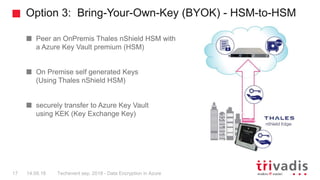
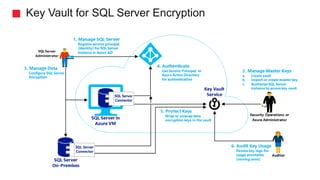
This document discusses data encryption in Azure. It covers Azure Key Vault for key management, which allows users to securely store and control encryption keys. It also describes the different key management options with Azure Key Vault, including using Microsoft-managed keys, customer-managed keys, and bringing your own keys via hardware security modules. Several encryption scenarios are presented, such as encrypting storage services, performing key rotation, and using Key Vault for SQL Server encryption.