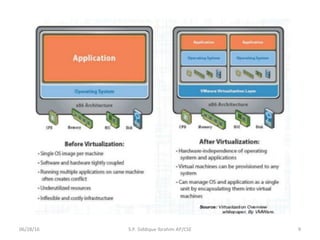
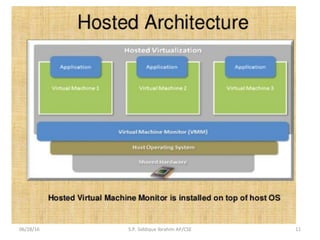
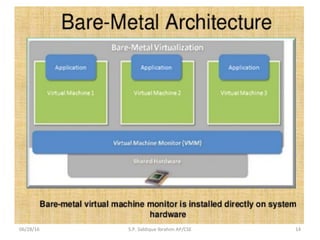
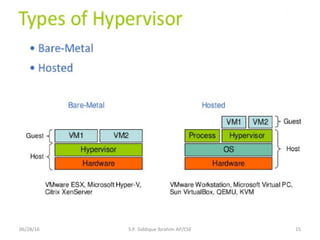
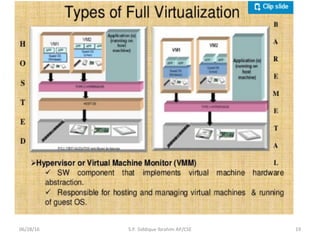
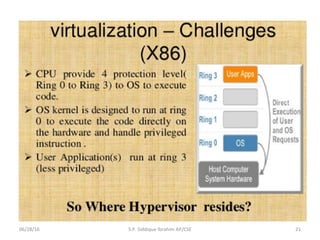
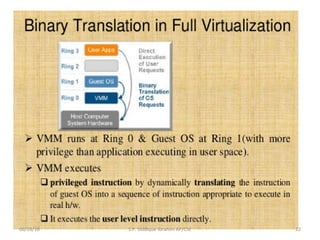
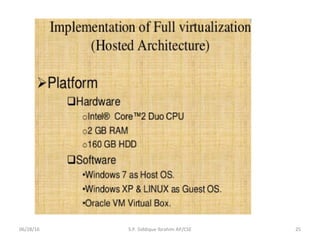
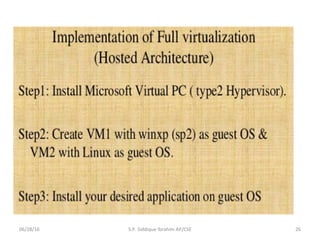
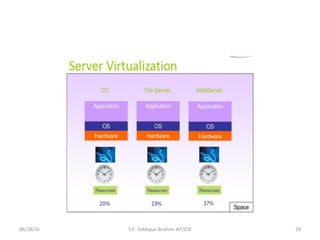
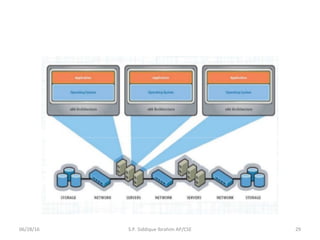
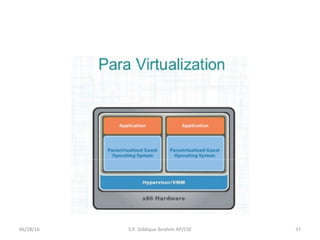
The document discusses virtualization concepts written by S.P. Siddique Ibrahim of Kumaraguru College of Technology. It describes para-virtualization where the guest operating system is recompiled before installation to act as an interface for the hardware, which somewhat increases performance by minimizing overhead compared to other virtualization methods.