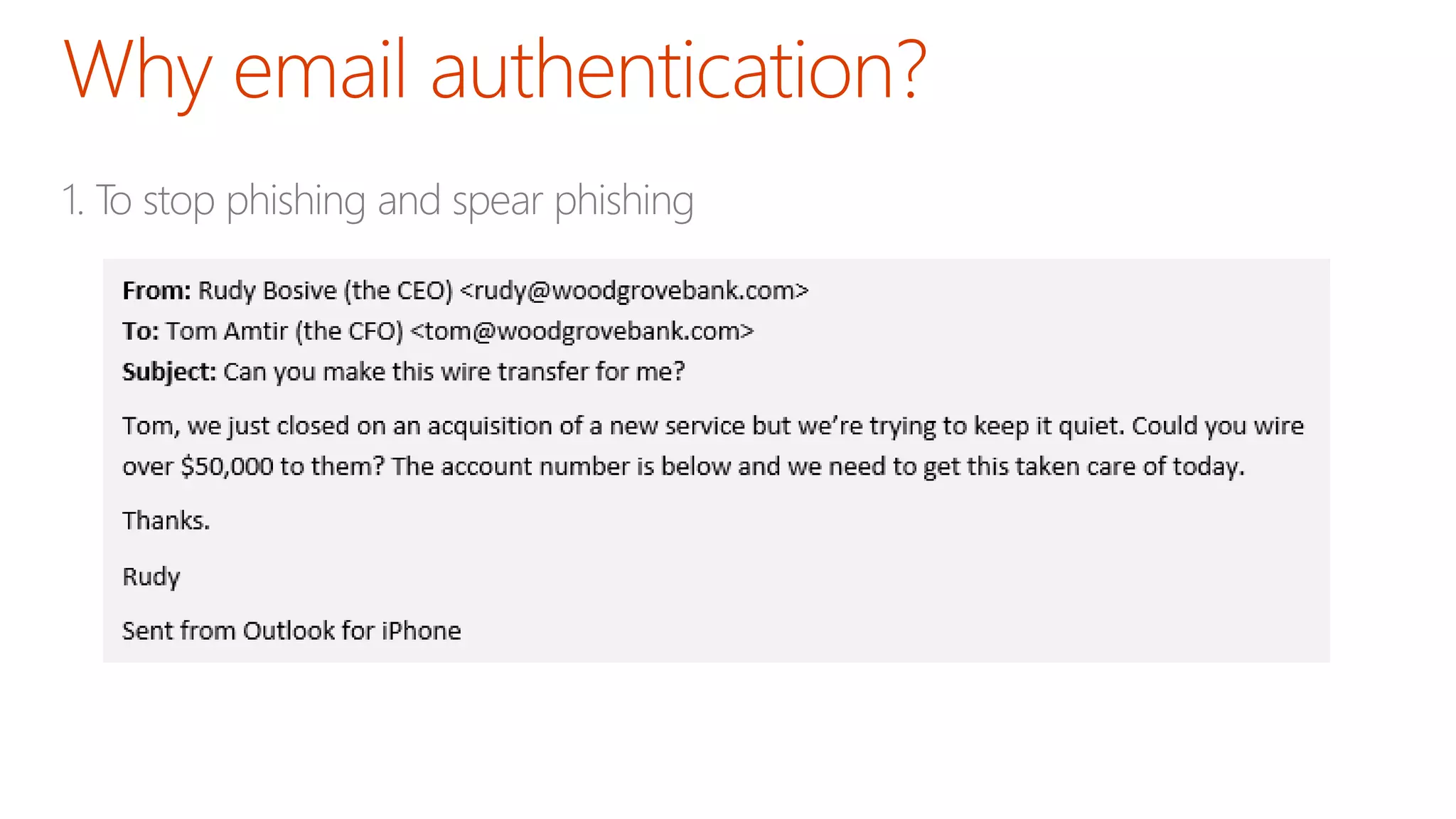
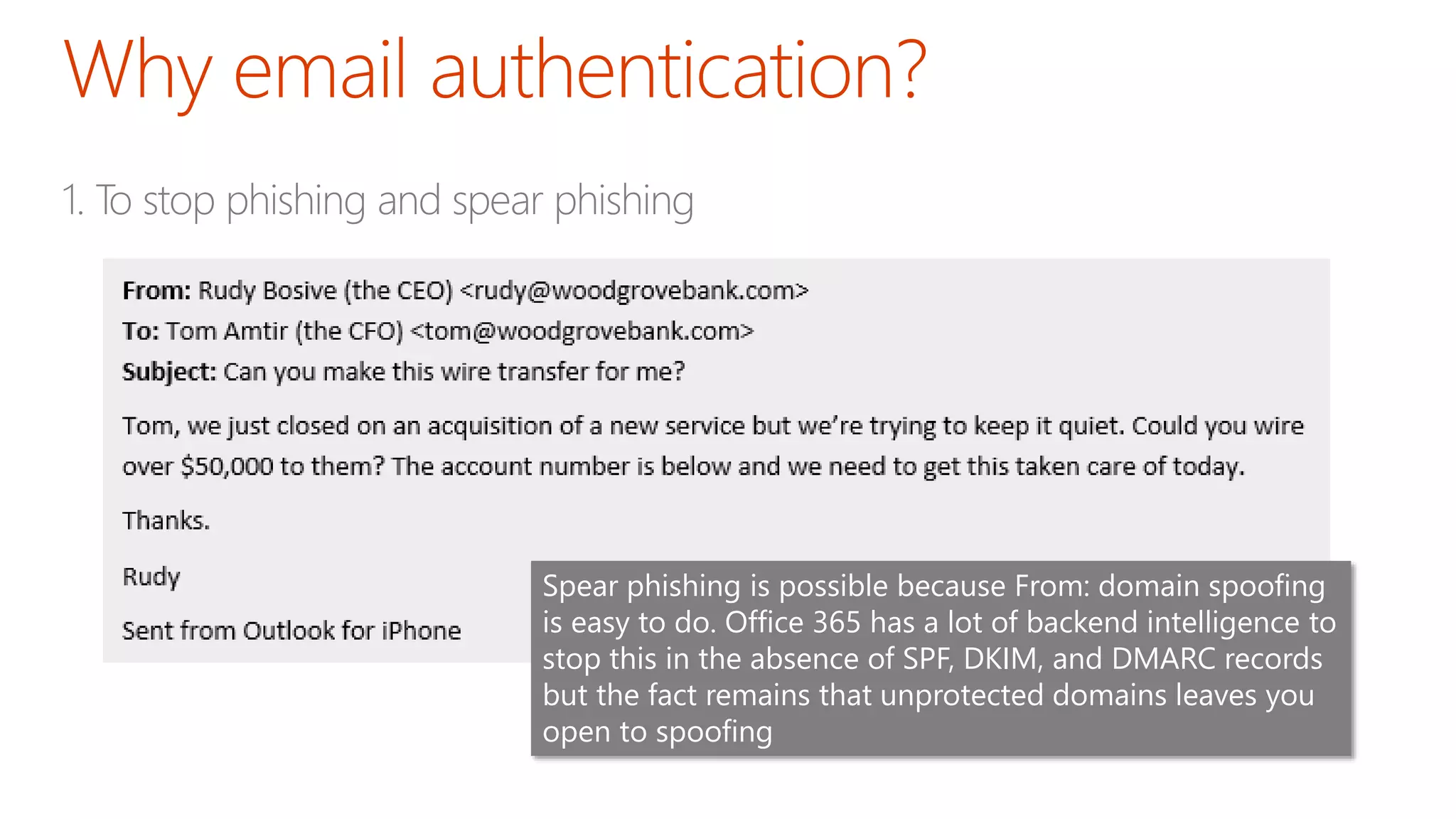
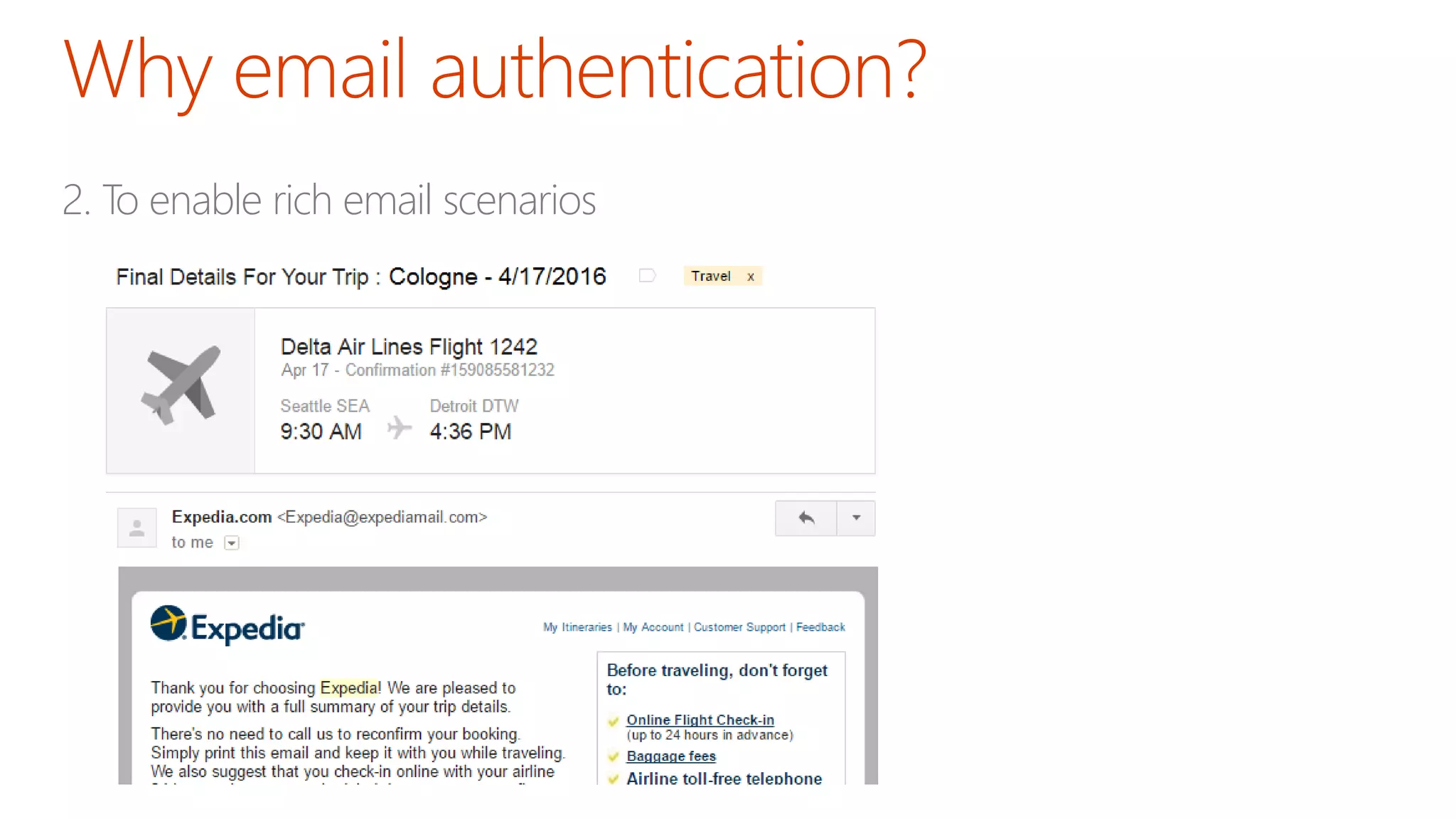
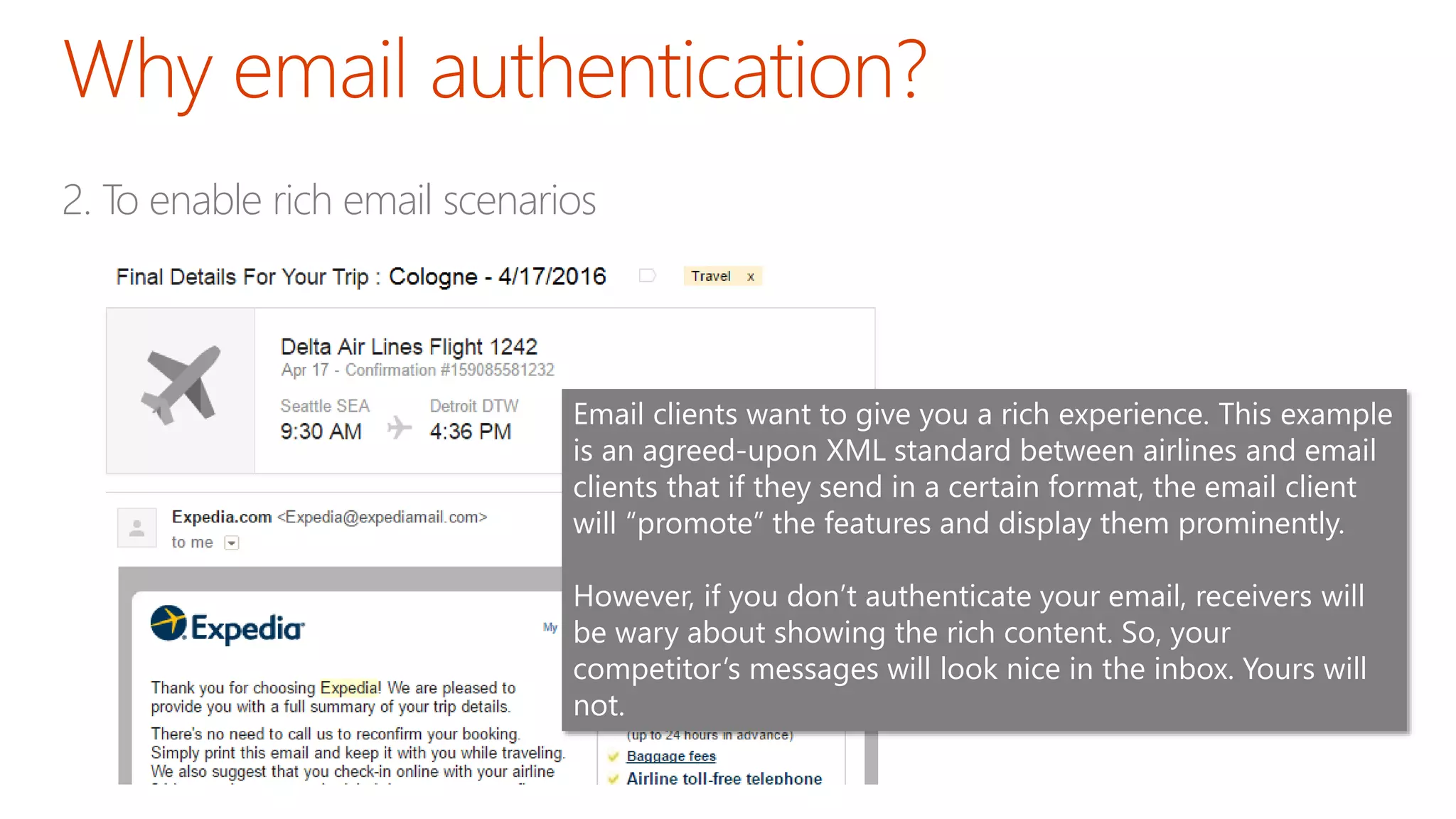
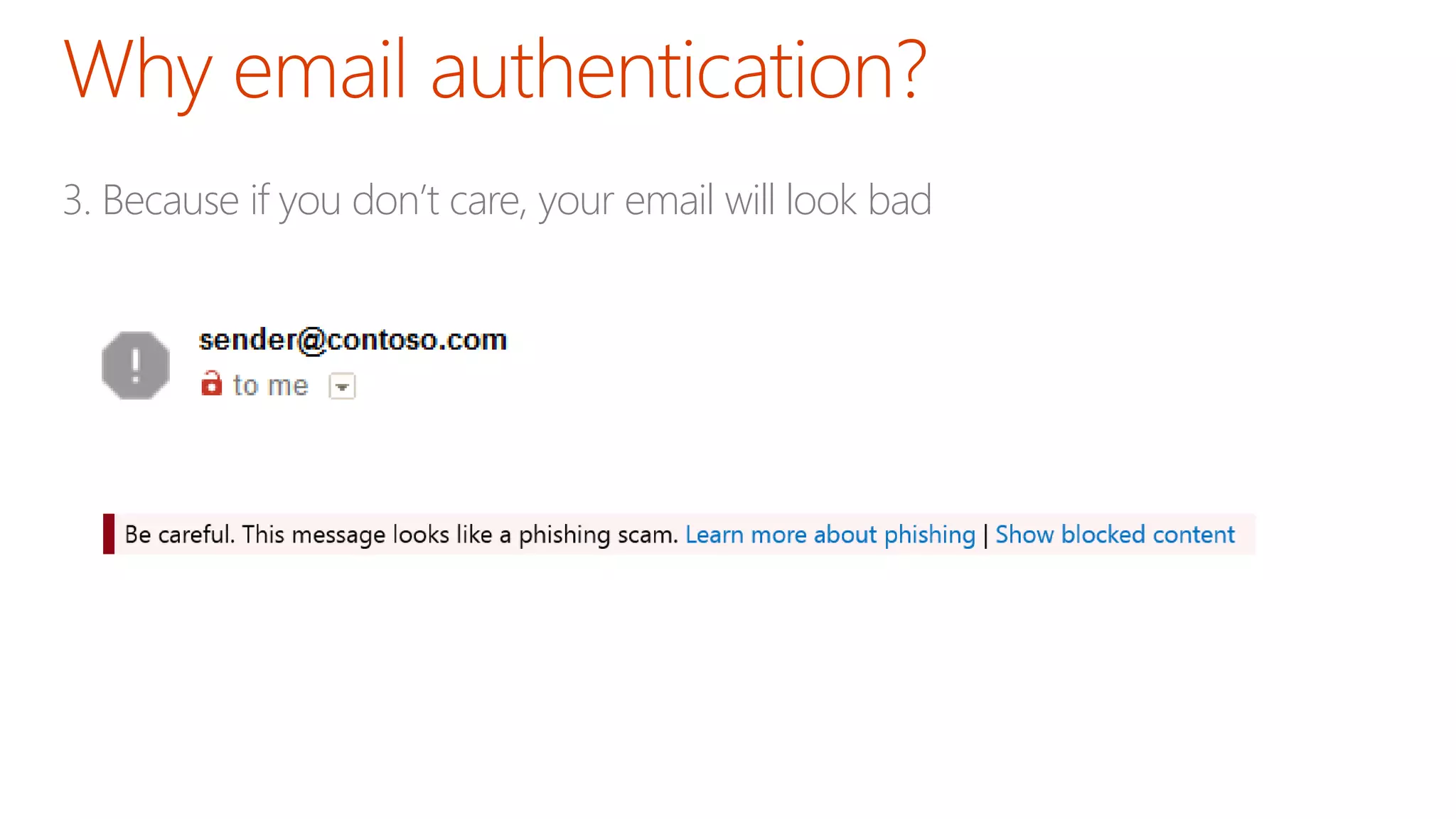
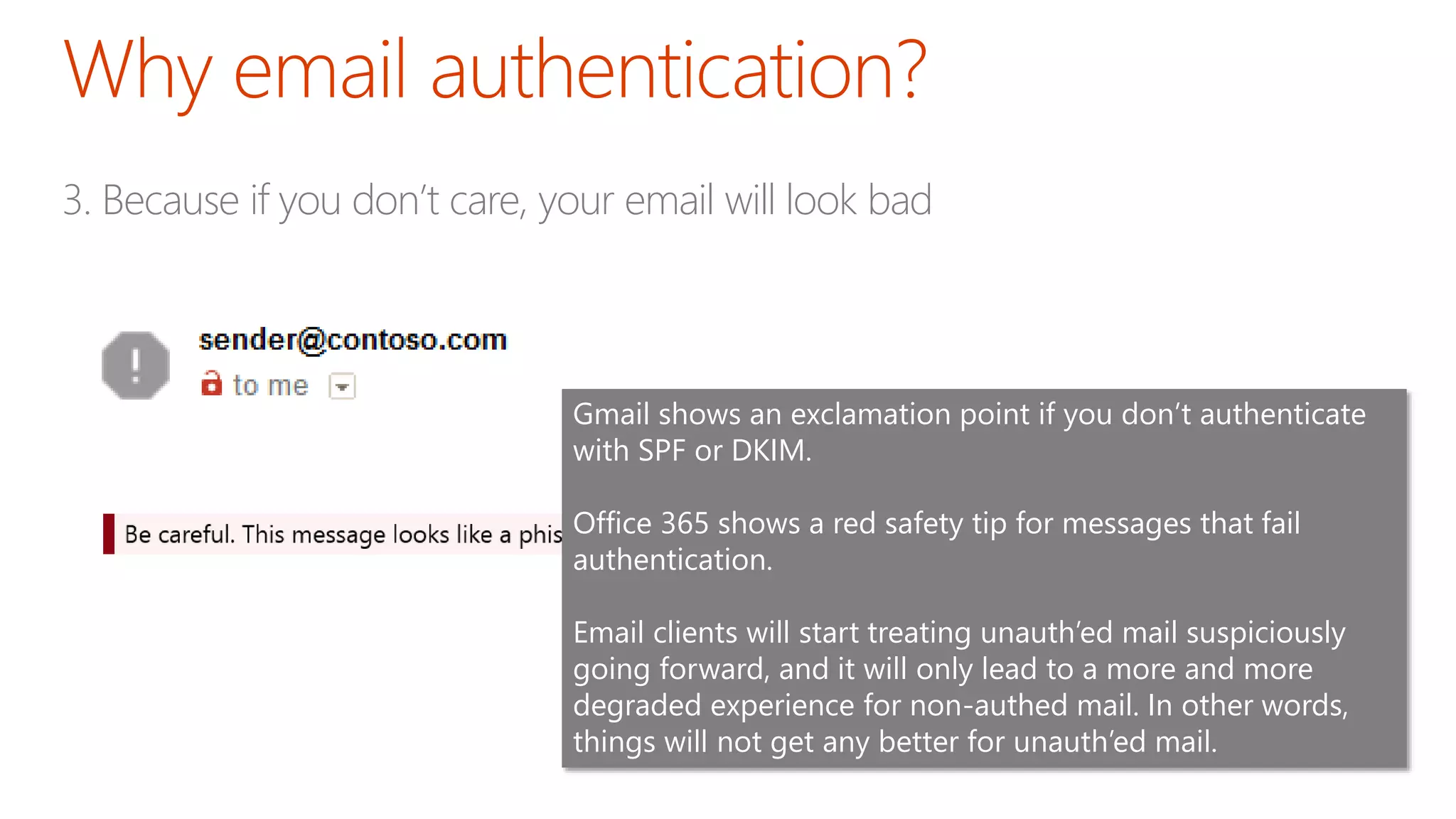
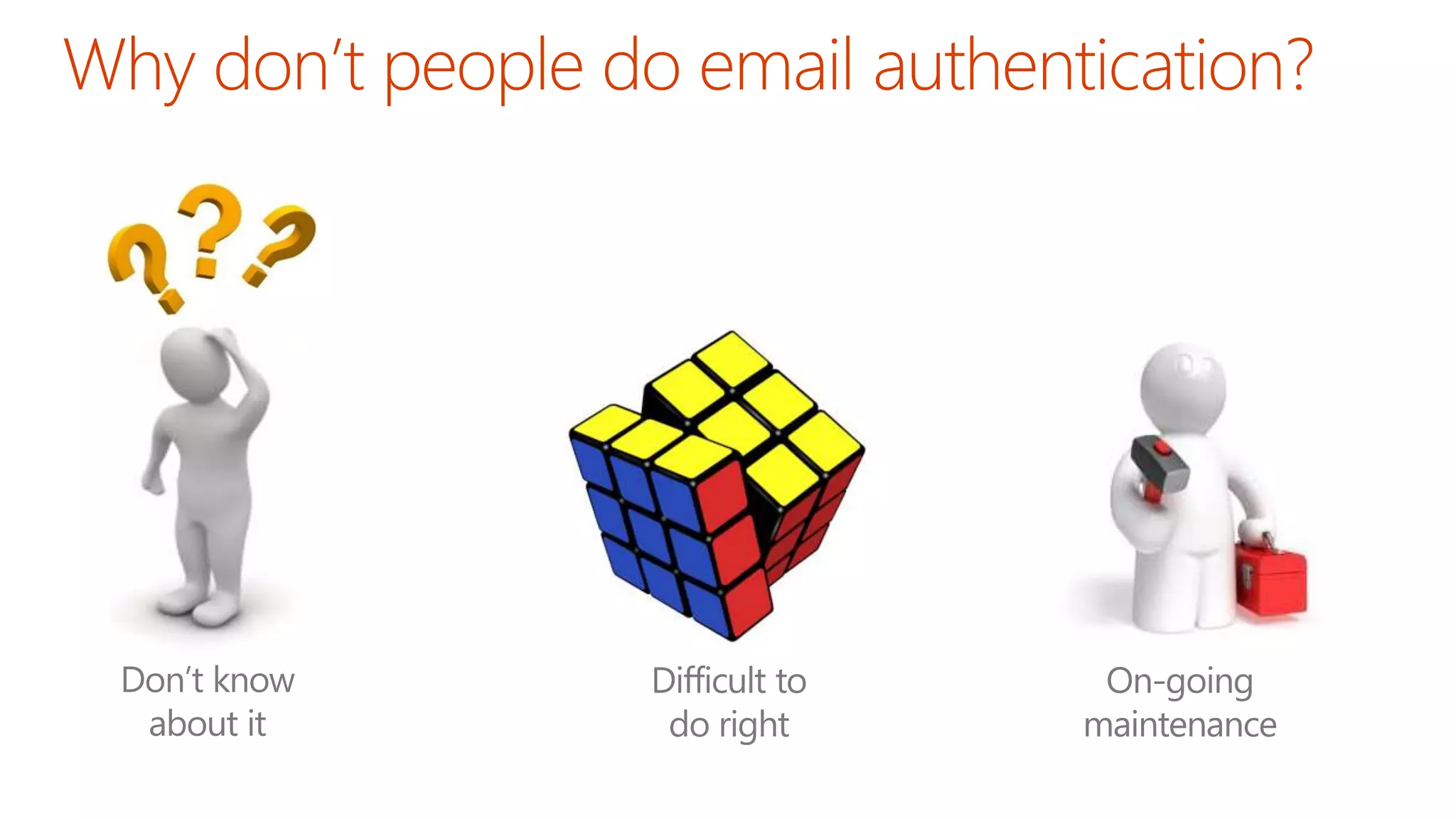
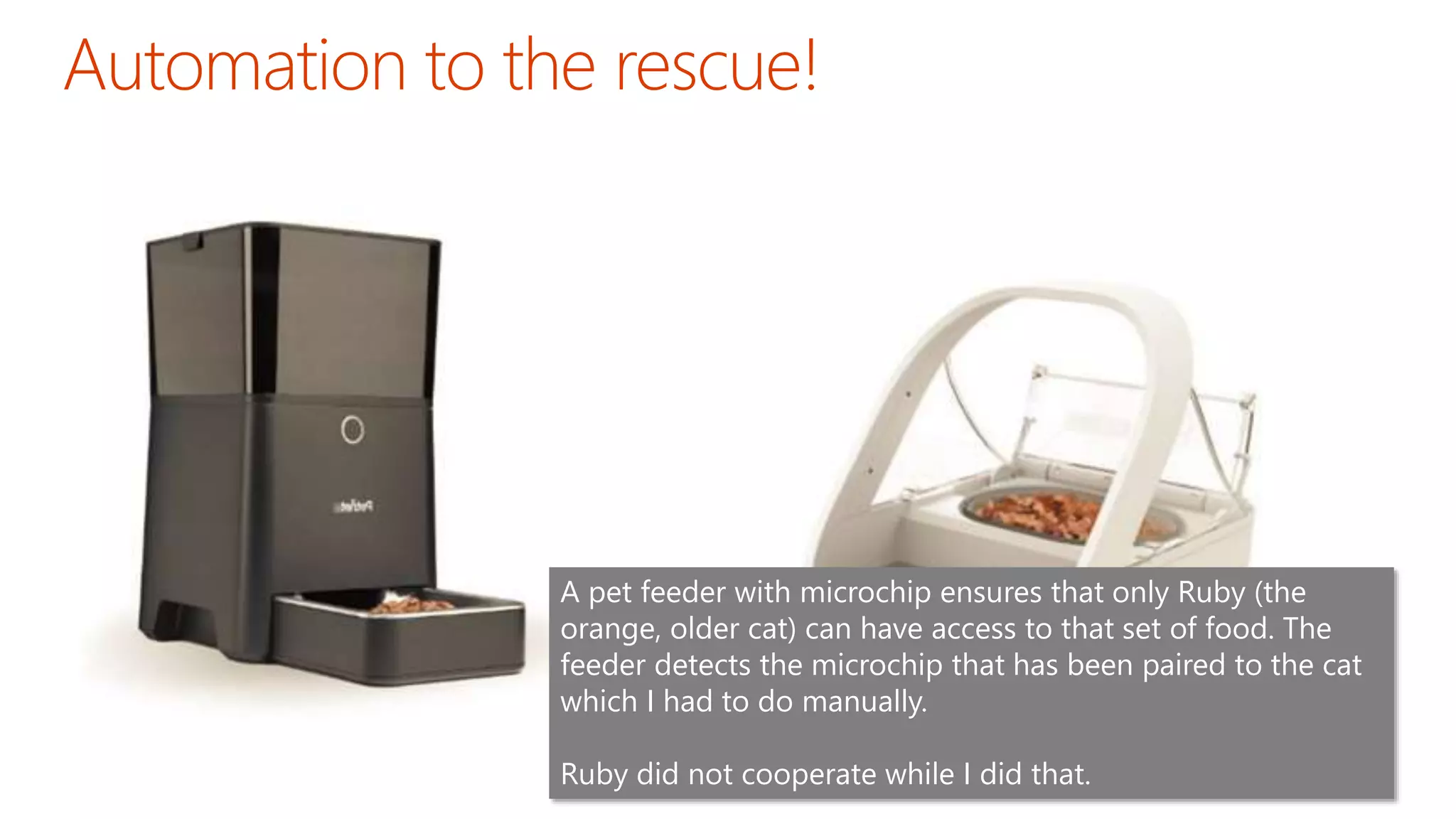
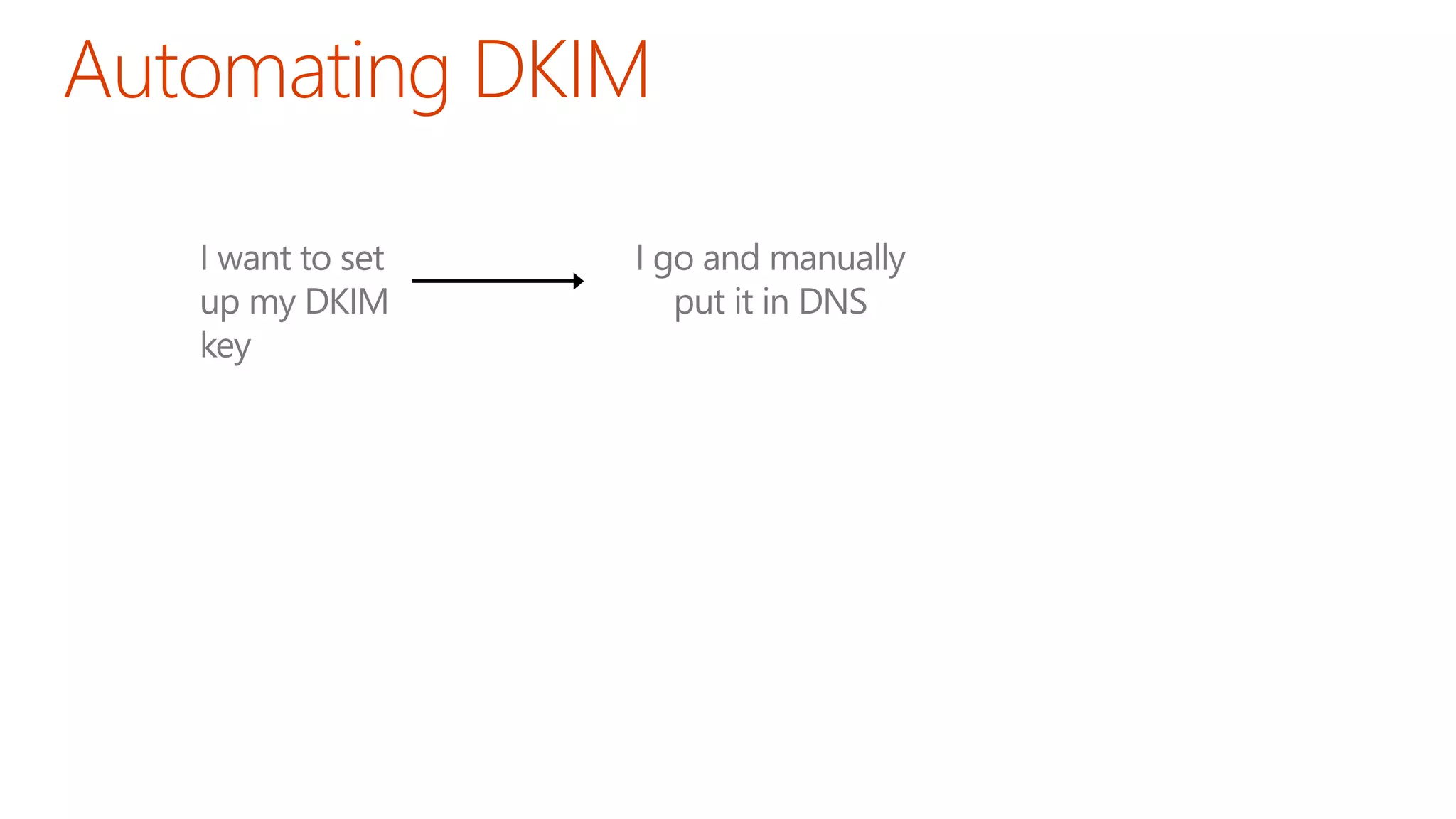
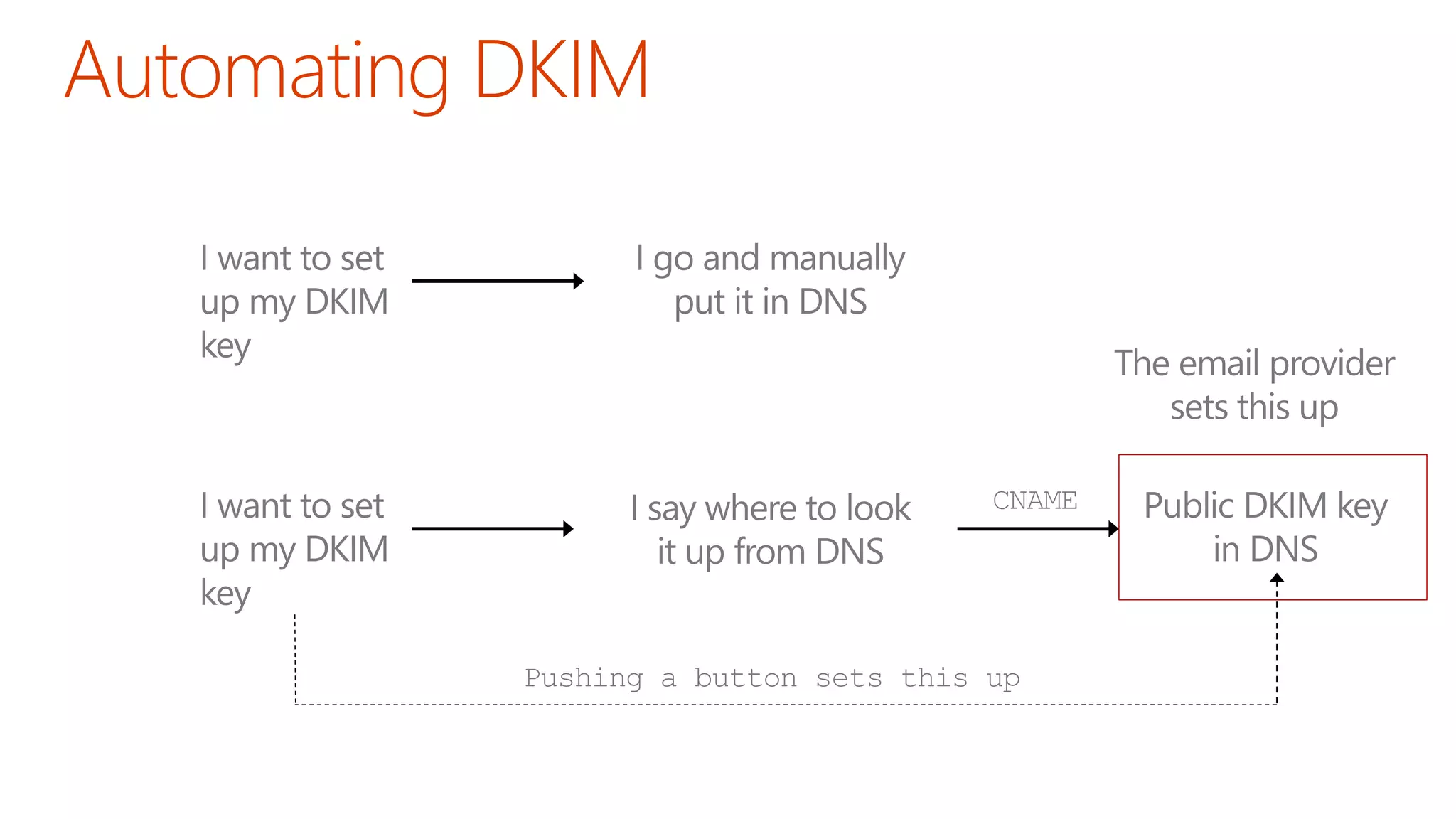
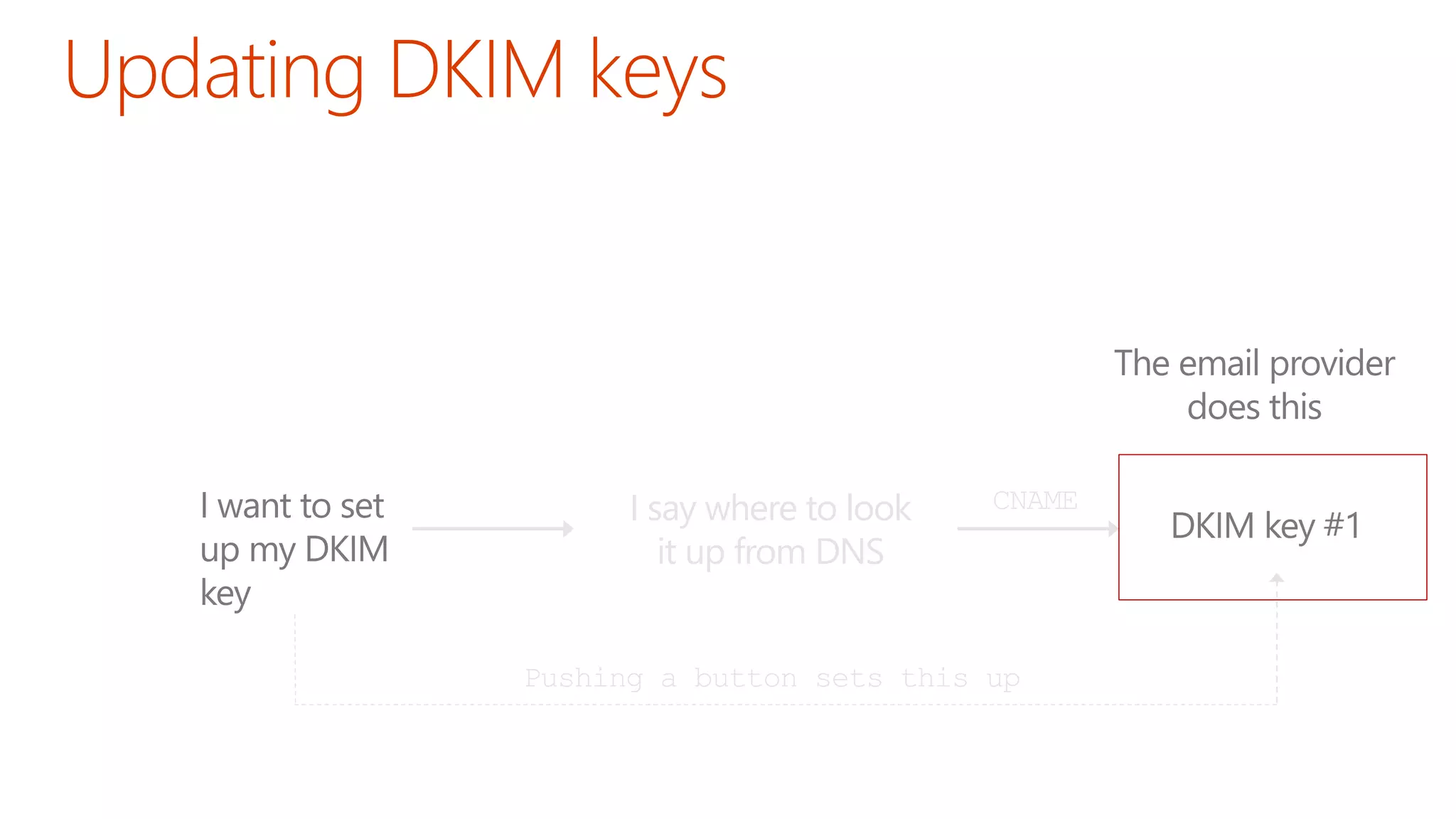
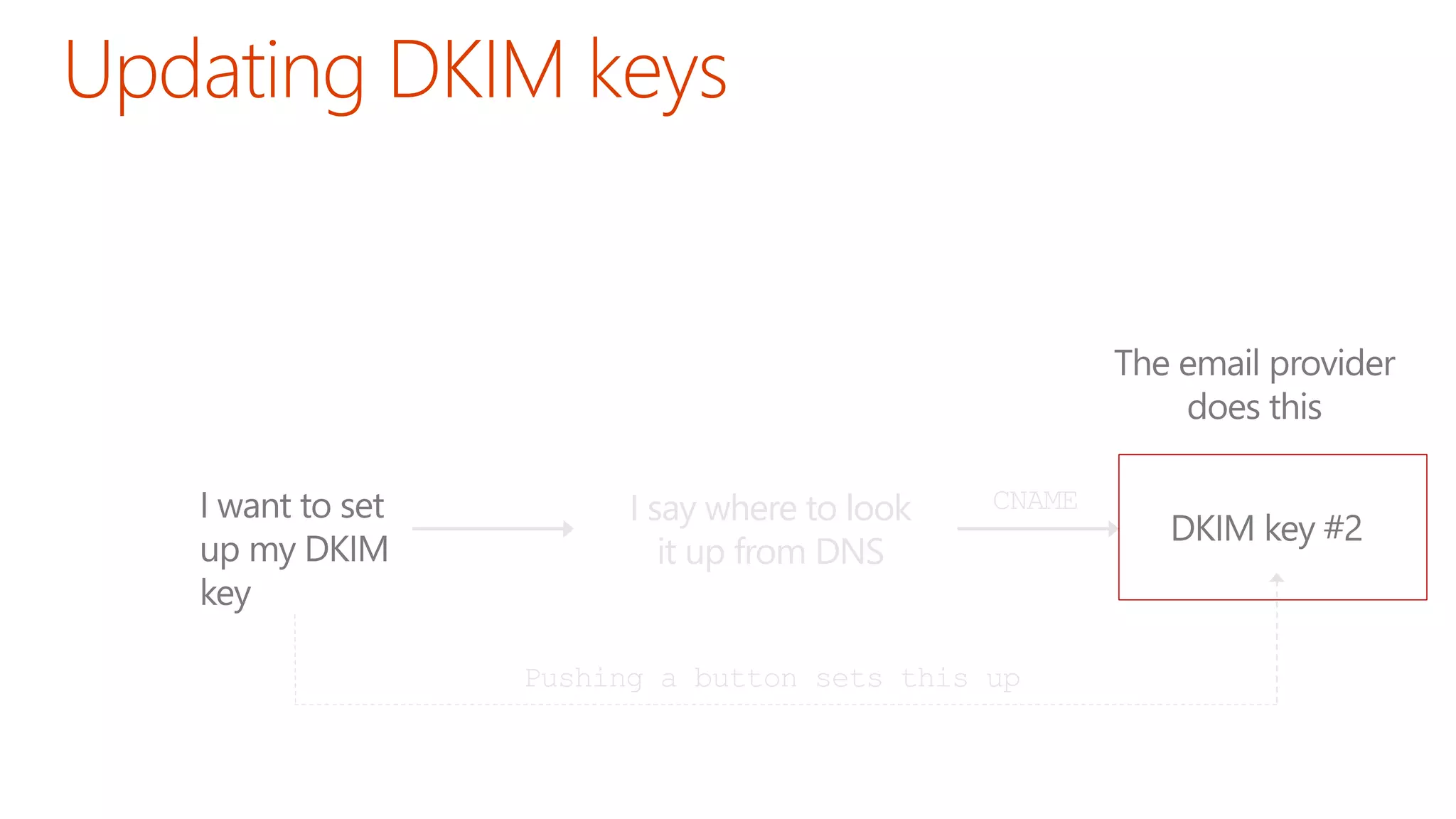
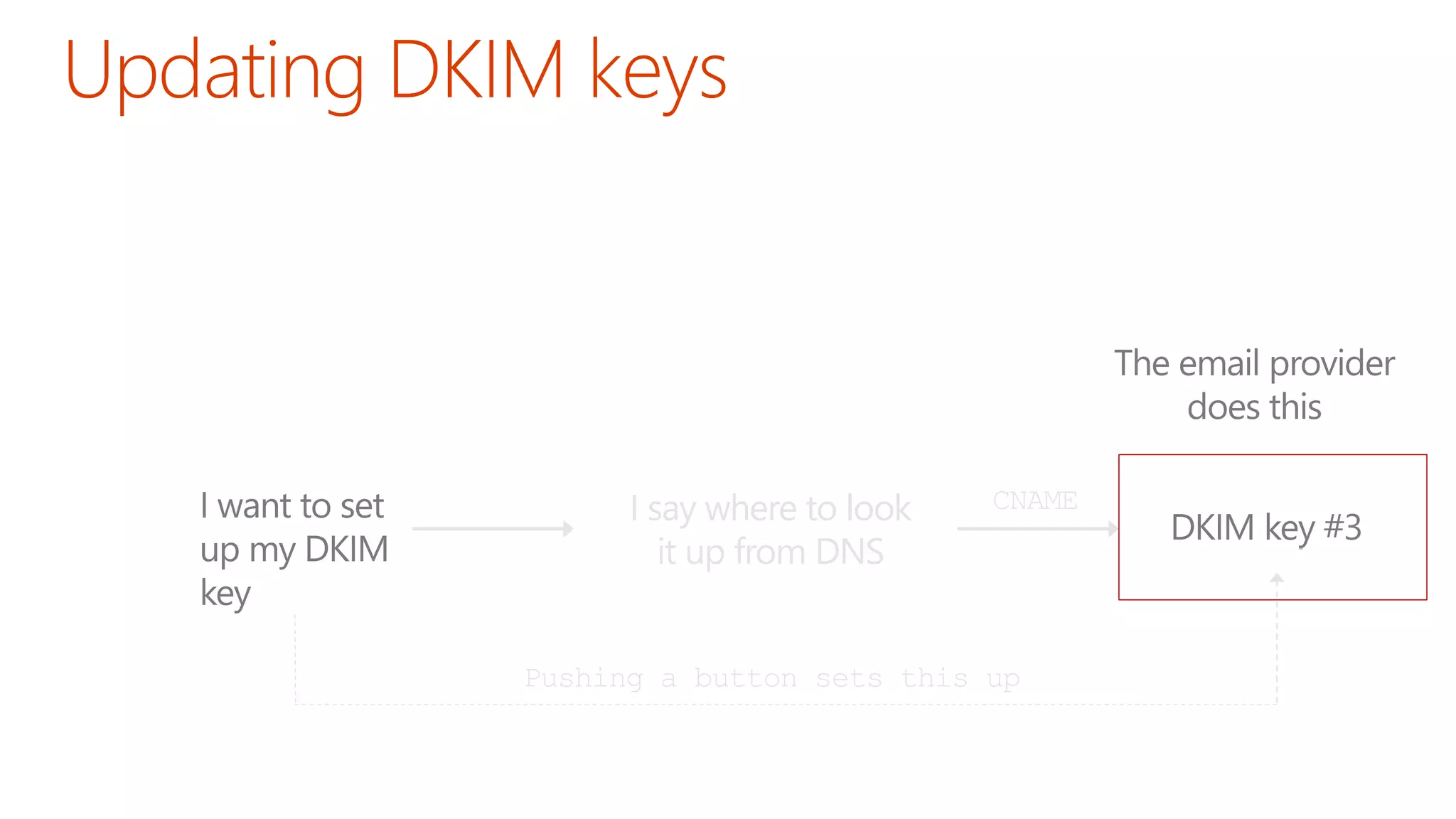
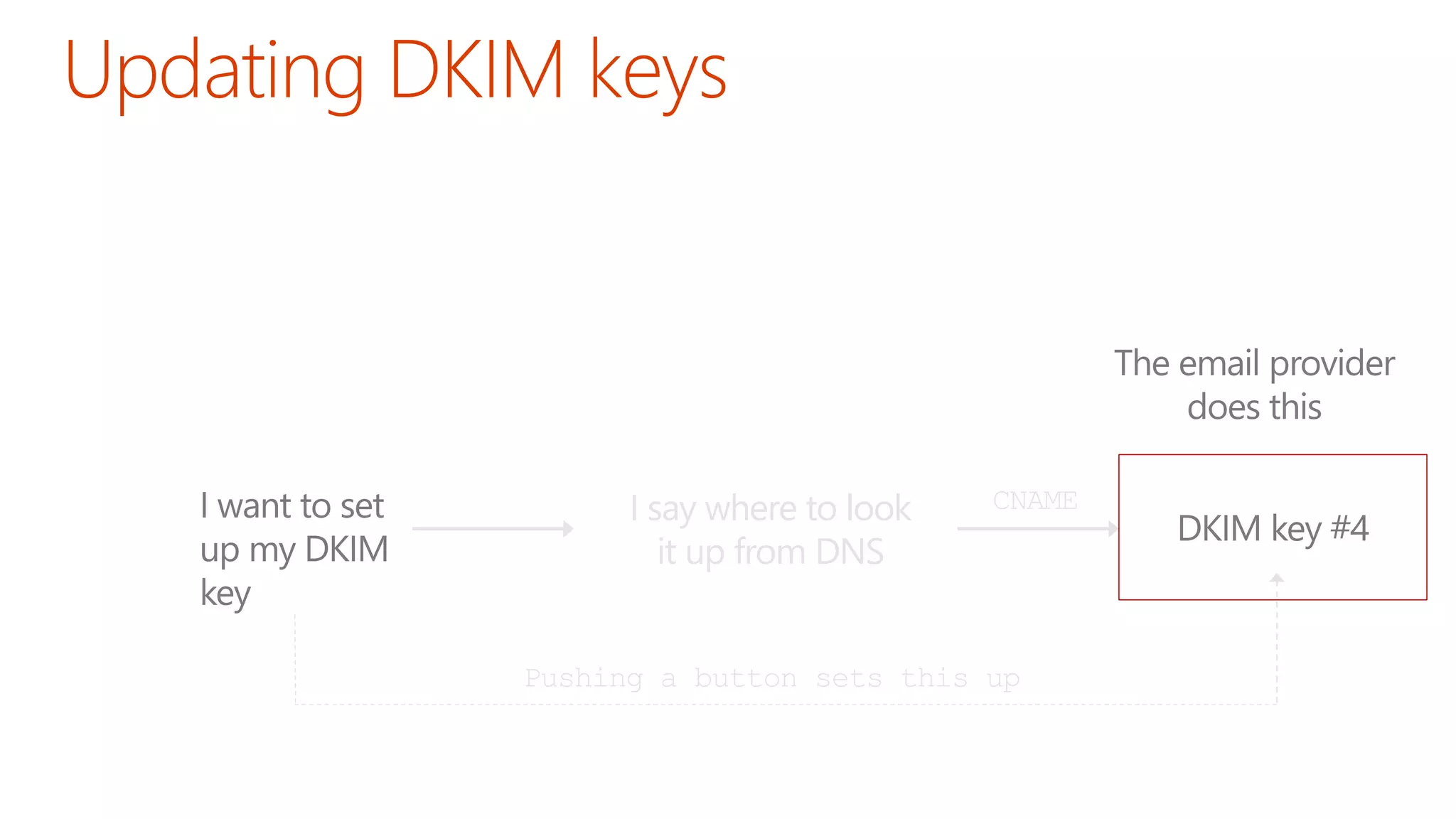
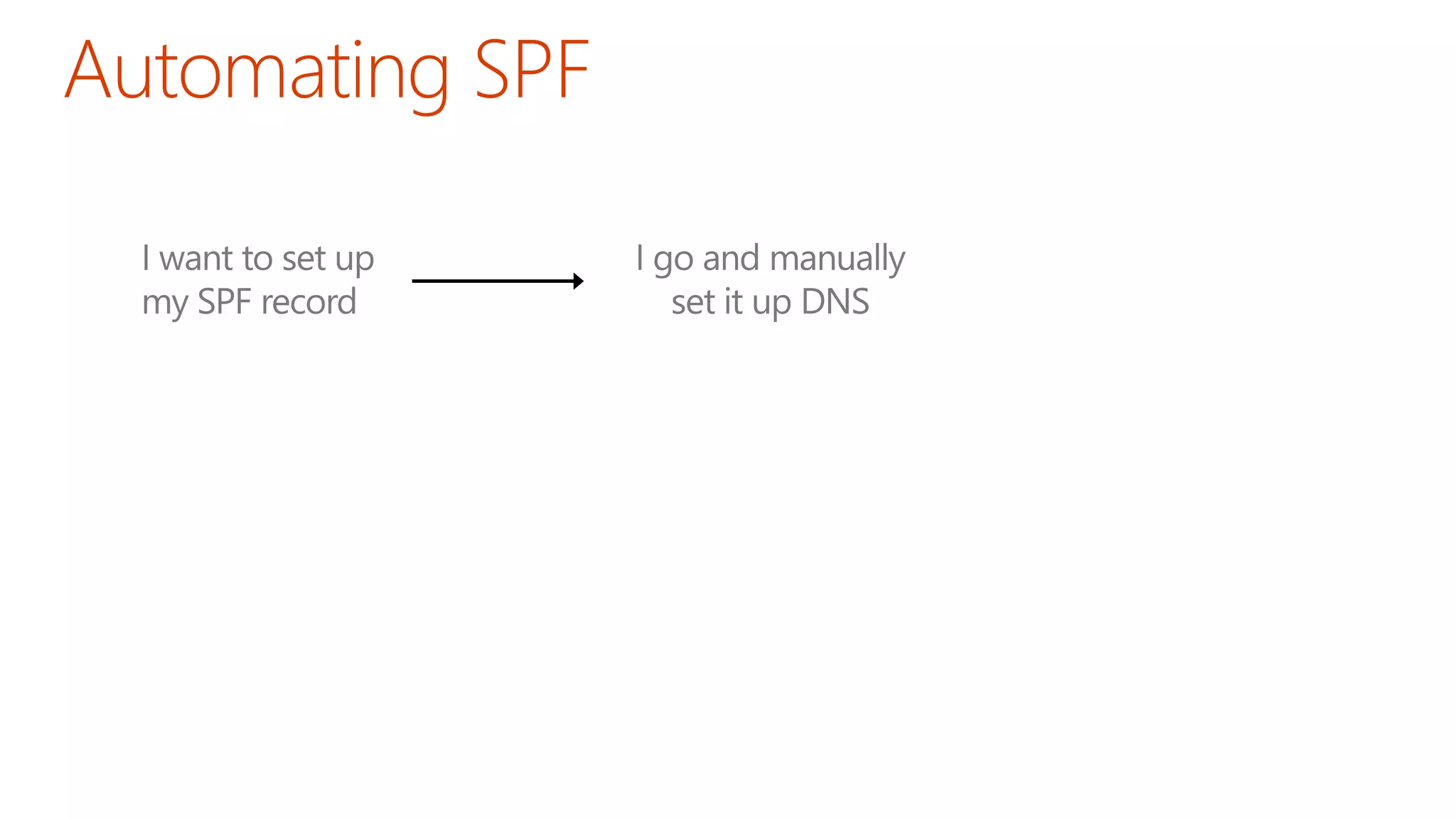
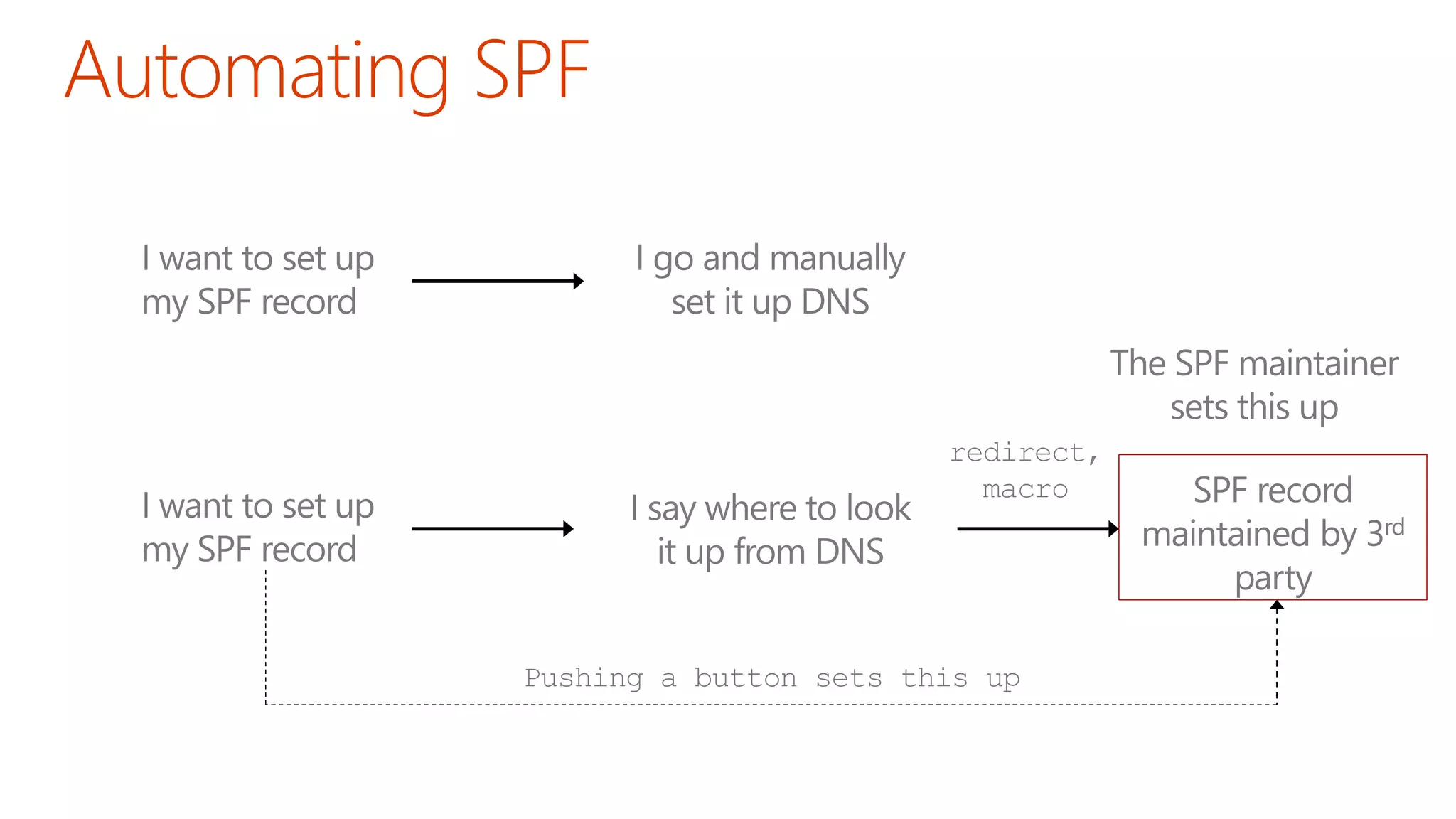
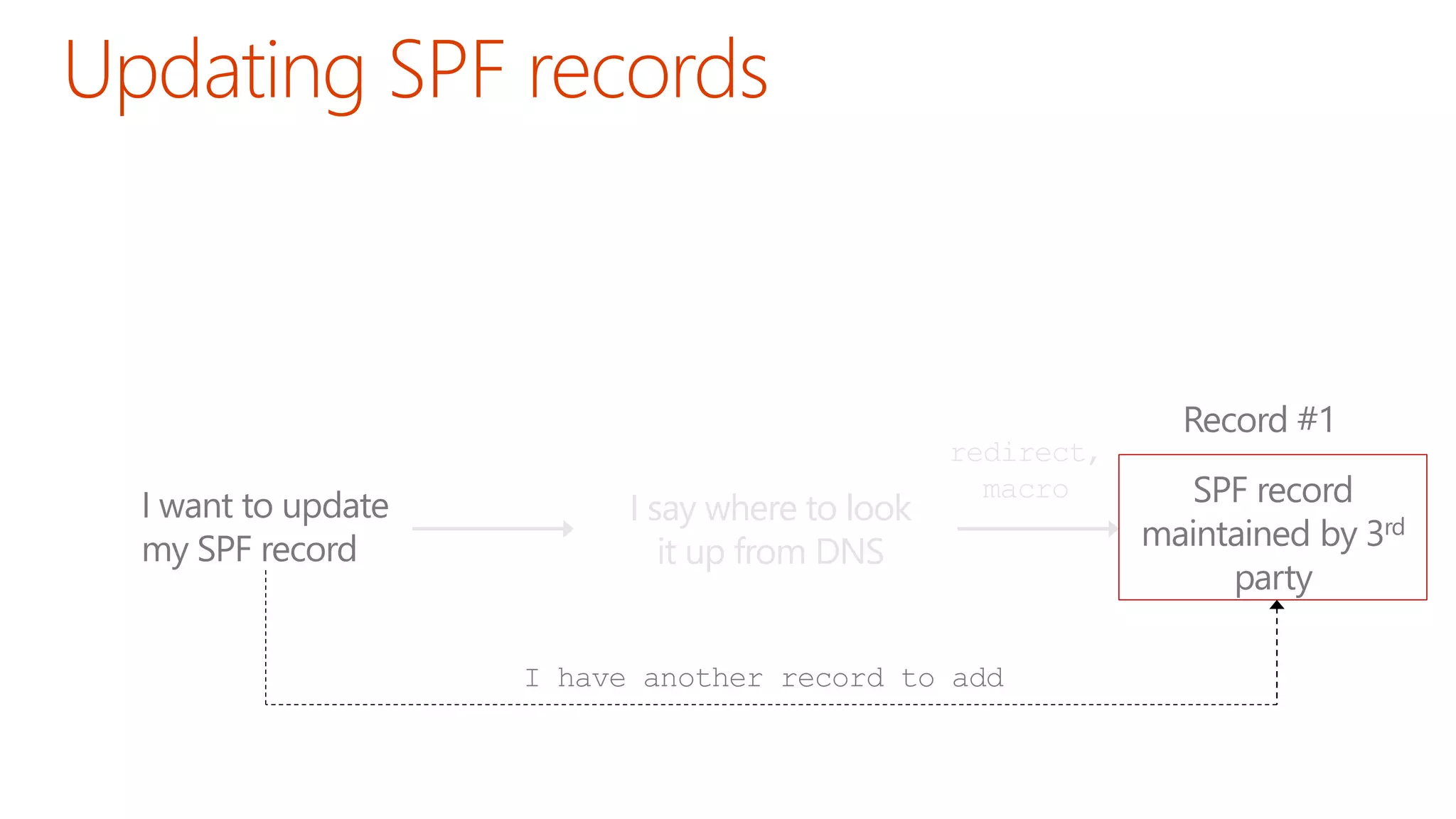
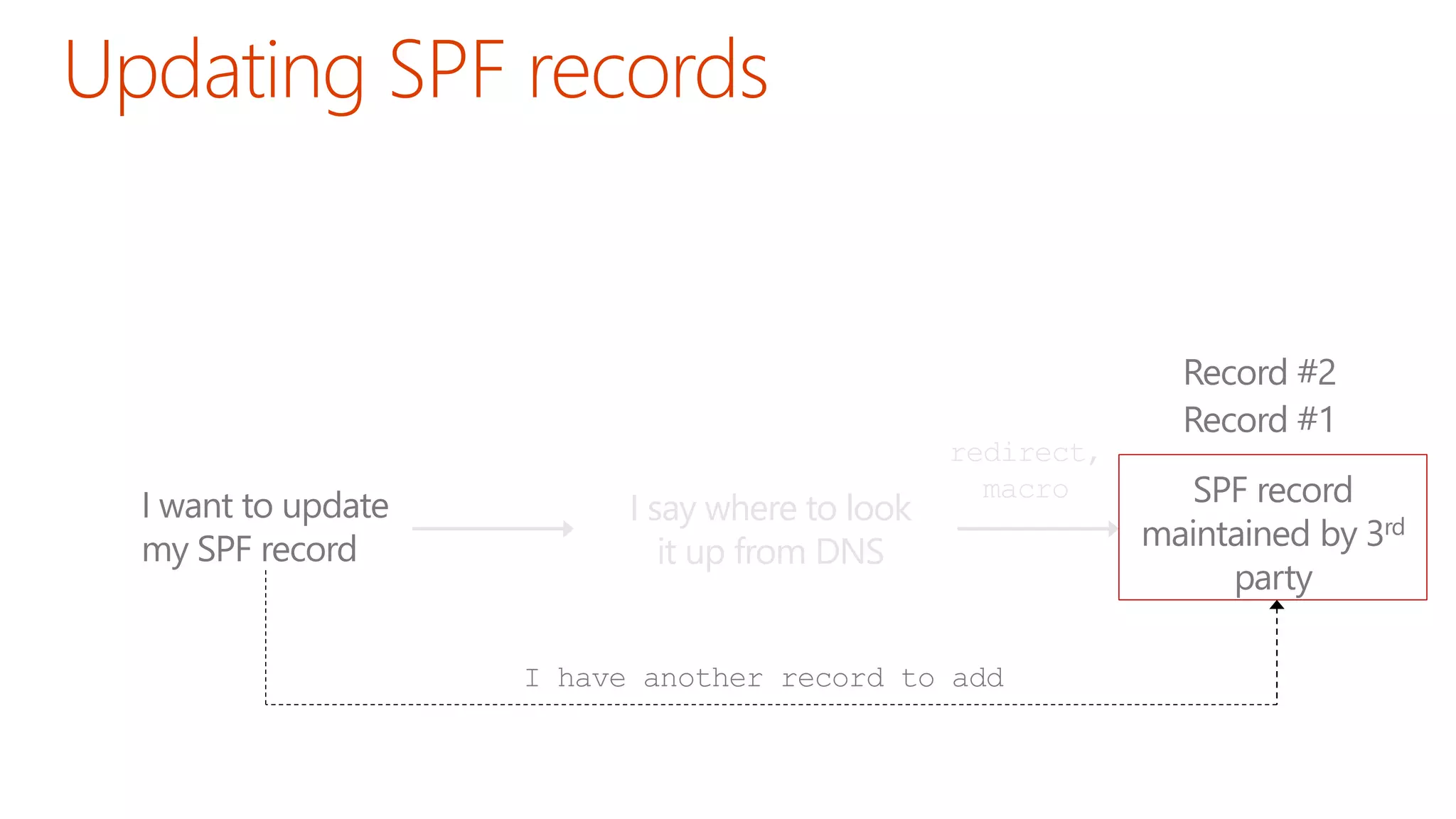
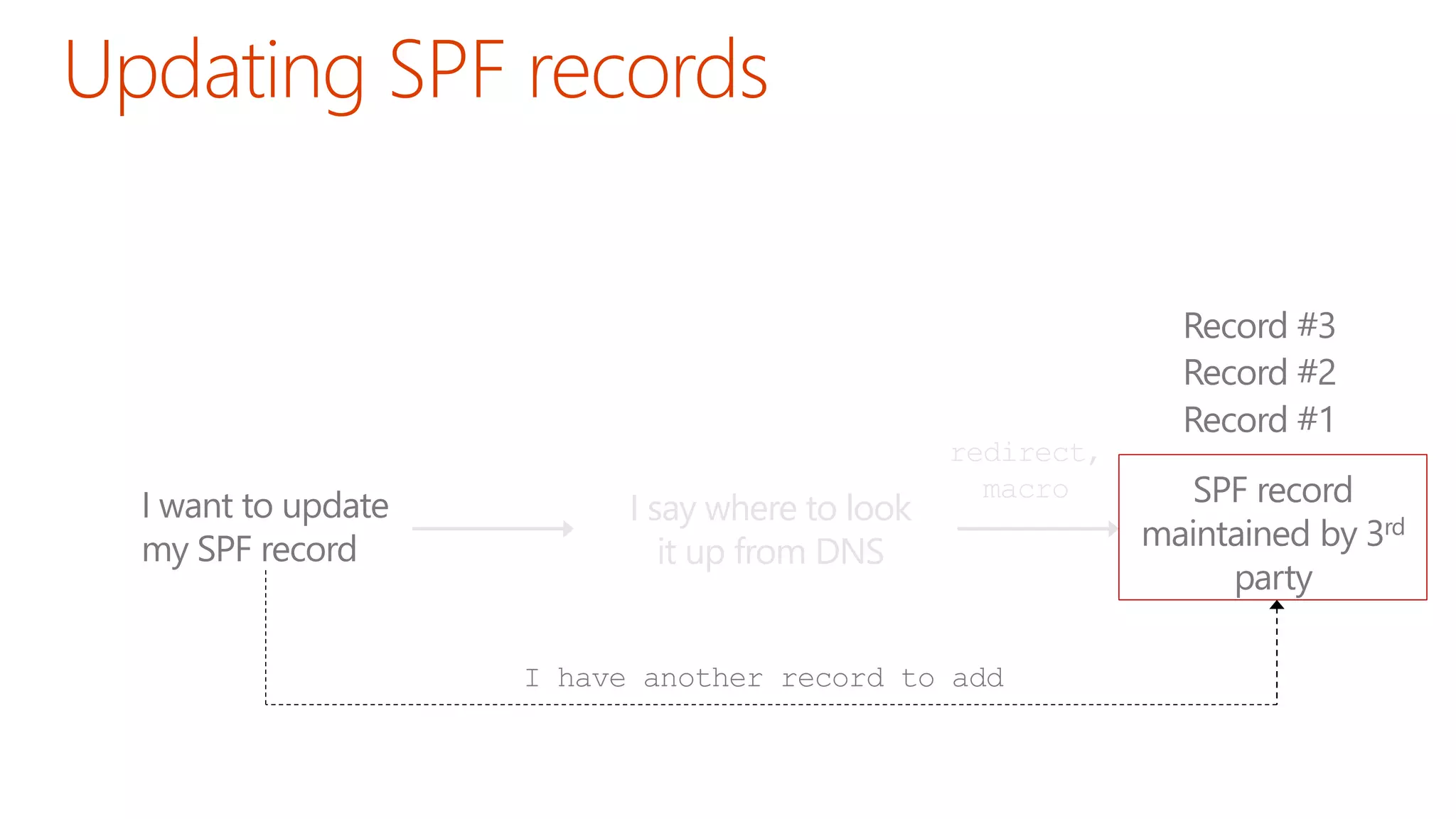
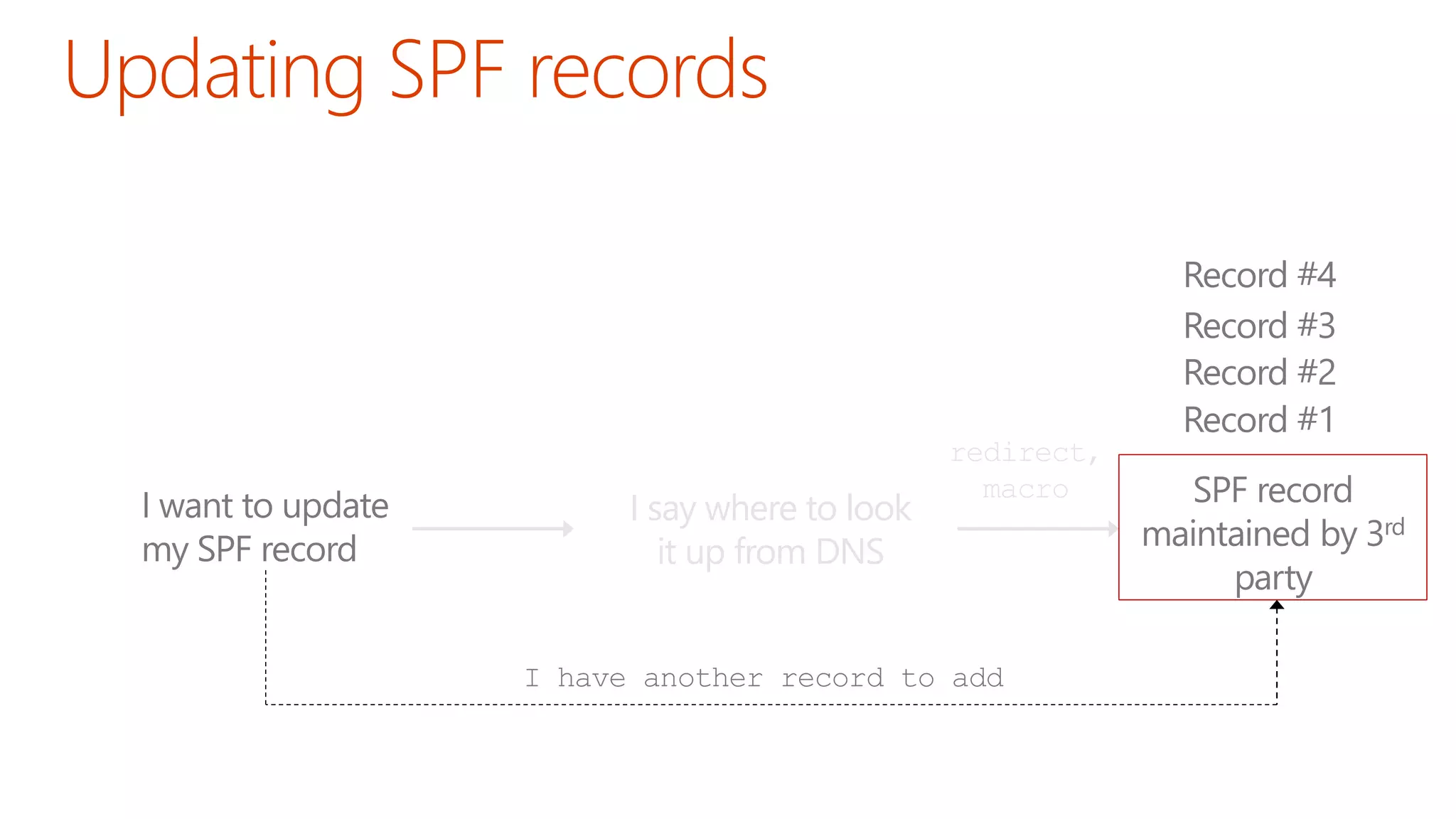
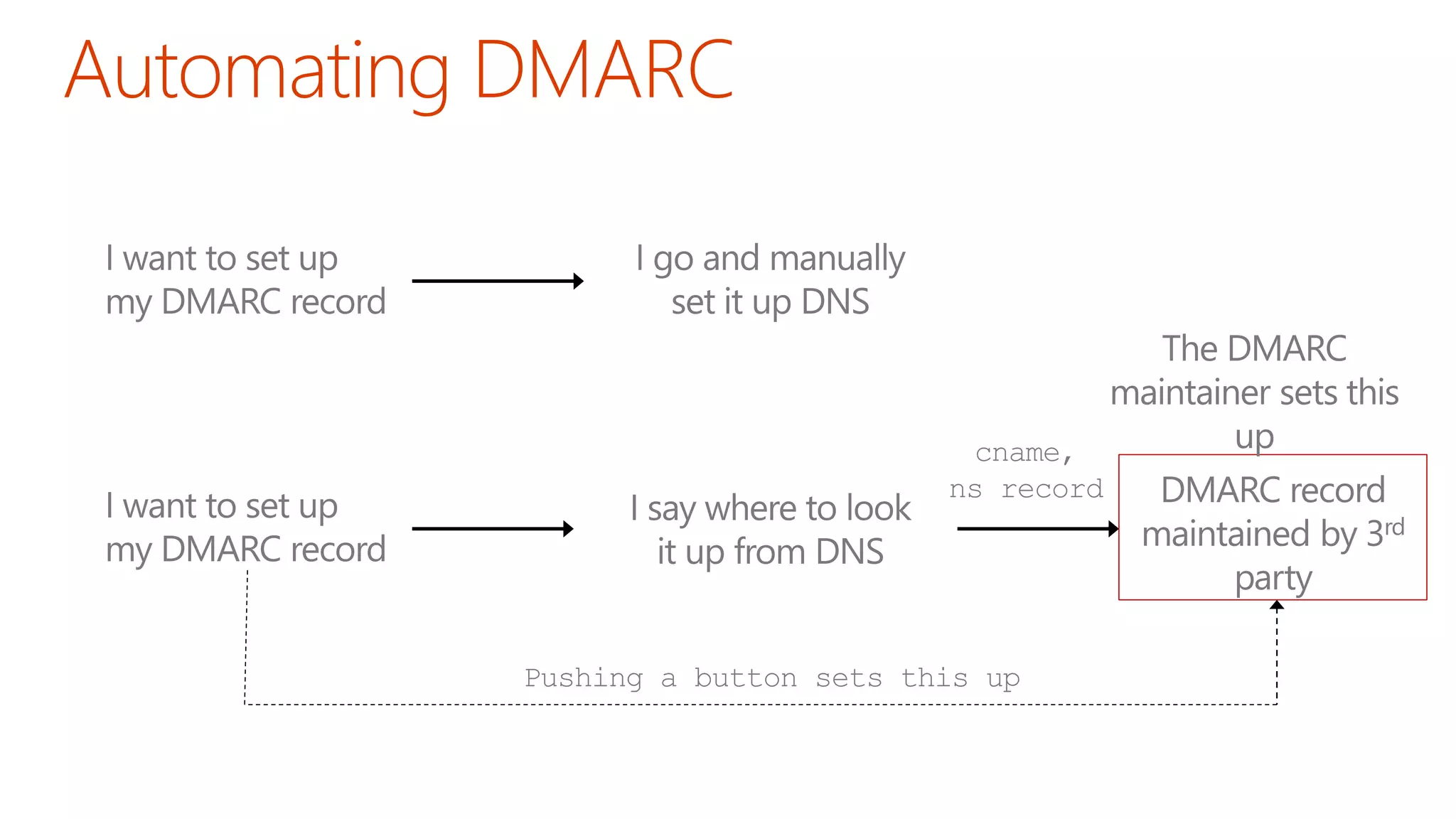
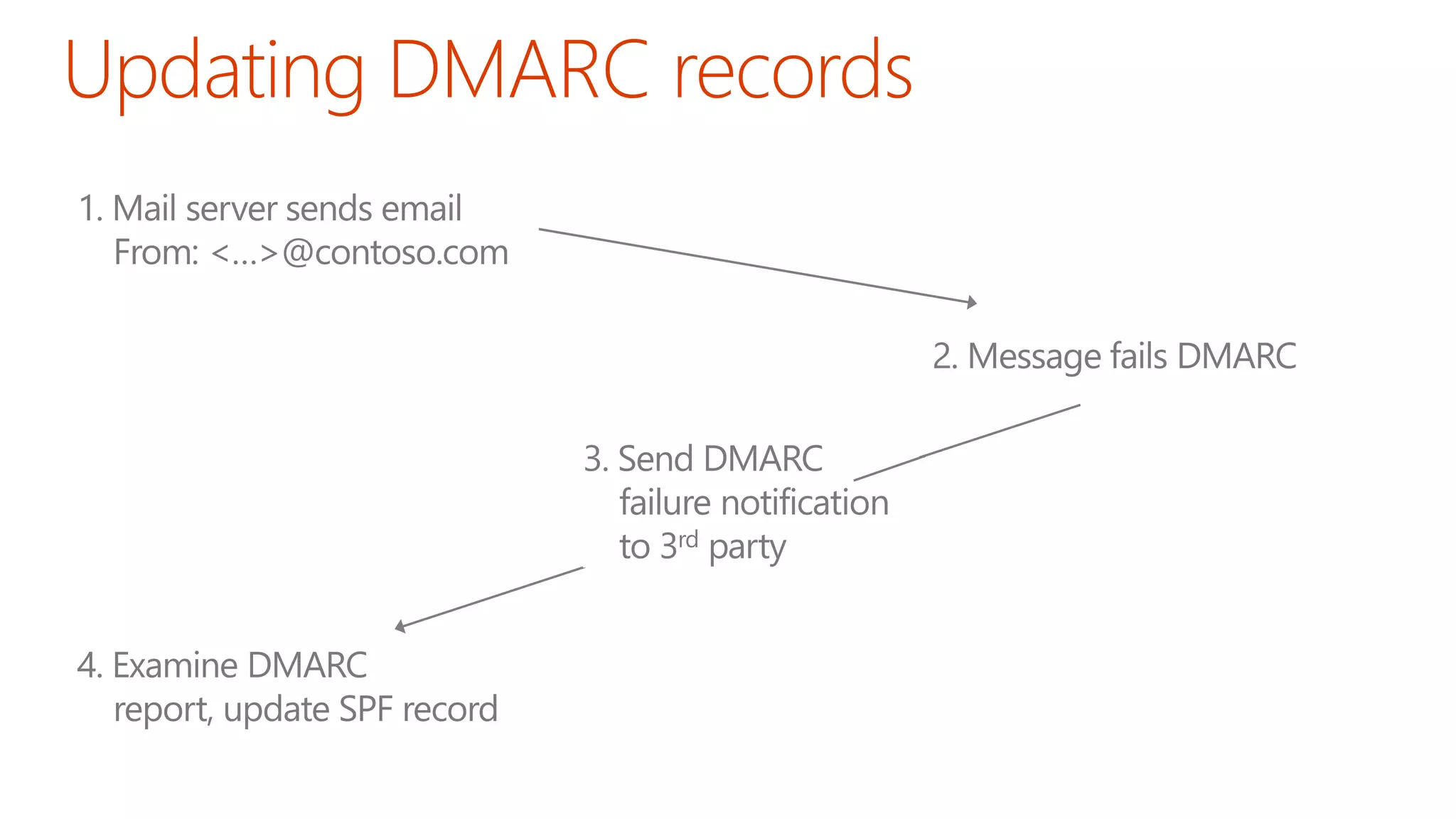
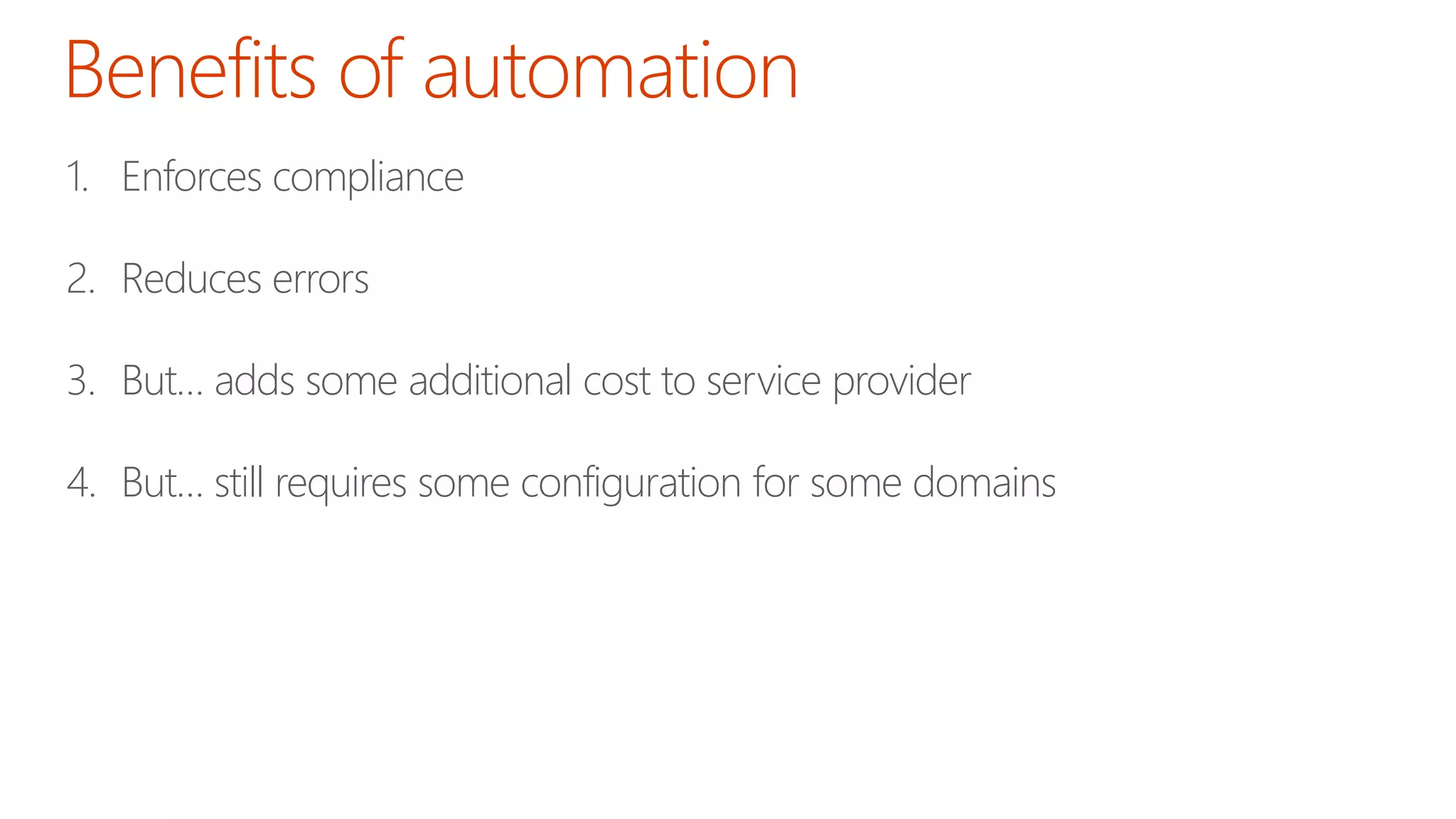
The document discusses the importance of email authentication to prevent phishing and improve email presentation, using the analogy of cat feeding problems to illustrate the complexities involved. It emphasizes that proper implementation of technologies like SPF, DKIM, and DMARC is crucial for maintaining email integrity and user experience. Automation is suggested as a solution to address the challenges of setting up and maintaining email authentication effectively.