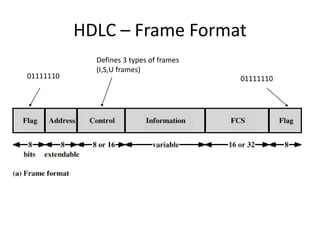
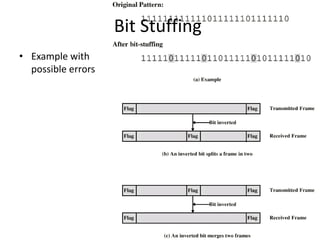
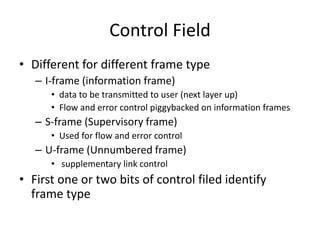
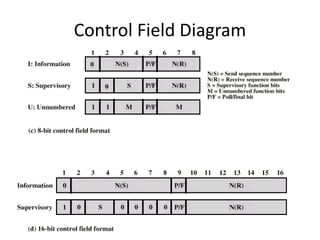
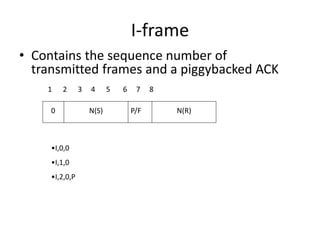
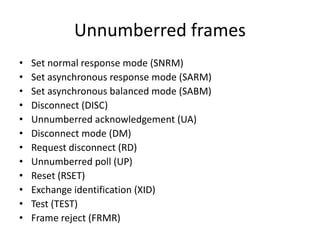
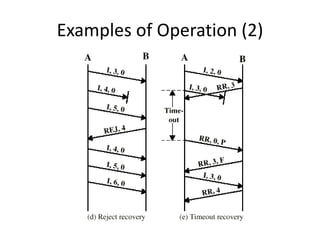
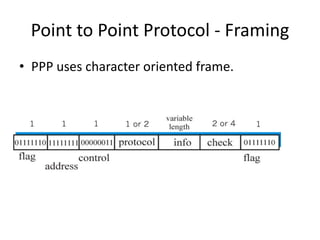
HDLC is a bit-oriented data link protocol that supports half-duplex and full-duplex communication over point-to-point and multi-point links. It defines three station types (primary, secondary, combined), three configurations (unbalanced, symmetric, balanced), and three response modes (NRM, ARM, ABM). HDLC uses a flag sequence, control field, optional information field, frame check sequence, and flag sequence to format frames. PPP is a common point-to-point protocol that uses character-oriented framing and establishes links through negotiation phases before allowing data transfer in the open state.