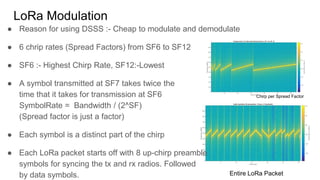
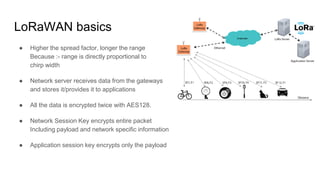
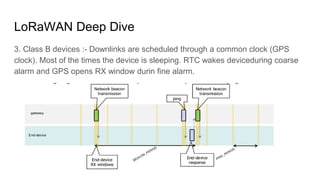
The document discusses LoRa modulation and LoRaWAN for low bandwidth communication in sensors. It describes how LoRa uses chirp spread spectrum modulation to achieve long range communication. It then explains key aspects of LoRaWAN including the classes of devices, activation methods, and encryption of data between devices, gateways and servers.