Embed presentation
Download as PDF, PPTX








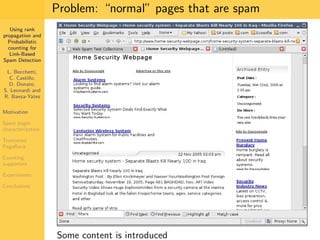


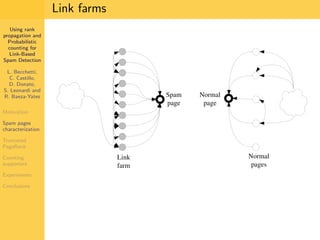
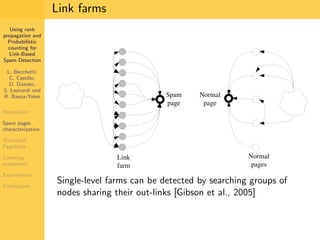


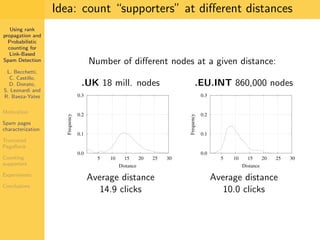
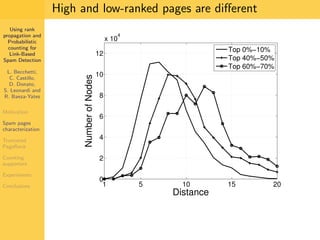
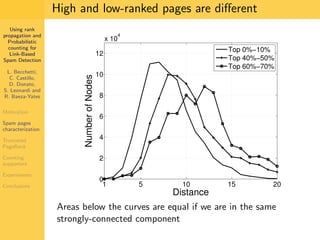


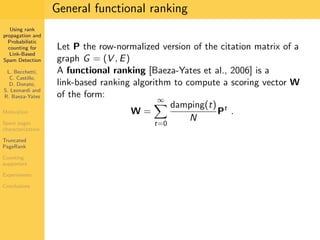

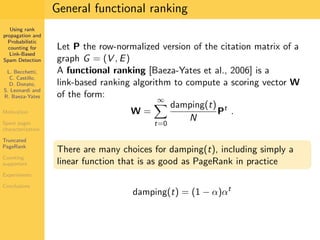
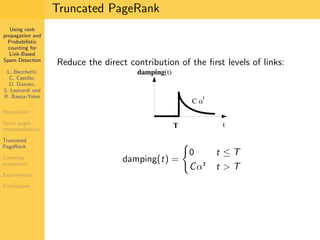
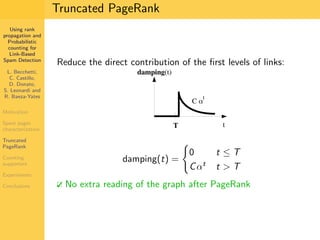


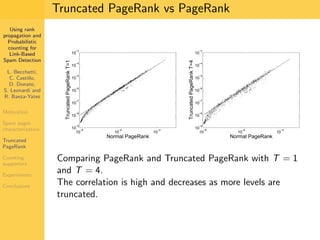

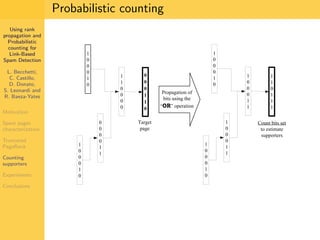

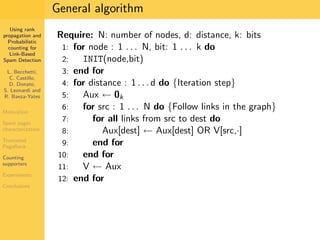
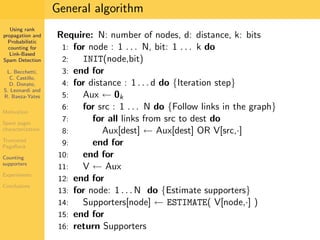

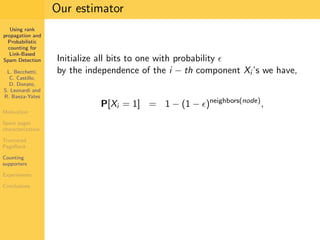
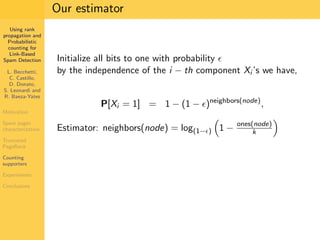



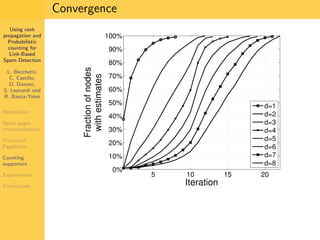
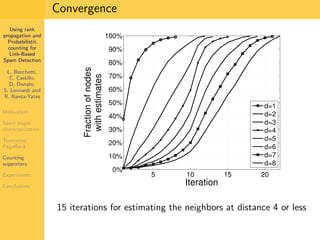
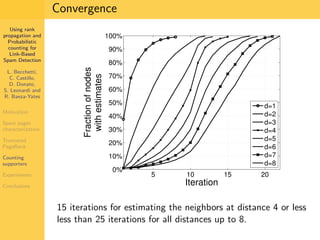
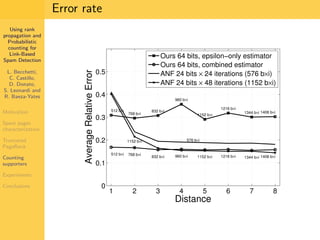





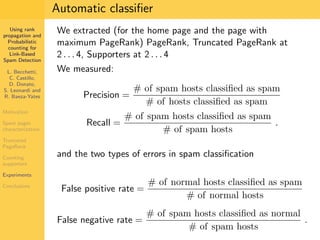
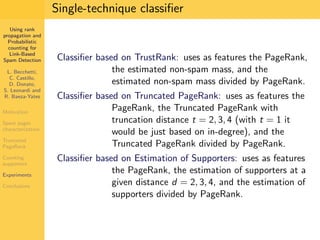
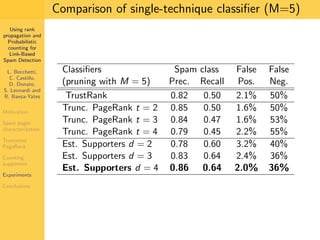
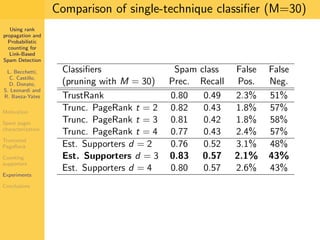
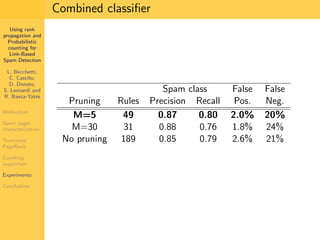

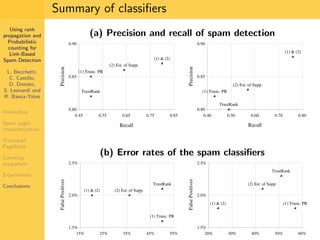
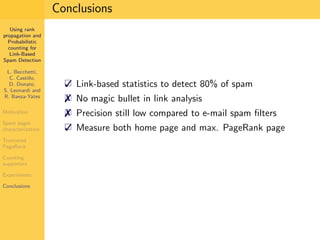
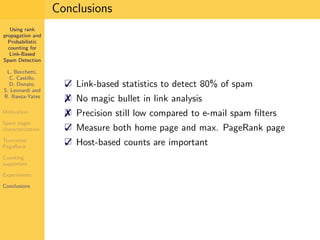
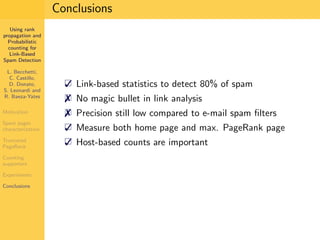
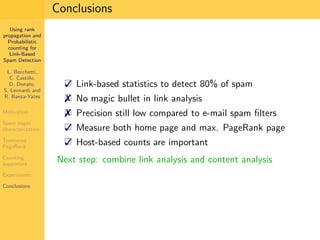






1. The document discusses techniques for detecting link-based spam using rank propagation and probabilistic counting. 2. It aims to characterize spam pages and analyze the distribution of statistics about pages to identify outliers associated with spam. 3. The key techniques involve counting the number of "supporters" or pages linking to a target page at different distances from that page.









































































