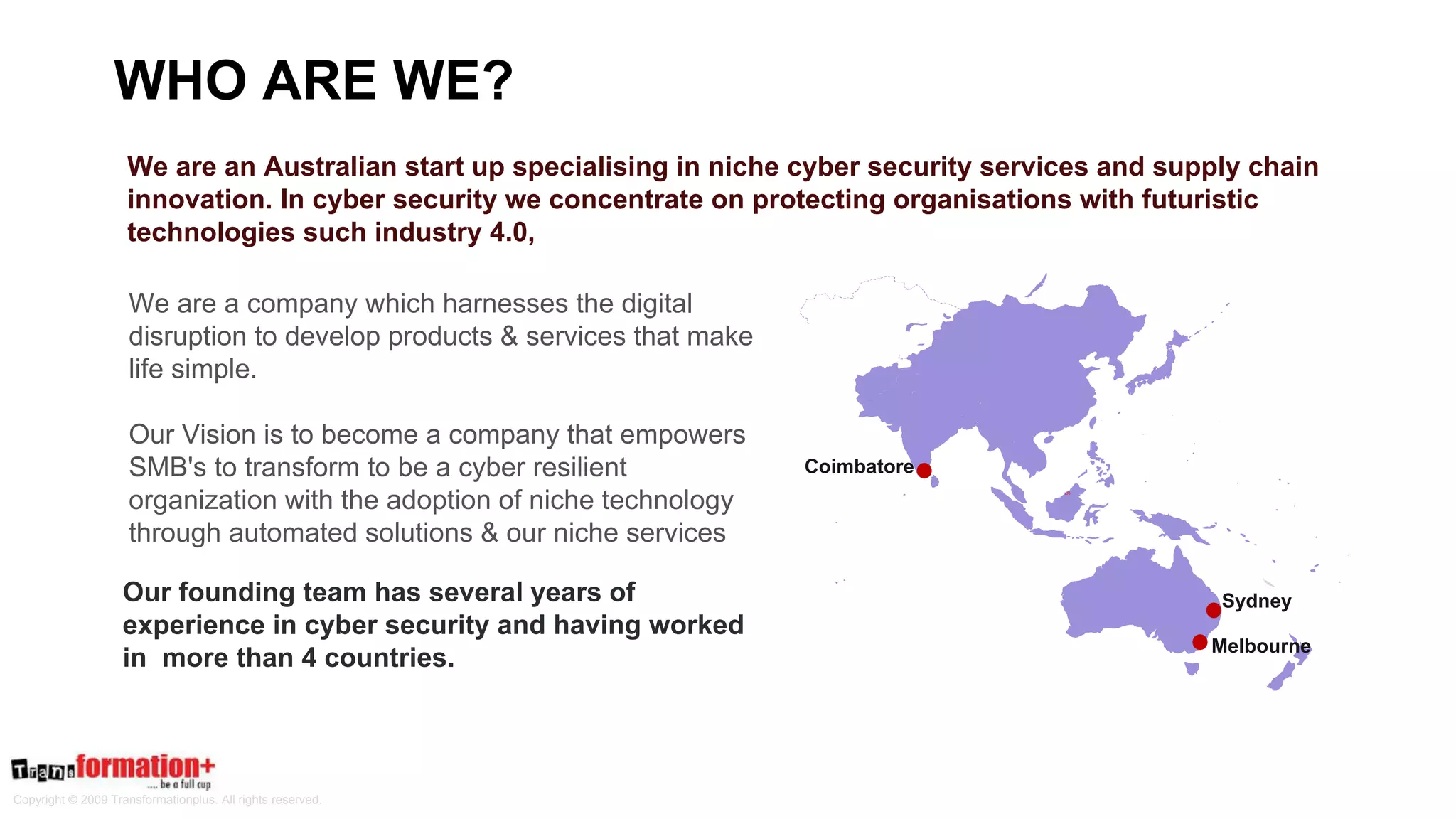
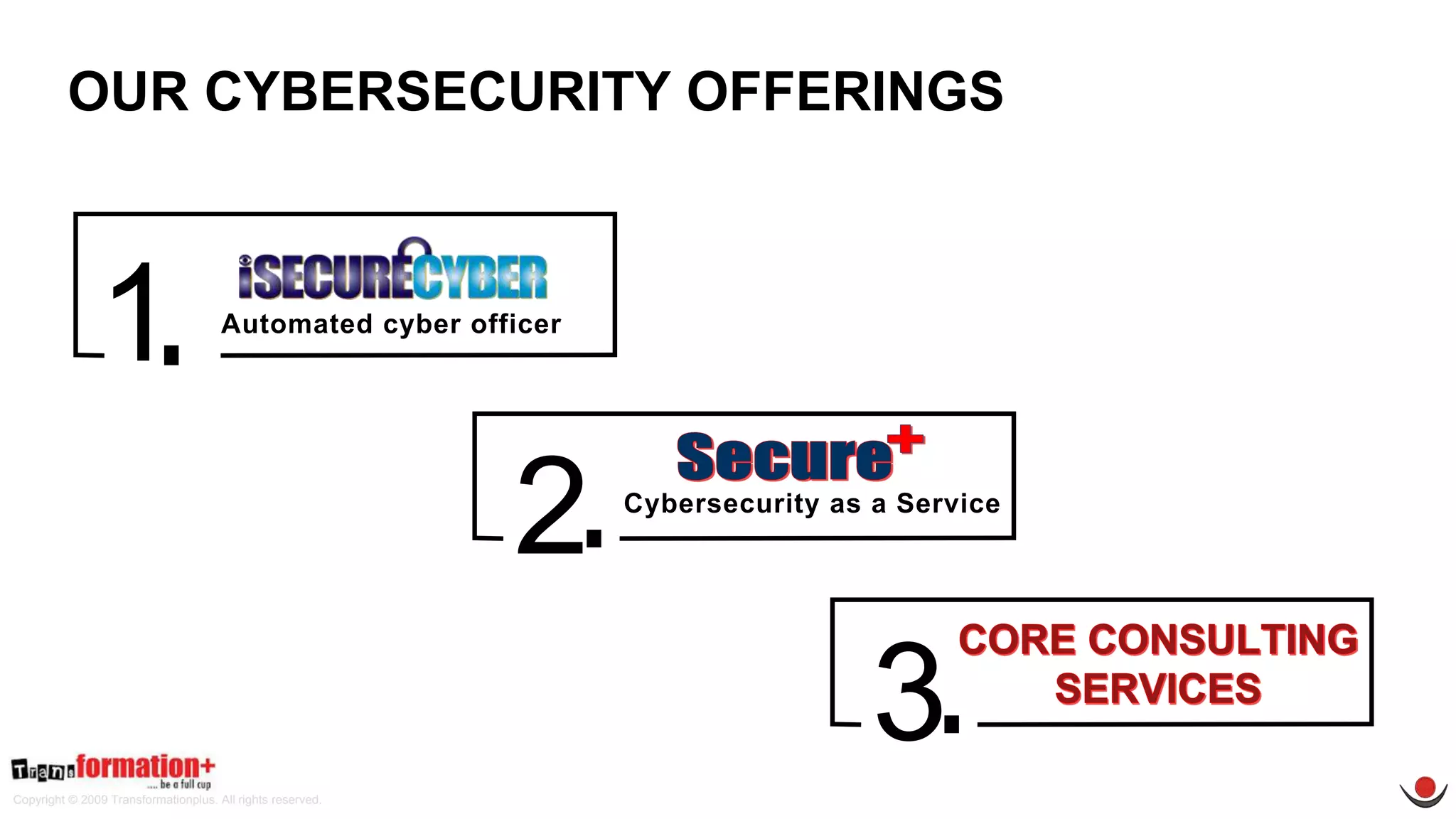
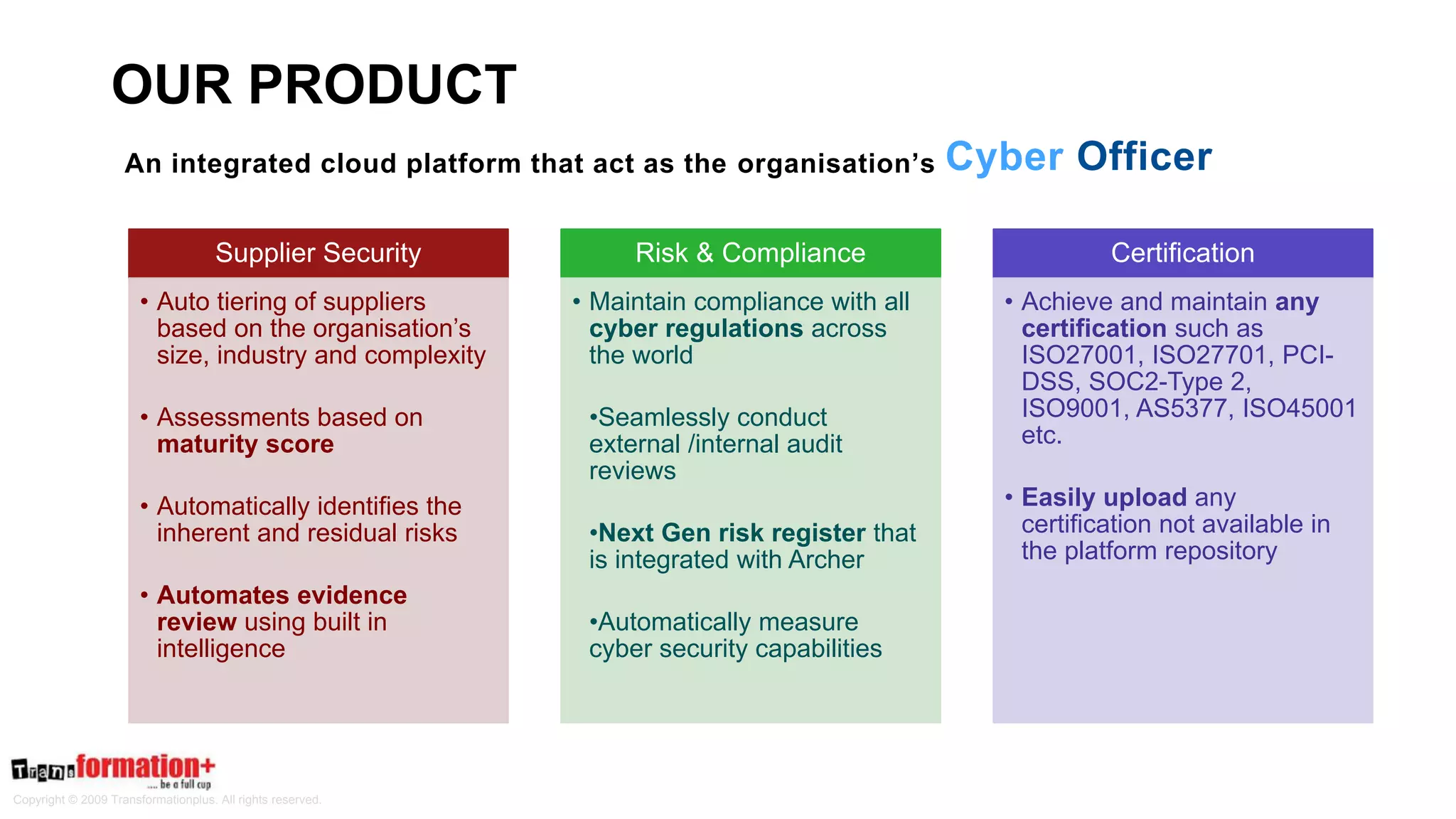
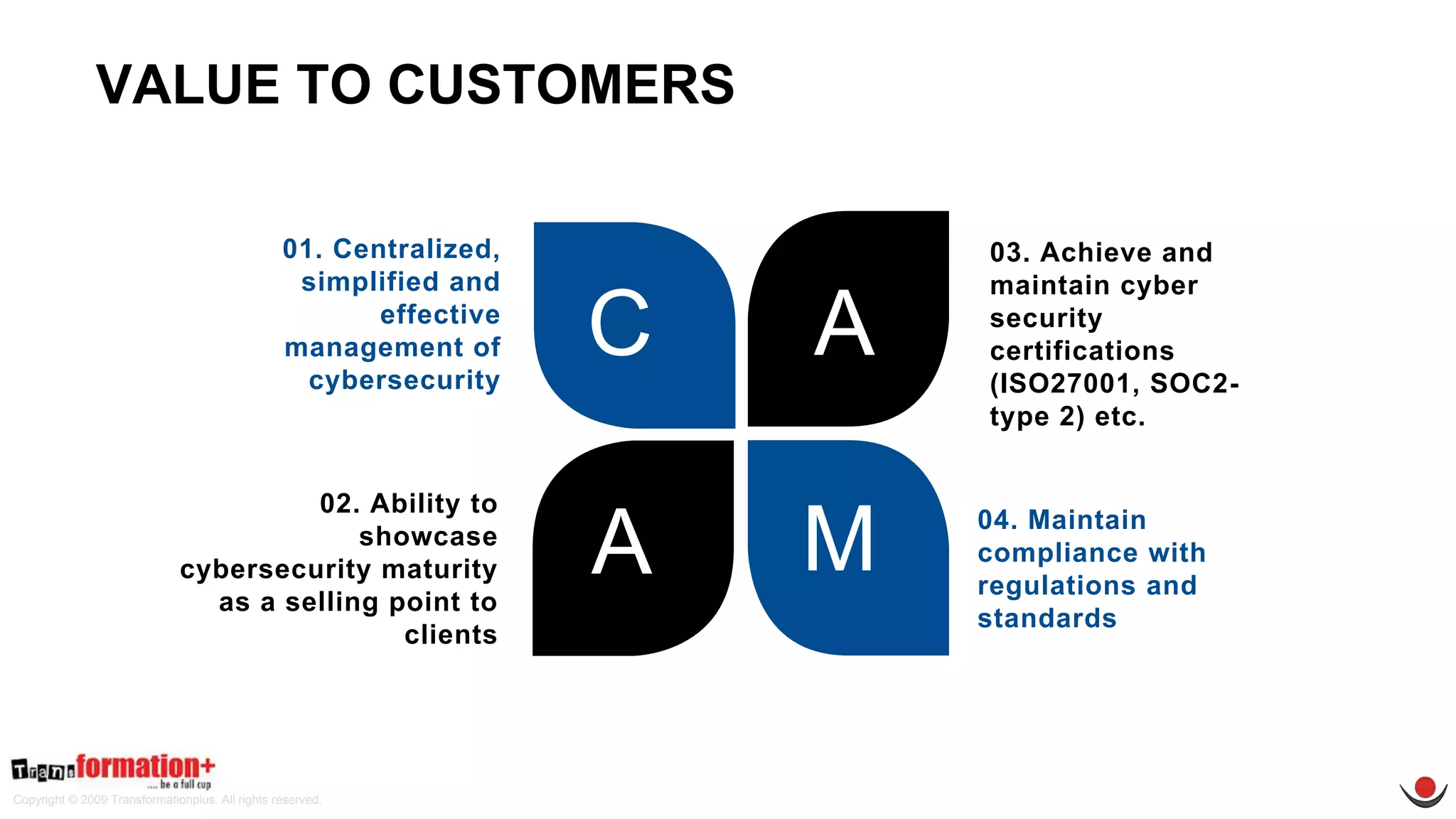
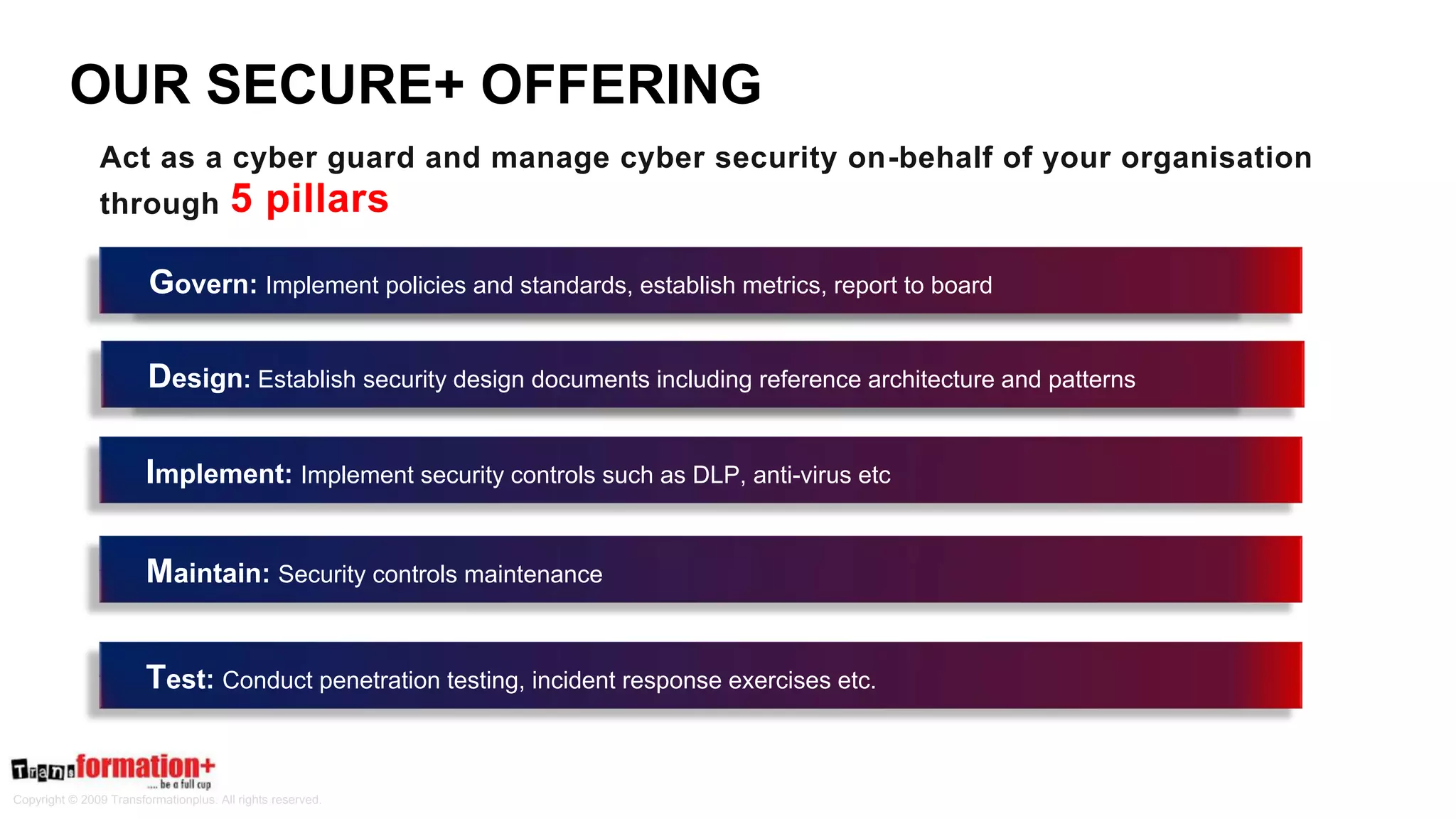
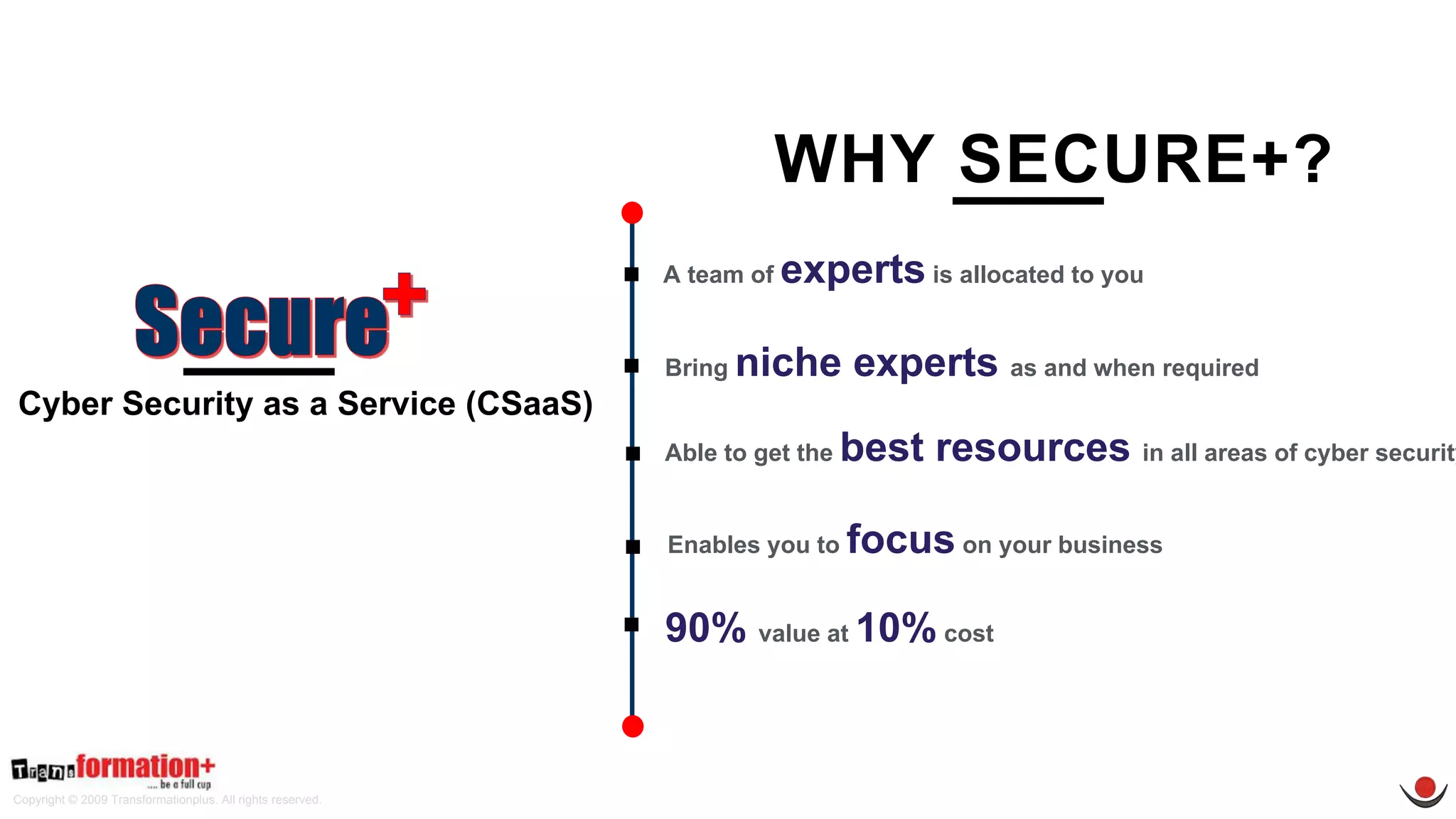
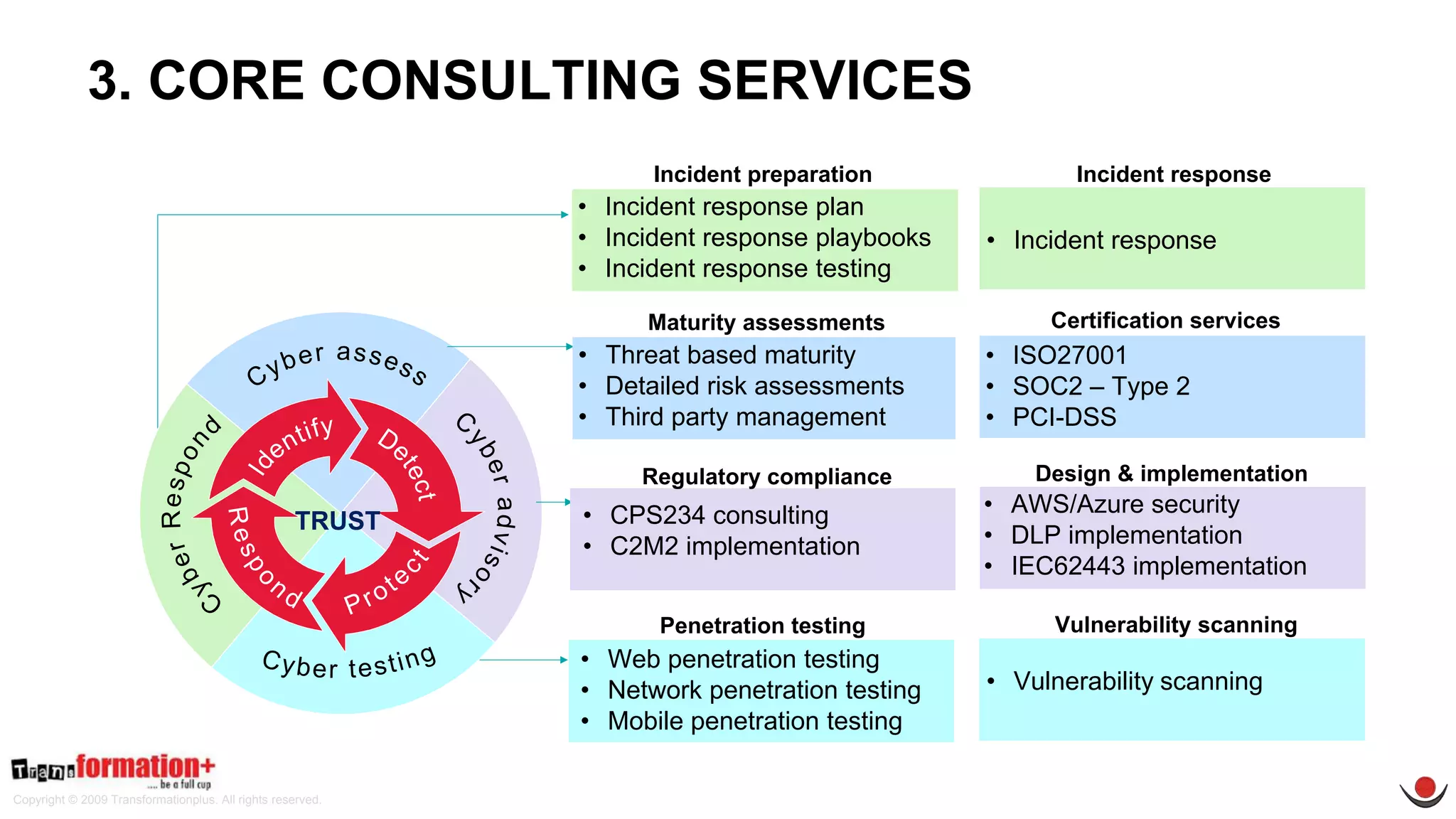
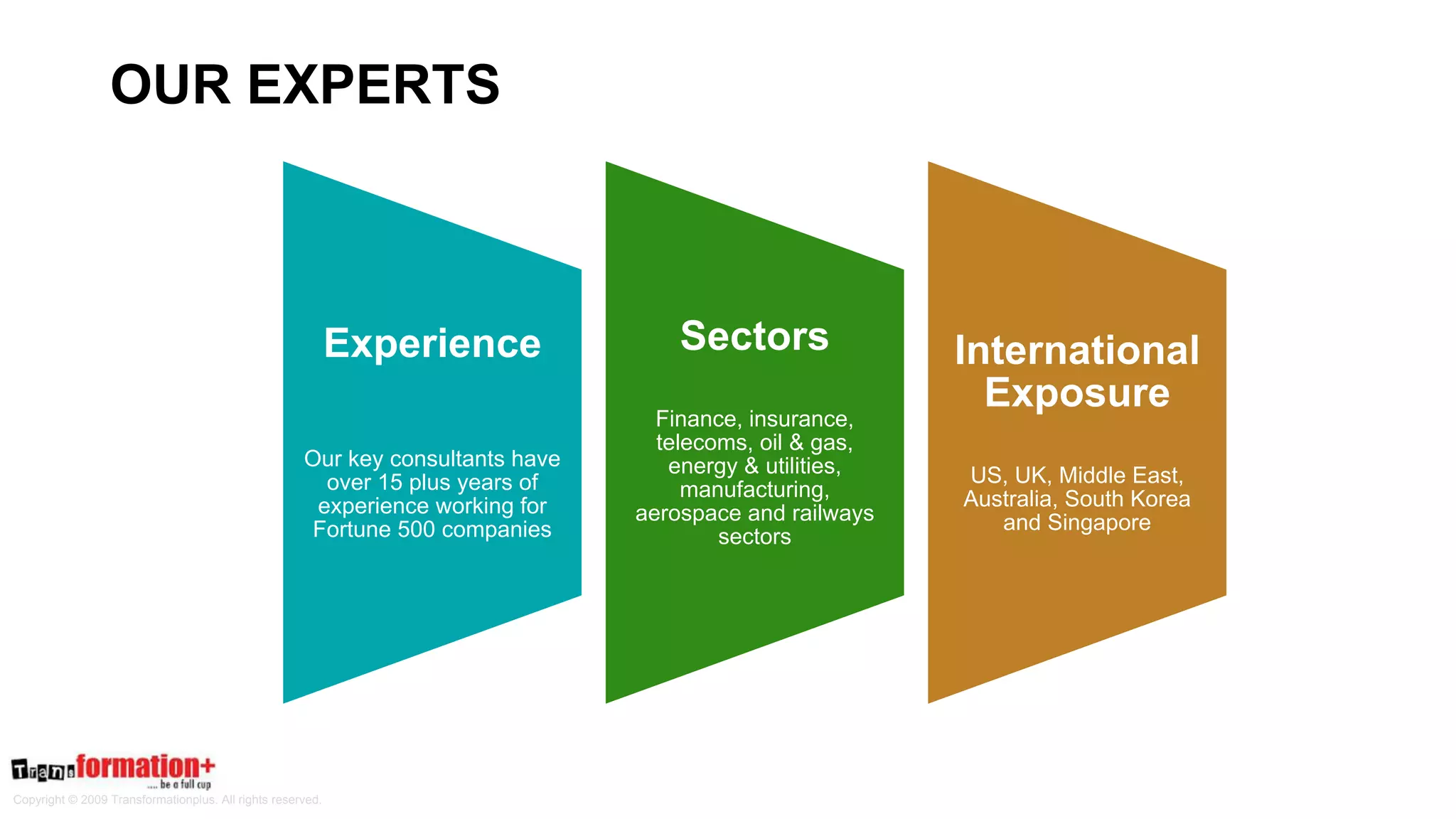
This document summarizes the cybersecurity offerings of Transformationplus, an Australian startup specializing in cybersecurity services and supply chain innovation. It describes an automated cyber officer product that acts as an organization's cybersecurity officer, managing supplier security assessments, risk and compliance, and certifications. It also describes a cybersecurity as a service offering called Secure+ that manages cybersecurity through governance, design, implementation, maintenance, and testing for clients. The document provides information on the company's experts, accreditations, testimonials, and contact information.