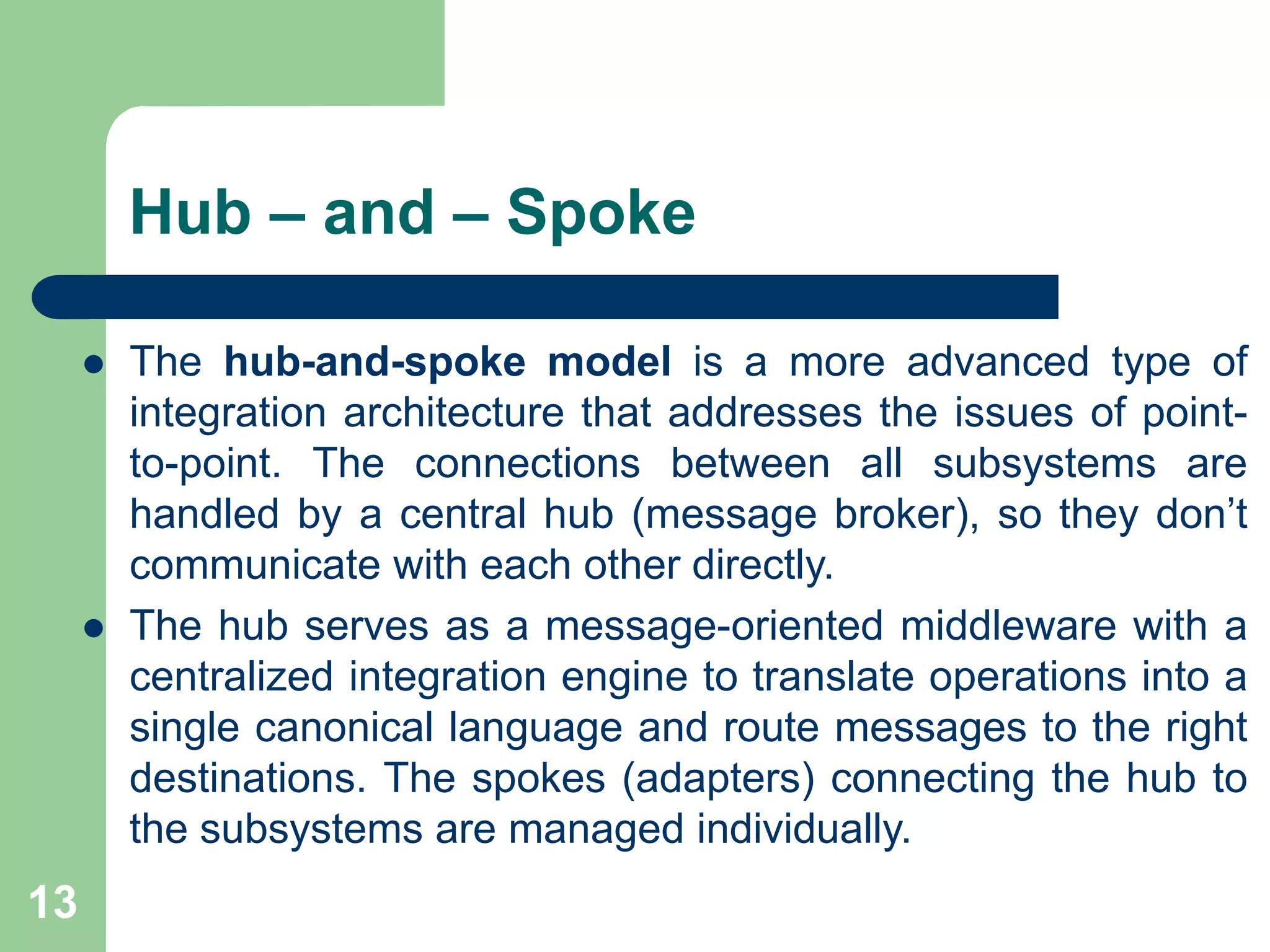
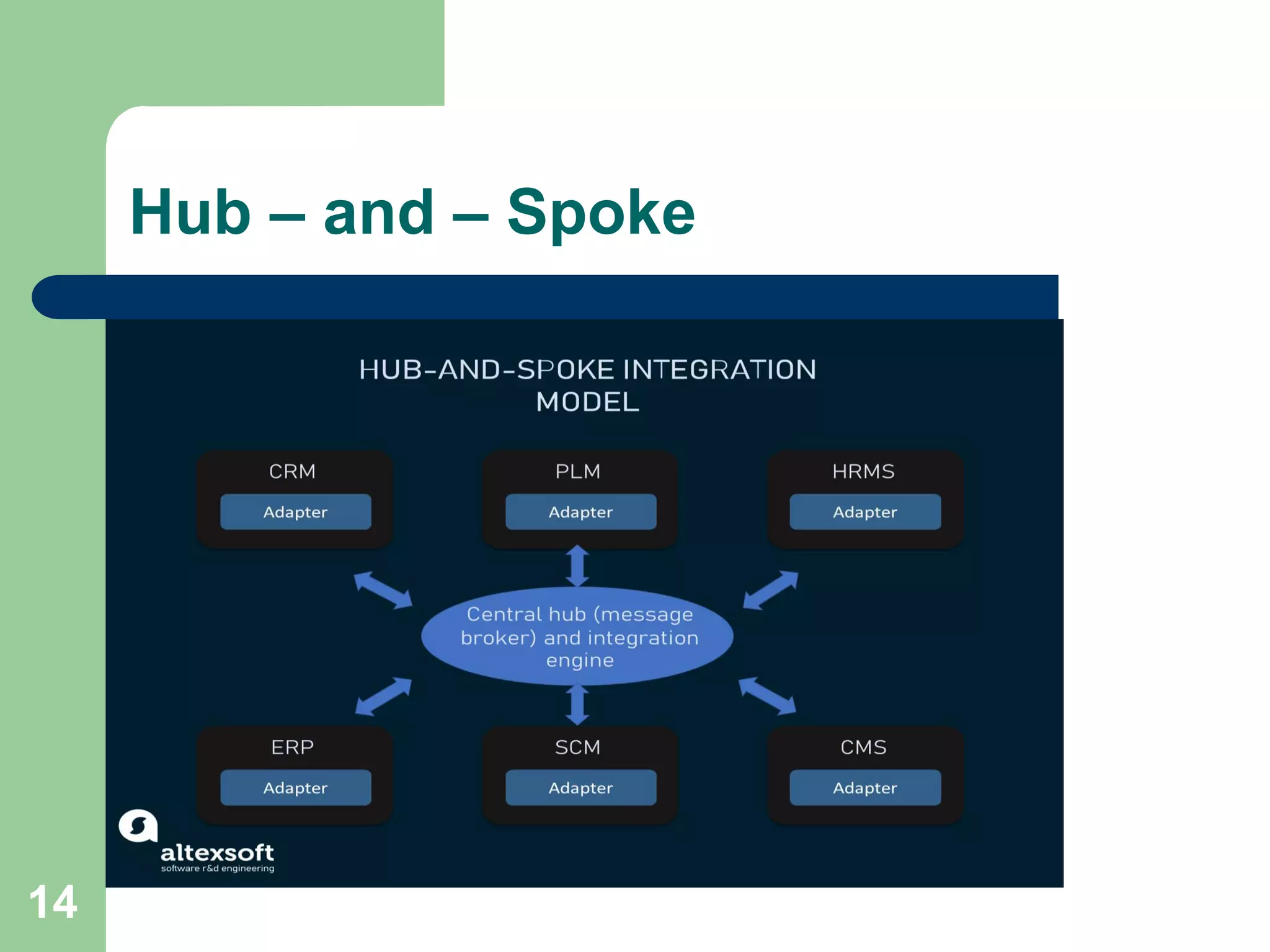
1. There are several integration topologies that can be used depending on the number and nature of components that need to be connected, including point-to-point connection, broker, message bus, and publish/subscribe.
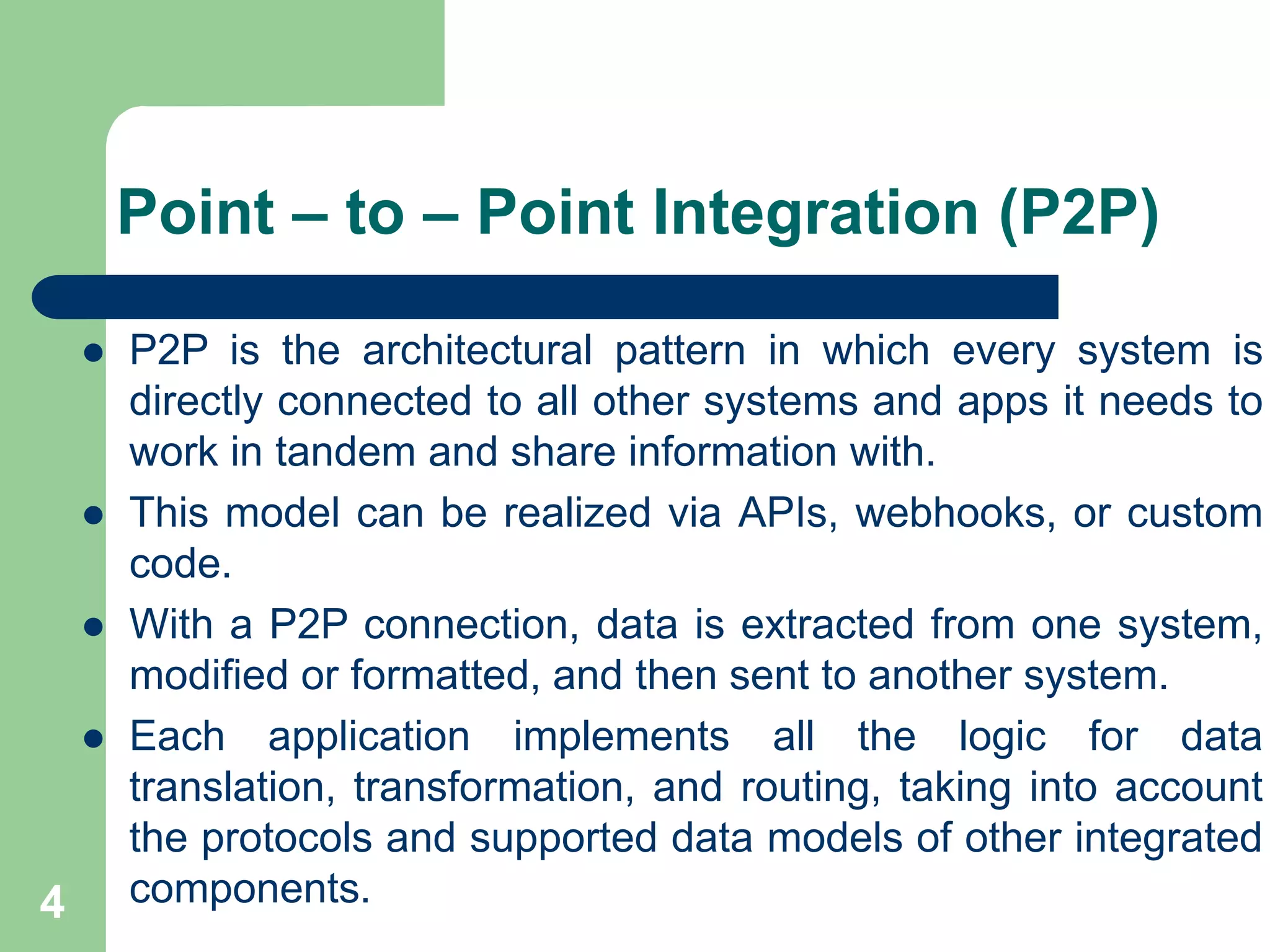
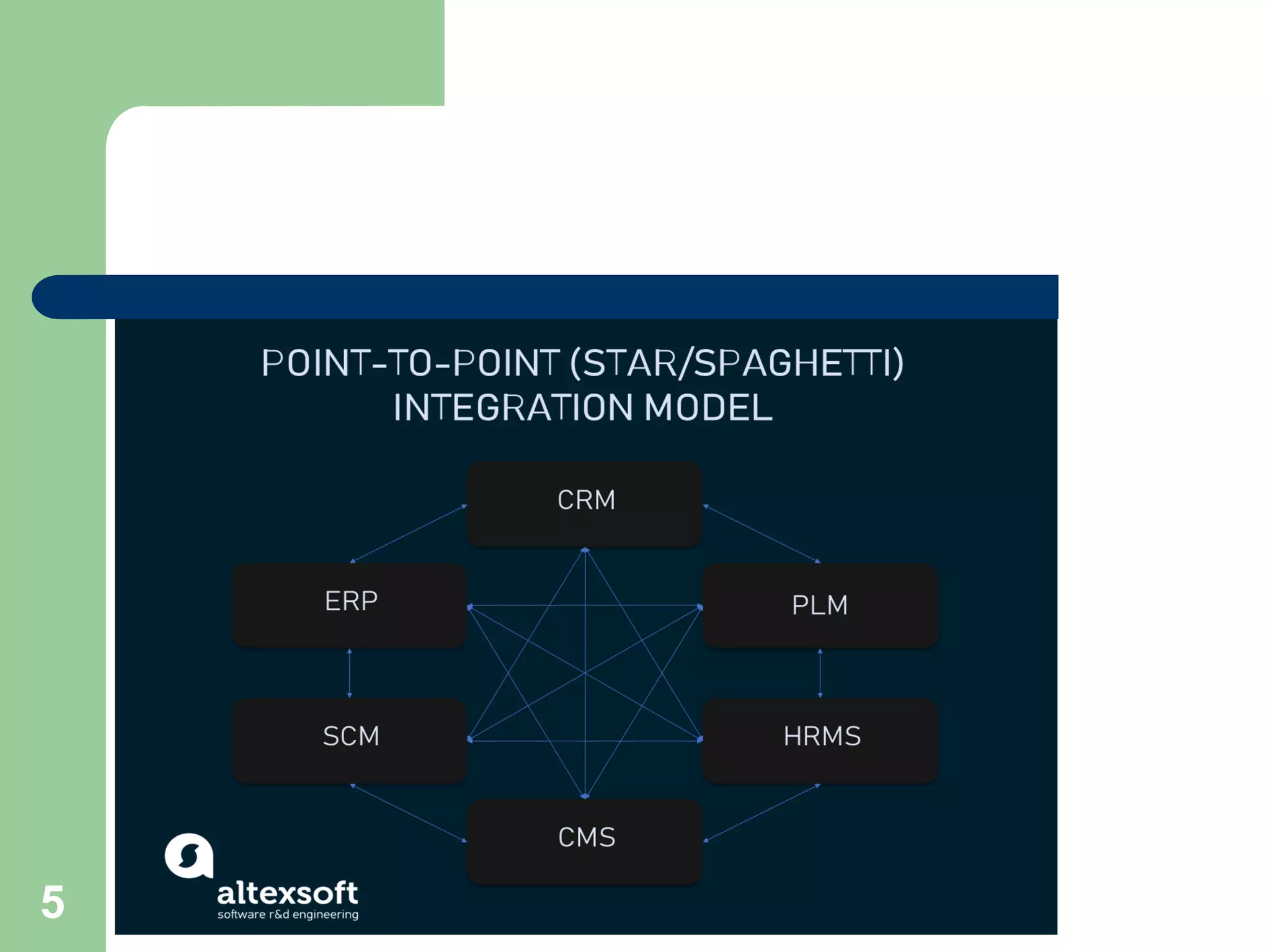
2. A point-to-point connection involves direct connections between all systems, requiring each system to implement logic for data translation. As the number of connections grows, this approach has high operational costs.
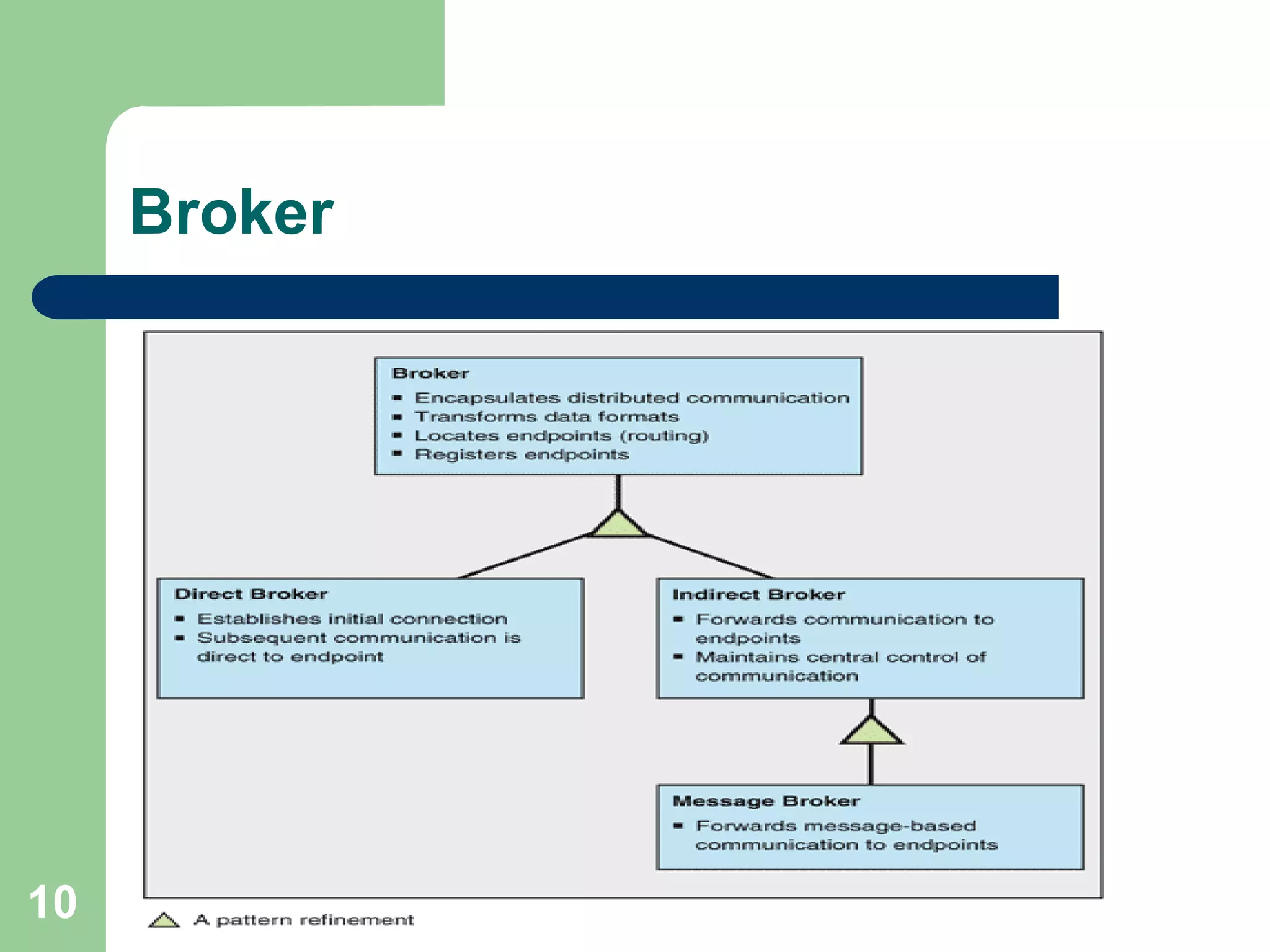
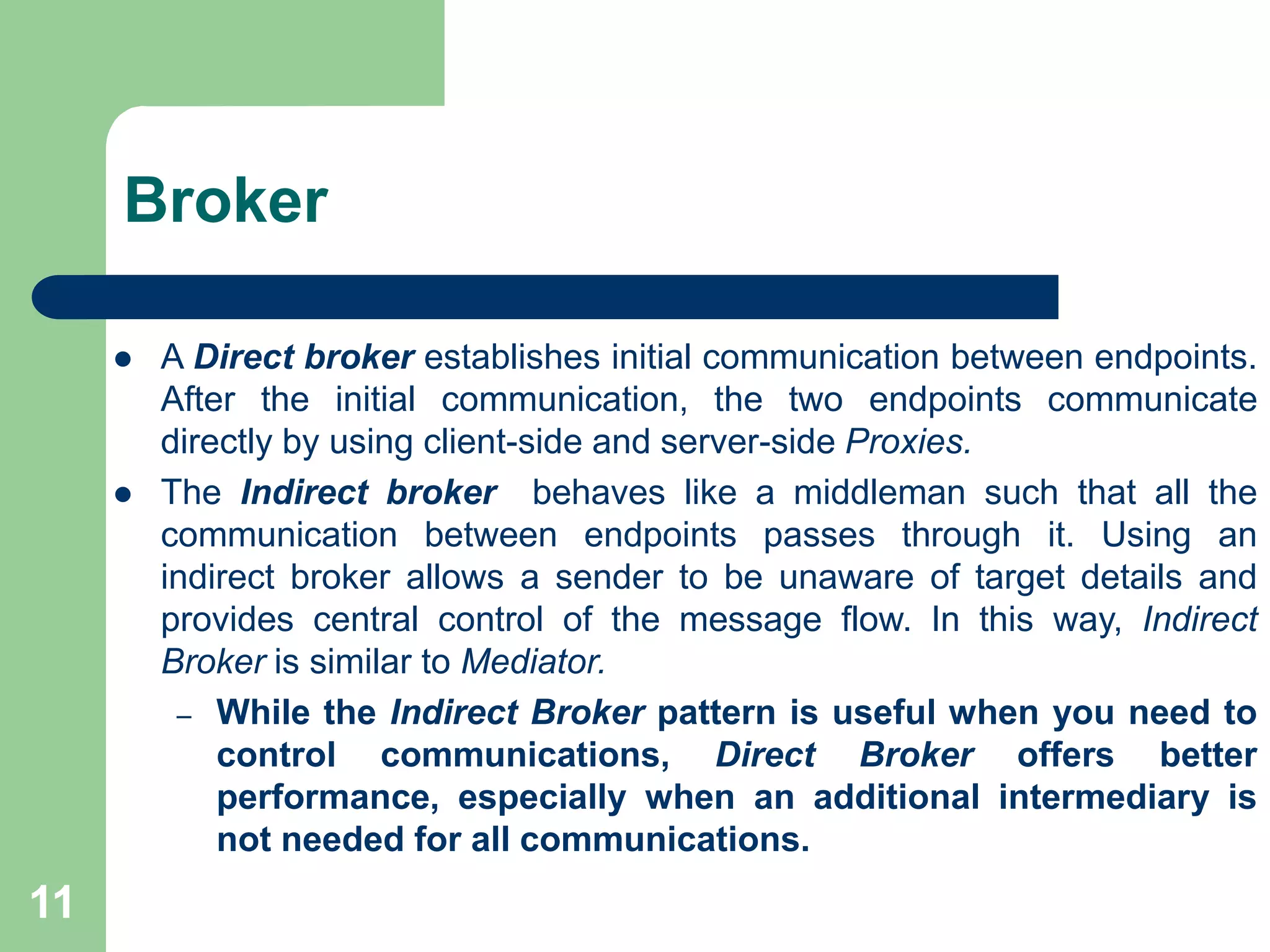
3. A broker decouples source and target systems by providing routing and transformation services. This reduces duplication and configuration costs compared to point-to-point. Common broker examples include message brokers, direct brokers, and indirect brokers.