Trust Based Recommendation Systems For Tourism System Zaffar Ahmed Shaikh
•Download as DOCX, PDF•
1 like•396 views
The document describes a trust-based recommendation system algorithm for tourism based on random walks on a voting network. The algorithm takes as input a voting network with positive and negative voter nodes and performs a random walk from a source node, terminating when a voter node is reached. It outputs the sign of the difference between the probability of reaching a positive voter vs. a negative voter as the recommendation. The algorithm assigns values to non-voter nodes to solve the system and outputs the sign of the value assigned to the source node as the recommendation.
Report
Share
Report
Share
Recommended
Trust-aware Recommender Systems

This document summarizes a research paper on trust-aware recommender systems. It introduces collaborative filtering and its problems like sparsity and cold start users. It then describes how trust-aware systems address these by using trust networks between users. The proposed Trust-Aware Recommender System (TARS) architecture takes trust and rating matrices as input. Experiments on an online reviews dataset show TARS improves accuracy especially for cold start users, compared to traditional collaborative filtering. Propagating trust increases coverage but also error. Incorporating trust is effective at alleviating weaknesses of recommendation systems.
Matrix Factorization Techniques For Recommender Systems

The document discusses matrix factorization techniques for recommender systems. It begins by describing common recommender system strategies like content-based and collaborative filtering approaches. It then introduces matrix factorization methods, which characterize both users and items by vectors of latent factors inferred from rating patterns. The basic matrix factorization model approximates user ratings as the inner product of user and item vectors in the joint latent factor space. Learning algorithms like stochastic gradient descent and alternating least squares are used to compute the user and item vectors by minimizing a regularized error function on known ratings.
SkillsRec: A Novel Semantic Analysis Driven Learner Skills Mining and Filteri...

Research paper presentation from AINA 2015 http://voyager.ce.fit.ac.jp/conf/aina/2015/
KDJ Center, Gwangju, Korea
Identifying Measures to Foster Teachers’ Competence for Personal Learning Env...

Personal learning environment (PLE) is a learner centered and controlled environment where learner constructs knowledge socially and collaboratively with the help of knowledgeable peers, mentors, and teachers. Teacher, being the most knowledgeable other in this environment, has to develop a strong and multifunctional association between the learner and the PLE. However, in real world scenarios, this is not the case as teachers’ current competencies are not sufficiently developed to provide desired results. A major reason for this inefficiency is the unawareness of the required roles that a teacher has to play in such environments. Our study is aimed at identifying measures to foster teachers’ competence in PLE conceived teaching scenarios. We used the modified version of policy-Delphi in which we worked with 34 international experts who are either associated with PLEs in one of the four dimensions: teachers, researchers, designers, or practitioners. These experts reviewed a 10-item teachers’ PLE competency developing measures list, which we developed through an exhaustive literature review. As per Delphi procedure, the consensus on measures list was achieved in three rounds. During the process, participants collaboratively modified measures list at length and extended list from 10 items to 16 items. Based on the findings, we argue that institutional support is of prime importance to improve teachers’ PLE competence.
Higher Education in Pakistan: An ICT Integration Viewpoint

1) The study surveyed 30 higher education experts in Pakistan using a modified Delphi method to understand their views on the role of information and communication technologies (ICTs) in shaping the future of Pakistan's higher education system.
2) Results showed significant gaps in current ICT demand and supply, usage, and ICT-related problems in higher education. Participants saw great potential for ICT to play a crucial role in developing Pakistan's higher education system but noted obstacles like poor infrastructure and lack of resources.
3) Participants suggested that developing an effective and robust ICT policy, increasing funding, providing training and high-tech facilities, and setting clear targets and guidelines could help integrate ICT successfully and improve higher education in
Presentation: Higher Education in Pakistan: An ICT Integration Viewpoint

This document summarizes a study examining challenges in integrating information and communication technology (ICT) into Pakistan's higher education system. A literature review found that ICT can improve education but its use faces barriers like lack of infrastructure and policy. The study used a Delphi method survey of 30 experts to evaluate ICT issues. Findings showed current ICT use is around 50% of potential and barriers include uneven ICT distribution and lack of funding. Recommendations include improving ICT skills, generating financial support, and developing a robust long-term ICT policy and implementation plan.
Presentation: ZPD Incidence Development Strategy for Demand of ICTs in Higher...

The document outlines a strategy for developing incidence of information and communication technologies (ICTs) in higher education institutions in Pakistan. It discusses relevant literature on ICT adoption in education and the concept of zone of proximal development (ZPD). A Delphi study was conducted to identify ZPD gaps in various dimensions of ICT use. The strategy proposes recommendations in six areas: using ICT for teaching and learning, gaining student attainment, improving teaching skills, managing and sharing information, partnerships and training, and connectivity and access. The goal is to provide guidance to higher education authorities on integrating ICT and improving learning outcomes.
Usage, Acceptance, Adoption, and Diffusion of Information & Communication Tec...

This document summarizes a study that measured critical factors related to the usage, acceptance, adoption and diffusion of information and communication technologies (ICTs) in higher education institutions in Pakistan. The study used the Delphi method to analyze differences in perceptions among higher education stakeholders. It found a significant "zone of proximal development gap" in ICT usage, acceptance and adoption in Pakistani institutions compared to developed nations. However, it did not find significant differences in perceptions regarding issues like ICT demand and supply or challenges to ICT integration. The study recommends its findings be considered in designing ICT policies for higher education in Pakistan and other developing countries.
Recommended
Trust-aware Recommender Systems

This document summarizes a research paper on trust-aware recommender systems. It introduces collaborative filtering and its problems like sparsity and cold start users. It then describes how trust-aware systems address these by using trust networks between users. The proposed Trust-Aware Recommender System (TARS) architecture takes trust and rating matrices as input. Experiments on an online reviews dataset show TARS improves accuracy especially for cold start users, compared to traditional collaborative filtering. Propagating trust increases coverage but also error. Incorporating trust is effective at alleviating weaknesses of recommendation systems.
Matrix Factorization Techniques For Recommender Systems

The document discusses matrix factorization techniques for recommender systems. It begins by describing common recommender system strategies like content-based and collaborative filtering approaches. It then introduces matrix factorization methods, which characterize both users and items by vectors of latent factors inferred from rating patterns. The basic matrix factorization model approximates user ratings as the inner product of user and item vectors in the joint latent factor space. Learning algorithms like stochastic gradient descent and alternating least squares are used to compute the user and item vectors by minimizing a regularized error function on known ratings.
SkillsRec: A Novel Semantic Analysis Driven Learner Skills Mining and Filteri...

Research paper presentation from AINA 2015 http://voyager.ce.fit.ac.jp/conf/aina/2015/
KDJ Center, Gwangju, Korea
Identifying Measures to Foster Teachers’ Competence for Personal Learning Env...

Personal learning environment (PLE) is a learner centered and controlled environment where learner constructs knowledge socially and collaboratively with the help of knowledgeable peers, mentors, and teachers. Teacher, being the most knowledgeable other in this environment, has to develop a strong and multifunctional association between the learner and the PLE. However, in real world scenarios, this is not the case as teachers’ current competencies are not sufficiently developed to provide desired results. A major reason for this inefficiency is the unawareness of the required roles that a teacher has to play in such environments. Our study is aimed at identifying measures to foster teachers’ competence in PLE conceived teaching scenarios. We used the modified version of policy-Delphi in which we worked with 34 international experts who are either associated with PLEs in one of the four dimensions: teachers, researchers, designers, or practitioners. These experts reviewed a 10-item teachers’ PLE competency developing measures list, which we developed through an exhaustive literature review. As per Delphi procedure, the consensus on measures list was achieved in three rounds. During the process, participants collaboratively modified measures list at length and extended list from 10 items to 16 items. Based on the findings, we argue that institutional support is of prime importance to improve teachers’ PLE competence.
Higher Education in Pakistan: An ICT Integration Viewpoint

1) The study surveyed 30 higher education experts in Pakistan using a modified Delphi method to understand their views on the role of information and communication technologies (ICTs) in shaping the future of Pakistan's higher education system.
2) Results showed significant gaps in current ICT demand and supply, usage, and ICT-related problems in higher education. Participants saw great potential for ICT to play a crucial role in developing Pakistan's higher education system but noted obstacles like poor infrastructure and lack of resources.
3) Participants suggested that developing an effective and robust ICT policy, increasing funding, providing training and high-tech facilities, and setting clear targets and guidelines could help integrate ICT successfully and improve higher education in
Presentation: Higher Education in Pakistan: An ICT Integration Viewpoint

This document summarizes a study examining challenges in integrating information and communication technology (ICT) into Pakistan's higher education system. A literature review found that ICT can improve education but its use faces barriers like lack of infrastructure and policy. The study used a Delphi method survey of 30 experts to evaluate ICT issues. Findings showed current ICT use is around 50% of potential and barriers include uneven ICT distribution and lack of funding. Recommendations include improving ICT skills, generating financial support, and developing a robust long-term ICT policy and implementation plan.
Presentation: ZPD Incidence Development Strategy for Demand of ICTs in Higher...

The document outlines a strategy for developing incidence of information and communication technologies (ICTs) in higher education institutions in Pakistan. It discusses relevant literature on ICT adoption in education and the concept of zone of proximal development (ZPD). A Delphi study was conducted to identify ZPD gaps in various dimensions of ICT use. The strategy proposes recommendations in six areas: using ICT for teaching and learning, gaining student attainment, improving teaching skills, managing and sharing information, partnerships and training, and connectivity and access. The goal is to provide guidance to higher education authorities on integrating ICT and improving learning outcomes.
Usage, Acceptance, Adoption, and Diffusion of Information & Communication Tec...

This document summarizes a study that measured critical factors related to the usage, acceptance, adoption and diffusion of information and communication technologies (ICTs) in higher education institutions in Pakistan. The study used the Delphi method to analyze differences in perceptions among higher education stakeholders. It found a significant "zone of proximal development gap" in ICT usage, acceptance and adoption in Pakistani institutions compared to developed nations. However, it did not find significant differences in perceptions regarding issues like ICT demand and supply or challenges to ICT integration. The study recommends its findings be considered in designing ICT policies for higher education in Pakistan and other developing countries.
Role of ICT in Shaping the Future of Pakistani Higher Education System

This study examined the challenges faced by the Pakistani higher education system (HES) in integrating information and communication technology (ICT); it aimed at understanding ICT needs, measuring the increase in ICT demand, determining the relationship between ICT and HES performance, and understanding how the HES copes with the challenges of implementing ICT. The results of these analyses were used as the basis to suggest solutions. The normative Delphi method was applied to evaluate a sample of 30 HES experts randomly selected from urban and rural areas of Pakistan by administering a literature-based 35-item questionnaire. The
experts revealed significant gaps in ICT demand and supply, ICT use, ICT-based higher education problems, and reasons for delays in ICT integration and provided suggestions for developing ICT-driven HES in Pakistan. This
study’s findings suggest that an effective and robust HES ICT policy could greatly improve the status of the Pakistani knowledge-based economy, thus helping establish ICT policy and planning, administration, and integration at the higher education level.
Role of Teacher in Personal Learning Environments

The aim of this paper is to discuss the changing roles and competencies of a teacher in context of prevailing developments accomplished by the vast availability of social software, which have made easy the development of Personal Learning Environments (PLEs). This has been accomplished by an in-depth review of the literature on teachers’ socially situated competencies and roles with regard to the tasks and guidance they provide to students shape their PLEs. Review process provides an insight of PLE research studies, constructivist learning theories, and teacher changing roles. The results of this study outline the roles that portray the importance of teacher competencies as role in Planning and Design, Instruction and Learning, Communication and Interaction, Management and Administration, and Use of Technology.
Presentation - Role of Teacher in Personal Learning Environments

Role of Teacher in PLEs - Presented by Zaffar Ahmed Shaikh in "The PLE Conference 2011", held during 11-13 July 2011 University of Southampton, UK.
Network Theory

This chapter will introduce you to the field of science known as Network Theory and tell you about the major researches that took place since its conceptualization. Since the course in question is social computing the chapter is written in a way to give examples and illustrations which mostly relate to social computing. It also contains theories and information which are mostly related to network theory and have some or no relation to social computing. But the basic purpose of this chapter is to explain Network theory and its applications in the field of social computing.
Introduction to Social Computing - Book Chapter

Social computing is a rapidly growing and constantly evolving technology that is aimed at increasing communication, encouraging collaboration, and enhancing productivity among people and resources. Social computing applications or Web 2.0 are built on a range of advanced and supporting technologies that enhance collective action and interaction which currently dominates the Web (Parameswaran & Whinston 2007).
Social computing applications are categorized into social media, social bookmarking, and social networks categories as identified by the continuing Web 2.0 trend (Schwartz et al. 2009; Amer-Yahia, 2009). Each of these categories has been embodied by various social software and web sites. Some of the best-known and equally famous social web sites that dominate the web are Facebook, YouTube, Twitter, Wikipedia, Delicious, and LinkedIn.
Chapter 2 Cover Updated By Zaffar Ahmed Shaikh

This document provides an introduction to network theory and its major concepts and research areas. It discusses what networks are, common network models, and seminal works that helped establish the field, including sociograms, the small world phenomenon, and theories of strong and weak social ties. Major areas of research covered include distance and effective distance between nodes, the size of interpersonal environments, degrees of separation, and how weak ties help integrate social systems. The document concludes with brief sections on network optimization and analysis.
Chapter 1 Cover Updated By Zaffar Ahmed Shaikh

This document provides an introduction to social computing, covering its history from early social software to modern applications enabled by Web 2.0 technologies. It discusses key concepts in social computing design and models of social behavior, comparing crowd sourcing to outsourcing. The document is intended to provide learning objectives on social computing topics.
Prediction Markets

The document discusses infrastructure requirements for social computing applications, including common tools like Ajax, podcasts, Yahoo Widgets, Python, and Perl. It also discusses social computing platforms like Ruby on Rails, MySQL, and Microsoft SharePoint. Microsoft SharePoint is highlighted as a platform that can be used to build eight social computing applications within one system, including features like My Sites, Team Sites, blogs, people search, wikis, community sites, announcements, and internal/external groups.
Nearest Neighbor Algorithm Zaffar Ahmed

The document summarizes the K-nearest neighbor (KNN) algorithm. KNN is a memory-based algorithm that finds the K training samples nearest to a query point and predicts the query's classification based on the majority classification of its neighbors. The summary explains:
1) KNN measures the distance between query points and training samples to classify new objects based on the majority category of its K nearest neighbors.
2) To make a prediction, KNN determines K, calculates distances between the query and all training points, identifies the K nearest neighbors, collects their classifications, and predicts the query's classification based on the majority of its neighbors.
3) An example is given where KNN predicts the winner of an
Social Computing Applications Infrastructure

The document discusses infrastructure requirements for social computing applications, including common tools like Ajax, podcasts, Yahoo Widgets, Python, and Perl. It also discusses social computing platforms like Ruby on Rails, MySQL, and Microsoft SharePoint. Microsoft SharePoint is highlighted as a platform that can be used to build eight social computing applications within one system, including features like My Sites, Team Sites, blogs, people search, wikis, community sites, announcements, and internal/external groups.
Zaffar+Ahmed+ +Collaborative+Filtering

Collaborative filtering analyzes data from multiple sources to develop profiles of people with similar tastes. It finds similarities between users based on their preferences and provides recommendations based on the preferences of similar users. Collaborative filtering requires a large amount of stored user data to make reliable recommendations, and the more users in the population, the more useful the recommendations will be. However, with small datasets it can produce false connections or poor predictions.
OpenID AuthZEN Interop Read Out - Authorization

During Identiverse 2024 and EIC 2024, members of the OpenID AuthZEN WG got together and demoed their authorization endpoints conforming to the AuthZEN API
Driving Business Innovation: Latest Generative AI Advancements & Success Story

Are you ready to revolutionize how you handle data? Join us for a webinar where we’ll bring you up to speed with the latest advancements in Generative AI technology and discover how leveraging FME with tools from giants like Google Gemini, Amazon, and Microsoft OpenAI can supercharge your workflow efficiency.
During the hour, we’ll take you through:
Guest Speaker Segment with Hannah Barrington: Dive into the world of dynamic real estate marketing with Hannah, the Marketing Manager at Workspace Group. Hear firsthand how their team generates engaging descriptions for thousands of office units by integrating diverse data sources—from PDF floorplans to web pages—using FME transformers, like OpenAIVisionConnector and AnthropicVisionConnector. This use case will show you how GenAI can streamline content creation for marketing across the board.
Ollama Use Case: Learn how Scenario Specialist Dmitri Bagh has utilized Ollama within FME to input data, create custom models, and enhance security protocols. This segment will include demos to illustrate the full capabilities of FME in AI-driven processes.
Custom AI Models: Discover how to leverage FME to build personalized AI models using your data. Whether it’s populating a model with local data for added security or integrating public AI tools, find out how FME facilitates a versatile and secure approach to AI.
We’ll wrap up with a live Q&A session where you can engage with our experts on your specific use cases, and learn more about optimizing your data workflows with AI.
This webinar is ideal for professionals seeking to harness the power of AI within their data management systems while ensuring high levels of customization and security. Whether you're a novice or an expert, gain actionable insights and strategies to elevate your data processes. Join us to see how FME and AI can revolutionize how you work with data!
Removing Uninteresting Bytes in Software Fuzzing

Imagine a world where software fuzzing, the process of mutating bytes in test seeds to uncover hidden and erroneous program behaviors, becomes faster and more effective. A lot depends on the initial seeds, which can significantly dictate the trajectory of a fuzzing campaign, particularly in terms of how long it takes to uncover interesting behaviour in your code. We introduce DIAR, a technique designed to speedup fuzzing campaigns by pinpointing and eliminating those uninteresting bytes in the seeds. Picture this: instead of wasting valuable resources on meaningless mutations in large, bloated seeds, DIAR removes the unnecessary bytes, streamlining the entire process.
In this work, we equipped AFL, a popular fuzzer, with DIAR and examined two critical Linux libraries -- Libxml's xmllint, a tool for parsing xml documents, and Binutil's readelf, an essential debugging and security analysis command-line tool used to display detailed information about ELF (Executable and Linkable Format). Our preliminary results show that AFL+DIAR does not only discover new paths more quickly but also achieves higher coverage overall. This work thus showcases how starting with lean and optimized seeds can lead to faster, more comprehensive fuzzing campaigns -- and DIAR helps you find such seeds.
- These are slides of the talk given at IEEE International Conference on Software Testing Verification and Validation Workshop, ICSTW 2022.
Presentation of the OECD Artificial Intelligence Review of Germany

Consult the full report at https://www.oecd.org/digital/oecd-artificial-intelligence-review-of-germany-609808d6-en.htm
Climate Impact of Software Testing at Nordic Testing Days

My slides at Nordic Testing Days 6.6.2024
Climate impact / sustainability of software testing discussed on the talk. ICT and testing must carry their part of global responsibility to help with the climat warming. We can minimize the carbon footprint but we can also have a carbon handprint, a positive impact on the climate. Quality characteristics can be added with sustainability, and then measured continuously. Test environments can be used less, and in smaller scale and on demand. Test techniques can be used in optimizing or minimizing number of tests. Test automation can be used to speed up testing.
AI-Powered Food Delivery Transforming App Development in Saudi Arabia.pdf

In this blog post, we'll delve into the intersection of AI and app development in Saudi Arabia, focusing on the food delivery sector. We'll explore how AI is revolutionizing the way Saudi consumers order food, how restaurants manage their operations, and how delivery partners navigate the bustling streets of cities like Riyadh, Jeddah, and Dammam. Through real-world case studies, we'll showcase how leading Saudi food delivery apps are leveraging AI to redefine convenience, personalization, and efficiency.
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Discover how MongoDB Atlas and vector search technology can revolutionize your application's search capabilities. This comprehensive presentation covers:
* What is Vector Search?
* Importance and benefits of vector search
* Practical use cases across various industries
* Step-by-step implementation guide
* Live demos with code snippets
* Enhancing LLM capabilities with vector search
* Best practices and optimization strategies
Perfect for developers, AI enthusiasts, and tech leaders. Learn how to leverage MongoDB Atlas to deliver highly relevant, context-aware search results, transforming your data retrieval process. Stay ahead in tech innovation and maximize the potential of your applications.
#MongoDB #VectorSearch #AI #SemanticSearch #TechInnovation #DataScience #LLM #MachineLearning #SearchTechnology
Building Production Ready Search Pipelines with Spark and Milvus

Spark is the widely used ETL tool for processing, indexing and ingesting data to serving stack for search. Milvus is the production-ready open-source vector database. In this talk we will show how to use Spark to process unstructured data to extract vector representations, and push the vectors to Milvus vector database for search serving.
20240605 QFM017 Machine Intelligence Reading List May 2024

Everything I found interesting about machines behaving intelligently during May 2024
CAKE: Sharing Slices of Confidential Data on Blockchain

Presented at the CAiSE 2024 Forum, Intelligent Information Systems, June 6th, Limassol, Cyprus.
Synopsis: Cooperative information systems typically involve various entities in a collaborative process within a distributed environment. Blockchain technology offers a mechanism for automating such processes, even when only partial trust exists among participants. The data stored on the blockchain is replicated across all nodes in the network, ensuring accessibility to all participants. While this aspect facilitates traceability, integrity, and persistence, it poses challenges for adopting public blockchains in enterprise settings due to confidentiality issues. In this paper, we present a software tool named Control Access via Key Encryption (CAKE), designed to ensure data confidentiality in scenarios involving public blockchains. After outlining its core components and functionalities, we showcase the application of CAKE in the context of a real-world cyber-security project within the logistics domain.
Paper: https://doi.org/10.1007/978-3-031-61000-4_16
“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...

“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...Edge AI and Vision Alliance
For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2024/06/building-and-scaling-ai-applications-with-the-nx-ai-manager-a-presentation-from-network-optix/
Robin van Emden, Senior Director of Data Science at Network Optix, presents the “Building and Scaling AI Applications with the Nx AI Manager,” tutorial at the May 2024 Embedded Vision Summit.
In this presentation, van Emden covers the basics of scaling edge AI solutions using the Nx tool kit. He emphasizes the process of developing AI models and deploying them globally. He also showcases the conversion of AI models and the creation of effective edge AI pipelines, with a focus on pre-processing, model conversion, selecting the appropriate inference engine for the target hardware and post-processing.
van Emden shows how Nx can simplify the developer’s life and facilitate a rapid transition from concept to production-ready applications.He provides valuable insights into developing scalable and efficient edge AI solutions, with a strong focus on practical implementation.More Related Content
More from Zaffar Ahmed Shaikh
Role of ICT in Shaping the Future of Pakistani Higher Education System

This study examined the challenges faced by the Pakistani higher education system (HES) in integrating information and communication technology (ICT); it aimed at understanding ICT needs, measuring the increase in ICT demand, determining the relationship between ICT and HES performance, and understanding how the HES copes with the challenges of implementing ICT. The results of these analyses were used as the basis to suggest solutions. The normative Delphi method was applied to evaluate a sample of 30 HES experts randomly selected from urban and rural areas of Pakistan by administering a literature-based 35-item questionnaire. The
experts revealed significant gaps in ICT demand and supply, ICT use, ICT-based higher education problems, and reasons for delays in ICT integration and provided suggestions for developing ICT-driven HES in Pakistan. This
study’s findings suggest that an effective and robust HES ICT policy could greatly improve the status of the Pakistani knowledge-based economy, thus helping establish ICT policy and planning, administration, and integration at the higher education level.
Role of Teacher in Personal Learning Environments

The aim of this paper is to discuss the changing roles and competencies of a teacher in context of prevailing developments accomplished by the vast availability of social software, which have made easy the development of Personal Learning Environments (PLEs). This has been accomplished by an in-depth review of the literature on teachers’ socially situated competencies and roles with regard to the tasks and guidance they provide to students shape their PLEs. Review process provides an insight of PLE research studies, constructivist learning theories, and teacher changing roles. The results of this study outline the roles that portray the importance of teacher competencies as role in Planning and Design, Instruction and Learning, Communication and Interaction, Management and Administration, and Use of Technology.
Presentation - Role of Teacher in Personal Learning Environments

Role of Teacher in PLEs - Presented by Zaffar Ahmed Shaikh in "The PLE Conference 2011", held during 11-13 July 2011 University of Southampton, UK.
Network Theory

This chapter will introduce you to the field of science known as Network Theory and tell you about the major researches that took place since its conceptualization. Since the course in question is social computing the chapter is written in a way to give examples and illustrations which mostly relate to social computing. It also contains theories and information which are mostly related to network theory and have some or no relation to social computing. But the basic purpose of this chapter is to explain Network theory and its applications in the field of social computing.
Introduction to Social Computing - Book Chapter

Social computing is a rapidly growing and constantly evolving technology that is aimed at increasing communication, encouraging collaboration, and enhancing productivity among people and resources. Social computing applications or Web 2.0 are built on a range of advanced and supporting technologies that enhance collective action and interaction which currently dominates the Web (Parameswaran & Whinston 2007).
Social computing applications are categorized into social media, social bookmarking, and social networks categories as identified by the continuing Web 2.0 trend (Schwartz et al. 2009; Amer-Yahia, 2009). Each of these categories has been embodied by various social software and web sites. Some of the best-known and equally famous social web sites that dominate the web are Facebook, YouTube, Twitter, Wikipedia, Delicious, and LinkedIn.
Chapter 2 Cover Updated By Zaffar Ahmed Shaikh

This document provides an introduction to network theory and its major concepts and research areas. It discusses what networks are, common network models, and seminal works that helped establish the field, including sociograms, the small world phenomenon, and theories of strong and weak social ties. Major areas of research covered include distance and effective distance between nodes, the size of interpersonal environments, degrees of separation, and how weak ties help integrate social systems. The document concludes with brief sections on network optimization and analysis.
Chapter 1 Cover Updated By Zaffar Ahmed Shaikh

This document provides an introduction to social computing, covering its history from early social software to modern applications enabled by Web 2.0 technologies. It discusses key concepts in social computing design and models of social behavior, comparing crowd sourcing to outsourcing. The document is intended to provide learning objectives on social computing topics.
Prediction Markets

The document discusses infrastructure requirements for social computing applications, including common tools like Ajax, podcasts, Yahoo Widgets, Python, and Perl. It also discusses social computing platforms like Ruby on Rails, MySQL, and Microsoft SharePoint. Microsoft SharePoint is highlighted as a platform that can be used to build eight social computing applications within one system, including features like My Sites, Team Sites, blogs, people search, wikis, community sites, announcements, and internal/external groups.
Nearest Neighbor Algorithm Zaffar Ahmed

The document summarizes the K-nearest neighbor (KNN) algorithm. KNN is a memory-based algorithm that finds the K training samples nearest to a query point and predicts the query's classification based on the majority classification of its neighbors. The summary explains:
1) KNN measures the distance between query points and training samples to classify new objects based on the majority category of its K nearest neighbors.
2) To make a prediction, KNN determines K, calculates distances between the query and all training points, identifies the K nearest neighbors, collects their classifications, and predicts the query's classification based on the majority of its neighbors.
3) An example is given where KNN predicts the winner of an
Social Computing Applications Infrastructure

The document discusses infrastructure requirements for social computing applications, including common tools like Ajax, podcasts, Yahoo Widgets, Python, and Perl. It also discusses social computing platforms like Ruby on Rails, MySQL, and Microsoft SharePoint. Microsoft SharePoint is highlighted as a platform that can be used to build eight social computing applications within one system, including features like My Sites, Team Sites, blogs, people search, wikis, community sites, announcements, and internal/external groups.
Zaffar+Ahmed+ +Collaborative+Filtering

Collaborative filtering analyzes data from multiple sources to develop profiles of people with similar tastes. It finds similarities between users based on their preferences and provides recommendations based on the preferences of similar users. Collaborative filtering requires a large amount of stored user data to make reliable recommendations, and the more users in the population, the more useful the recommendations will be. However, with small datasets it can produce false connections or poor predictions.
More from Zaffar Ahmed Shaikh (11)
Role of ICT in Shaping the Future of Pakistani Higher Education System

Role of ICT in Shaping the Future of Pakistani Higher Education System
Presentation - Role of Teacher in Personal Learning Environments

Presentation - Role of Teacher in Personal Learning Environments
Recently uploaded
OpenID AuthZEN Interop Read Out - Authorization

During Identiverse 2024 and EIC 2024, members of the OpenID AuthZEN WG got together and demoed their authorization endpoints conforming to the AuthZEN API
Driving Business Innovation: Latest Generative AI Advancements & Success Story

Are you ready to revolutionize how you handle data? Join us for a webinar where we’ll bring you up to speed with the latest advancements in Generative AI technology and discover how leveraging FME with tools from giants like Google Gemini, Amazon, and Microsoft OpenAI can supercharge your workflow efficiency.
During the hour, we’ll take you through:
Guest Speaker Segment with Hannah Barrington: Dive into the world of dynamic real estate marketing with Hannah, the Marketing Manager at Workspace Group. Hear firsthand how their team generates engaging descriptions for thousands of office units by integrating diverse data sources—from PDF floorplans to web pages—using FME transformers, like OpenAIVisionConnector and AnthropicVisionConnector. This use case will show you how GenAI can streamline content creation for marketing across the board.
Ollama Use Case: Learn how Scenario Specialist Dmitri Bagh has utilized Ollama within FME to input data, create custom models, and enhance security protocols. This segment will include demos to illustrate the full capabilities of FME in AI-driven processes.
Custom AI Models: Discover how to leverage FME to build personalized AI models using your data. Whether it’s populating a model with local data for added security or integrating public AI tools, find out how FME facilitates a versatile and secure approach to AI.
We’ll wrap up with a live Q&A session where you can engage with our experts on your specific use cases, and learn more about optimizing your data workflows with AI.
This webinar is ideal for professionals seeking to harness the power of AI within their data management systems while ensuring high levels of customization and security. Whether you're a novice or an expert, gain actionable insights and strategies to elevate your data processes. Join us to see how FME and AI can revolutionize how you work with data!
Removing Uninteresting Bytes in Software Fuzzing

Imagine a world where software fuzzing, the process of mutating bytes in test seeds to uncover hidden and erroneous program behaviors, becomes faster and more effective. A lot depends on the initial seeds, which can significantly dictate the trajectory of a fuzzing campaign, particularly in terms of how long it takes to uncover interesting behaviour in your code. We introduce DIAR, a technique designed to speedup fuzzing campaigns by pinpointing and eliminating those uninteresting bytes in the seeds. Picture this: instead of wasting valuable resources on meaningless mutations in large, bloated seeds, DIAR removes the unnecessary bytes, streamlining the entire process.
In this work, we equipped AFL, a popular fuzzer, with DIAR and examined two critical Linux libraries -- Libxml's xmllint, a tool for parsing xml documents, and Binutil's readelf, an essential debugging and security analysis command-line tool used to display detailed information about ELF (Executable and Linkable Format). Our preliminary results show that AFL+DIAR does not only discover new paths more quickly but also achieves higher coverage overall. This work thus showcases how starting with lean and optimized seeds can lead to faster, more comprehensive fuzzing campaigns -- and DIAR helps you find such seeds.
- These are slides of the talk given at IEEE International Conference on Software Testing Verification and Validation Workshop, ICSTW 2022.
Presentation of the OECD Artificial Intelligence Review of Germany

Consult the full report at https://www.oecd.org/digital/oecd-artificial-intelligence-review-of-germany-609808d6-en.htm
Climate Impact of Software Testing at Nordic Testing Days

My slides at Nordic Testing Days 6.6.2024
Climate impact / sustainability of software testing discussed on the talk. ICT and testing must carry their part of global responsibility to help with the climat warming. We can minimize the carbon footprint but we can also have a carbon handprint, a positive impact on the climate. Quality characteristics can be added with sustainability, and then measured continuously. Test environments can be used less, and in smaller scale and on demand. Test techniques can be used in optimizing or minimizing number of tests. Test automation can be used to speed up testing.
AI-Powered Food Delivery Transforming App Development in Saudi Arabia.pdf

In this blog post, we'll delve into the intersection of AI and app development in Saudi Arabia, focusing on the food delivery sector. We'll explore how AI is revolutionizing the way Saudi consumers order food, how restaurants manage their operations, and how delivery partners navigate the bustling streets of cities like Riyadh, Jeddah, and Dammam. Through real-world case studies, we'll showcase how leading Saudi food delivery apps are leveraging AI to redefine convenience, personalization, and efficiency.
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Discover how MongoDB Atlas and vector search technology can revolutionize your application's search capabilities. This comprehensive presentation covers:
* What is Vector Search?
* Importance and benefits of vector search
* Practical use cases across various industries
* Step-by-step implementation guide
* Live demos with code snippets
* Enhancing LLM capabilities with vector search
* Best practices and optimization strategies
Perfect for developers, AI enthusiasts, and tech leaders. Learn how to leverage MongoDB Atlas to deliver highly relevant, context-aware search results, transforming your data retrieval process. Stay ahead in tech innovation and maximize the potential of your applications.
#MongoDB #VectorSearch #AI #SemanticSearch #TechInnovation #DataScience #LLM #MachineLearning #SearchTechnology
Building Production Ready Search Pipelines with Spark and Milvus

Spark is the widely used ETL tool for processing, indexing and ingesting data to serving stack for search. Milvus is the production-ready open-source vector database. In this talk we will show how to use Spark to process unstructured data to extract vector representations, and push the vectors to Milvus vector database for search serving.
20240605 QFM017 Machine Intelligence Reading List May 2024

Everything I found interesting about machines behaving intelligently during May 2024
CAKE: Sharing Slices of Confidential Data on Blockchain

Presented at the CAiSE 2024 Forum, Intelligent Information Systems, June 6th, Limassol, Cyprus.
Synopsis: Cooperative information systems typically involve various entities in a collaborative process within a distributed environment. Blockchain technology offers a mechanism for automating such processes, even when only partial trust exists among participants. The data stored on the blockchain is replicated across all nodes in the network, ensuring accessibility to all participants. While this aspect facilitates traceability, integrity, and persistence, it poses challenges for adopting public blockchains in enterprise settings due to confidentiality issues. In this paper, we present a software tool named Control Access via Key Encryption (CAKE), designed to ensure data confidentiality in scenarios involving public blockchains. After outlining its core components and functionalities, we showcase the application of CAKE in the context of a real-world cyber-security project within the logistics domain.
Paper: https://doi.org/10.1007/978-3-031-61000-4_16
“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...

“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...Edge AI and Vision Alliance
For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2024/06/building-and-scaling-ai-applications-with-the-nx-ai-manager-a-presentation-from-network-optix/
Robin van Emden, Senior Director of Data Science at Network Optix, presents the “Building and Scaling AI Applications with the Nx AI Manager,” tutorial at the May 2024 Embedded Vision Summit.
In this presentation, van Emden covers the basics of scaling edge AI solutions using the Nx tool kit. He emphasizes the process of developing AI models and deploying them globally. He also showcases the conversion of AI models and the creation of effective edge AI pipelines, with a focus on pre-processing, model conversion, selecting the appropriate inference engine for the target hardware and post-processing.
van Emden shows how Nx can simplify the developer’s life and facilitate a rapid transition from concept to production-ready applications.He provides valuable insights into developing scalable and efficient edge AI solutions, with a strong focus on practical implementation.Video Streaming: Then, Now, and in the Future

In his public lecture, Christian Timmerer provides insights into the fascinating history of video streaming, starting from its humble beginnings before YouTube to the groundbreaking technologies that now dominate platforms like Netflix and ORF ON. Timmerer also presents provocative contributions of his own that have significantly influenced the industry. He concludes by looking at future challenges and invites the audience to join in a discussion.
20240607 QFM018 Elixir Reading List May 2024

Everything I found interesting about the Elixir programming ecosystem in May 2024
GraphRAG for Life Science to increase LLM accuracy

GraphRAG for life science domain, where you retriever information from biomedical knowledge graphs using LLMs to increase the accuracy and performance of generated answers
Best 20 SEO Techniques To Improve Website Visibility In SERP

Boost your website's visibility with proven SEO techniques! Our latest blog dives into essential strategies to enhance your online presence, increase traffic, and rank higher on search engines. From keyword optimization to quality content creation, learn how to make your site stand out in the crowded digital landscape. Discover actionable tips and expert insights to elevate your SEO game.
Monitoring and Managing Anomaly Detection on OpenShift.pdf

Monitoring and Managing Anomaly Detection on OpenShift
Overview
Dive into the world of anomaly detection on edge devices with our comprehensive hands-on tutorial. This SlideShare presentation will guide you through the entire process, from data collection and model training to edge deployment and real-time monitoring. Perfect for those looking to implement robust anomaly detection systems on resource-constrained IoT/edge devices.
Key Topics Covered
1. Introduction to Anomaly Detection
- Understand the fundamentals of anomaly detection and its importance in identifying unusual behavior or failures in systems.
2. Understanding Edge (IoT)
- Learn about edge computing and IoT, and how they enable real-time data processing and decision-making at the source.
3. What is ArgoCD?
- Discover ArgoCD, a declarative, GitOps continuous delivery tool for Kubernetes, and its role in deploying applications on edge devices.
4. Deployment Using ArgoCD for Edge Devices
- Step-by-step guide on deploying anomaly detection models on edge devices using ArgoCD.
5. Introduction to Apache Kafka and S3
- Explore Apache Kafka for real-time data streaming and Amazon S3 for scalable storage solutions.
6. Viewing Kafka Messages in the Data Lake
- Learn how to view and analyze Kafka messages stored in a data lake for better insights.
7. What is Prometheus?
- Get to know Prometheus, an open-source monitoring and alerting toolkit, and its application in monitoring edge devices.
8. Monitoring Application Metrics with Prometheus
- Detailed instructions on setting up Prometheus to monitor the performance and health of your anomaly detection system.
9. What is Camel K?
- Introduction to Camel K, a lightweight integration framework built on Apache Camel, designed for Kubernetes.
10. Configuring Camel K Integrations for Data Pipelines
- Learn how to configure Camel K for seamless data pipeline integrations in your anomaly detection workflow.
11. What is a Jupyter Notebook?
- Overview of Jupyter Notebooks, an open-source web application for creating and sharing documents with live code, equations, visualizations, and narrative text.
12. Jupyter Notebooks with Code Examples
- Hands-on examples and code snippets in Jupyter Notebooks to help you implement and test anomaly detection models.
HCL Notes and Domino License Cost Reduction in the World of DLAU

Webinar Recording: https://www.panagenda.com/webinars/hcl-notes-and-domino-license-cost-reduction-in-the-world-of-dlau/
The introduction of DLAU and the CCB & CCX licensing model caused quite a stir in the HCL community. As a Notes and Domino customer, you may have faced challenges with unexpected user counts and license costs. You probably have questions on how this new licensing approach works and how to benefit from it. Most importantly, you likely have budget constraints and want to save money where possible. Don’t worry, we can help with all of this!
We’ll show you how to fix common misconfigurations that cause higher-than-expected user counts, and how to identify accounts which you can deactivate to save money. There are also frequent patterns that can cause unnecessary cost, like using a person document instead of a mail-in for shared mailboxes. We’ll provide examples and solutions for those as well. And naturally we’ll explain the new licensing model.
Join HCL Ambassador Marc Thomas in this webinar with a special guest appearance from Franz Walder. It will give you the tools and know-how to stay on top of what is going on with Domino licensing. You will be able lower your cost through an optimized configuration and keep it low going forward.
These topics will be covered
- Reducing license cost by finding and fixing misconfigurations and superfluous accounts
- How do CCB and CCX licenses really work?
- Understanding the DLAU tool and how to best utilize it
- Tips for common problem areas, like team mailboxes, functional/test users, etc
- Practical examples and best practices to implement right away
Artificial Intelligence for XMLDevelopment

In the rapidly evolving landscape of technologies, XML continues to play a vital role in structuring, storing, and transporting data across diverse systems. The recent advancements in artificial intelligence (AI) present new methodologies for enhancing XML development workflows, introducing efficiency, automation, and intelligent capabilities. This presentation will outline the scope and perspective of utilizing AI in XML development. The potential benefits and the possible pitfalls will be highlighted, providing a balanced view of the subject.
We will explore the capabilities of AI in understanding XML markup languages and autonomously creating structured XML content. Additionally, we will examine the capacity of AI to enrich plain text with appropriate XML markup. Practical examples and methodological guidelines will be provided to elucidate how AI can be effectively prompted to interpret and generate accurate XML markup.
Further emphasis will be placed on the role of AI in developing XSLT, or schemas such as XSD and Schematron. We will address the techniques and strategies adopted to create prompts for generating code, explaining code, or refactoring the code, and the results achieved.
The discussion will extend to how AI can be used to transform XML content. In particular, the focus will be on the use of AI XPath extension functions in XSLT, Schematron, Schematron Quick Fixes, or for XML content refactoring.
The presentation aims to deliver a comprehensive overview of AI usage in XML development, providing attendees with the necessary knowledge to make informed decisions. Whether you’re at the early stages of adopting AI or considering integrating it in advanced XML development, this presentation will cover all levels of expertise.
By highlighting the potential advantages and challenges of integrating AI with XML development tools and languages, the presentation seeks to inspire thoughtful conversation around the future of XML development. We’ll not only delve into the technical aspects of AI-powered XML development but also discuss practical implications and possible future directions.
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Discover the seamless integration of RPA (Robotic Process Automation), COMPOSER, and APM with AWS IDP enhanced with Slack notifications. Explore how these technologies converge to streamline workflows, optimize performance, and ensure secure access, all while leveraging the power of AWS IDP and real-time communication via Slack notifications.
Recently uploaded (20)
Driving Business Innovation: Latest Generative AI Advancements & Success Story

Driving Business Innovation: Latest Generative AI Advancements & Success Story
Presentation of the OECD Artificial Intelligence Review of Germany

Presentation of the OECD Artificial Intelligence Review of Germany
Climate Impact of Software Testing at Nordic Testing Days

Climate Impact of Software Testing at Nordic Testing Days
AI-Powered Food Delivery Transforming App Development in Saudi Arabia.pdf

AI-Powered Food Delivery Transforming App Development in Saudi Arabia.pdf
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf
Building Production Ready Search Pipelines with Spark and Milvus

Building Production Ready Search Pipelines with Spark and Milvus
20240605 QFM017 Machine Intelligence Reading List May 2024

20240605 QFM017 Machine Intelligence Reading List May 2024
CAKE: Sharing Slices of Confidential Data on Blockchain

CAKE: Sharing Slices of Confidential Data on Blockchain
“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...

“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...
GraphRAG for Life Science to increase LLM accuracy

GraphRAG for Life Science to increase LLM accuracy
Best 20 SEO Techniques To Improve Website Visibility In SERP

Best 20 SEO Techniques To Improve Website Visibility In SERP
Monitoring and Managing Anomaly Detection on OpenShift.pdf

Monitoring and Managing Anomaly Detection on OpenShift.pdf
HCL Notes and Domino License Cost Reduction in the World of DLAU

HCL Notes and Domino License Cost Reduction in the World of DLAU
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack
Trust Based Recommendation Systems For Tourism System Zaffar Ahmed Shaikh
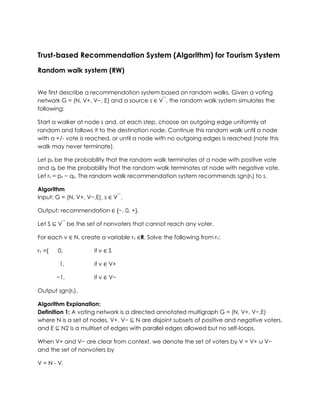
- 1. Trust-based Recommendation System (Algorithm) for Tourism System<br />Random walk system (RW)<br />We first describe a recommendation system based on random walks. Given a voting network G = (N, V+, V−, E) and a source s ∈ V‾, the random walk system simulates the following: <br />Start a walker at node s and, at each step, choose an outgoing edge uniformly at random and follows it to the destination node. Continue this random walk until a node with a +/- vote is reached, or until a node with no outgoing edges is reached (note this walk may never terminate). <br />Let ps be the probability that the random walk terminates at a node with positive vote and qs be the probability that the random walk terminates at node with negative vote. Let rs = ps − qs. The random walk recommendation system recommends sgn(rs) to s. <br />Algorithm<br />Input: G = (N, V+, V−,E), s ∈ V‾.<br />Output: recommendation ∈ {−, 0, +}.<br />Let S ⊆ V‾ be the set of nonvoters that cannot reach any voter.<br />For each v ∈ N, create a variable rv ∈R. Solve the following from rv:<br />rv ={ 0, if v ∈ S<br /> 1, if v ∈ V+<br />−1, if v ∈ V−<br />Output sgn(rs).<br />Algorithm Explanation:<br />Definition 1: A voting network is a directed annotated multigraph G = (N, V+, V−,E) where N is a set of nodes, V+, V− ⊆ N are disjoint subsets of positive and negative voters, and E ⊆ N2 is a multiset of edges with parallel edges allowed but no self-loops.<br />When V+ and V− are clear from context, we denote the set of voters by V = V+ ∪ V− and the set of nonvoters by<br />V = N - V. <br />Definition 2: A recommendation system R takes as input a voting network G and source s ∈ V and outputs recommendation R(G, s) ∈ {−, 0,+}.<br />We denote by sgn: R -> {−, 0,+} the function that computes the sign of its input. <br />Given a multiset of recommendations, S ⊆ {−, 0,+}, we define the majority MAJ(S) to be: + if more than half the elements of S are +; − if more than half of S are −; and 0 otherwise.<br />Reference: Reid Andersen, Christian Borgs, Jennifer Chayes, Uriel Feige, Abraham Flaxman, Adam Kalai, Vahab Mirrokni, and Moshe Tennenholtz, Trust-based recommendation systems: an axiomatic approach, WWW '08: Proceeding of the 17th international conference on World Wide Web (New York, NY, USA), ACM, 2008, pp. 199-208.<br />
