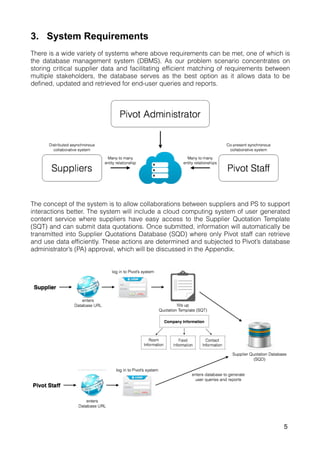
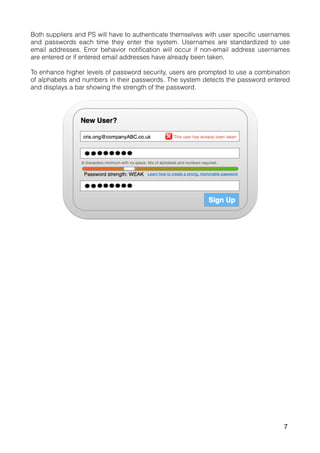
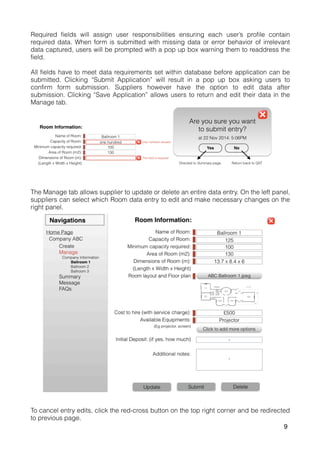
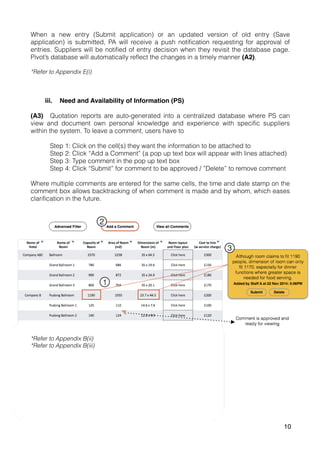
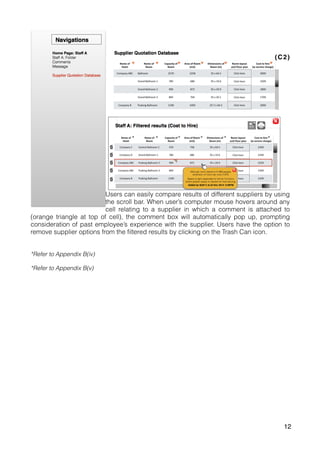
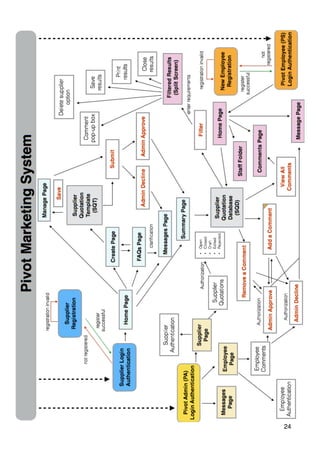
The document outlines a proposal for a database management system to improve Pivot Marketing's project management and supplier information retention, addressing issues like inefficient supplier matching and data collection. It details system requirements to automate data entry and access, streamline user interactions, and preserve valuable past knowledge. A SWOT analysis is included, identifying the strengths, weaknesses, opportunities, and threats associated with implementing the proposed system.



















![Bibliography
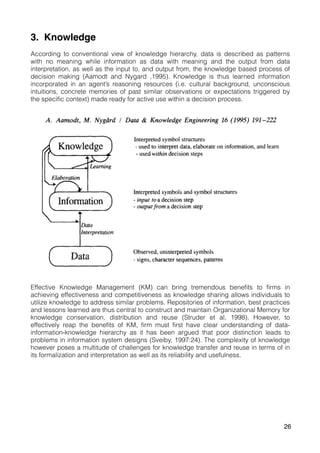
Aamodt, A. and Nygård, M. (1995). Different roles and mutual dependencies of data, information,
and knowledge — An AI perspective on their integration. Data & Knowledge Engineering,
16(3), pp.191-222.
Carroll, J., Rosson, M., Chin, G. and Koenemann, J. (1998). Requirements development in
scenario-based design. IIEEE Trans. Software Eng., 24(12), pp.1156-1170.
Connell, N., Klein, J. and Powell, P. (2003). It's tacit knowledge but not as we know it: redirecting
the search for knowledge. Journal of the Operational Research Society, 54(2), pp.140-152.
Fayyad, U., Shapiro, G. and Smyth, P. (1996). 1st ed. [ebook] pp.82-88. Available at: http://
www.aaai.org/Papers/KDD/1996/KDD96-014 [Accessed 4 Dec. 2014].
Fernandez, I. and Sabherwal, R. (2014). Organizational Knowledge Management: A Contingency
Perspective. Journal of Management Information Systems, 18(1), pp.23-55.
Heiser, J. (2009). What you need to know about cloud computing security and compliance,
Gartner, Research, ID Number: G00168345, 2009.
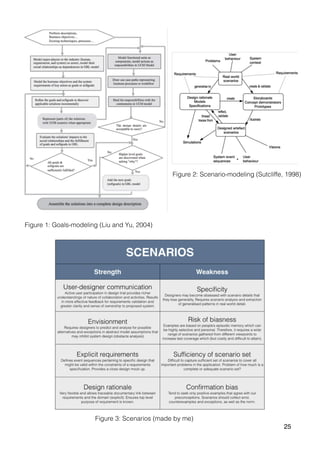
Liu, L. and Yu, E. (2004). Designing information systems in social context: a goal and scenario
modelling approach. Information Systems, 29(2), pp.187-203.
Markus, M. (2014). Toward a Theory of Knowledge Reuse: Types of Knowledge Reuse Situations
and Factors in Reuse Success. Journal of Management Information Systems, 18(1), pp.
57-93.
Nonaka, I. (1994). A Dynamic Theory of Organizational Knowledge Creation. Organization
Science, 5(1), pp.14-37.
Nonaka, I. and H. Takeuchi (1995). The Knowledge- Creating Company: How Japanese
Companies Create the Dynamics of Innovation. Oxford University Press, Oxford.
Nonaka, I. and von Krogh, G. (2009). Perspective—Tacit Knowledge and Knowledge Conversion:
Controversy and Advancement in Organizational Knowledge Creation Theory. Organization
Science, 20(3), pp.635-652.
Pearson. 2009. Taking account of privacy when designing cloud computing services.
InProceedings of the 2009 ICSE Workshop on Software Engineering Challenges of
Cloud Computing(CLOUD '09). IEEE Computer Society, Washington, DC, USA, 44-52.
doi=10.1109/cloud.2009.5071532 http://dx.doi.org/10.1109/CLOUD.2009.5071532
Sambamurthy, V. and Subramani, M. (2014). Special Issue on Information Technologies and
Knowledge Management. MIS Quarterly, 29(1), pp.1-7.
Santos, N., Gummadi, K. P. & Rodrigues, R. (2009). Towards Trusted Cloud
Computing, accessed 30 September 2011, URL:
http://www.mpi-sws.org/~gummadi/papers/trusted_cloud.pdf
Studer, R., Benjamins, V. and Fensel, D. (1998). Knowledge engineering: Principles and
methods. Data & Knowledge Engineering, 25(1-2), pp.161-197.
Subashini, S. and Kavitha, V. (2011). A survey on security issues in service delivery models of
cloud computing. Journal of Network and Computer Applications, 34(1), pp.1-11.
Sutcliffe, A. (1998). Scenario-based requirements analysis. Requirements Engineering, 3(1), pp.
48-65.
28](https://image.slidesharecdn.com/technologyinnovation-userexperienceinbusinessdatabasesystems-170225165027/85/Technology-Innovation-User-Experience-in-Business-Database-Systems-28-320.jpg)
