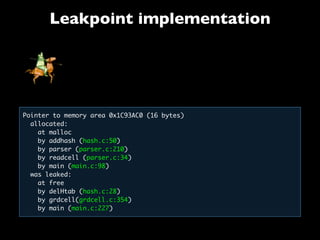
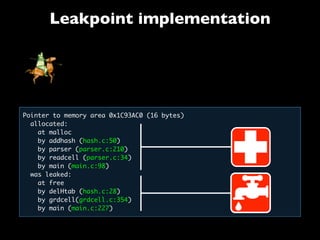
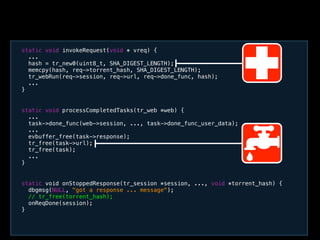
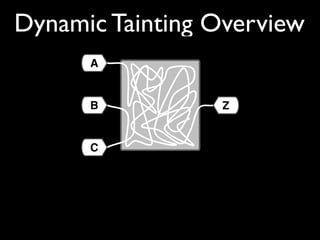
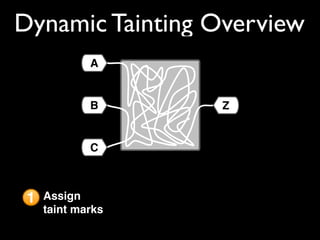
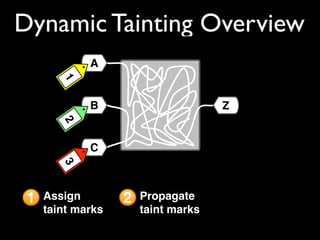
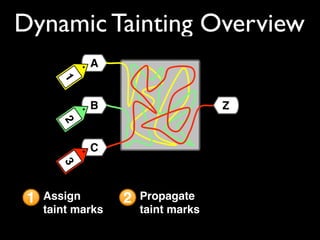
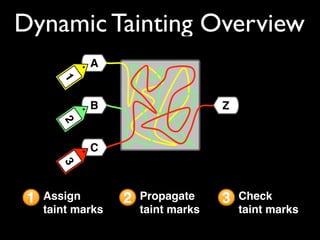
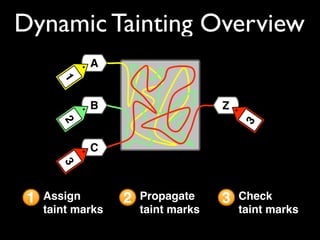
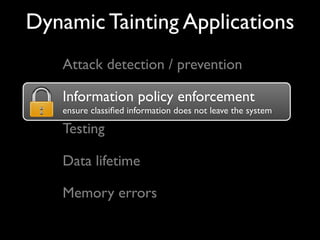
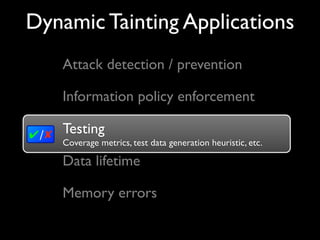
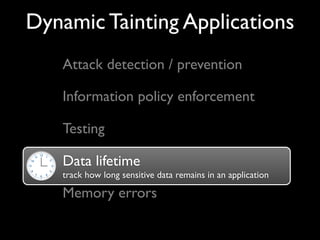
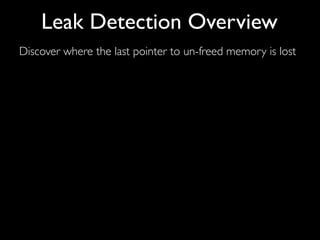
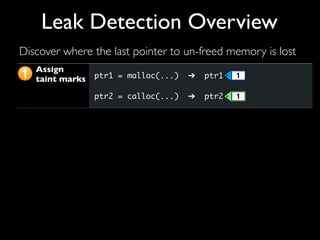
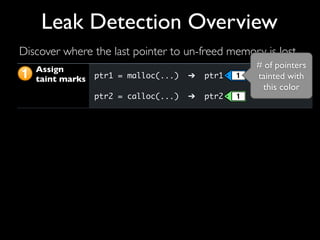
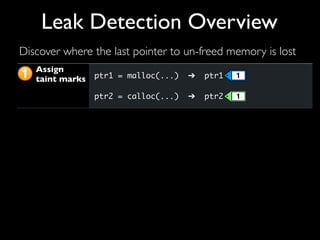
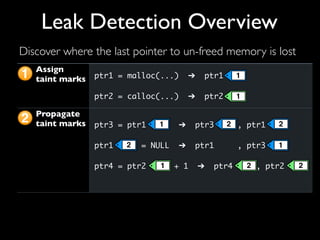
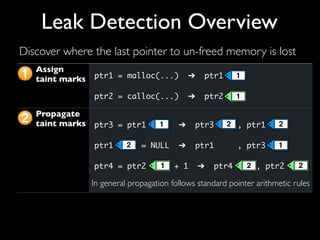
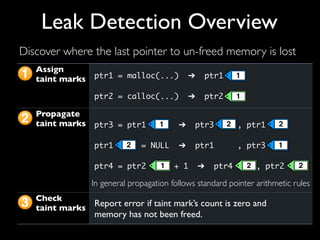
This document discusses taint-based dynamic analysis and leak detection. It provides an overview of how taint analysis works by assigning taint marks to tracked values, propagating those marks as values are operated on, and checking the taint marks to detect issues. It then discusses applications of taint analysis like attack prevention, information flow monitoring, testing, and detecting memory errors and leaks. Finally, it dives deeper into how leak detection specifically tracks pointers to allocated memory and reports errors if a pointer's taint mark reaches zero but the memory has not been freed.
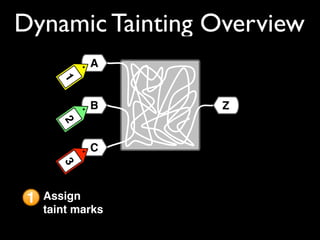



![addhash(char hname[]) {
35. int i;
36. HASHPTR hptr;
37. unsigned int hsum = 0;
38. for(i = 0 ; i < strlen(hname) ; i++) {
39. sum += (unsigned int) hname[i];
40. }
41. hsum %= 3001;
42. if((hptr = hashtab[hsum]) == (HASHPTR) NULL) {
43. hptr = hashtab[hsum] = (HASHPTR) malloc(sizeof(HASHBOX));
44. hptr->hnext = (HASHPTR) NULL;
45. hptr->hnum = ++netctr;
46. hptr->hname = (char *) malloc((strlen(hname) + 1) *
! ! ! ! ! ! ! ! ! ! sizeof(char));
47. sprintf(hptr->hname , "%s" , hname);
48. return(1);
49. } else {
! ...
67. }
}
Detecting leaks is easy](https://image.slidesharecdn.com/coc-researchday-130605203706-phpapp02/85/Taint-based-Dynamic-Analysis-CoC-Research-Day-2009-16-320.jpg)
![addhash(char hname[]) {
35. int i;
36. HASHPTR hptr;
37. unsigned int hsum = 0;
38. for(i = 0 ; i < strlen(hname) ; i++) {
39. sum += (unsigned int) hname[i];
40. }
41. hsum %= 3001;
42. if((hptr = hashtab[hsum]) == (HASHPTR) NULL) {
43. hptr = hashtab[hsum] = (HASHPTR) malloc(sizeof(HASHBOX));
44. hptr->hnext = (HASHPTR) NULL;
45. hptr->hnum = ++netctr;
46. hptr->hname = (char *) malloc((strlen(hname) + 1) *
! ! ! ! ! ! ! ! ! ! sizeof(char));
47. sprintf(hptr->hname , "%s" , hname);
48. return(1);
49. } else {
! ...
67. }
}
Detecting leaks is easy](https://image.slidesharecdn.com/coc-researchday-130605203706-phpapp02/85/Taint-based-Dynamic-Analysis-CoC-Research-Day-2009-17-320.jpg)
![addhash(char hname[]) {
35. int i;
36. HASHPTR hptr;
37. unsigned int hsum = 0;
38. for(i = 0 ; i < strlen(hname) ; i++) {
39. sum += (unsigned int) hname[i];
40. }
41. hsum %= 3001;
42. if((hptr = hashtab[hsum]) == (HASHPTR) NULL) {
43. hptr = hashtab[hsum] = (HASHPTR) malloc(sizeof(HASHBOX));
44. hptr->hnext = (HASHPTR) NULL;
45. hptr->hnum = ++netctr;
46. hptr->hname = (char *) malloc((strlen(hname) + 1) *
! ! ! ! ! ! ! ! ! ! sizeof(char));
47. sprintf(hptr->hname , "%s" , hname);
48. return(1);
49. } else {
! ...
67. }
}
Detecting leaks is easy; fixing them is not](https://image.slidesharecdn.com/coc-researchday-130605203706-phpapp02/85/Taint-based-Dynamic-Analysis-CoC-Research-Day-2009-18-320.jpg)
![addhash(char hname[]) {
35. int i;
36. HASHPTR hptr;
37. unsigned int hsum = 0;
38. for(i = 0 ; i < strlen(hname) ; i++) {
39. sum += (unsigned int) hname[i];
40. }
41. hsum %= 3001;
42. if((hptr = hashtab[hsum]) == (HASHPTR) NULL) {
43. hptr = hashtab[hsum] = (HASHPTR) malloc(sizeof(HASHBOX));
44. hptr->hnext = (HASHPTR) NULL;
45. hptr->hnum = ++netctr;
46. hptr->hname = (char *) malloc((strlen(hname) + 1) *
! ! ! ! ! ! ! ! ! ! sizeof(char));
47. sprintf(hptr->hname , "%s" , hname);
48. return(1);
49. } else {
! ...
67. }
}
Detecting leaks is easy](https://image.slidesharecdn.com/coc-researchday-130605203706-phpapp02/85/Taint-based-Dynamic-Analysis-CoC-Research-Day-2009-26-320.jpg)
![46. hptr->hname = (char *) malloc((strlen(hname) + 1) *
! ! ! ! ! ! ! ! ! ! sizeof(char));
delHtab() {
15. int i;
16. HASHPTR hptr , zapptr;
17. for(i = 0; i < 3001; i++) {
18. hptr = hashtab[i];
19. if(hptr != (HASHPTR) NULL) {
20. zapptr = hptr ;
21. while(hptr->hnext != (HASHPTR) NULL) {
22.! ! hptr = hptr->hnext;
23.! ! free(zapptr);
24.! ! zapptr = hptr ;
25.! ! }
26.! ! free(hptr);
27.! }
28. }!
29. free(hashtab);
30. return;
}
Detecting leaks is easy](https://image.slidesharecdn.com/coc-researchday-130605203706-phpapp02/85/Taint-based-Dynamic-Analysis-CoC-Research-Day-2009-27-320.jpg)
![46. hptr->hname = (char *) malloc((strlen(hname) + 1) *
! ! ! ! ! ! ! ! ! ! sizeof(char));
Detecting leaks is easy; fixing them is, too
delHtab() {
15. int i;
16. HASHPTR hptr , zapptr;
17. for(i = 0; i < 3001; i++) {
18. hptr = hashtab[i];
19. if(hptr != (HASHPTR) NULL) {
20. zapptr = hptr ;
21. while(hptr->hnext != (HASHPTR) NULL) {
22.! ! hptr = hptr->hnext;
23.! ! free(zapptr);
24.! ! zapptr = hptr ;
25.! ! }
26.! ! free(hptr);
27.! }
28. }!
29. free(hashtab);
30. return;
}](https://image.slidesharecdn.com/coc-researchday-130605203706-phpapp02/85/Taint-based-Dynamic-Analysis-CoC-Research-Day-2009-28-320.jpg)
![46. hptr->hname = (char *) malloc((strlen(hname) + 1) *
! ! ! ! ! ! ! ! ! ! sizeof(char));
Detecting leaks is easy; fixing them is, too
delHtab() {
15. int i;
16. HASHPTR hptr , zapptr;
17. for(i = 0; i < 3001; i++) {
18. hptr = hashtab[i];
19. if(hptr != (HASHPTR) NULL) {
20. zapptr = hptr ;
21. while(hptr->hnext != (HASHPTR) NULL) {
22.! ! hptr = hptr->hnext;
23.! ! free(zapptr);
24.! ! zapptr = hptr ;
25.! ! }
26.! ! free(hptr);
27.! }
28. }!
29. free(hashtab);
30. return;
}
free(hptr->hname)](https://image.slidesharecdn.com/coc-researchday-130605203706-phpapp02/85/Taint-based-Dynamic-Analysis-CoC-Research-Day-2009-29-320.jpg)