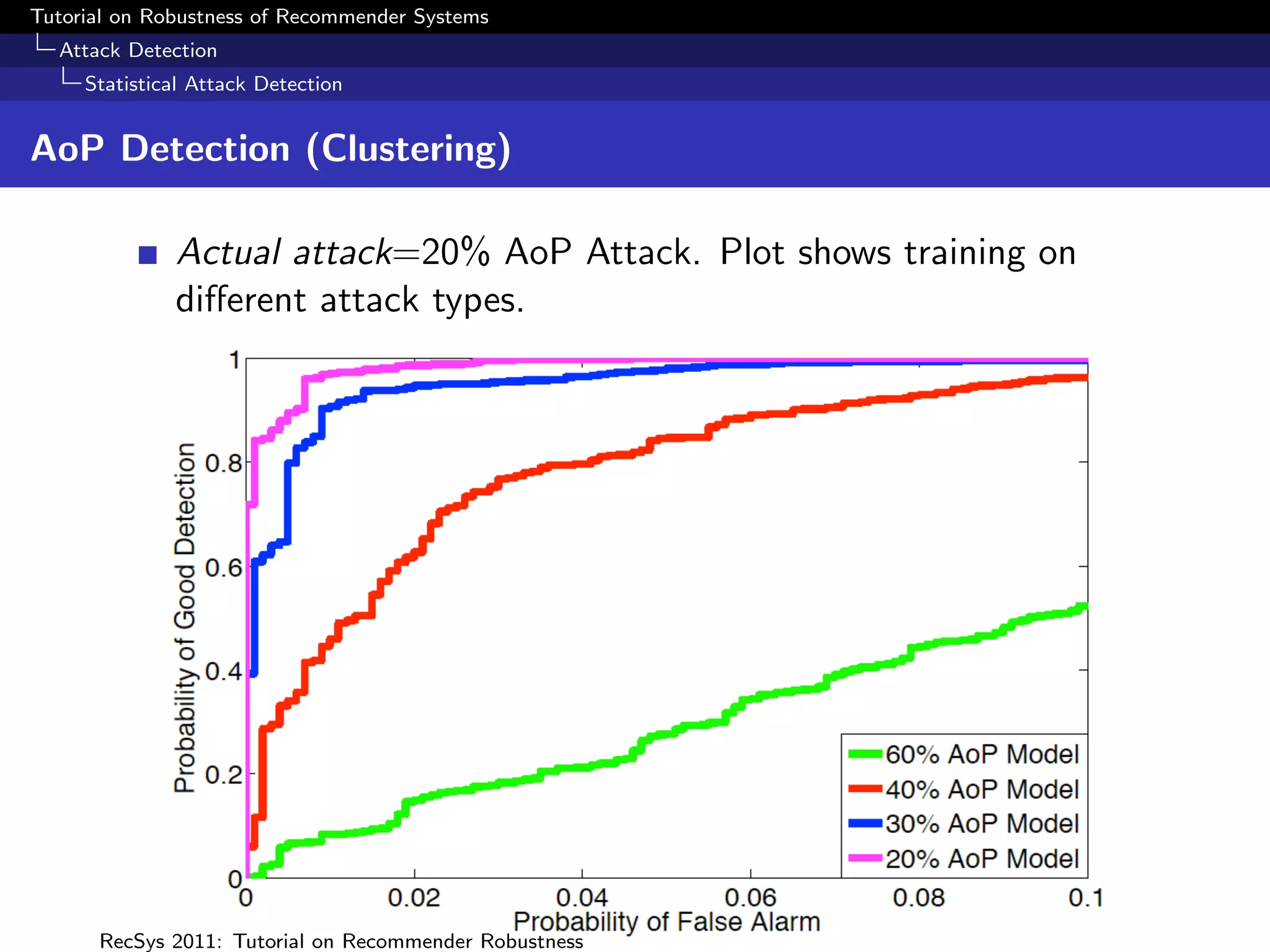
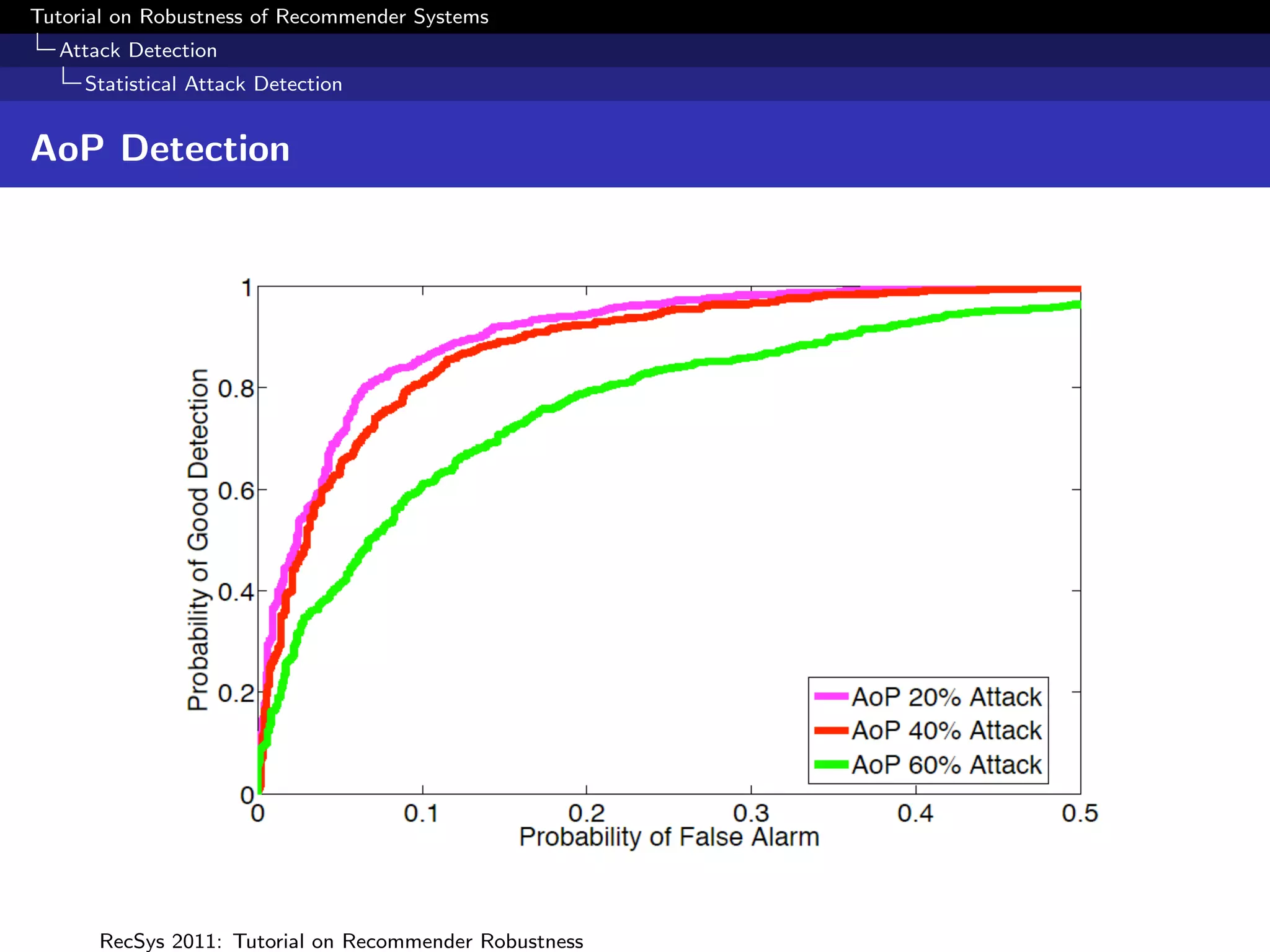
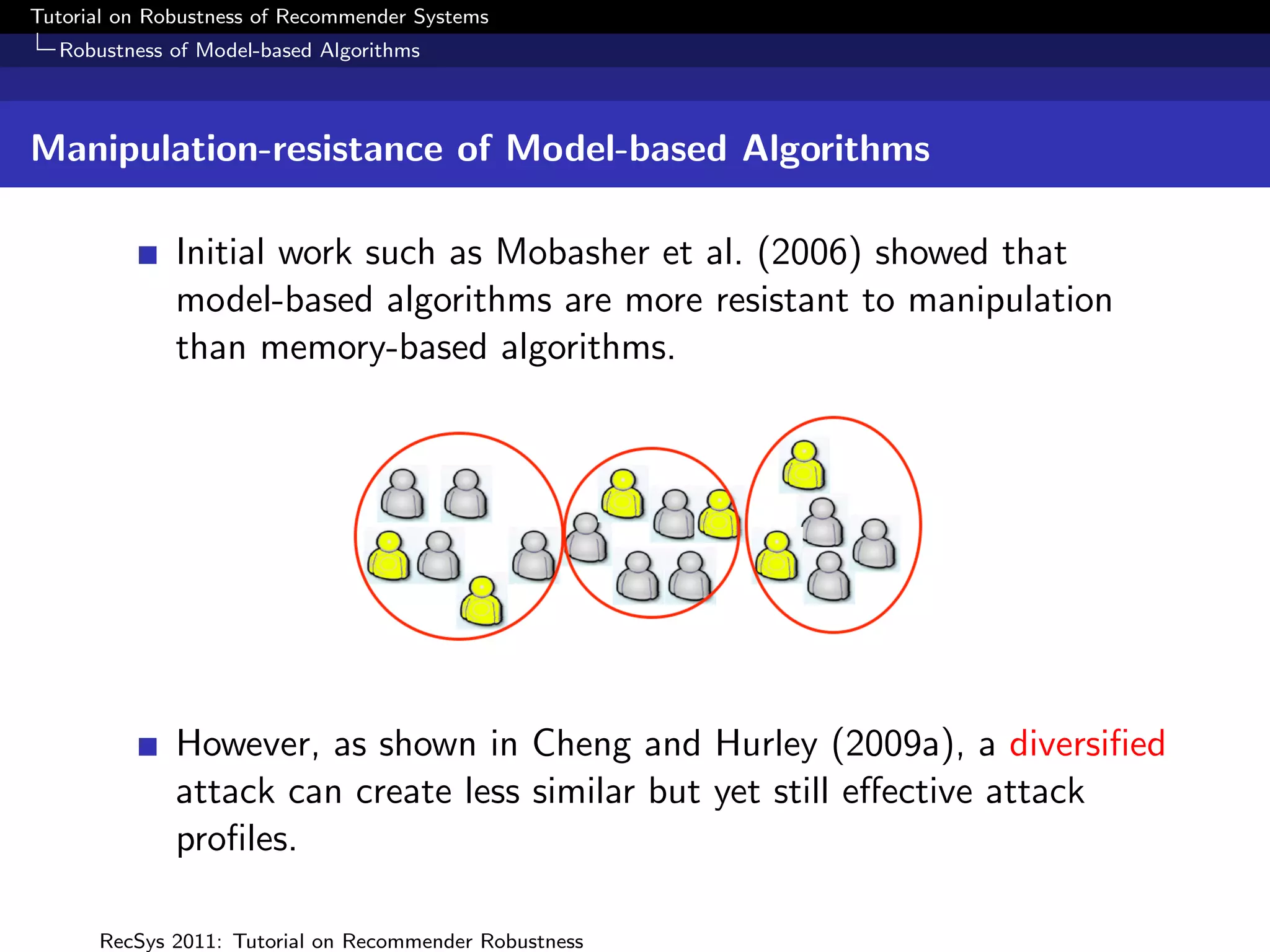
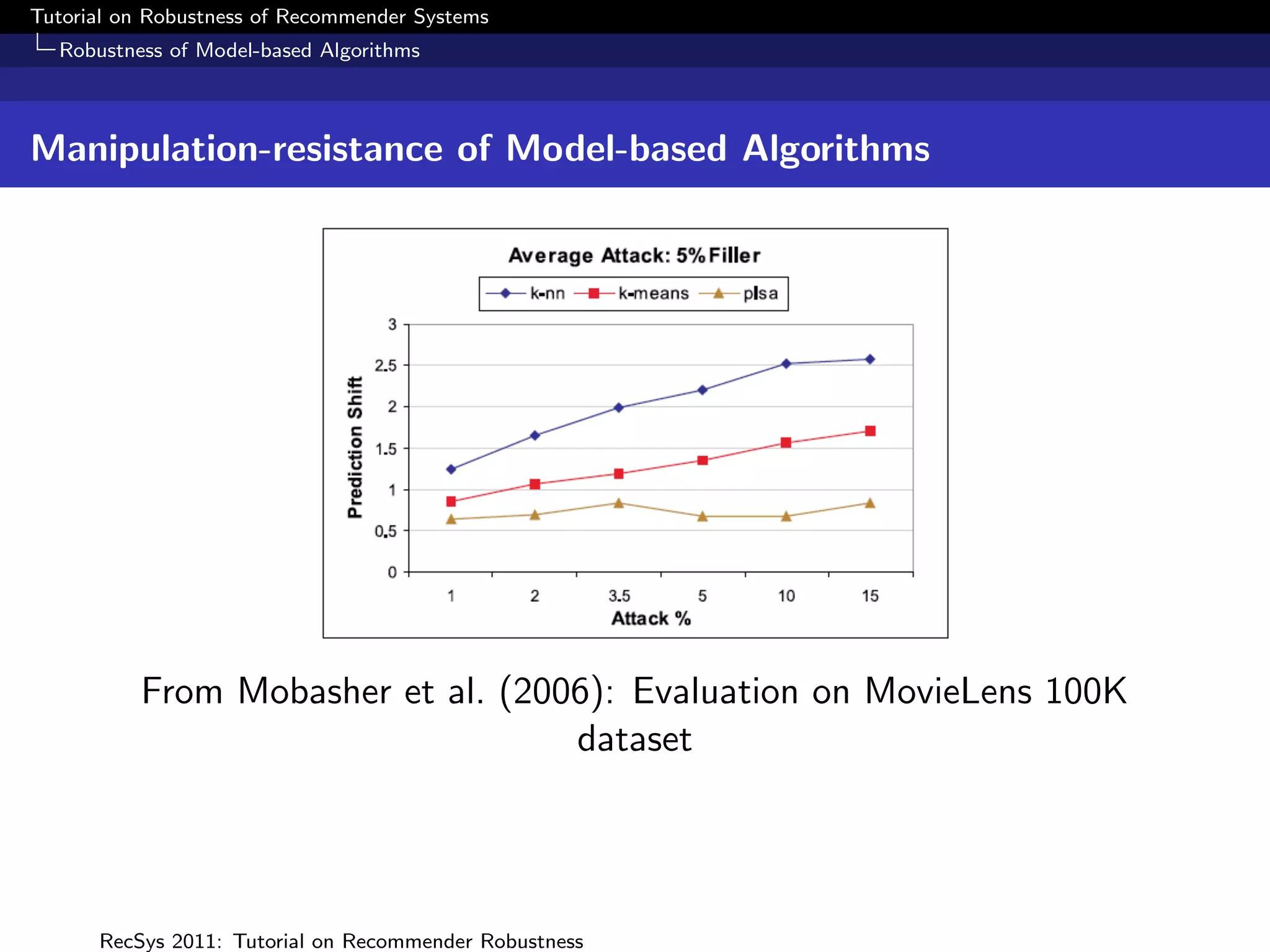
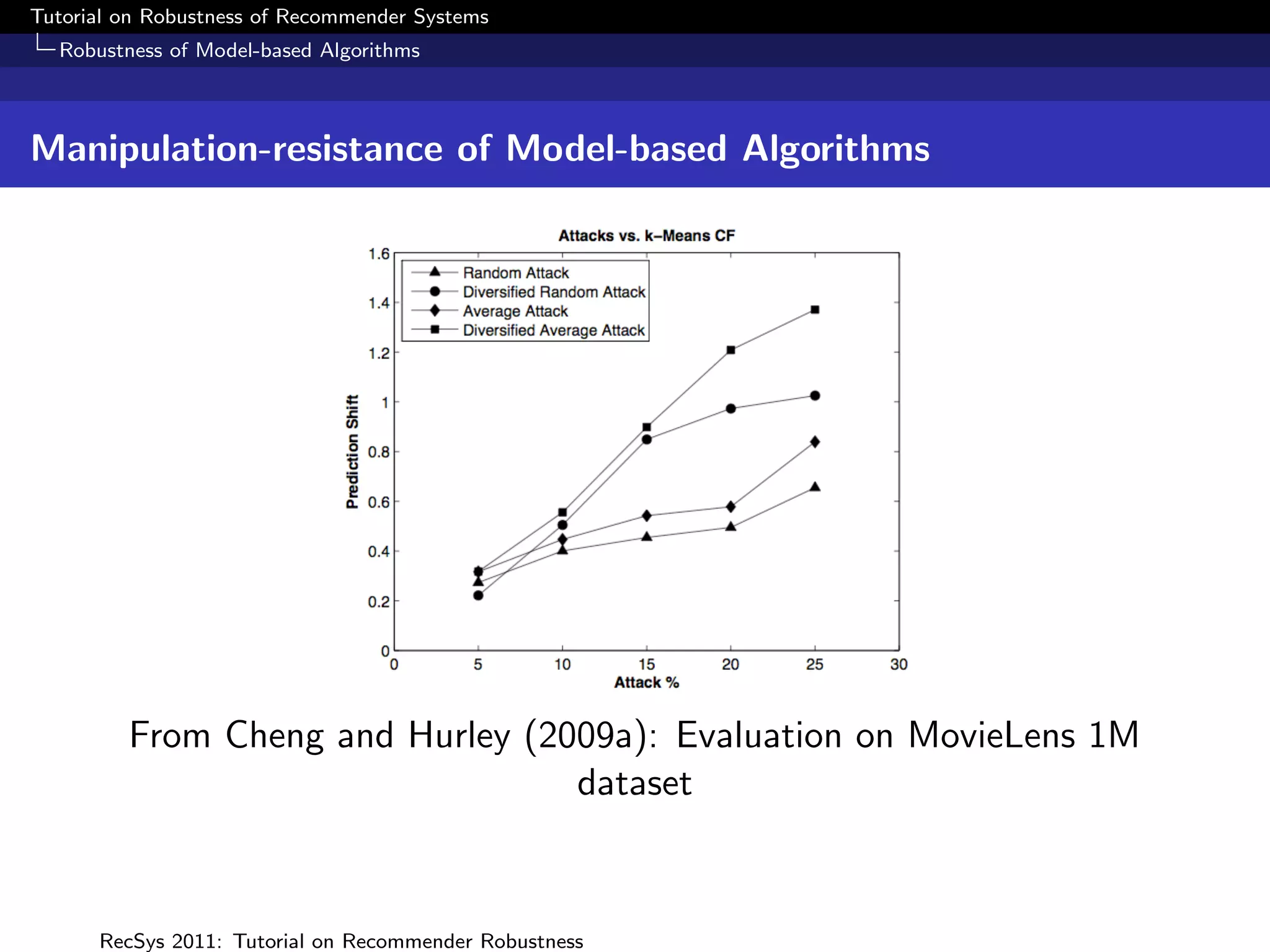
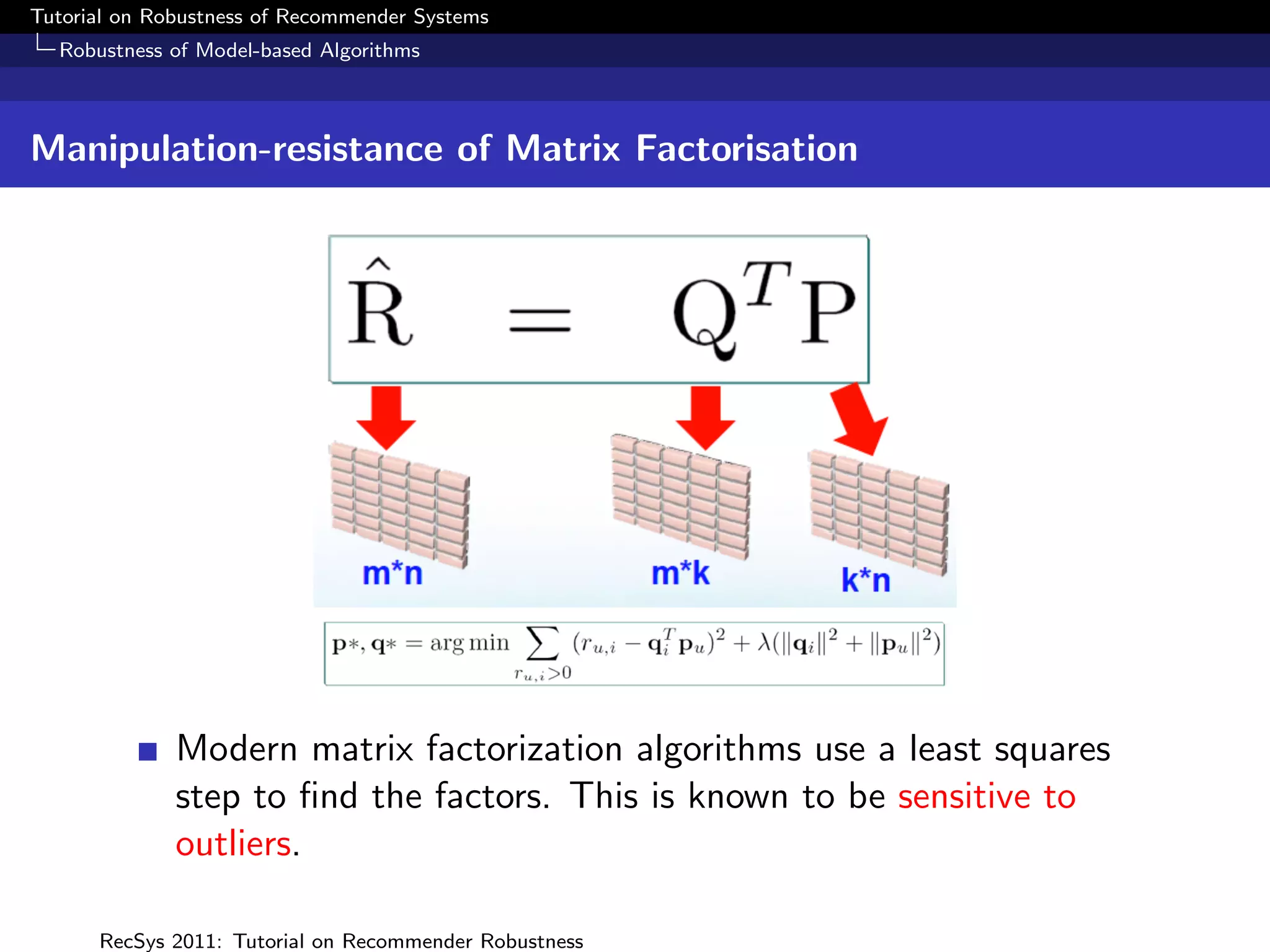
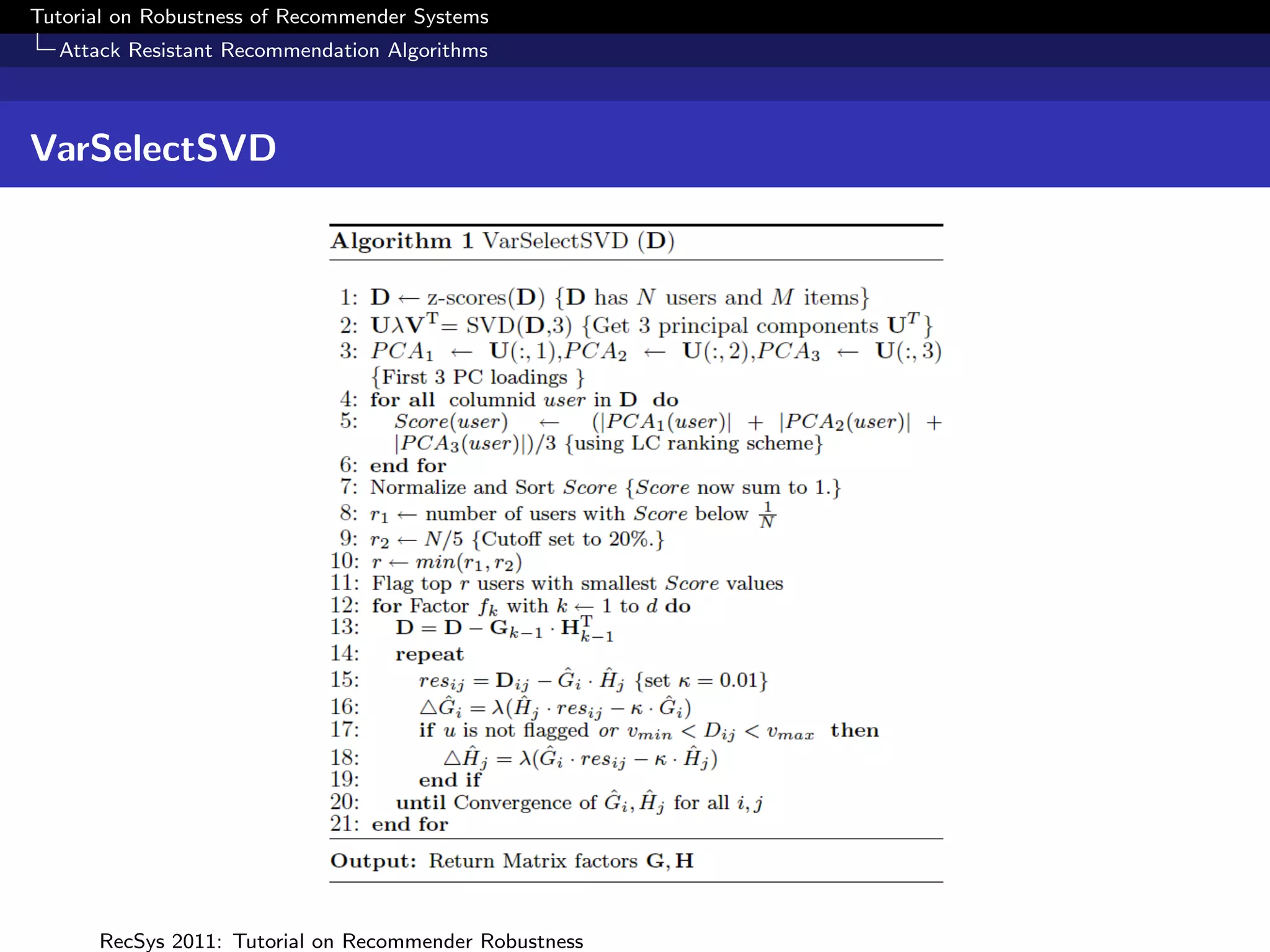
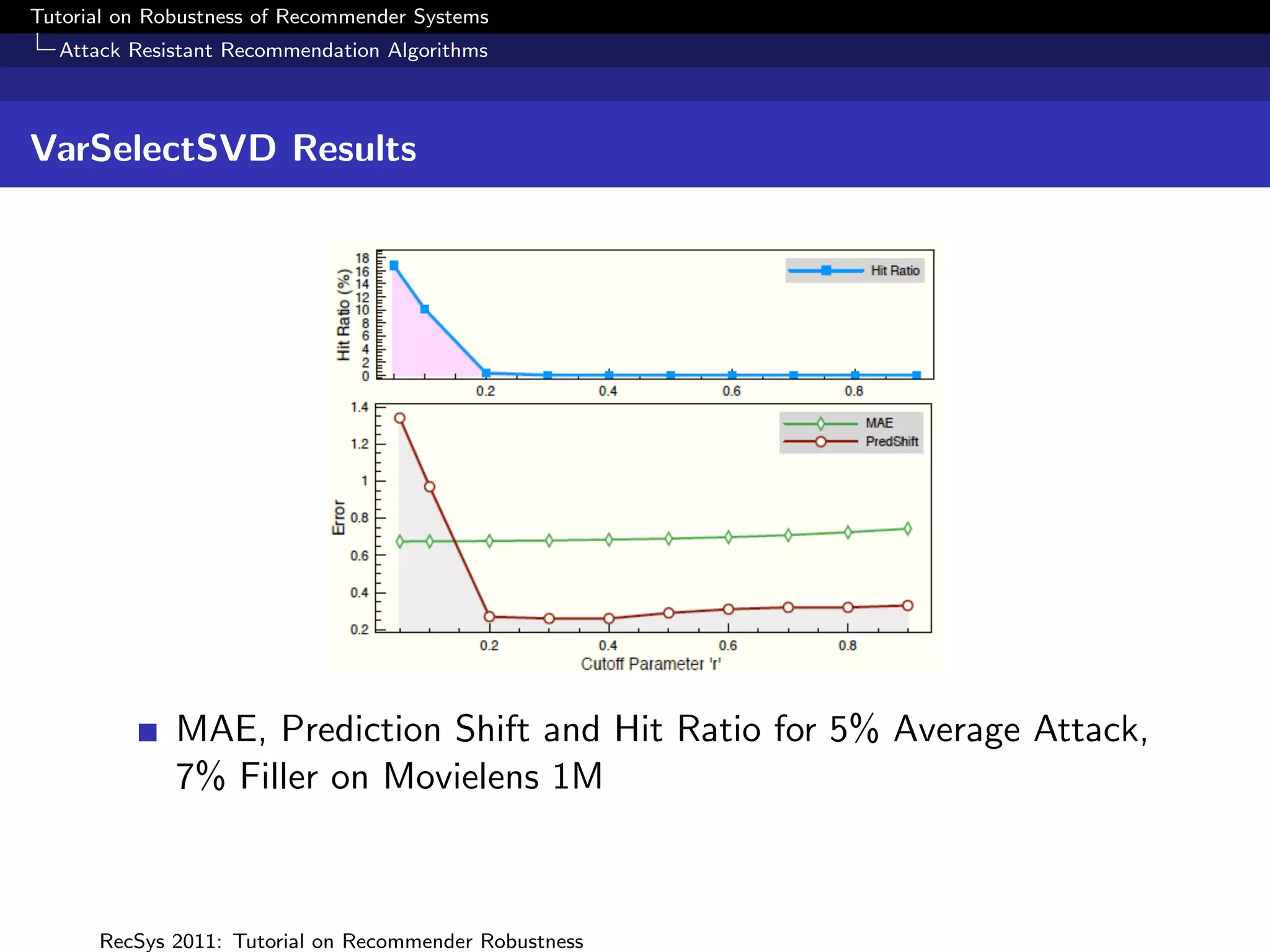
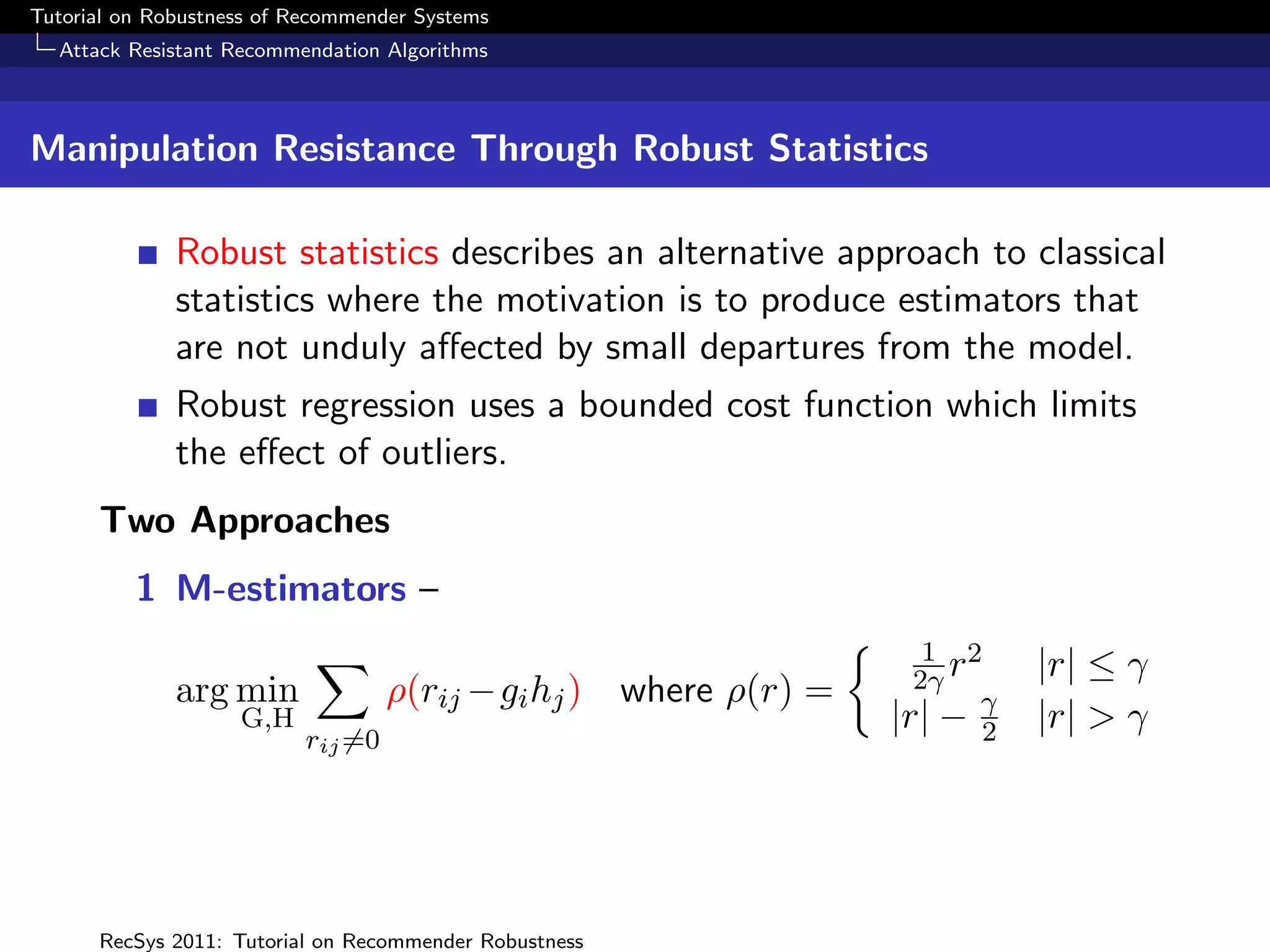
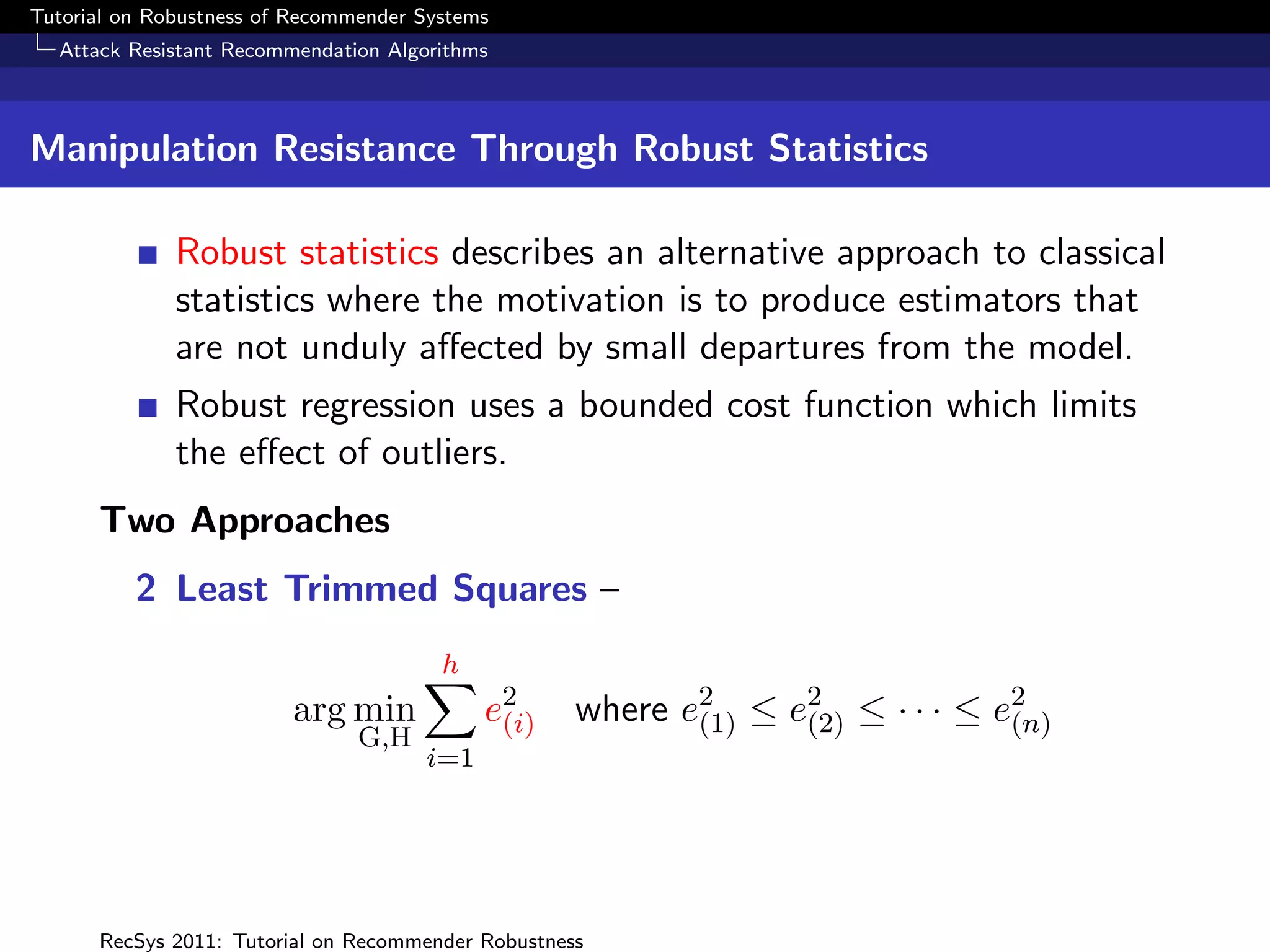
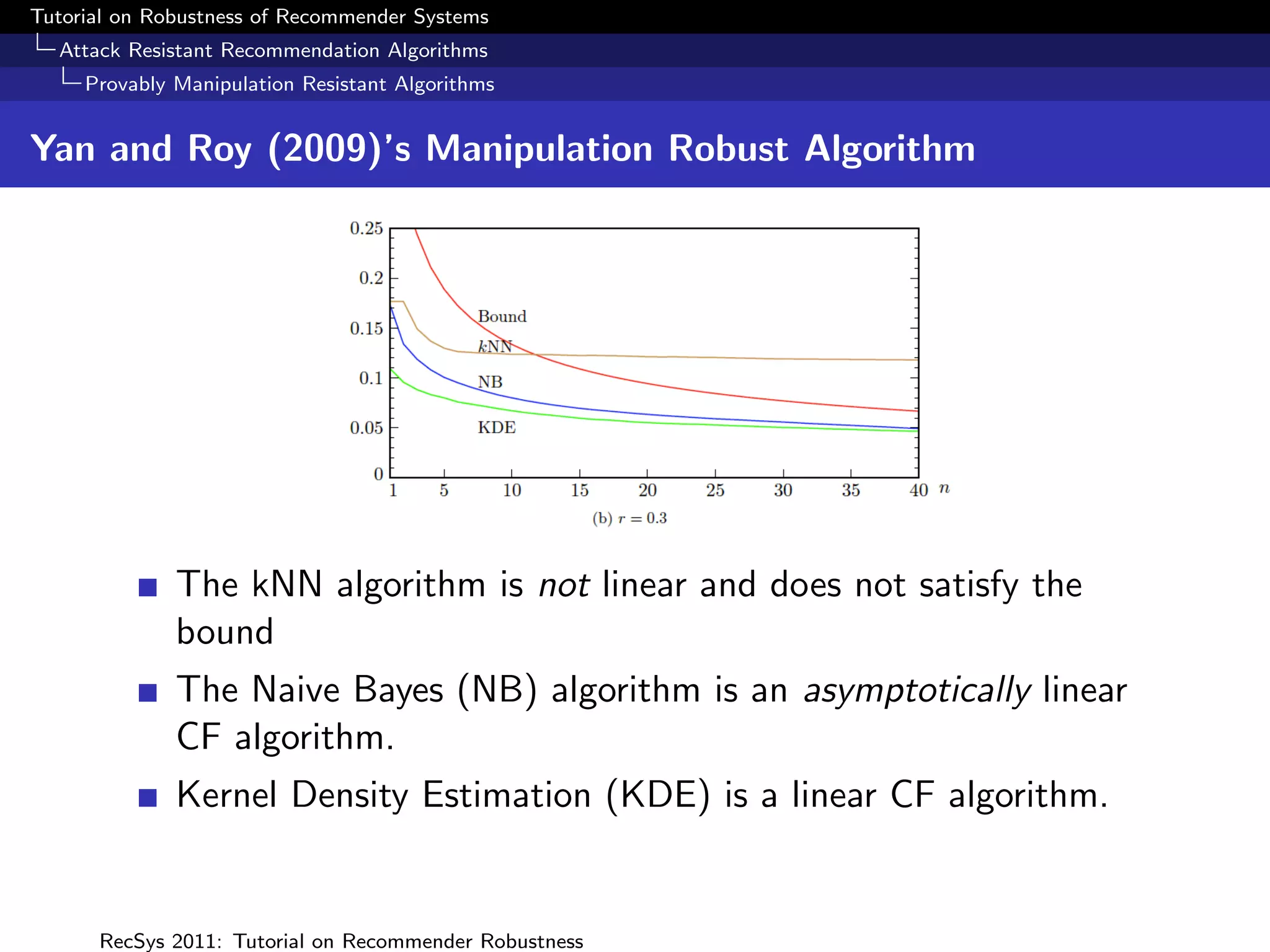
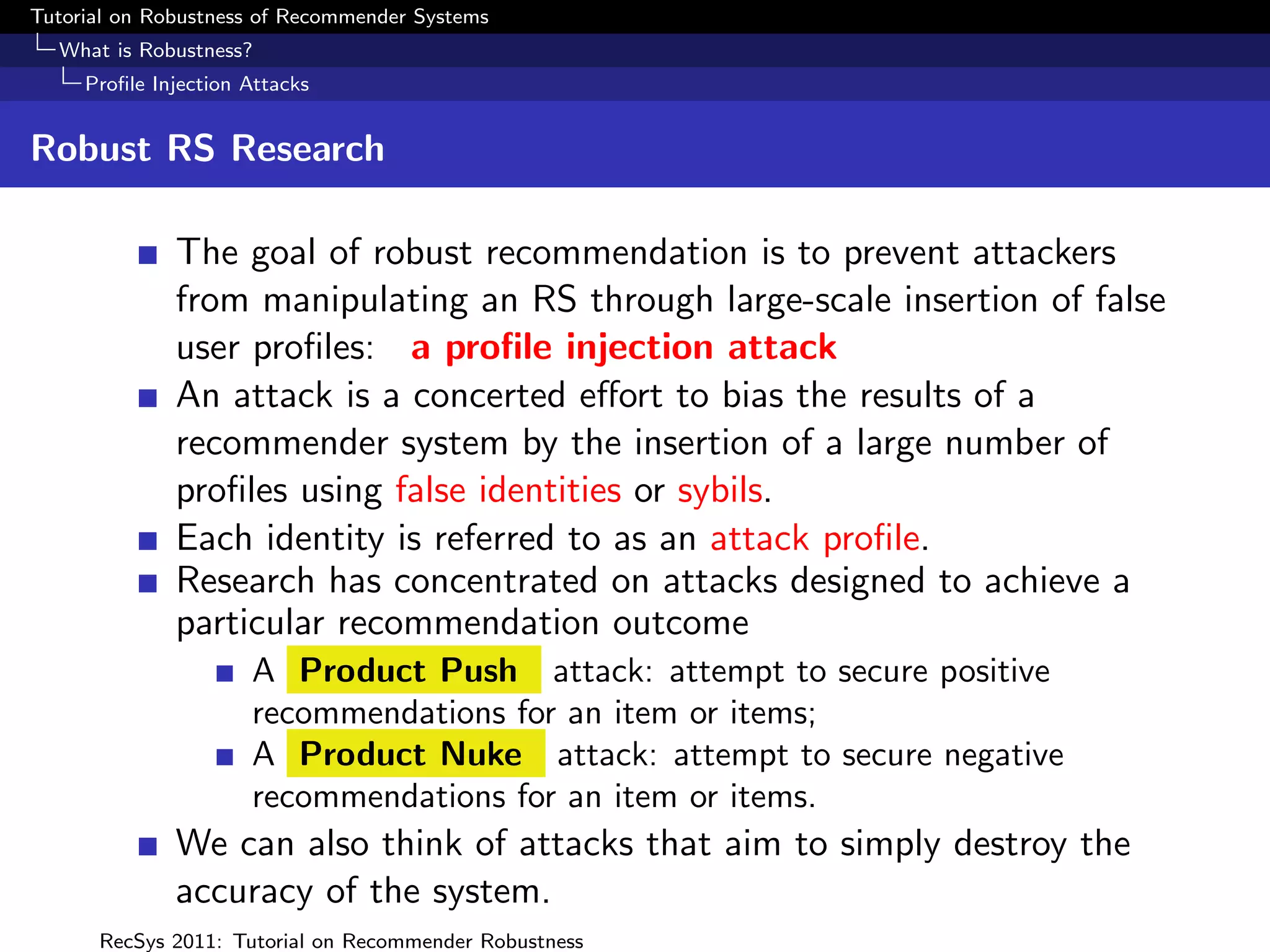
The document presents a tutorial on the robustness of recommender systems, defined as their ability to function under stress, particularly against profile injection attacks, where multiple false identities aim to bias recommendations. It covers various topics including attack strategies, detection methods, and robust algorithm design, emphasizing the importance of understanding and defending against such vulnerabilities to preserve the integrity of recommendations. The tutorial also highlights the implications of these attacks on user experience and system trustworthiness.























![Tutorial on Robustness of Recommender Systems
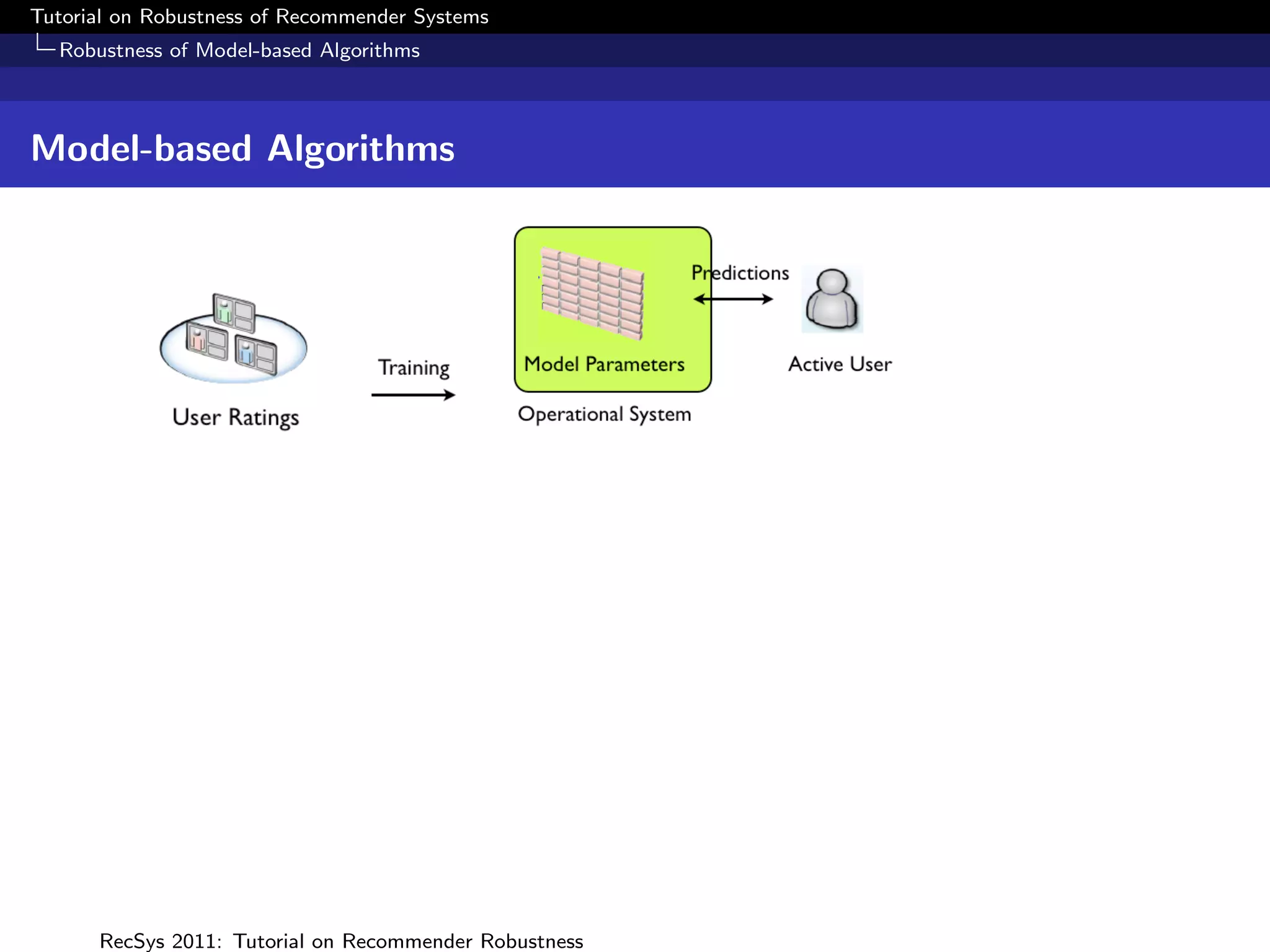
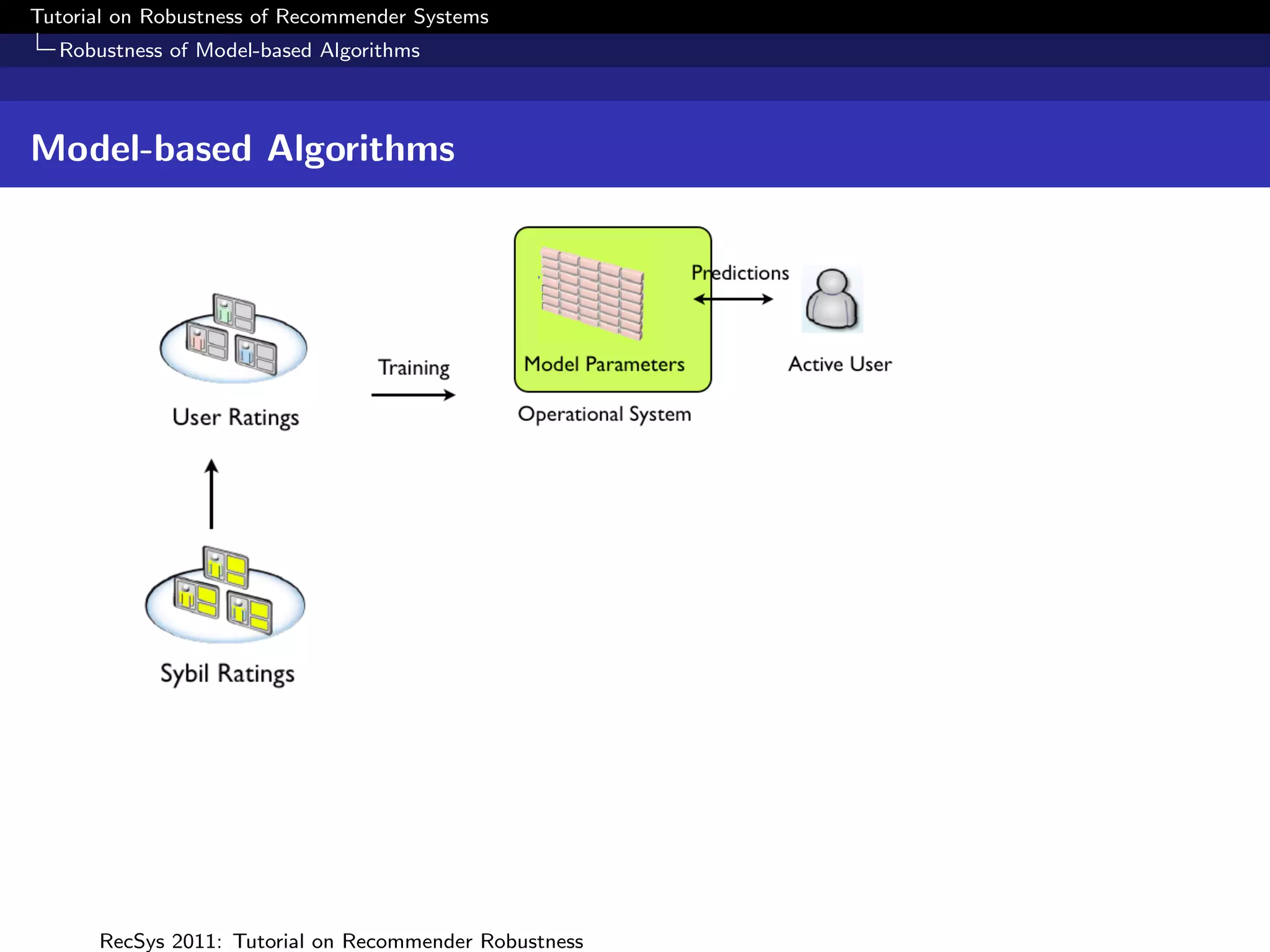
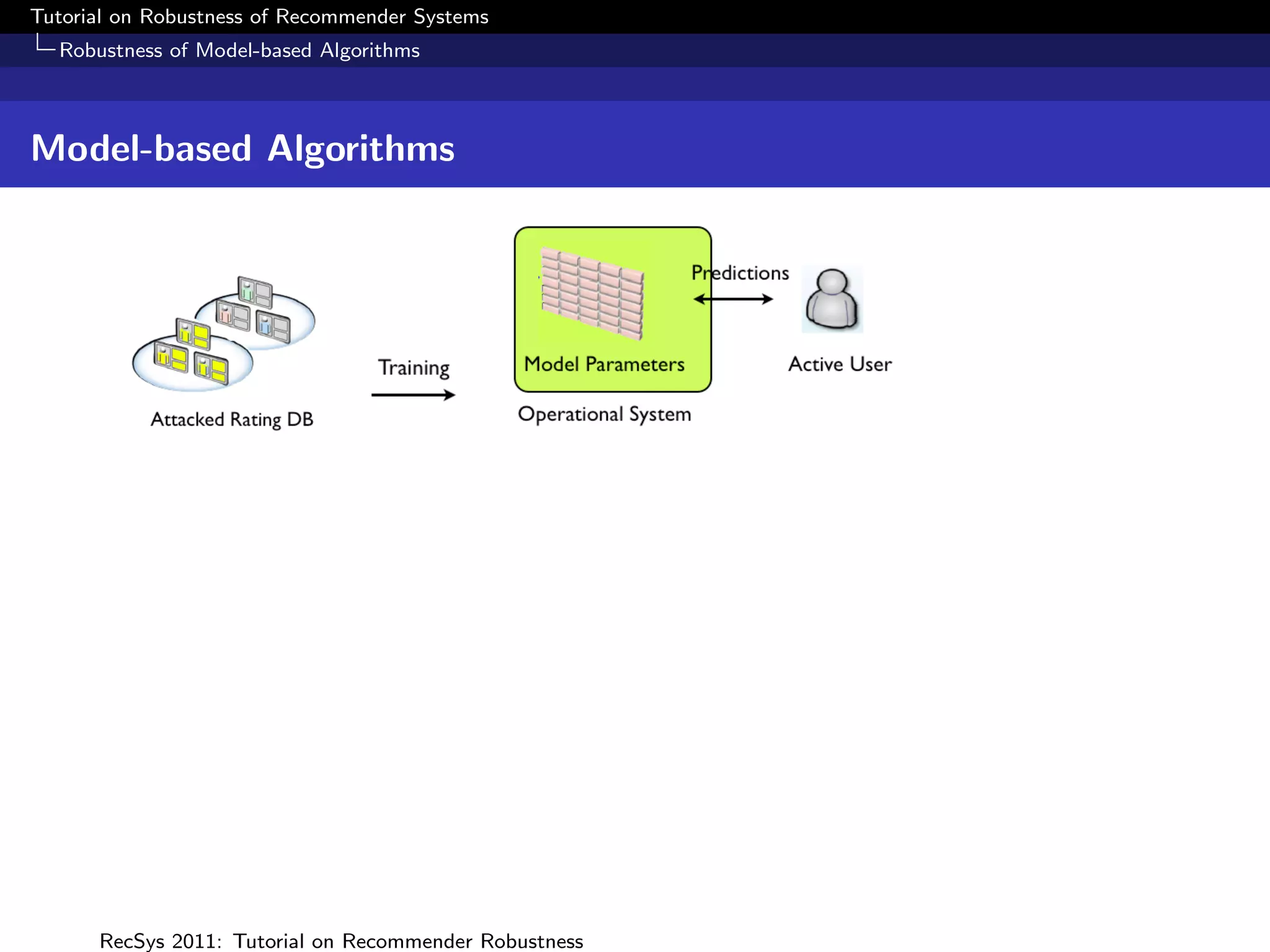
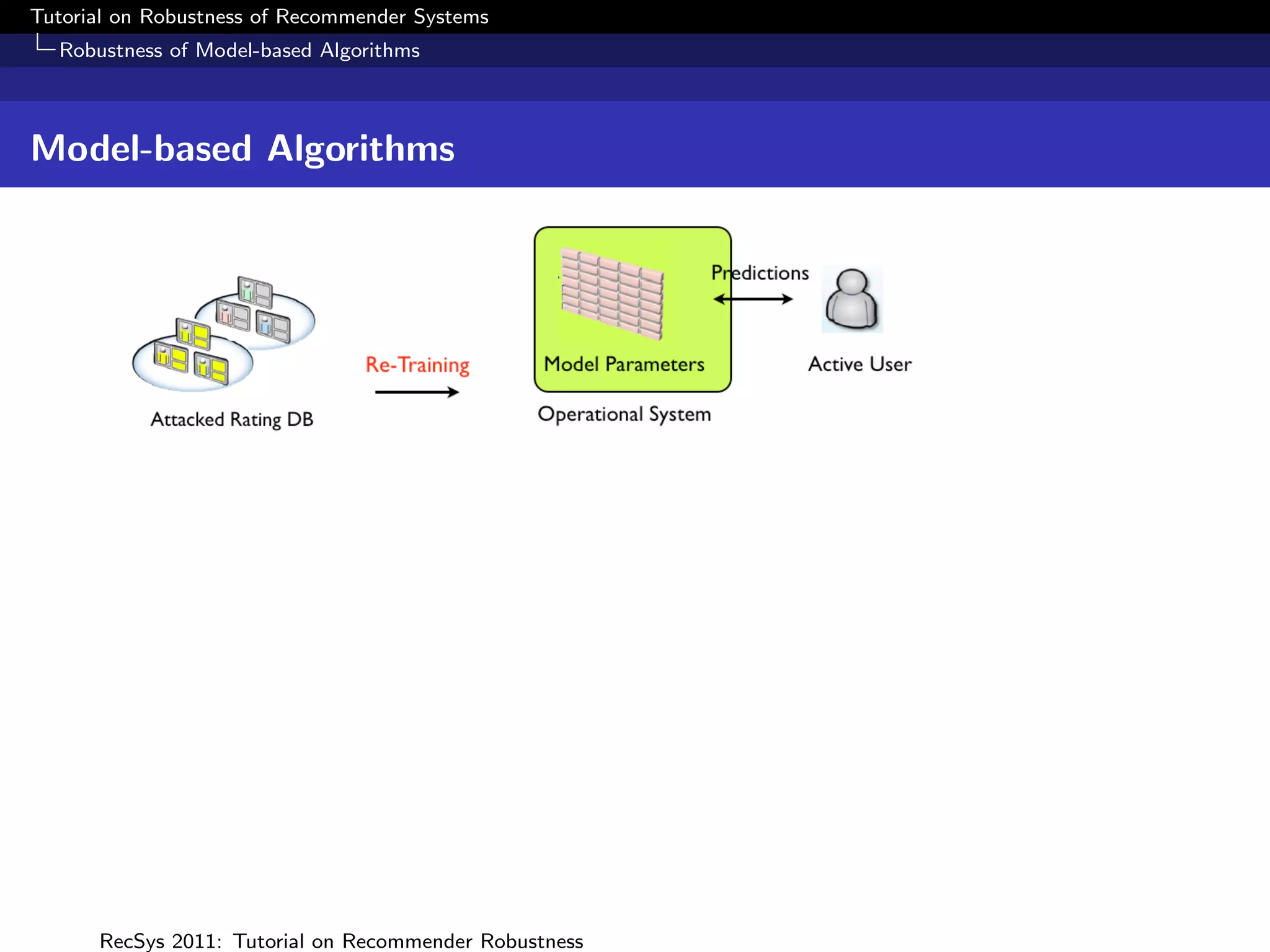
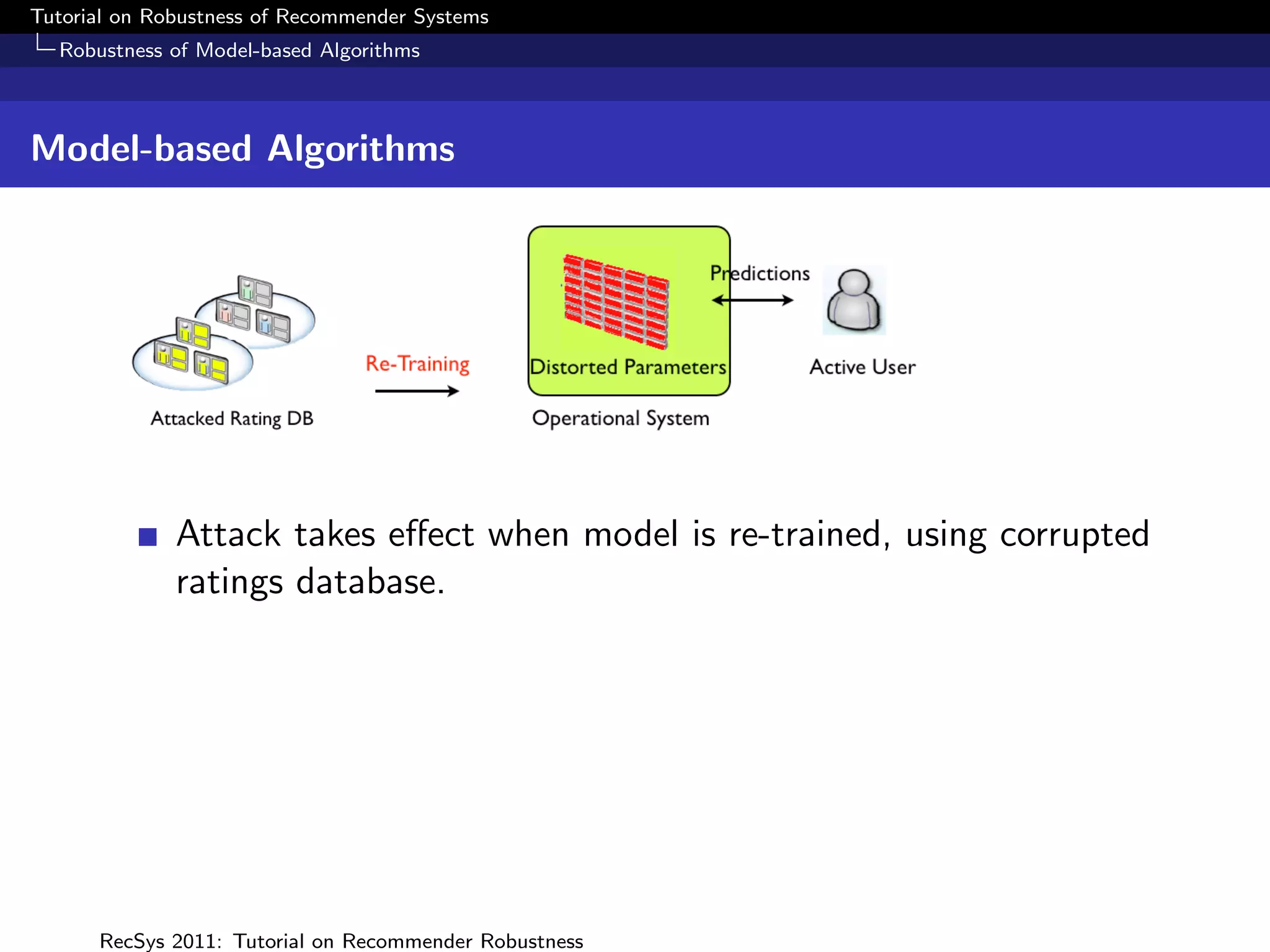
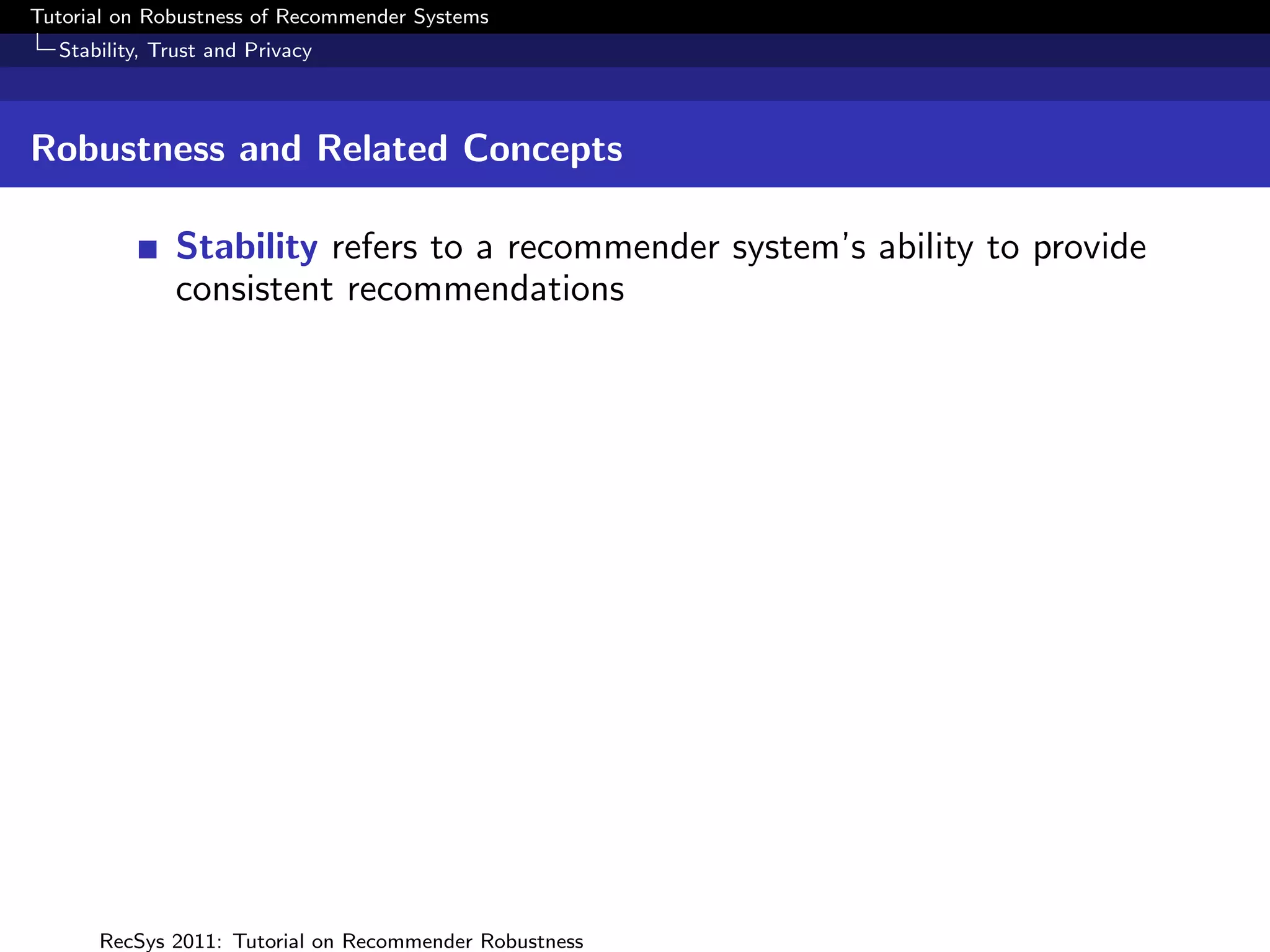
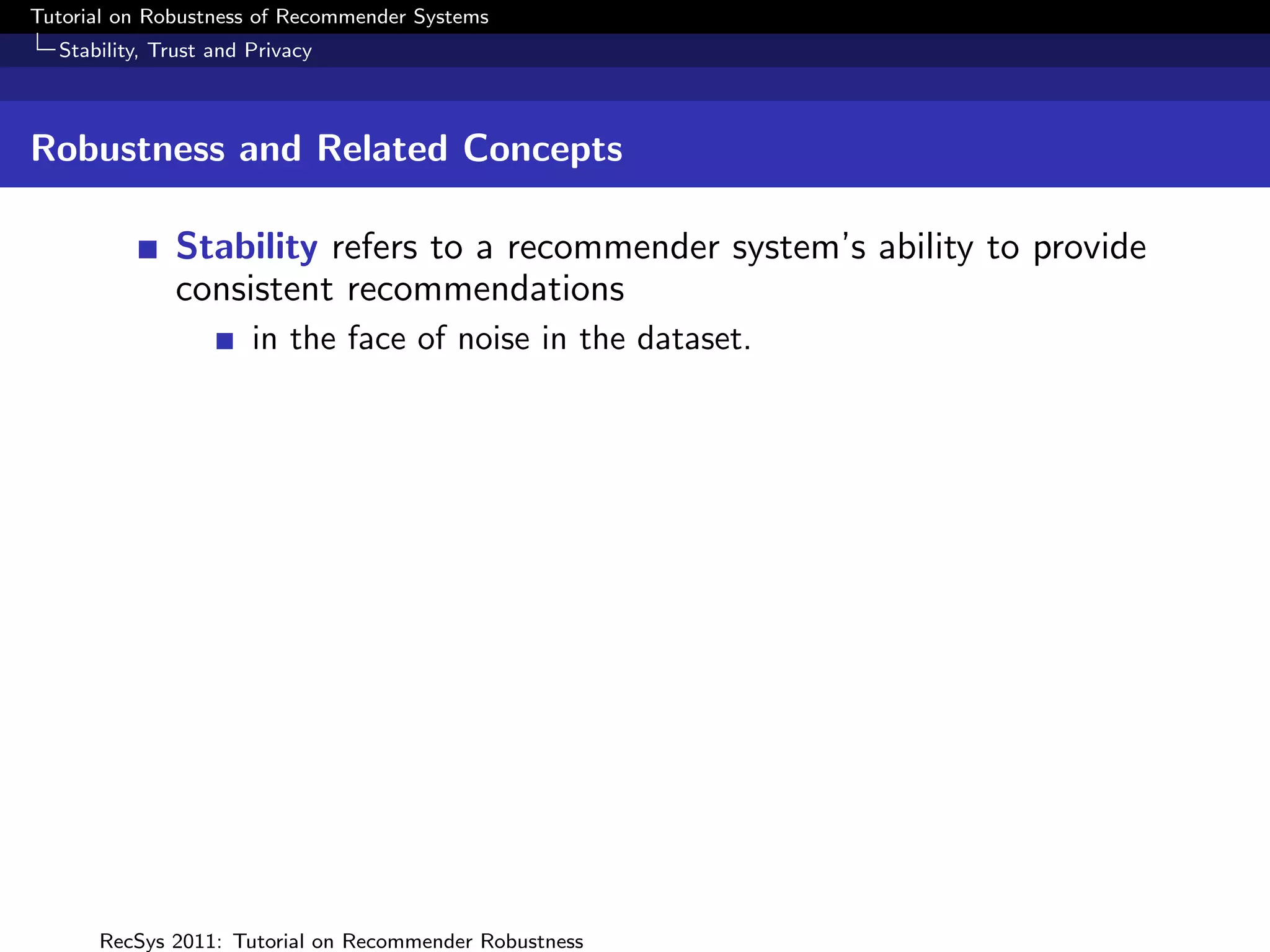
What is Robustness?
Measuring Robustness
Other Measures of Attack Impact
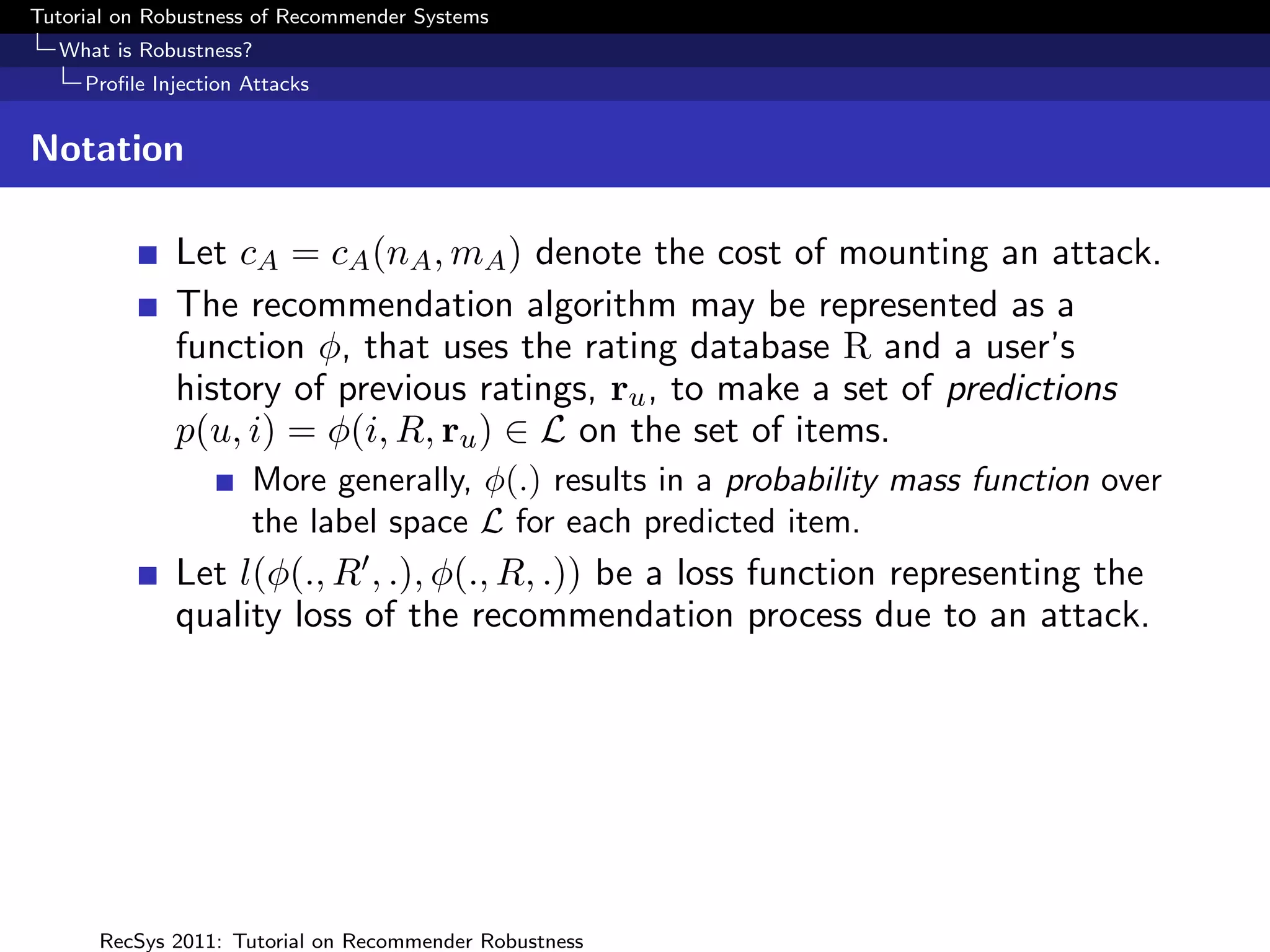
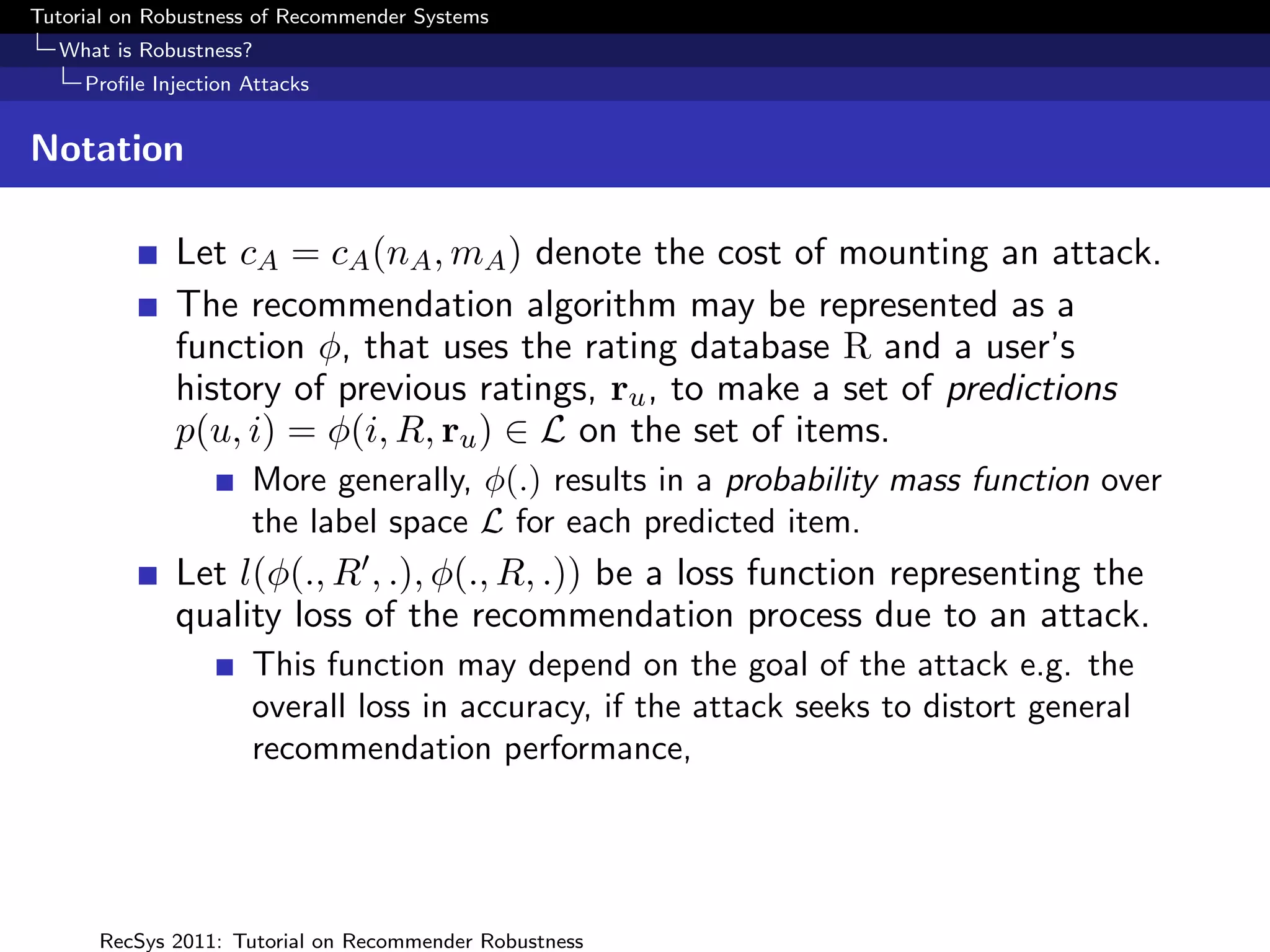
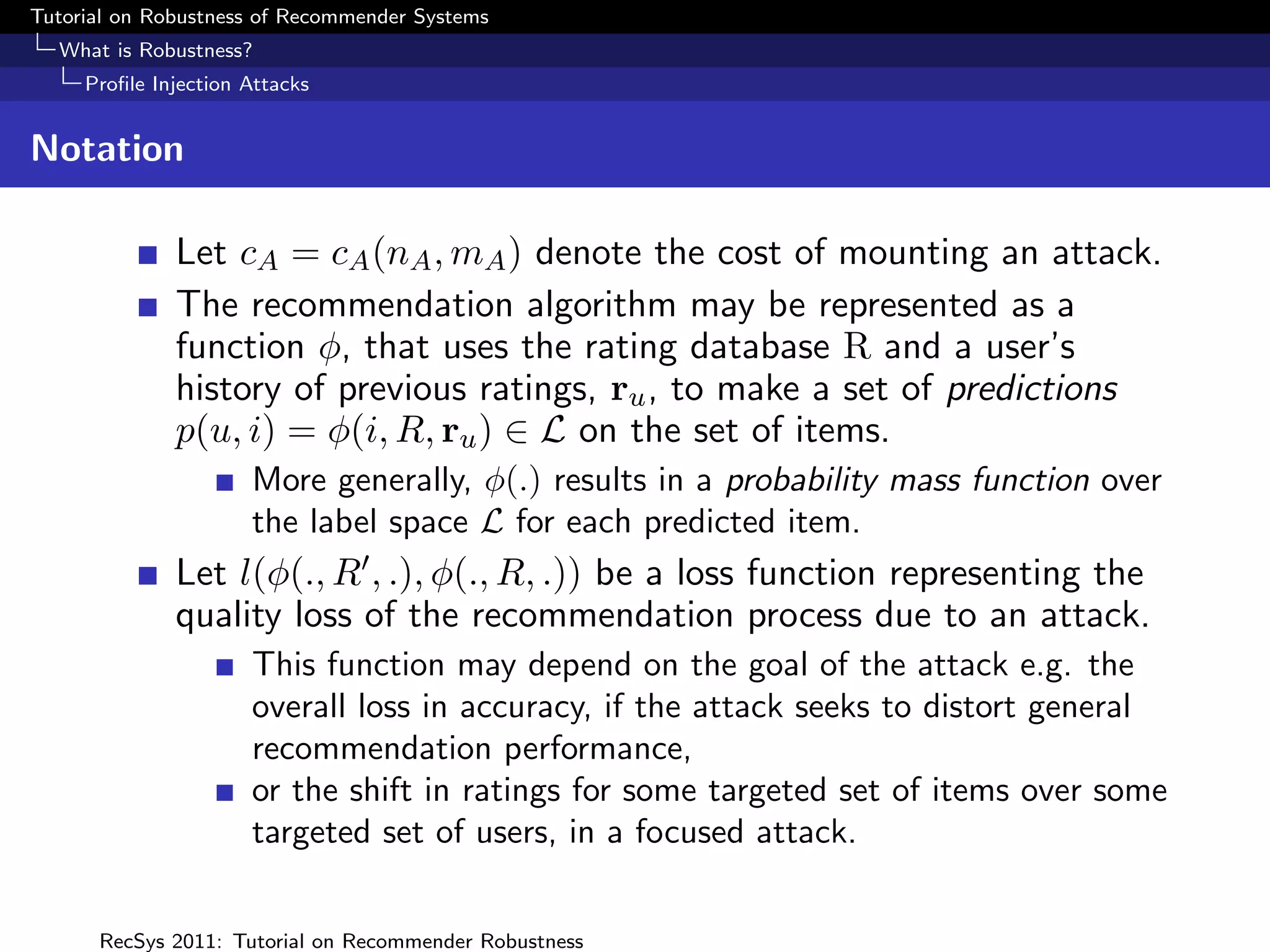
Considering φ(i, R, ru ) as a pmf over L, attack impact can be
measured in terms of the change in this distribution as a
result of the attack.
For instance (Yan and Roy 2009), measure impact in terms of
the average Kullback-Liebler distance between φ(i, R, ru ) and
φ(i, R , ru ) over the set of inspected items.
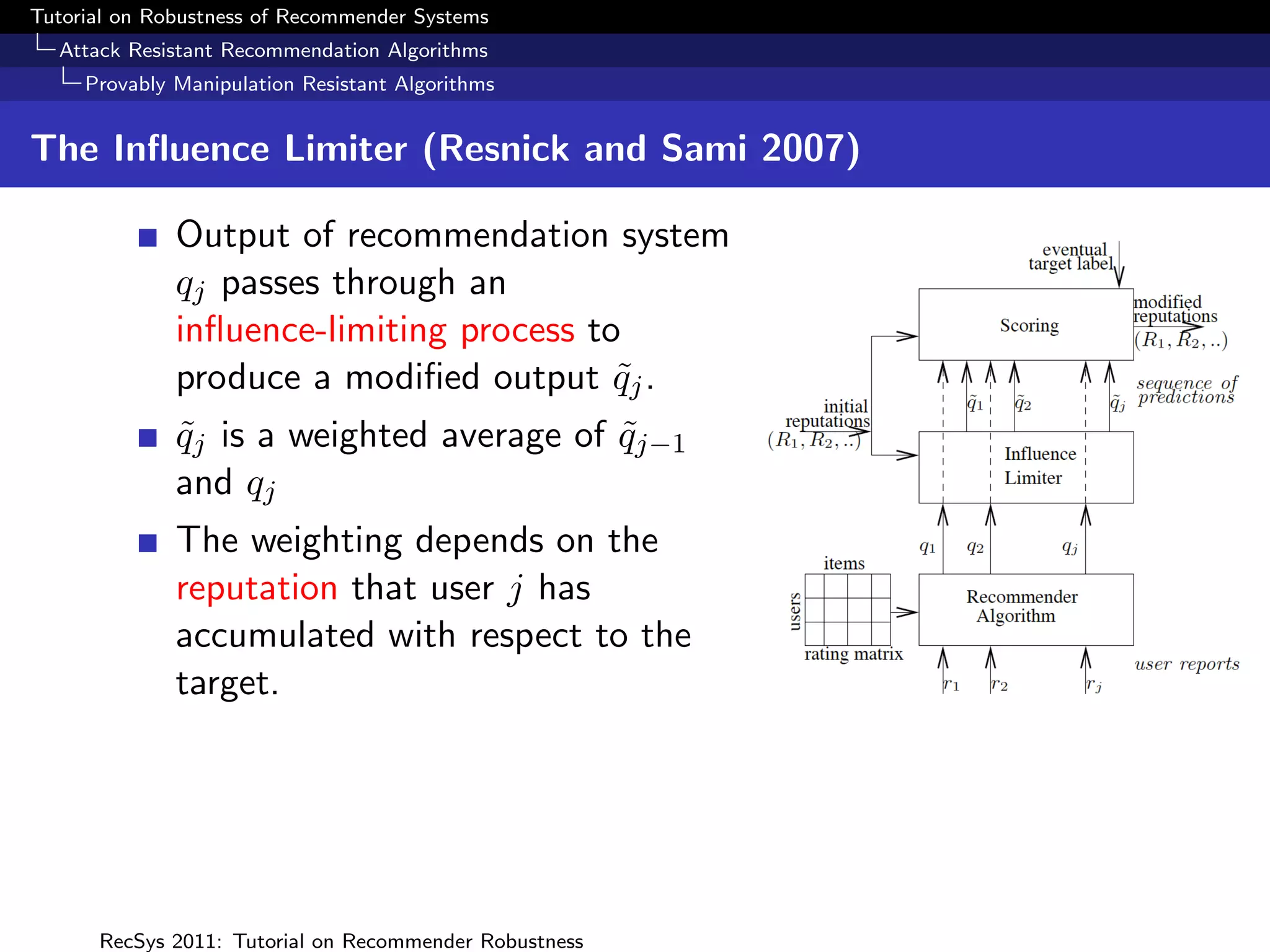
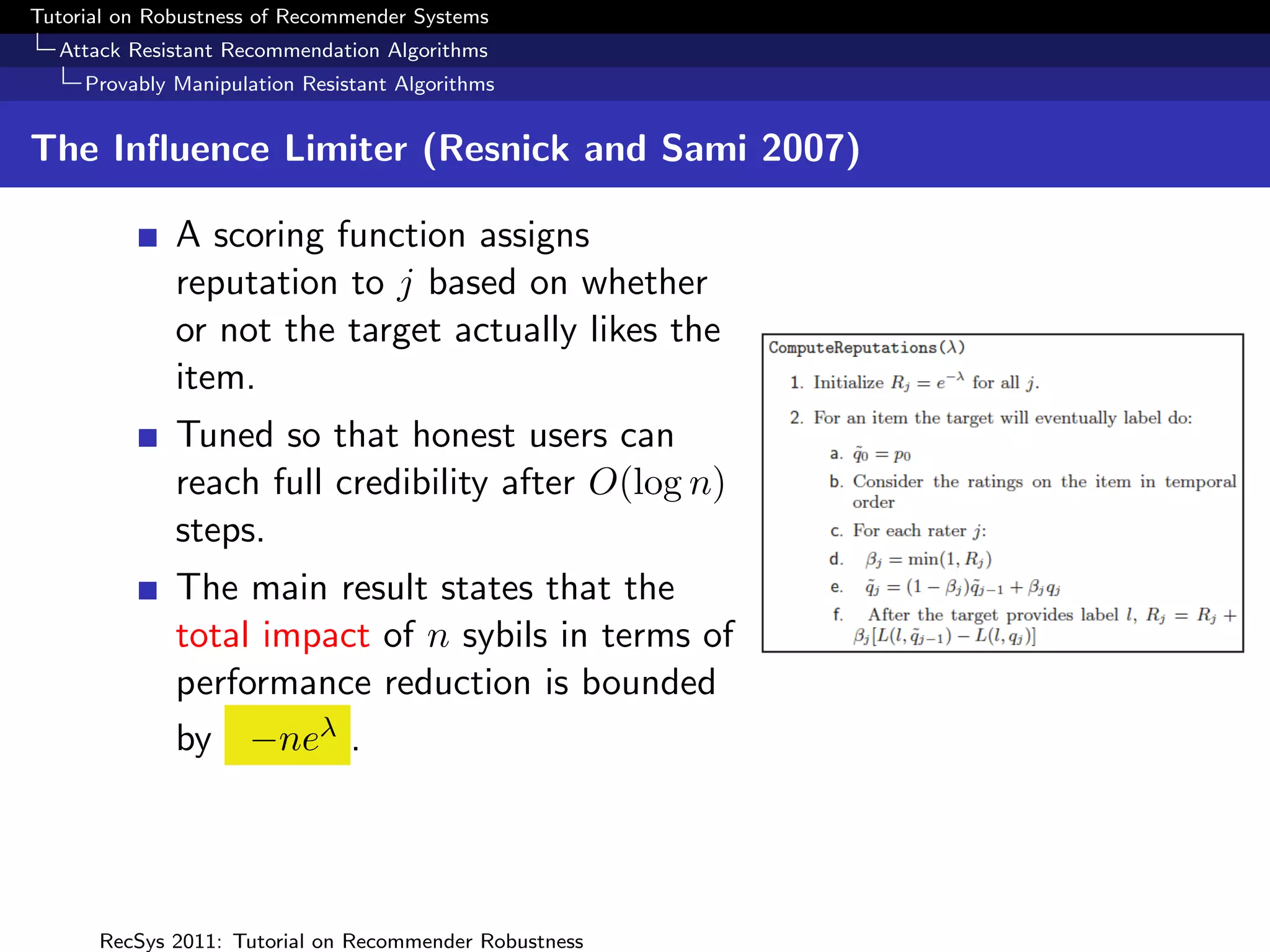
Resnick and Sami (2007) propose loss functions L(l, q) where
l ∈ L, q = φ(i, R, ru ) where the true label of item i is l
e.g. the quadratic loss over a two rating scale [HI, LO], with
q the probability of HI is given by
L(HI, q) = (1 − q)2 ; L(LO, q) = q 2
RecSys 2011: Tutorial on Recommender Robustness](https://image.slidesharecdn.com/robusttutorial-111024141820-phpapp01/75/Tutorial-on-Robustness-of-Recommender-Systems-65-2048.jpg)
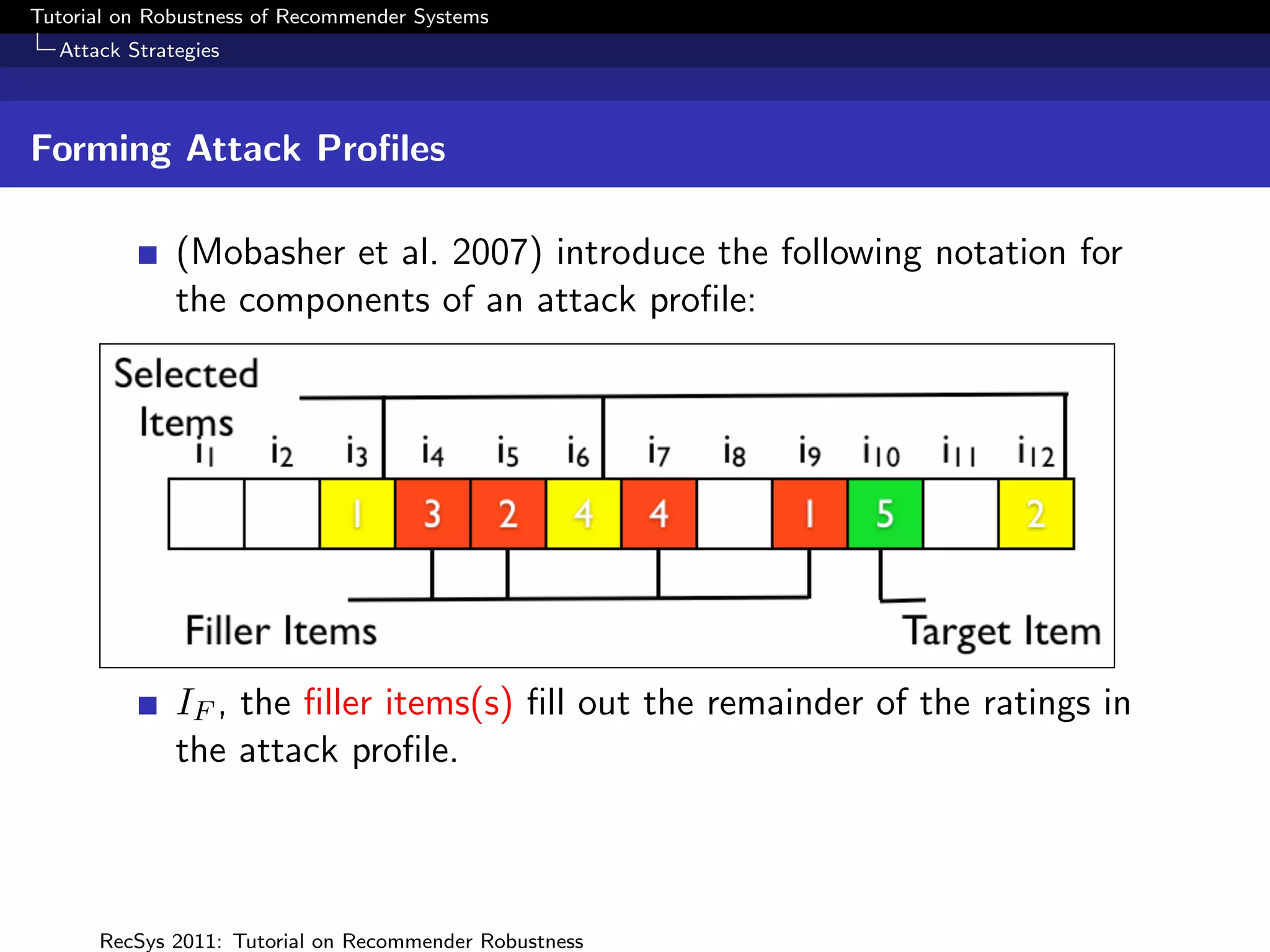






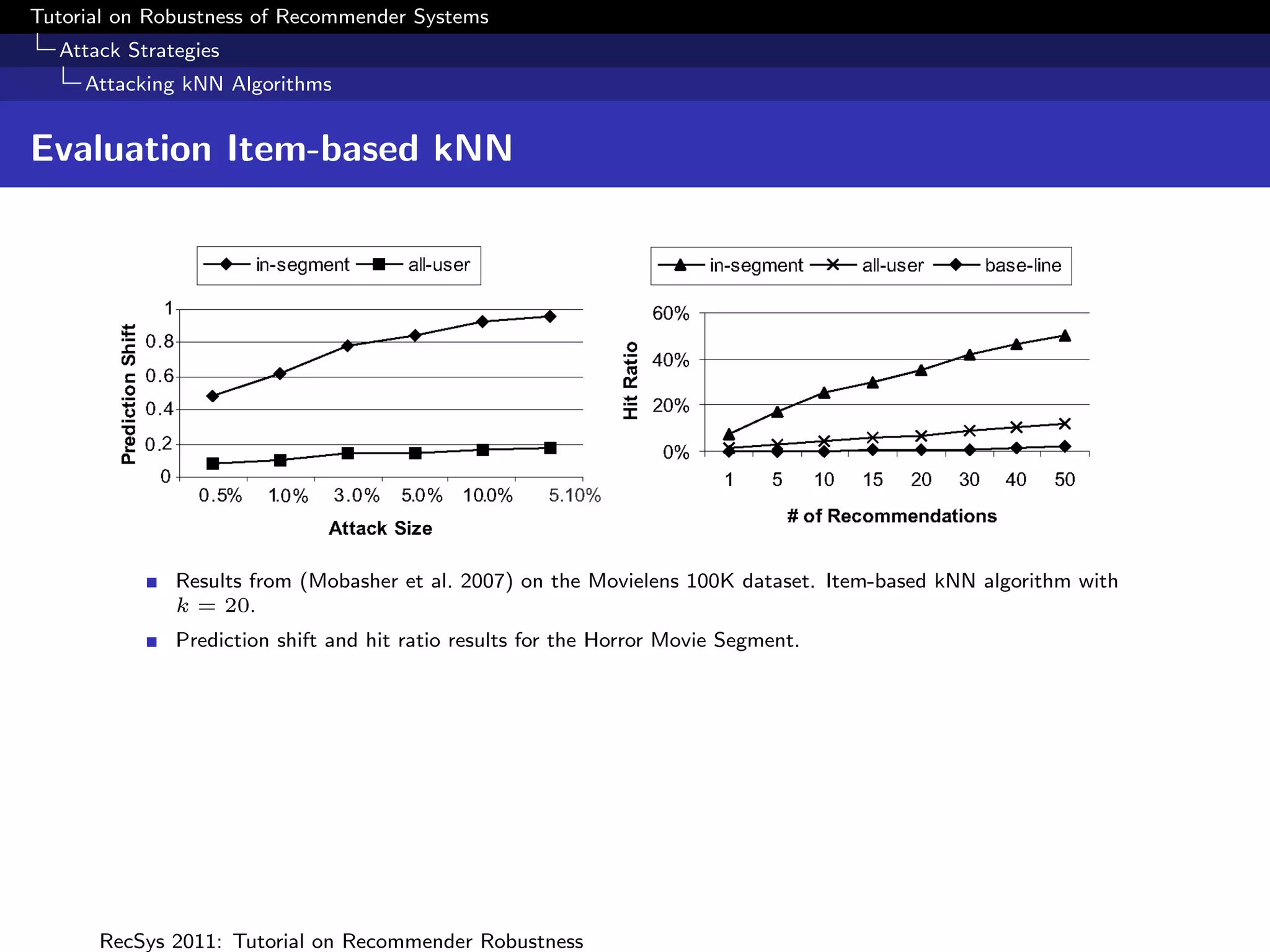
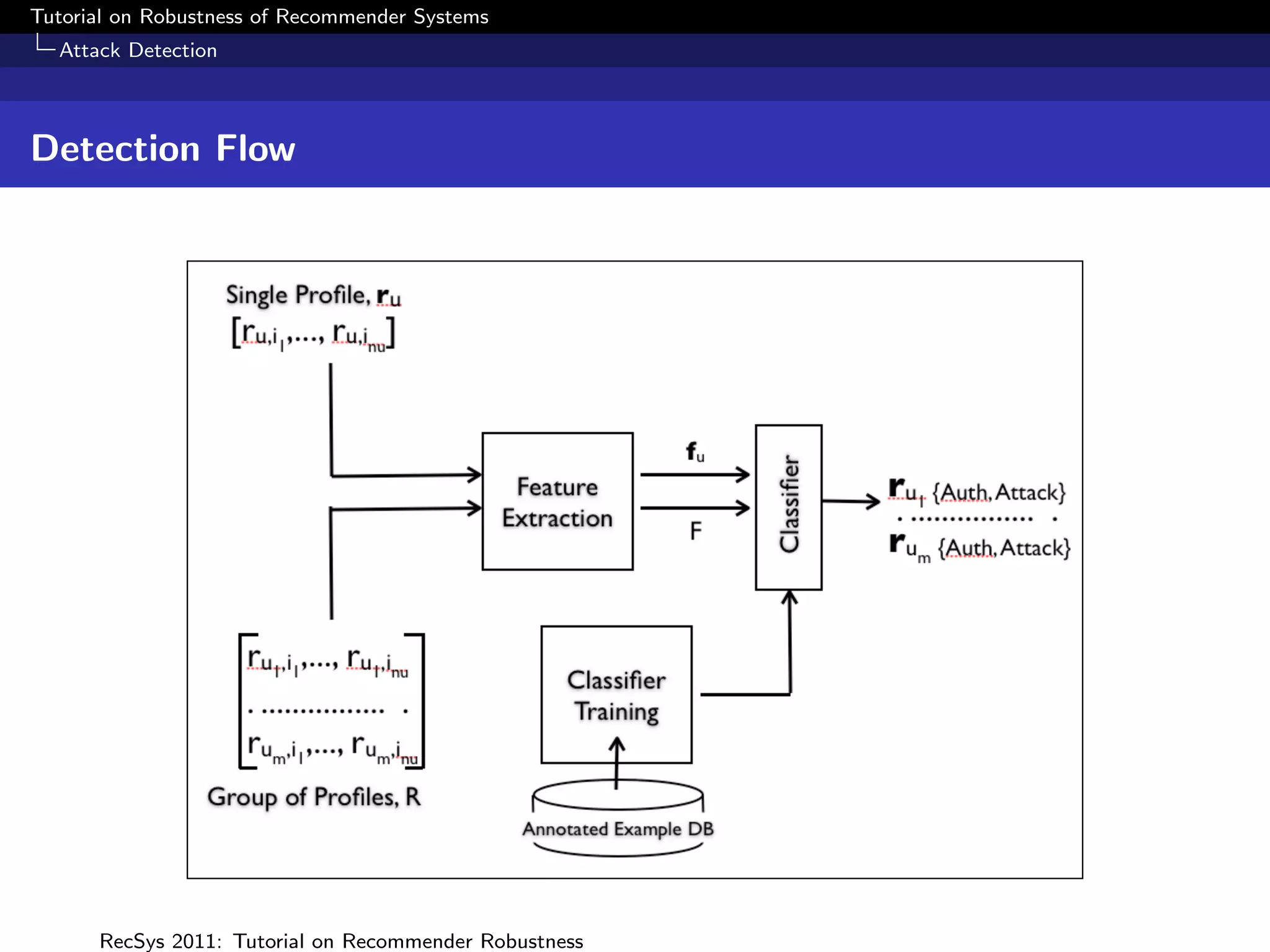
![Tutorial on Robustness of Recommender Systems
Attack Detection
Statistical Attack Detection
Modelling Attack Profiles
As attacks follow well-defined construction, easy to construct
model:
m
Pr[Yi = yi ]
i=1
m
= Pr[Yi = φ]θi (Pr[Yi = yi |Yi = φ]Pr[Yi = φ])1−θi
i=1
Which items are rated?
RecSys 2011: Tutorial on Recommender Robustness](https://image.slidesharecdn.com/robusttutorial-111024141820-phpapp01/75/Tutorial-on-Robustness-of-Recommender-Systems-103-2048.jpg)
![Tutorial on Robustness of Recommender Systems
Attack Detection
Statistical Attack Detection
Modelling Attack Profiles
As attacks follow well-defined construction, easy to construct
model:
m
Pr[Yi = yi ]
i=1
m
= Pr[Yi = φ]θi (Pr[Yi = yi |Yi = φ]Pr[Yi = φ])1−θi
i=1
What ratings used?
RecSys 2011: Tutorial on Recommender Robustness](https://image.slidesharecdn.com/robusttutorial-111024141820-phpapp01/75/Tutorial-on-Robustness-of-Recommender-Systems-104-2048.jpg)
![Tutorial on Robustness of Recommender Systems
Attack Detection
Statistical Attack Detection
Modelling Attack Profiles
As attacks follow well-defined construction, easy to construct
model:
m
Pr[Yi = yi ]
i=1
m 1 1 1−θi
θi yi − 2 − µi yi + 2 − µi
= Pr[Yi = φ] Q −Q
σi σi
i=1
Q(.) = Gaussian Q-function
RecSys 2011: Tutorial on Recommender Robustness](https://image.slidesharecdn.com/robusttutorial-111024141820-phpapp01/75/Tutorial-on-Robustness-of-Recommender-Systems-105-2048.jpg)
![Tutorial on Robustness of Recommender Systems
Attack Detection
Statistical Attack Detection
Modelling Genuine Profiles
Simple model – identical to attack model except that
probability of selecting a filler item is estimated as
pi Pr[Yi = φ] from a dataset of genuine profiles.
ˆ
m
Pr[Yi = yi ]
i=1
m
= pi θi (Pr[Yi = yi |Yi = φ](1 − pi ))1−θi
ˆ ˆ
i=1
Not a realistic model of genuine ratings – assumes user’s
ratings are all independent
But sufficient (almost) to distinguish from attack profiles.
RecSys 2011: Tutorial on Recommender Robustness](https://image.slidesharecdn.com/robusttutorial-111024141820-phpapp01/75/Tutorial-on-Robustness-of-Recommender-Systems-106-2048.jpg)
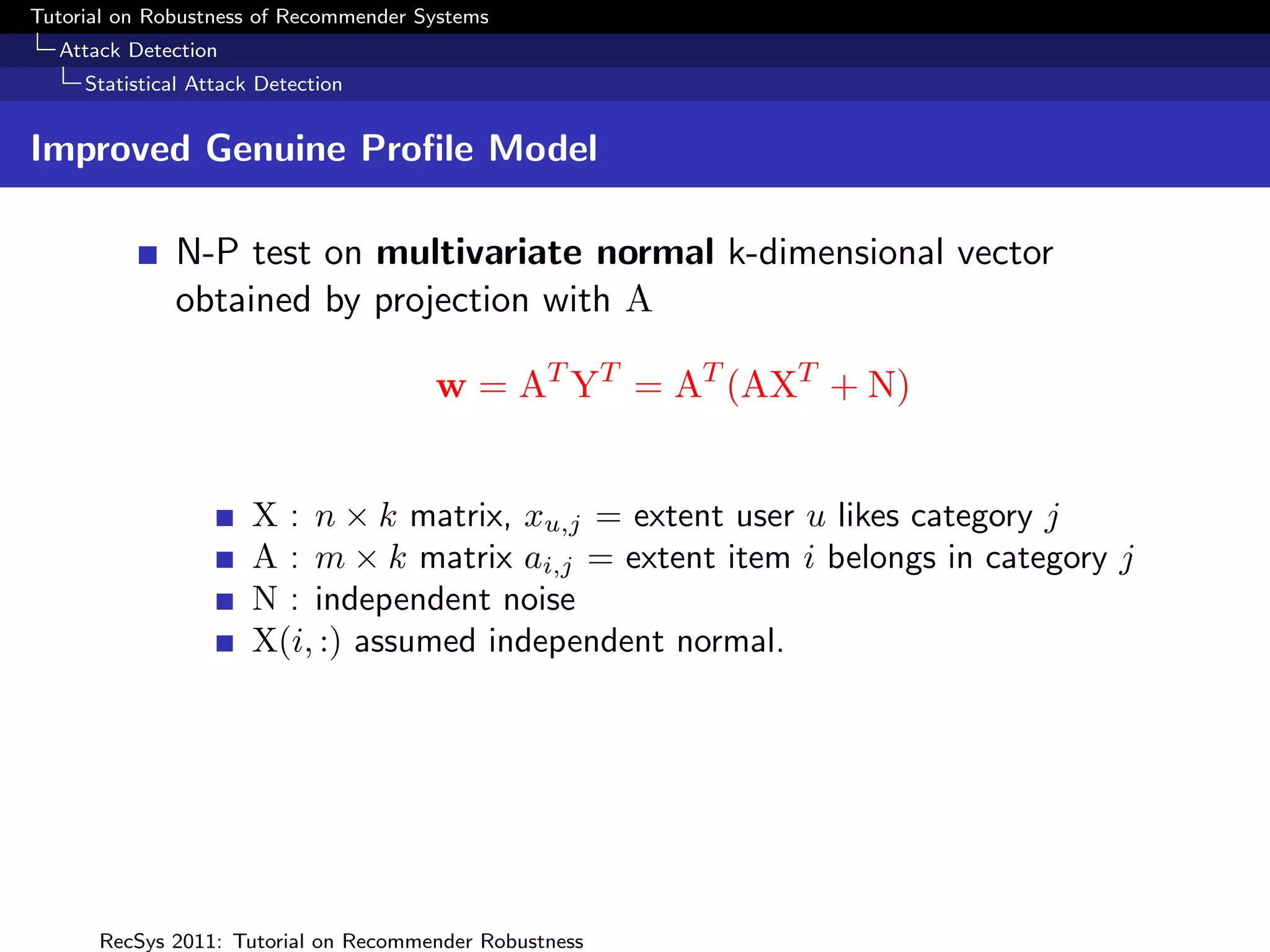
![Tutorial on Robustness of Recommender Systems
Attack Detection
Statistical Attack Detection
Improved Genuine Profile Model
Difficulty
Very high dimensional vectors
Missing values
Factor Model : Assume that the rating matrix can be
represented by the linear model
YT = AXT + N ,
X : n × k matrix, xu,j = extent user u likes category j
A : m × k matrix ai,j = extent item i belongs in category j
N : independent noise
X(i, :) assumed independent normal.
Expectation maximisation to learn A from dataset ([Canny,
2002]).
RecSys 2011: Tutorial on Recommender Robustness](https://image.slidesharecdn.com/robusttutorial-111024141820-phpapp01/75/Tutorial-on-Robustness-of-Recommender-Systems-116-2048.jpg)