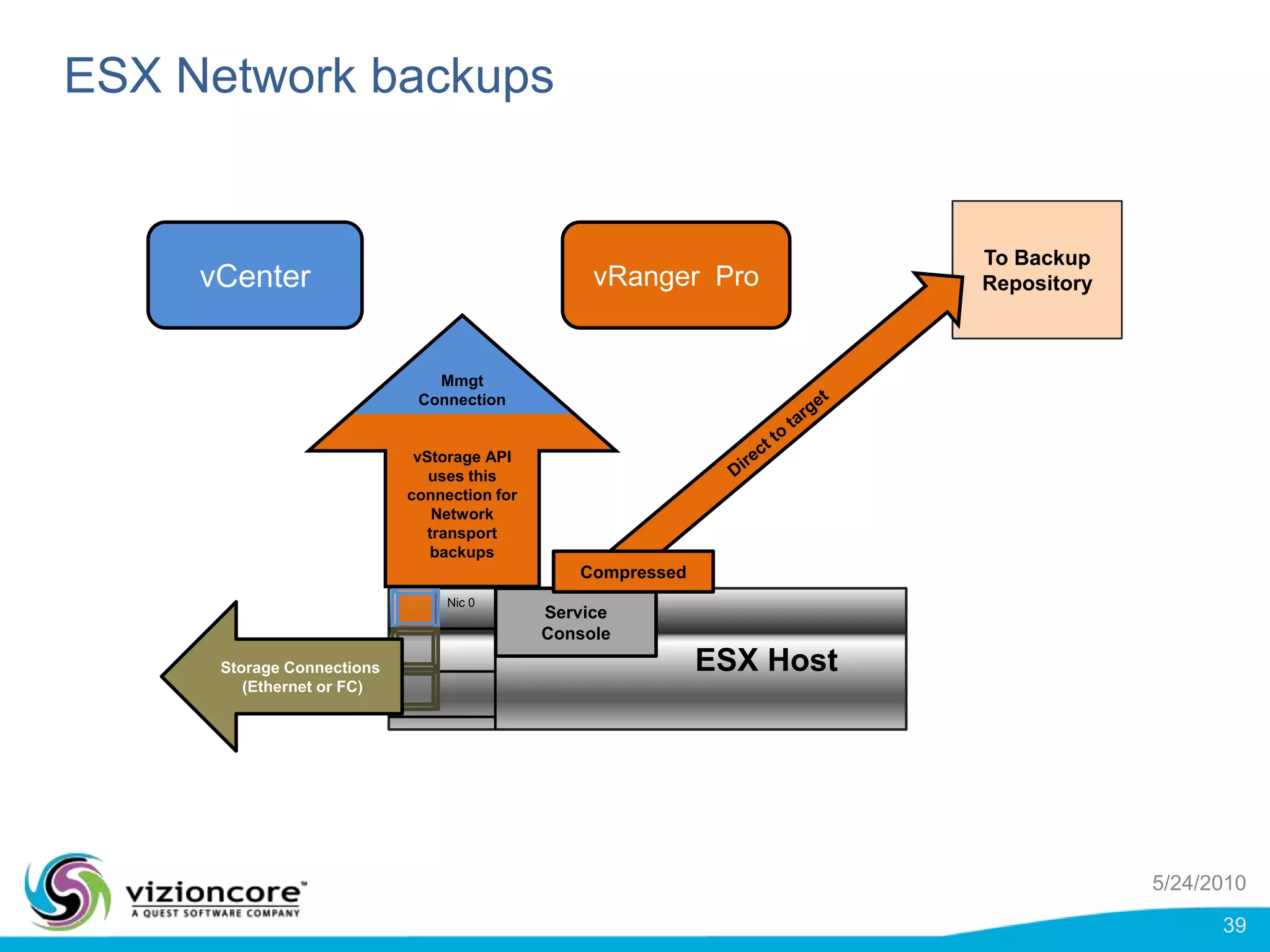
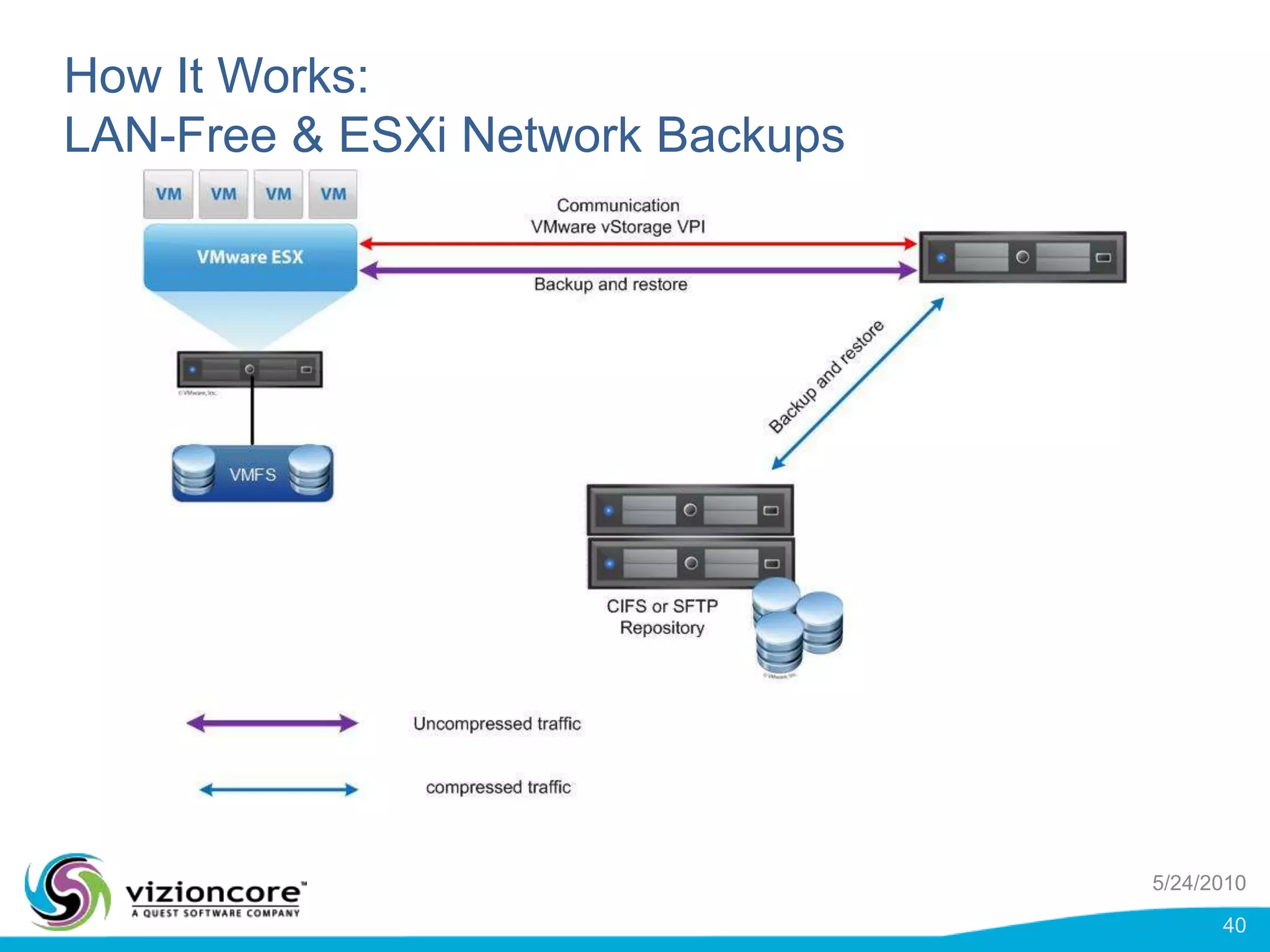
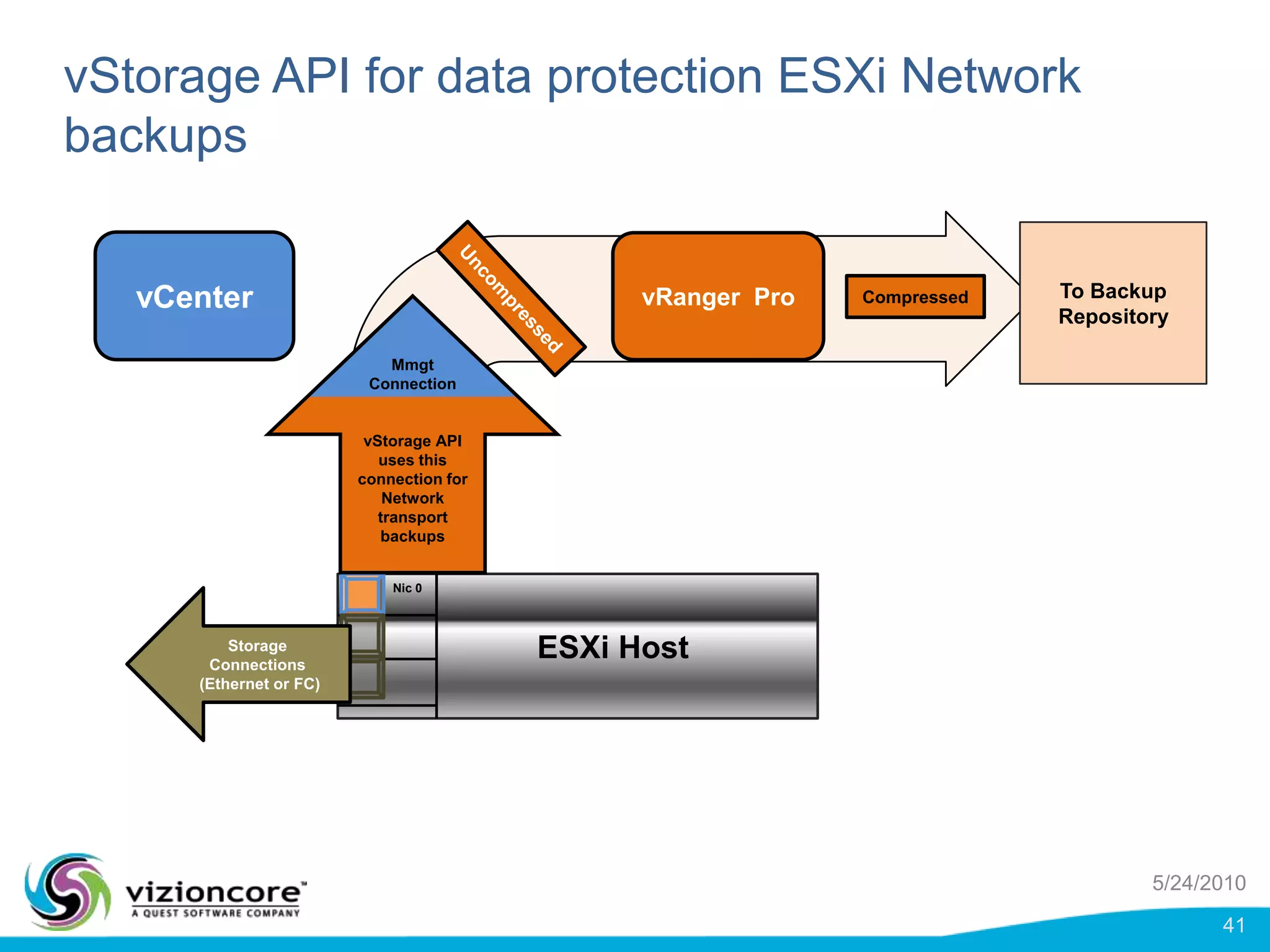
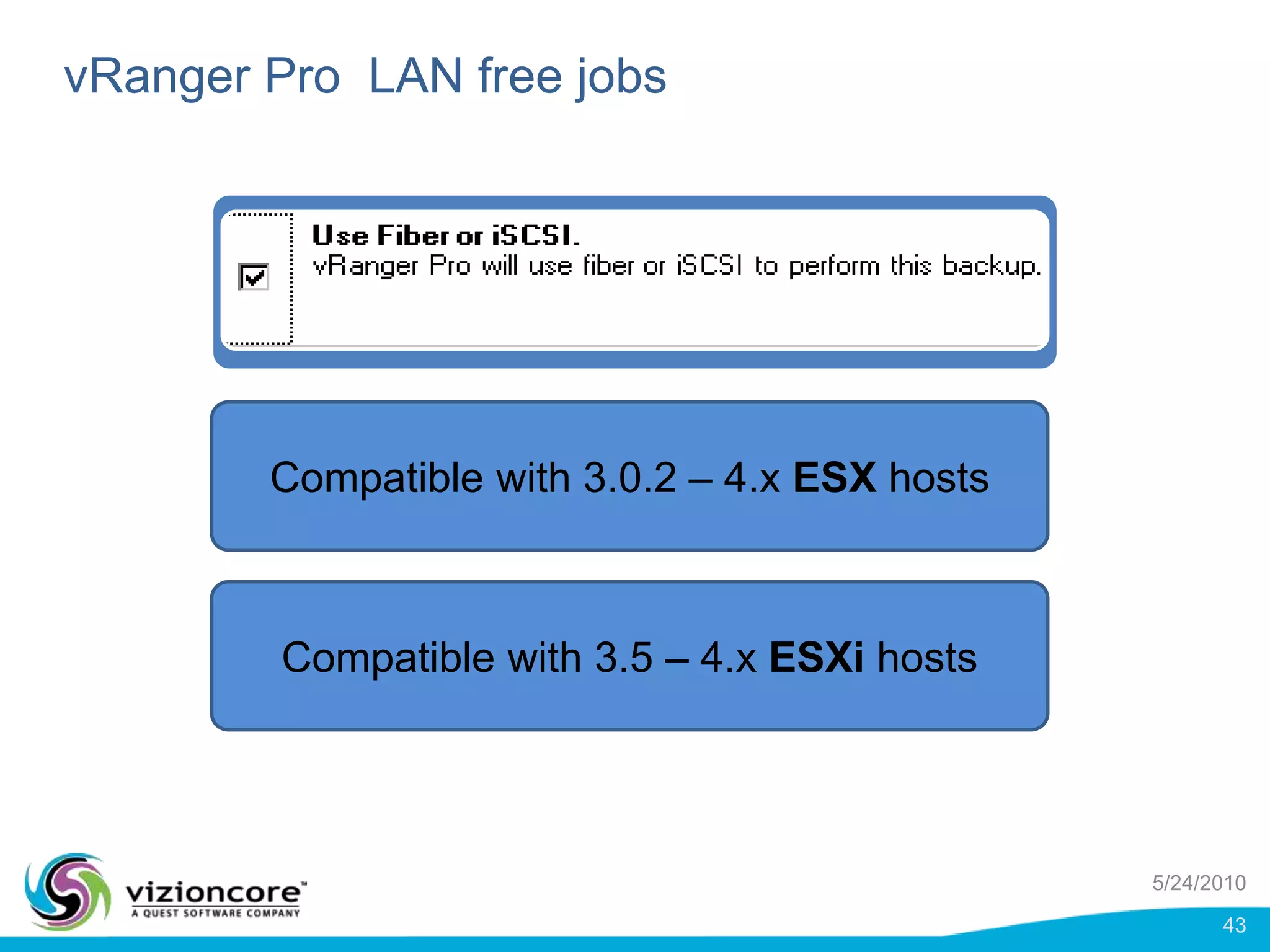
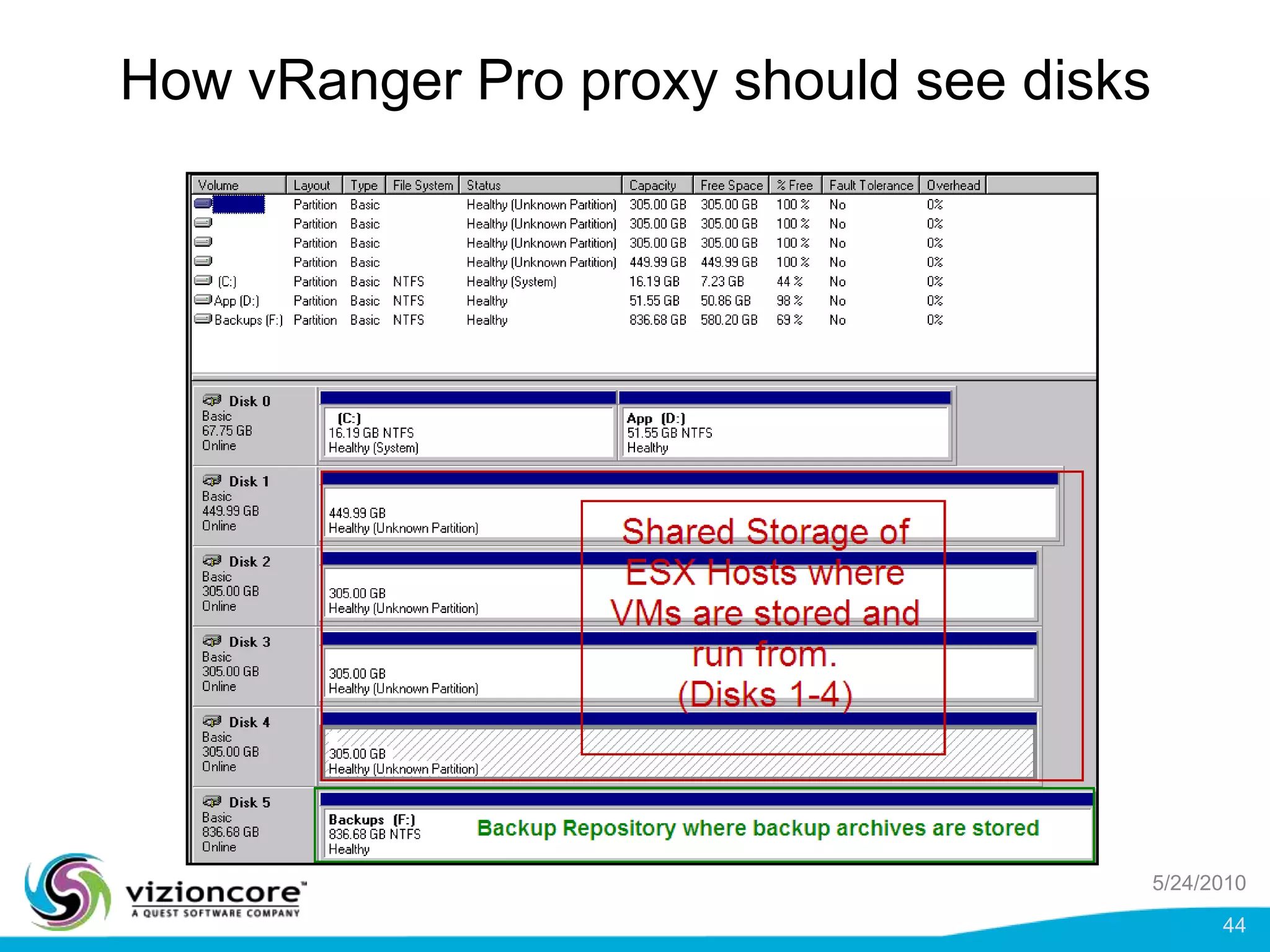
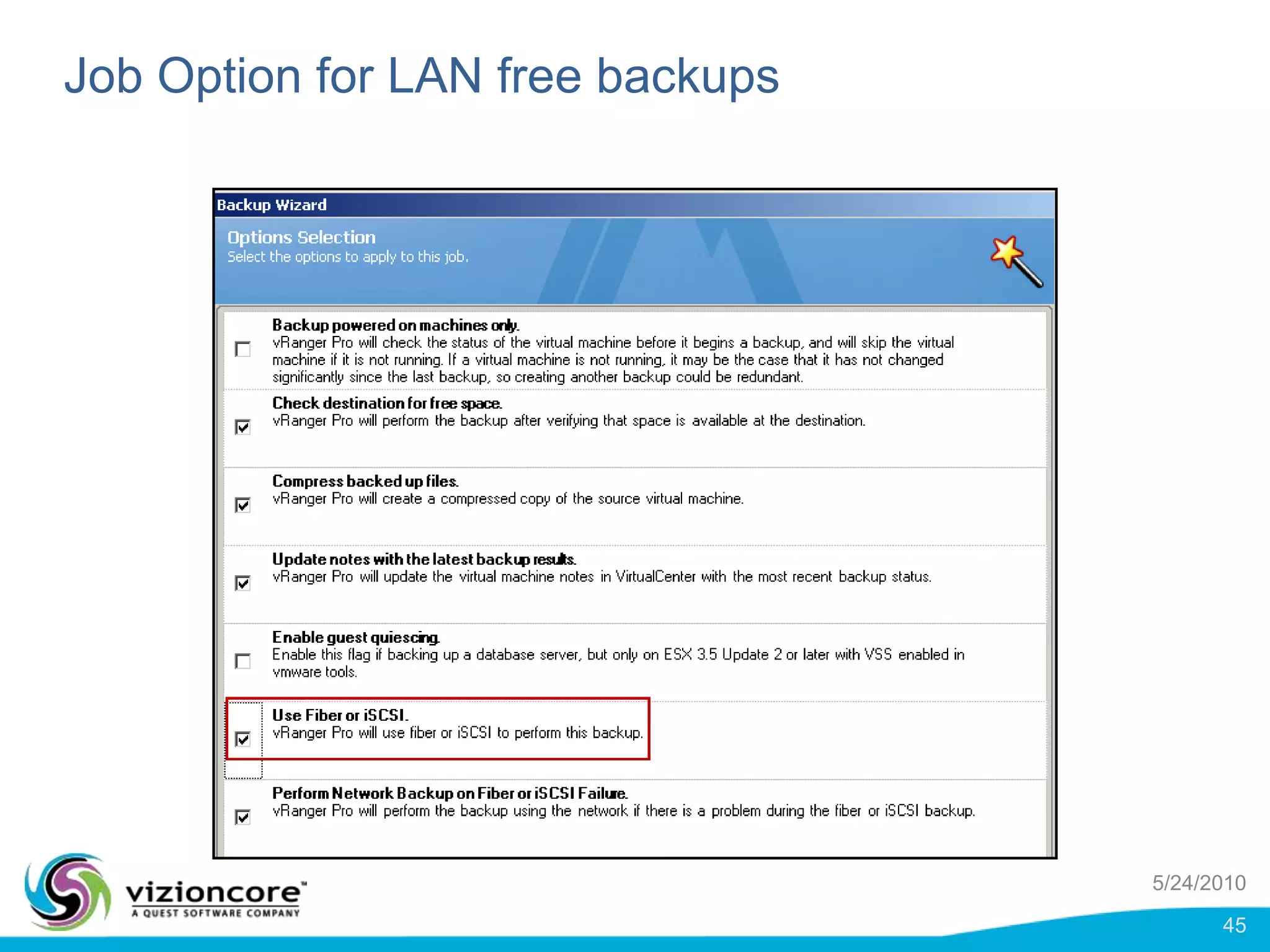
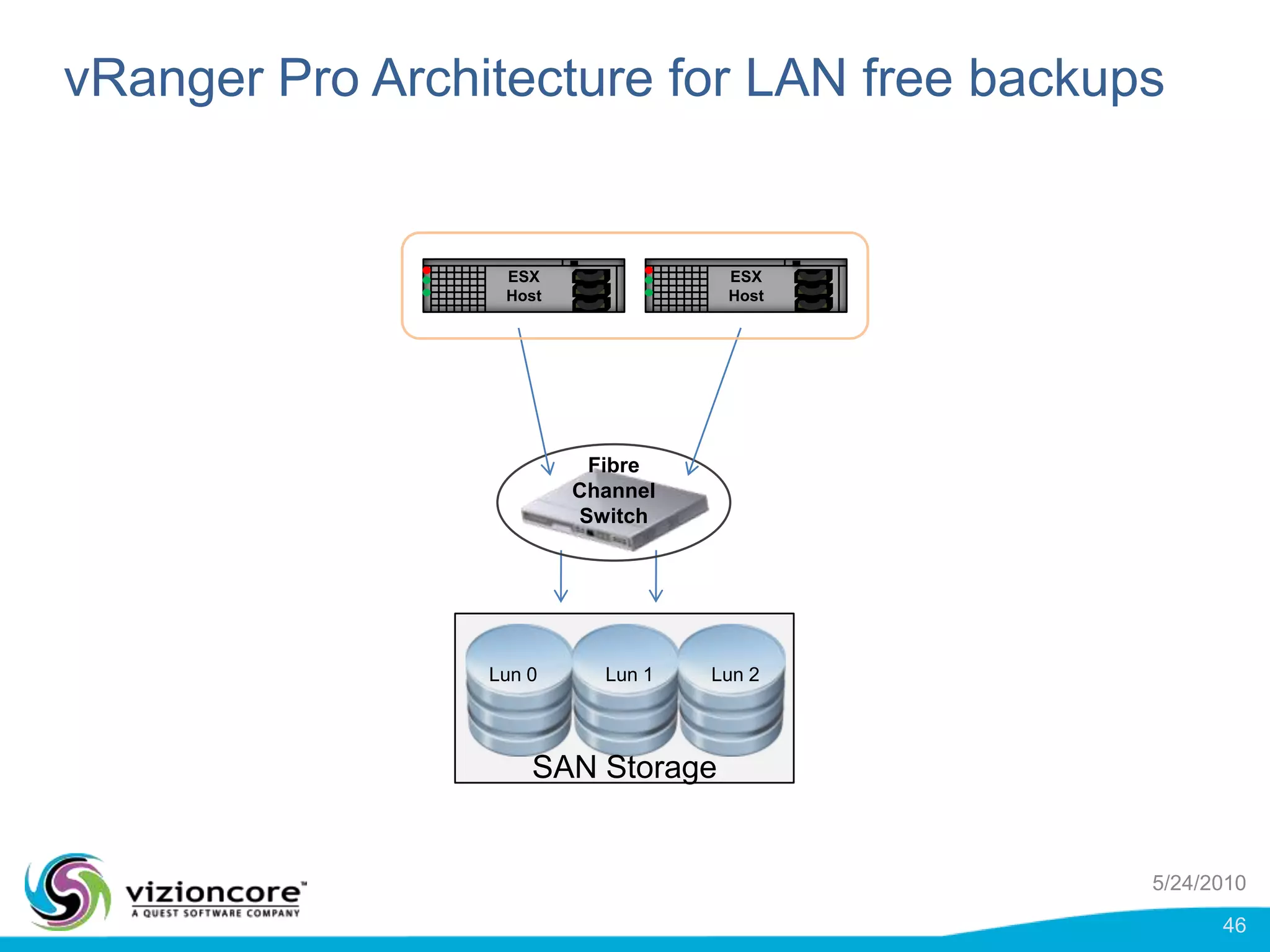
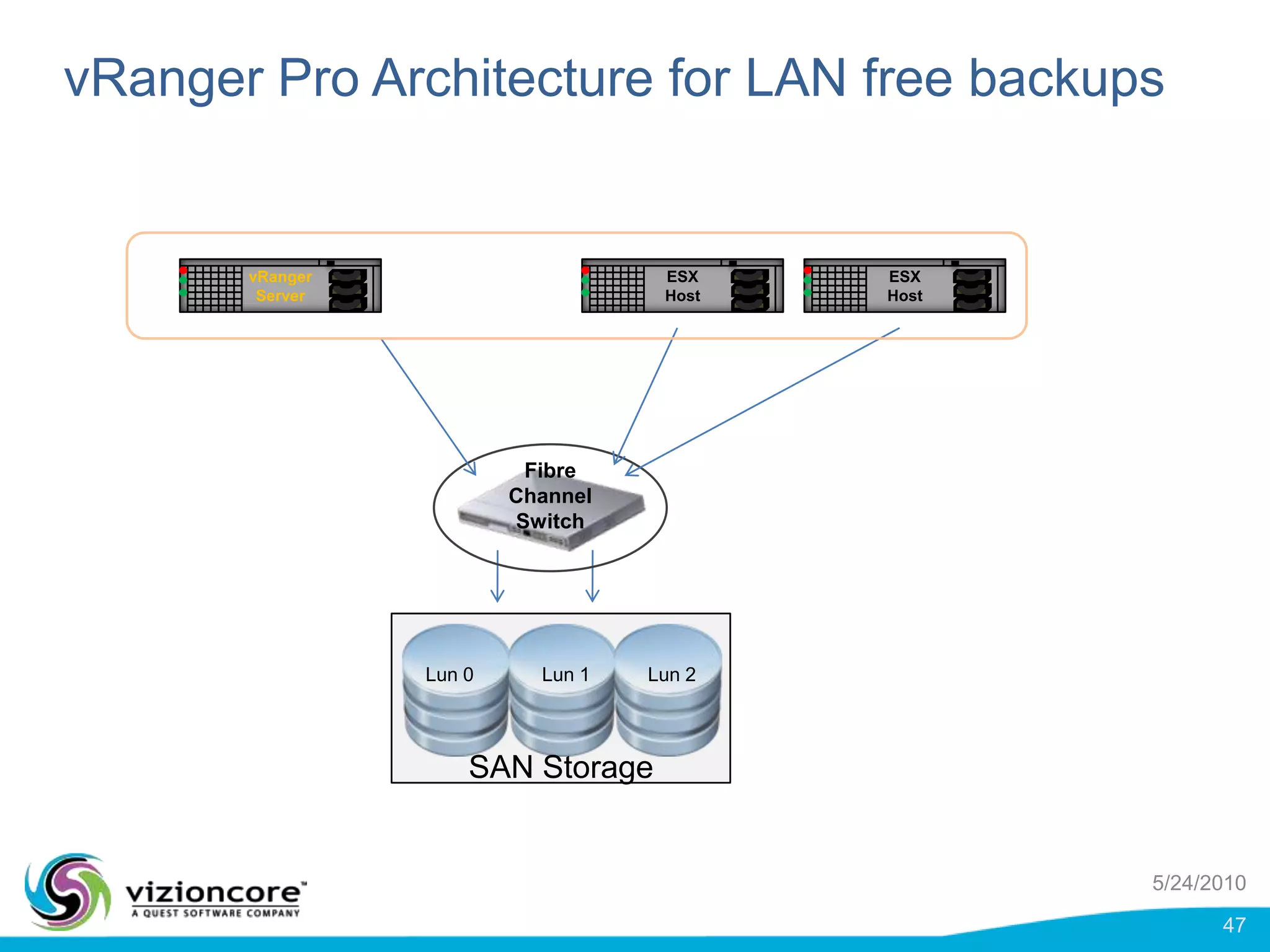
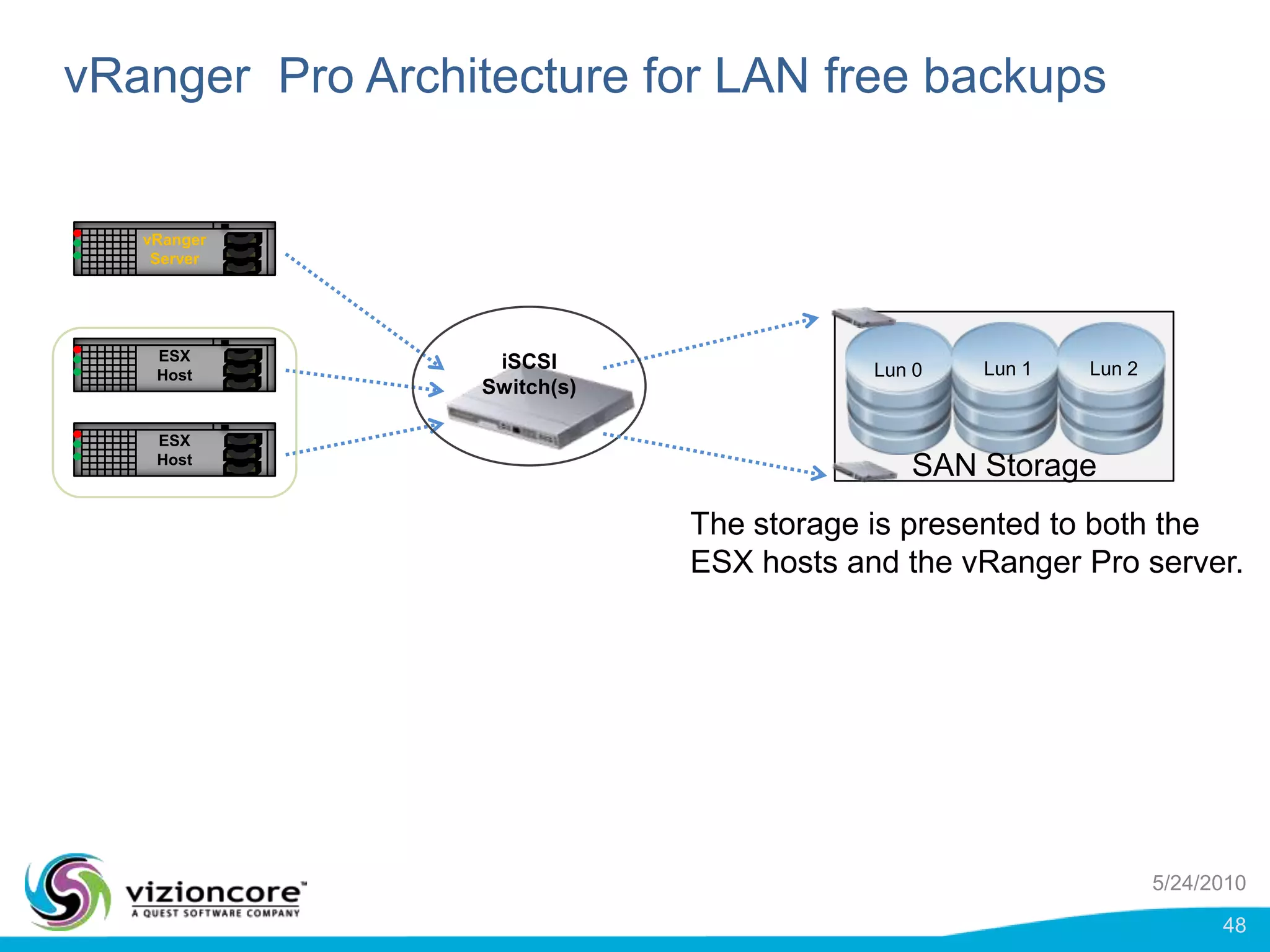
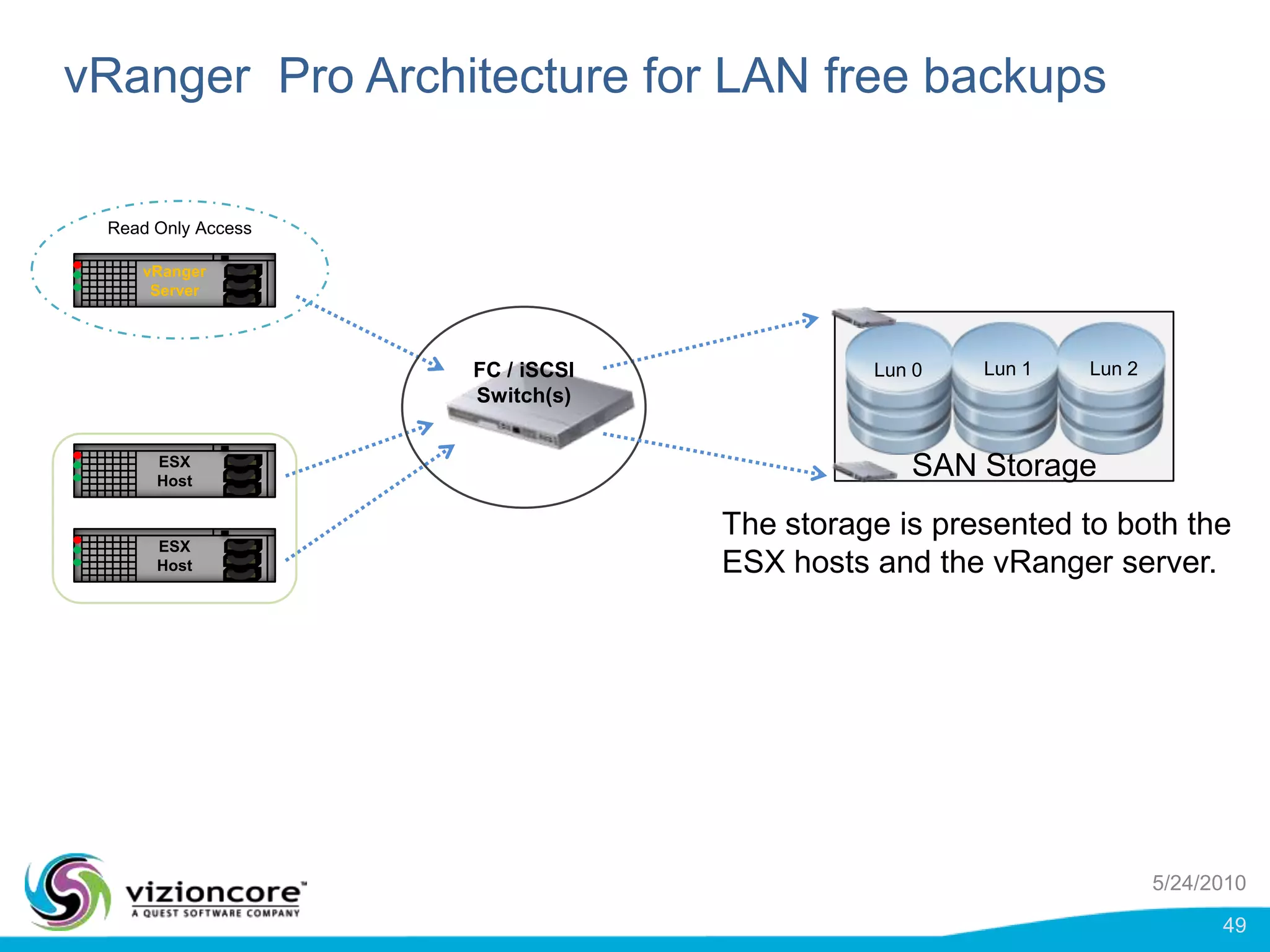
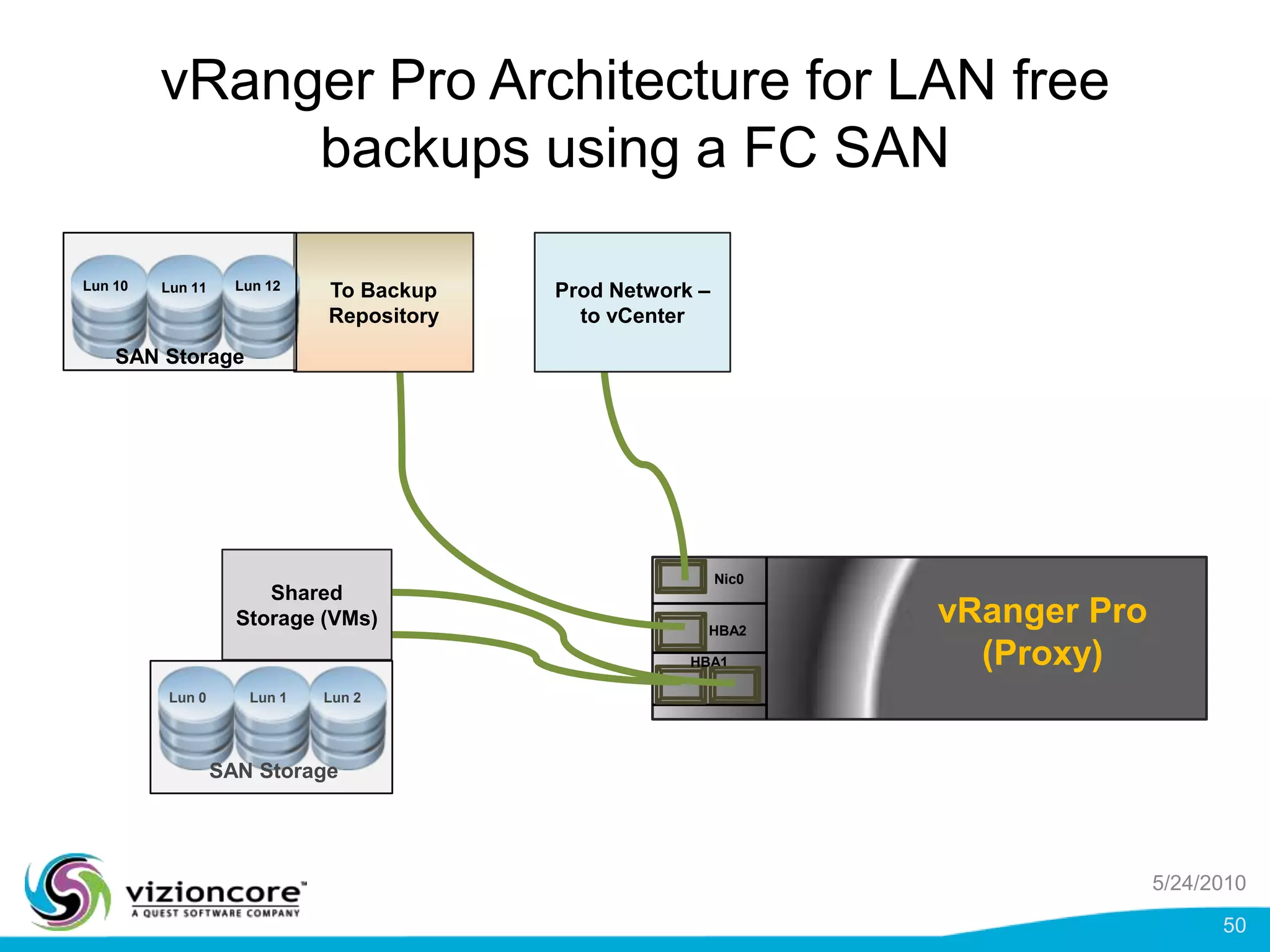
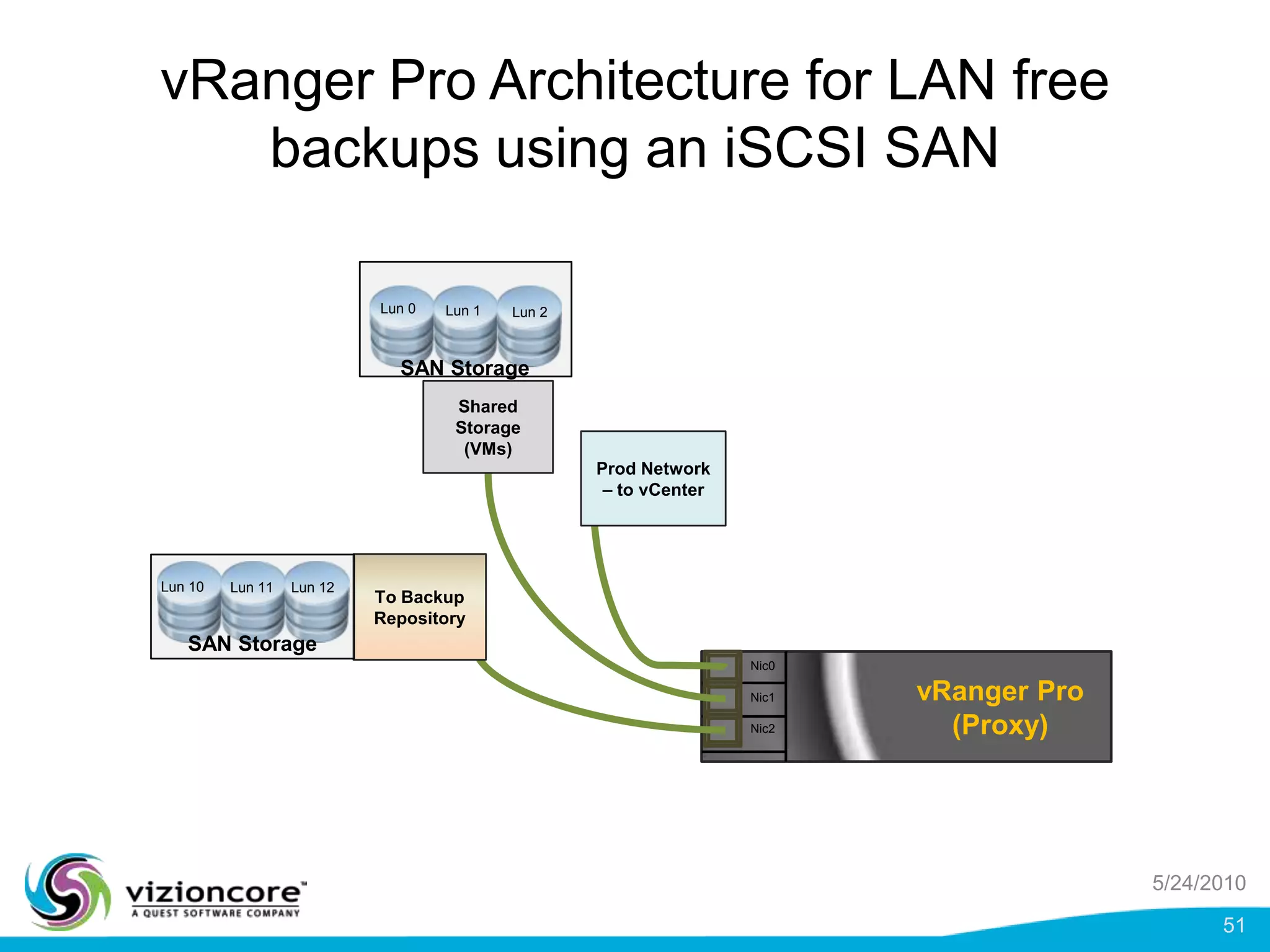
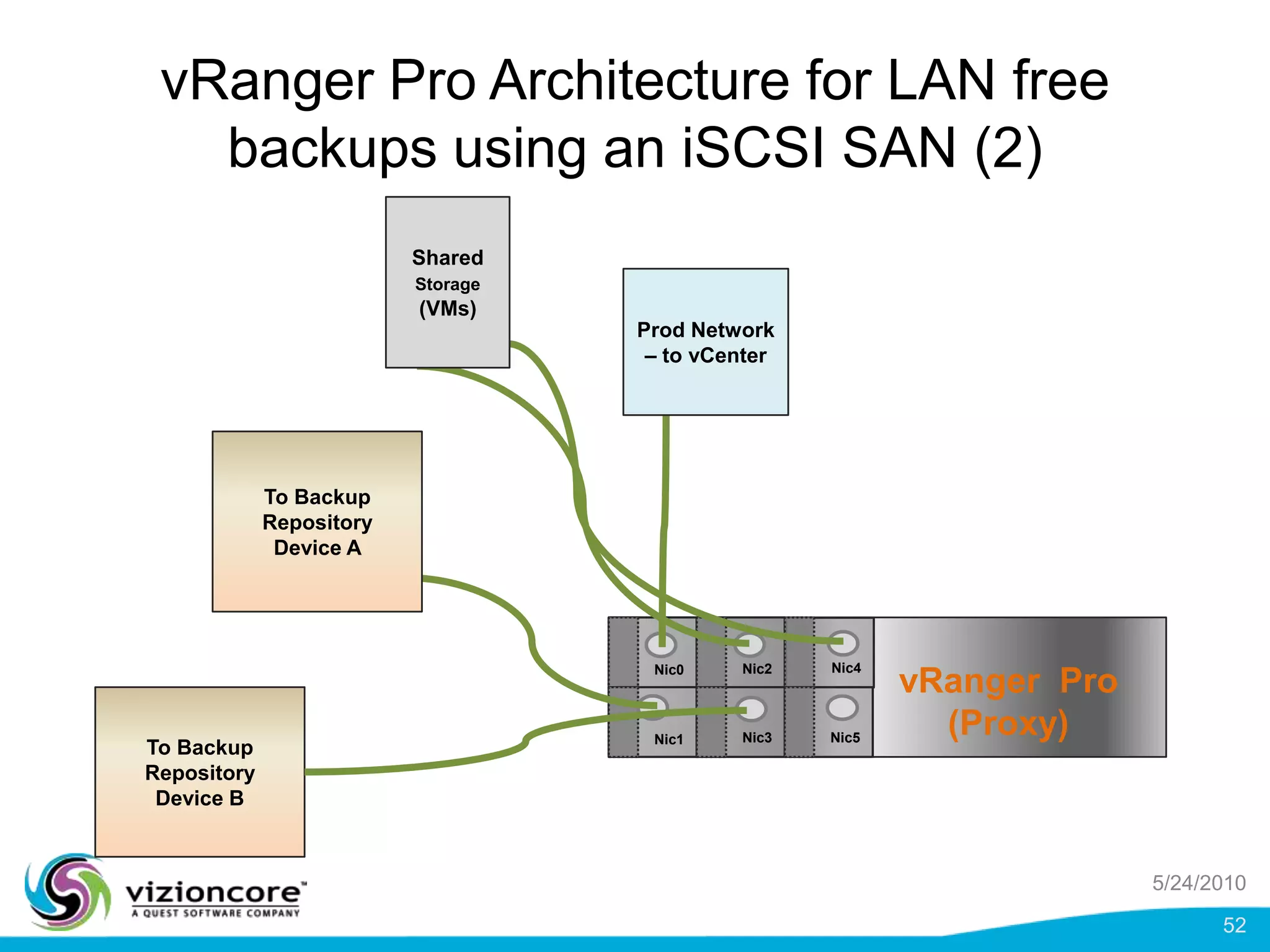
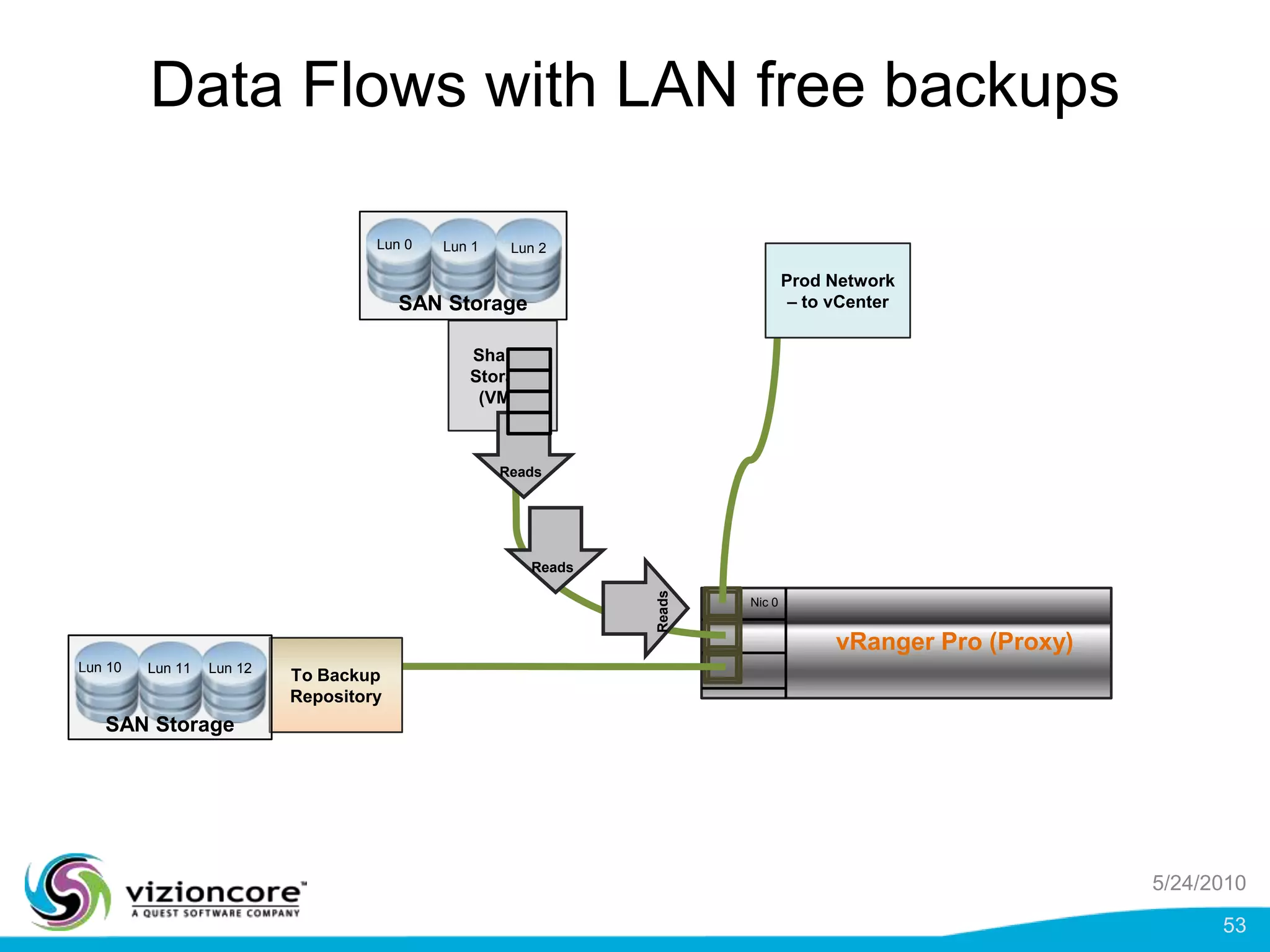
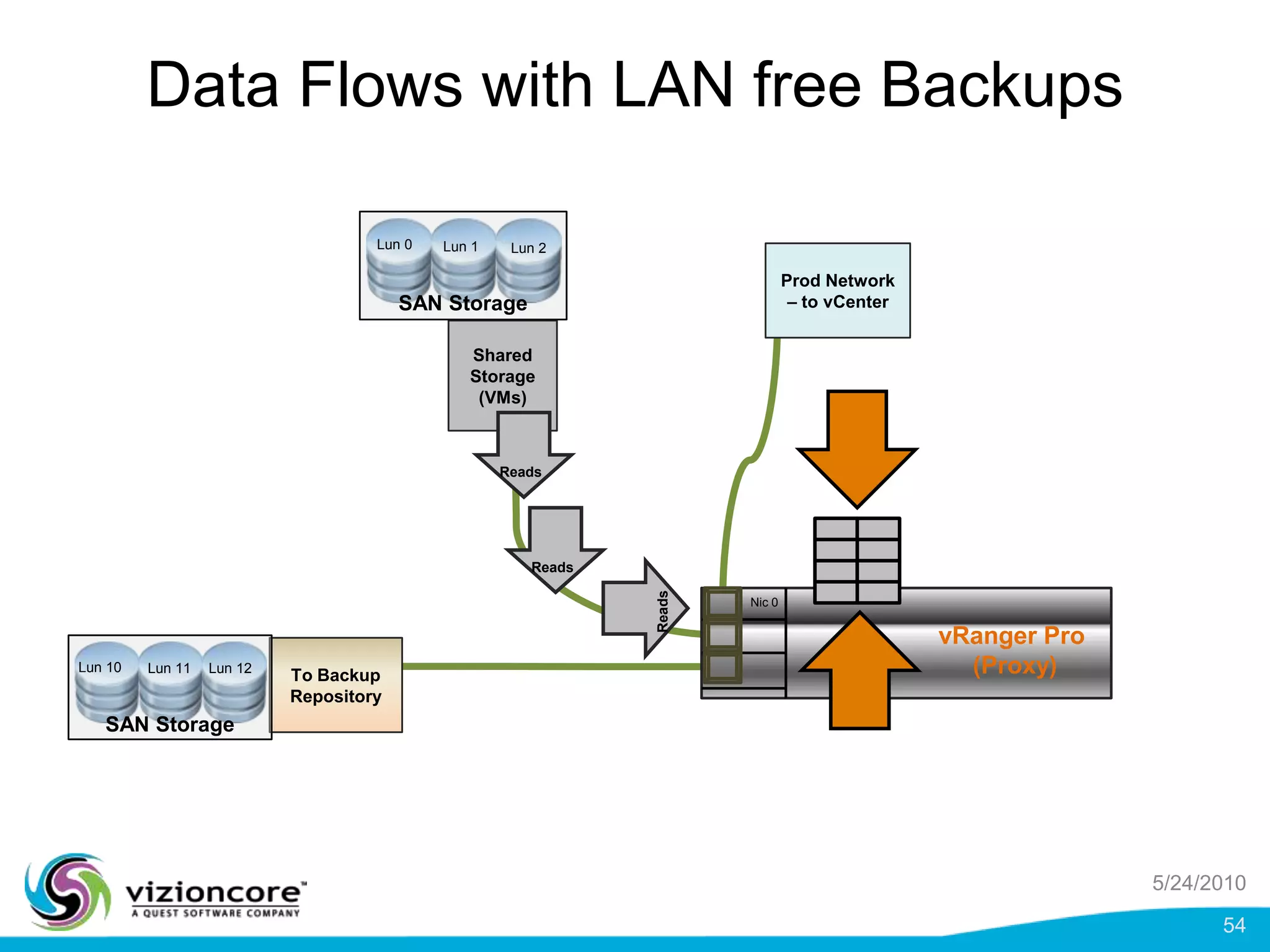
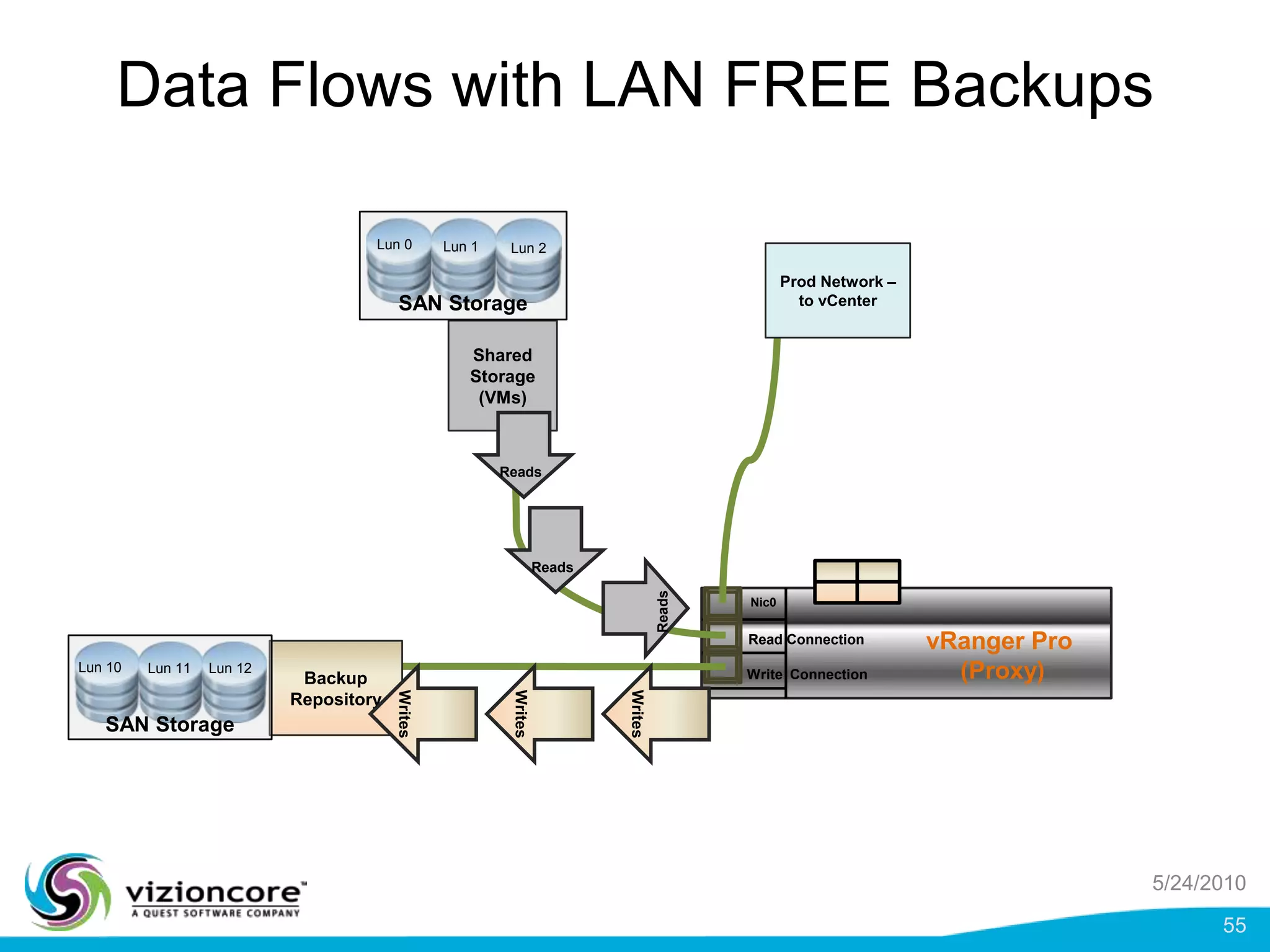
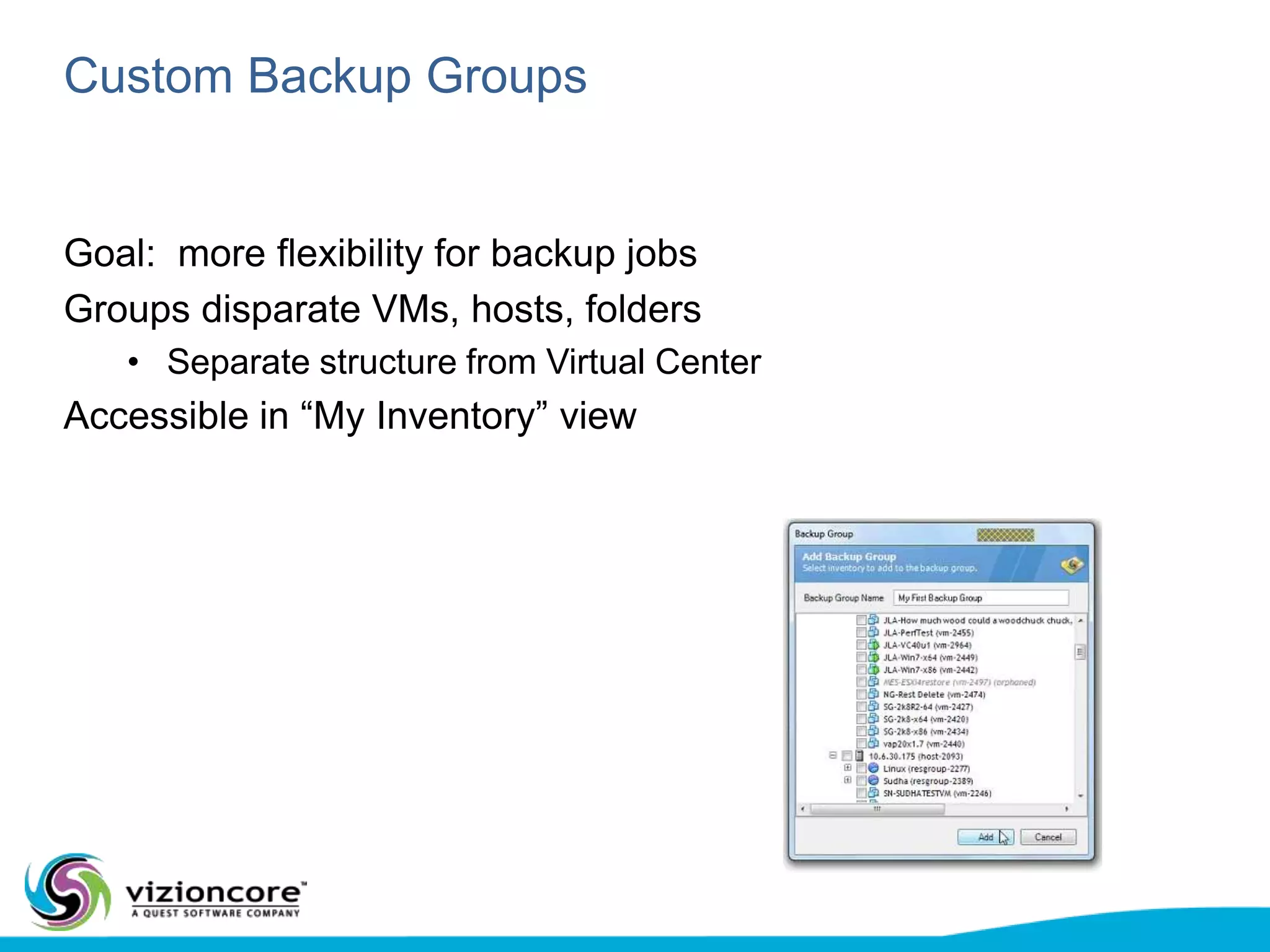
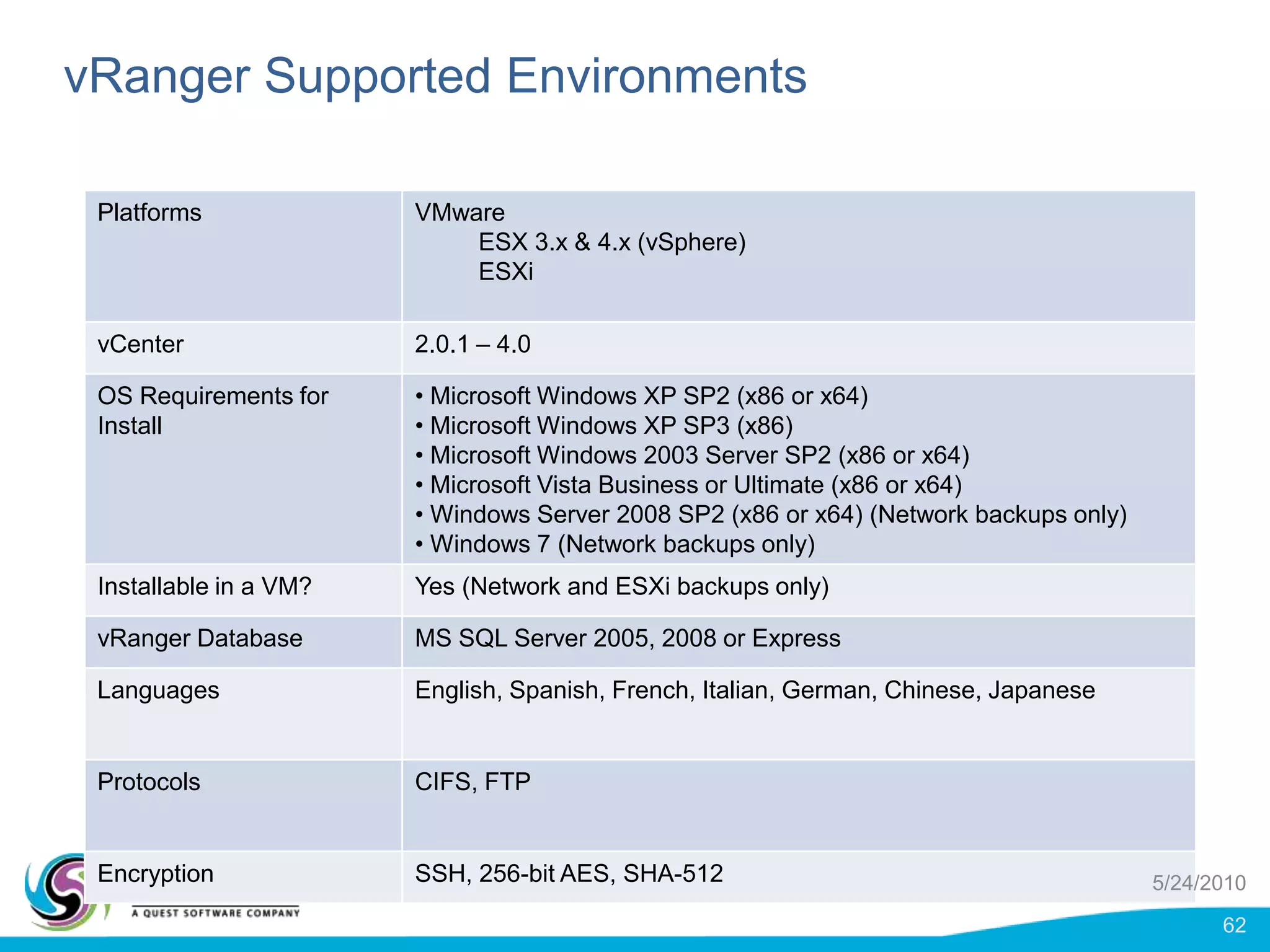
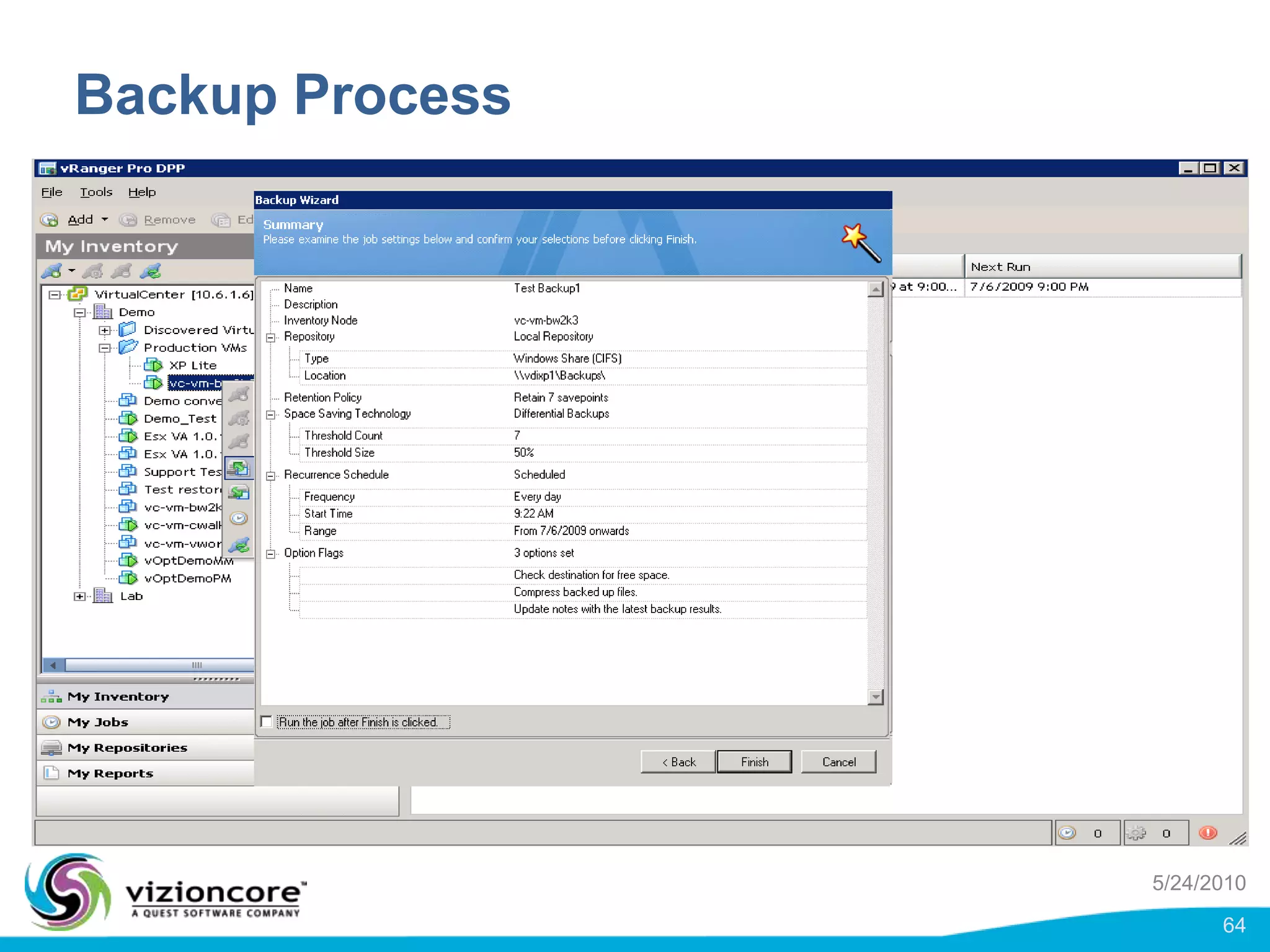
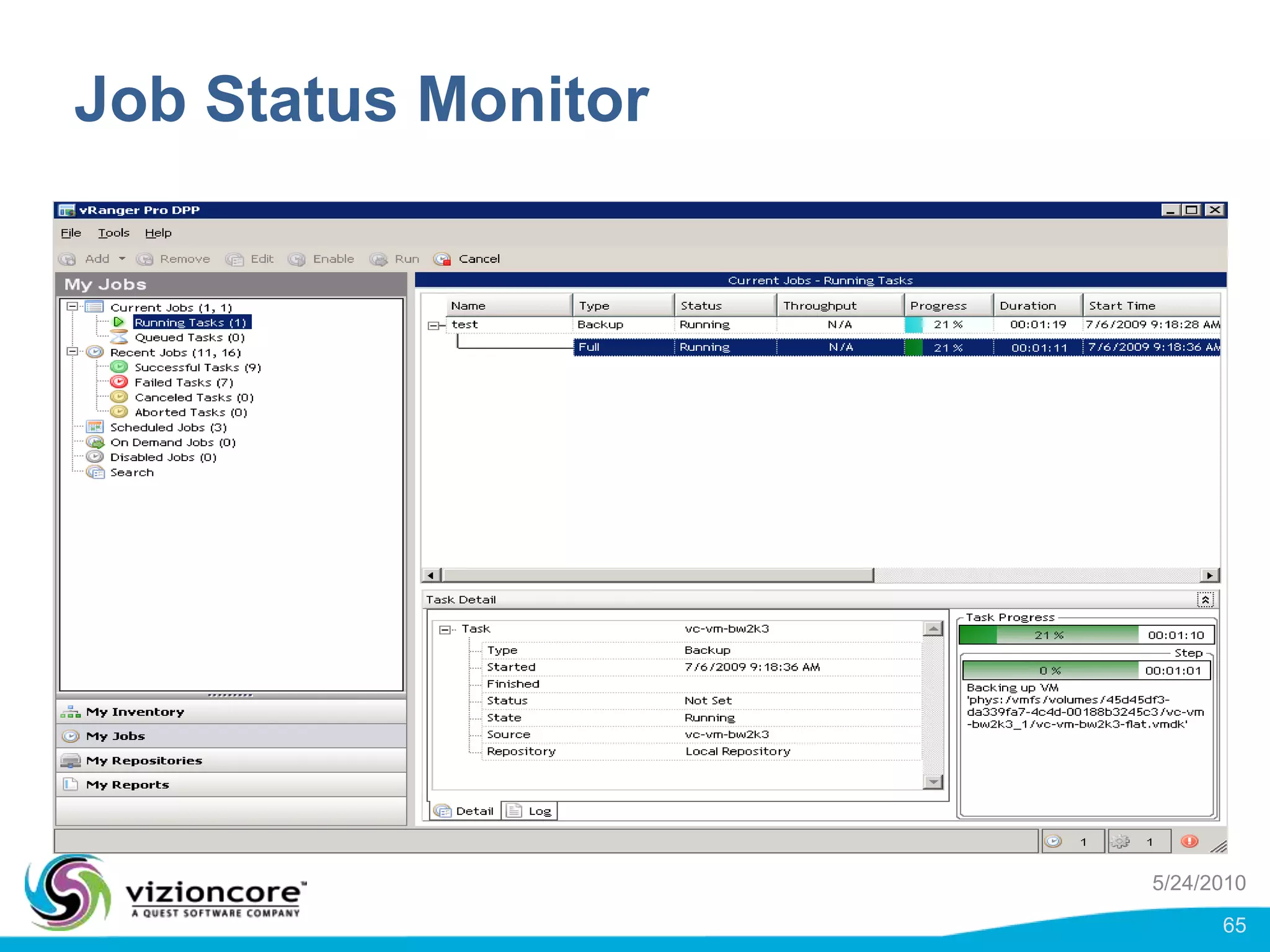
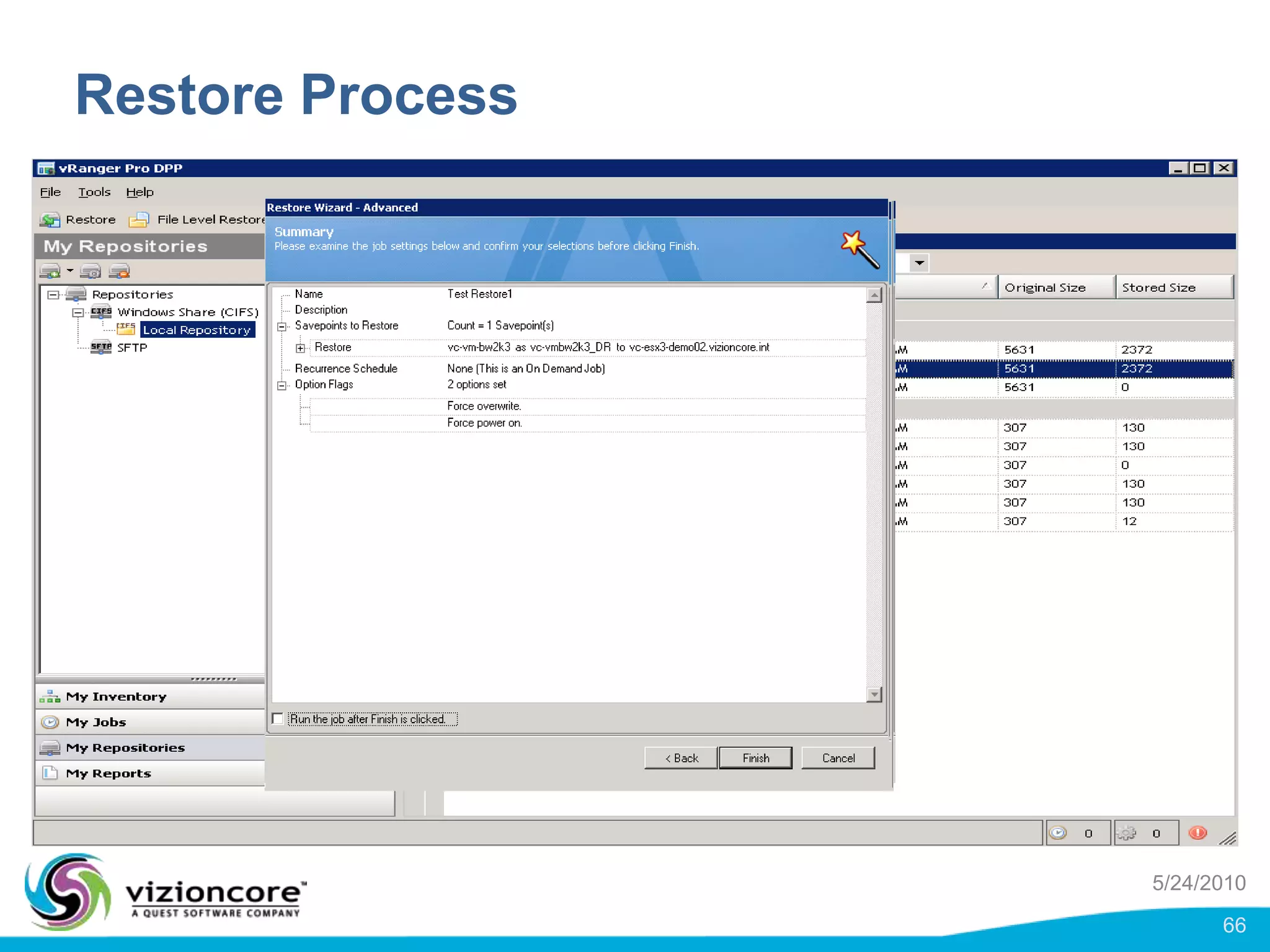
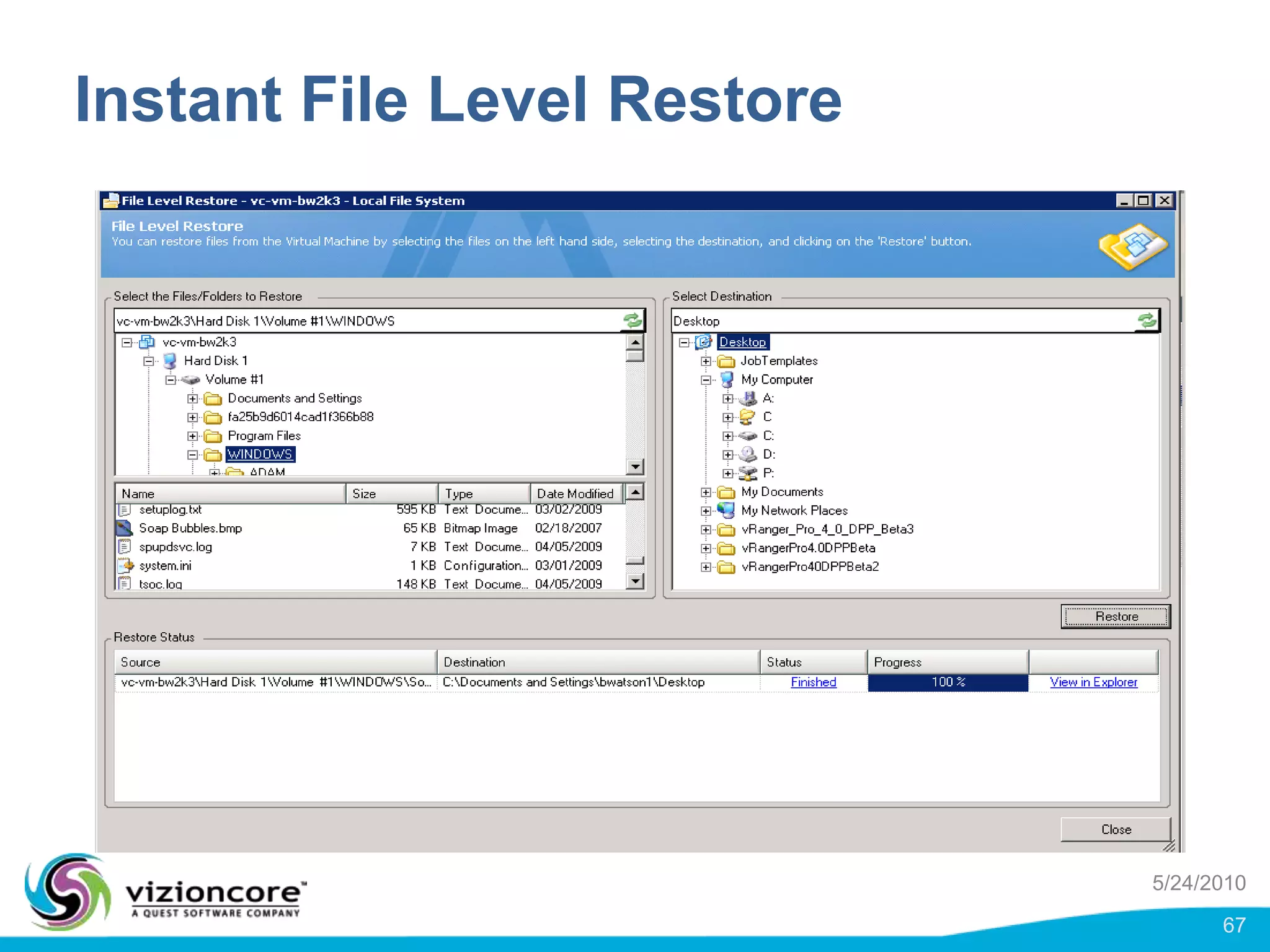
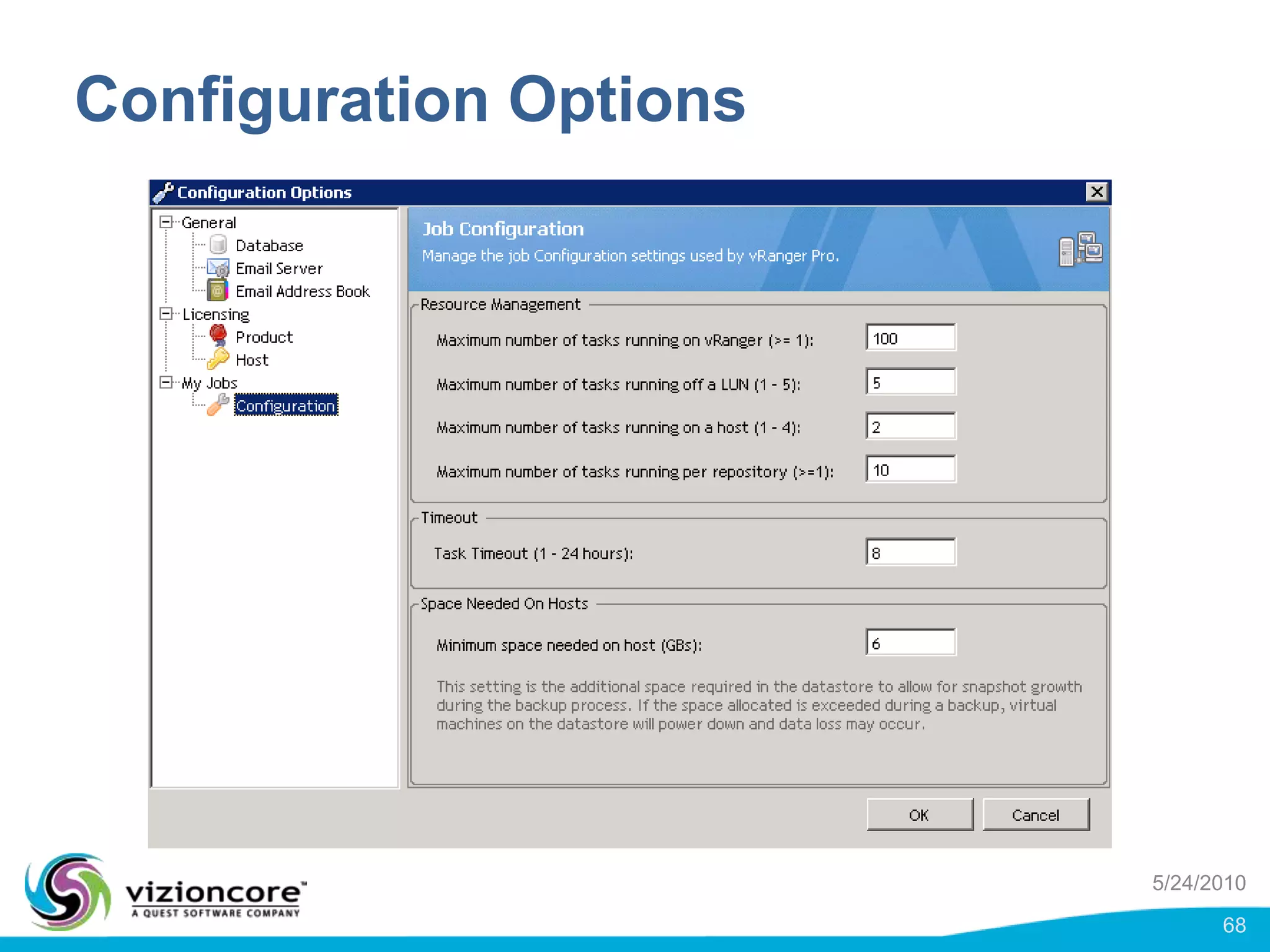
vRanger provides image-based backup and recovery of virtual machines using VMware snapshots. It creates an image of the entire virtual machine, including the operating system, applications, and data. This image can then be restored on any system running the correct hypervisor. vRanger backups are fast because it leverages snapshot technology instead of copying files. It also supports deduplication, compression, and encryption of backups. Restores can be done at the image, file, or object level and images can be restored on-premises or to the cloud.