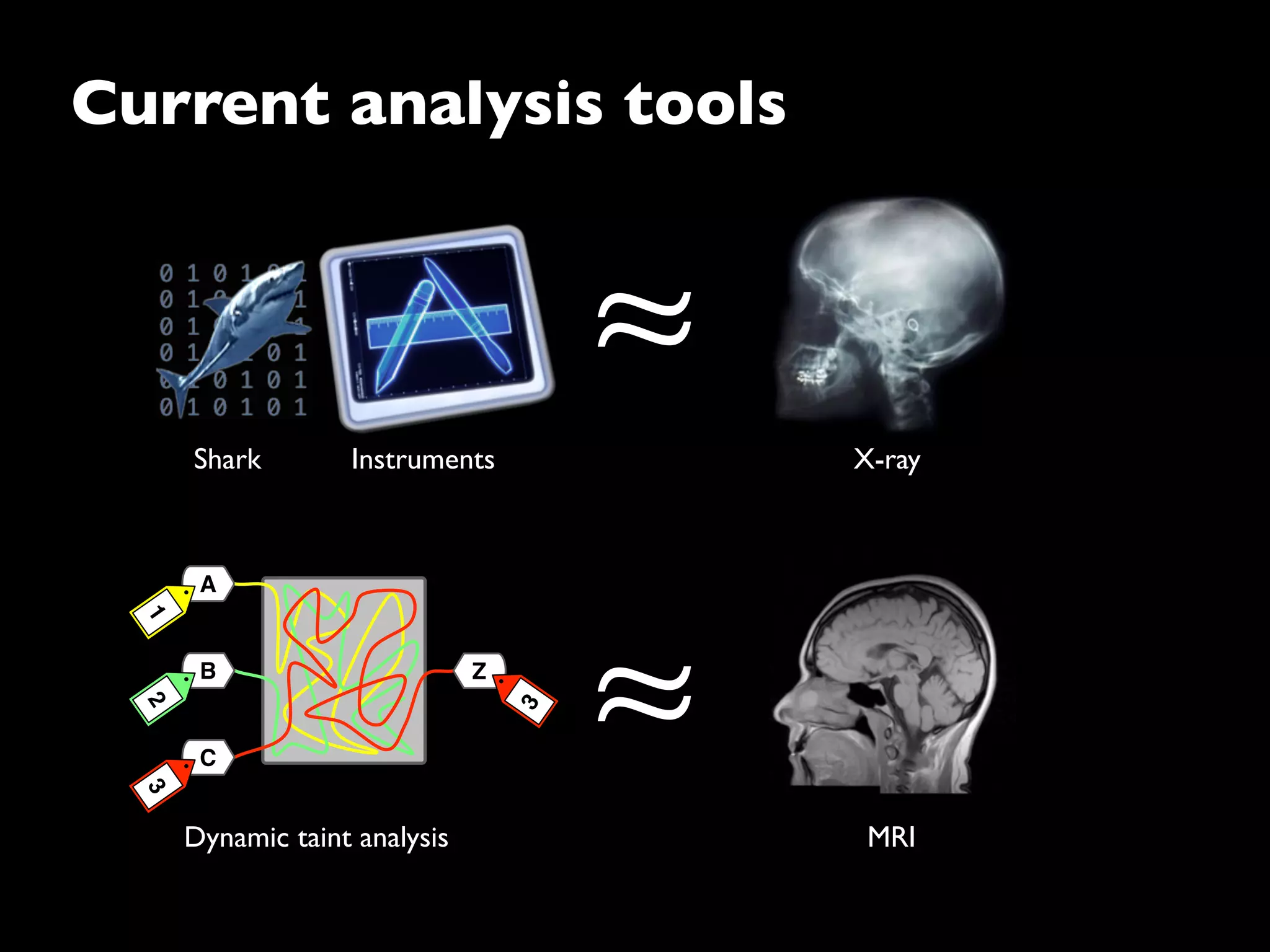
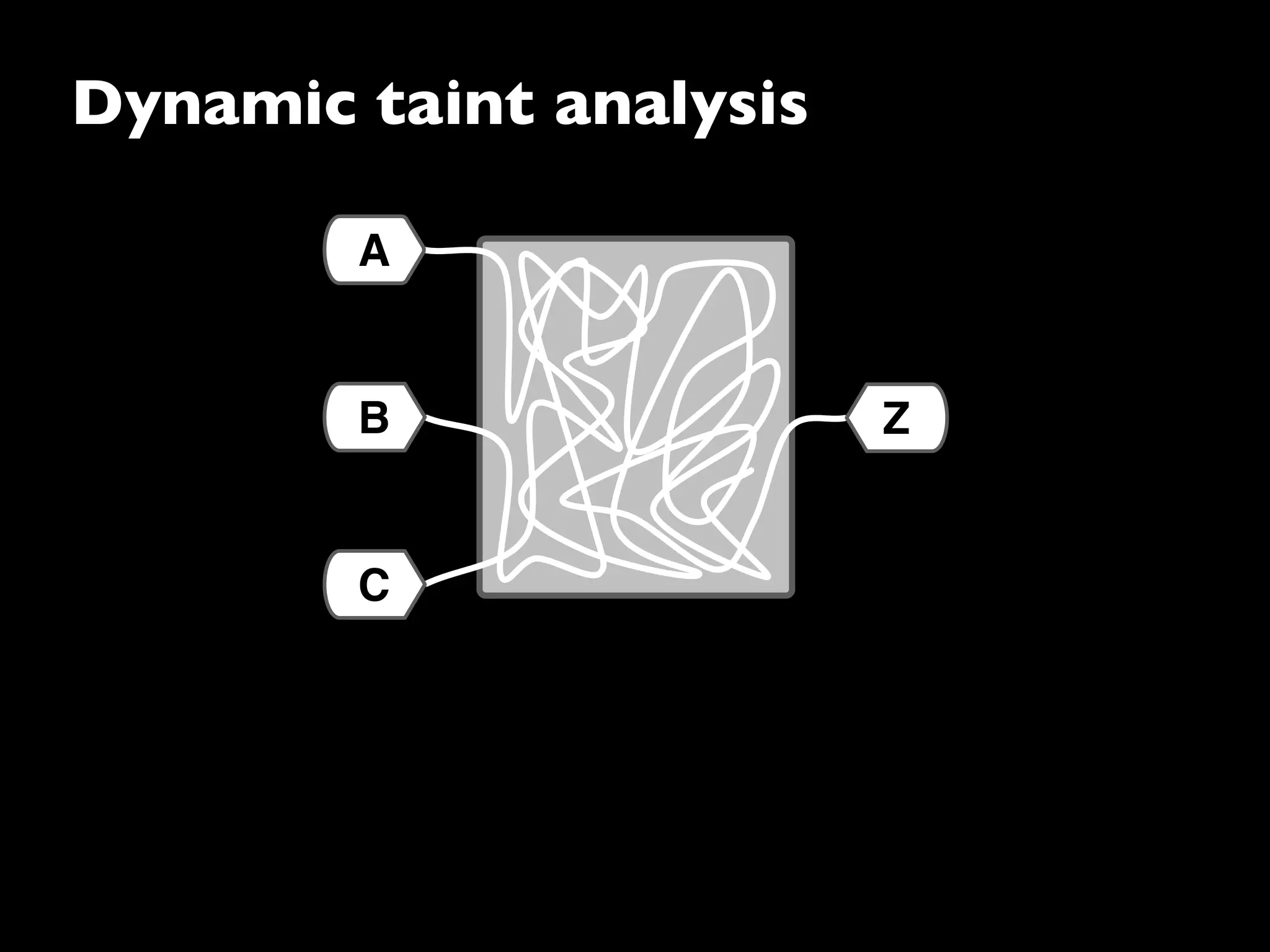
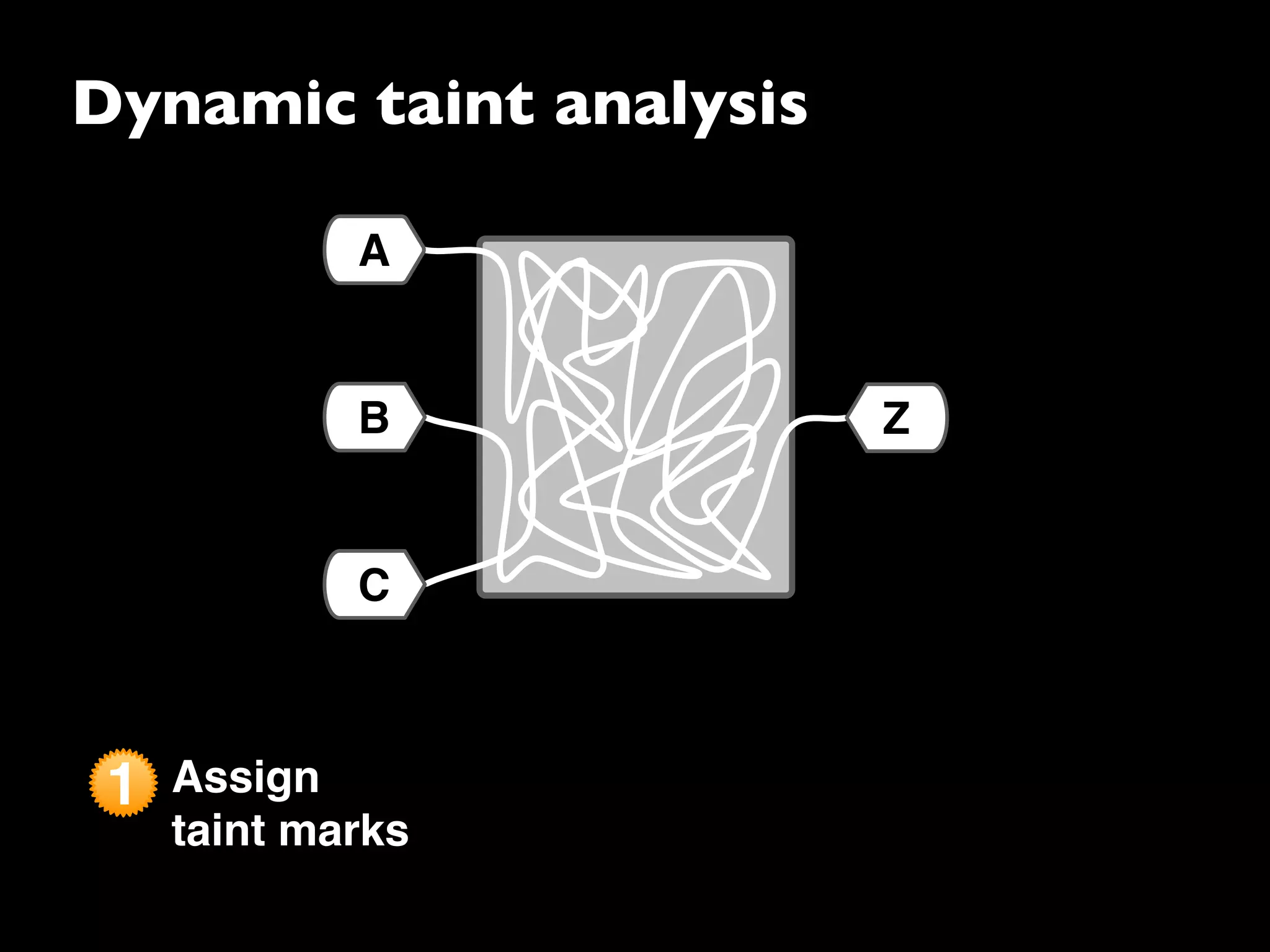
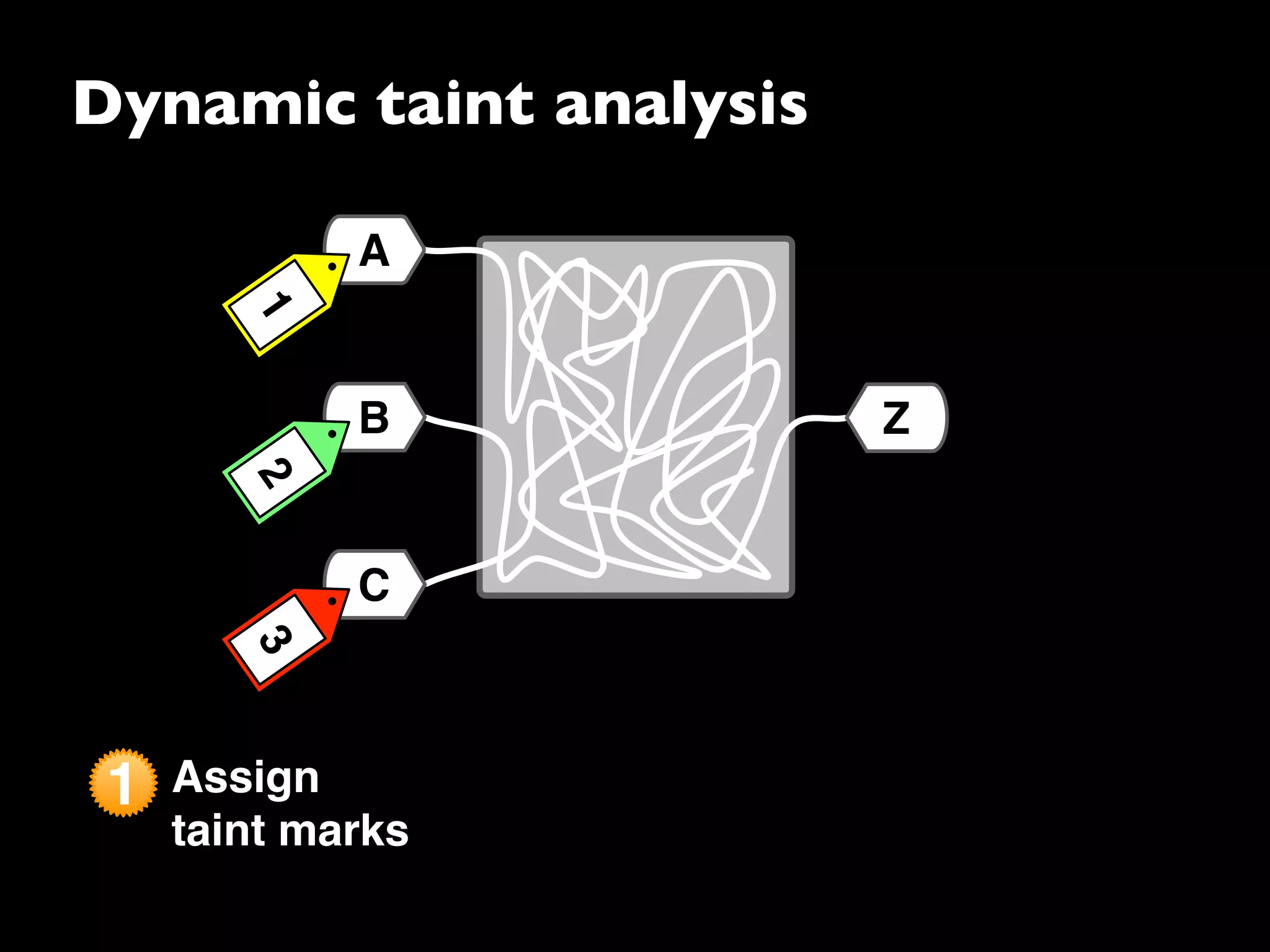
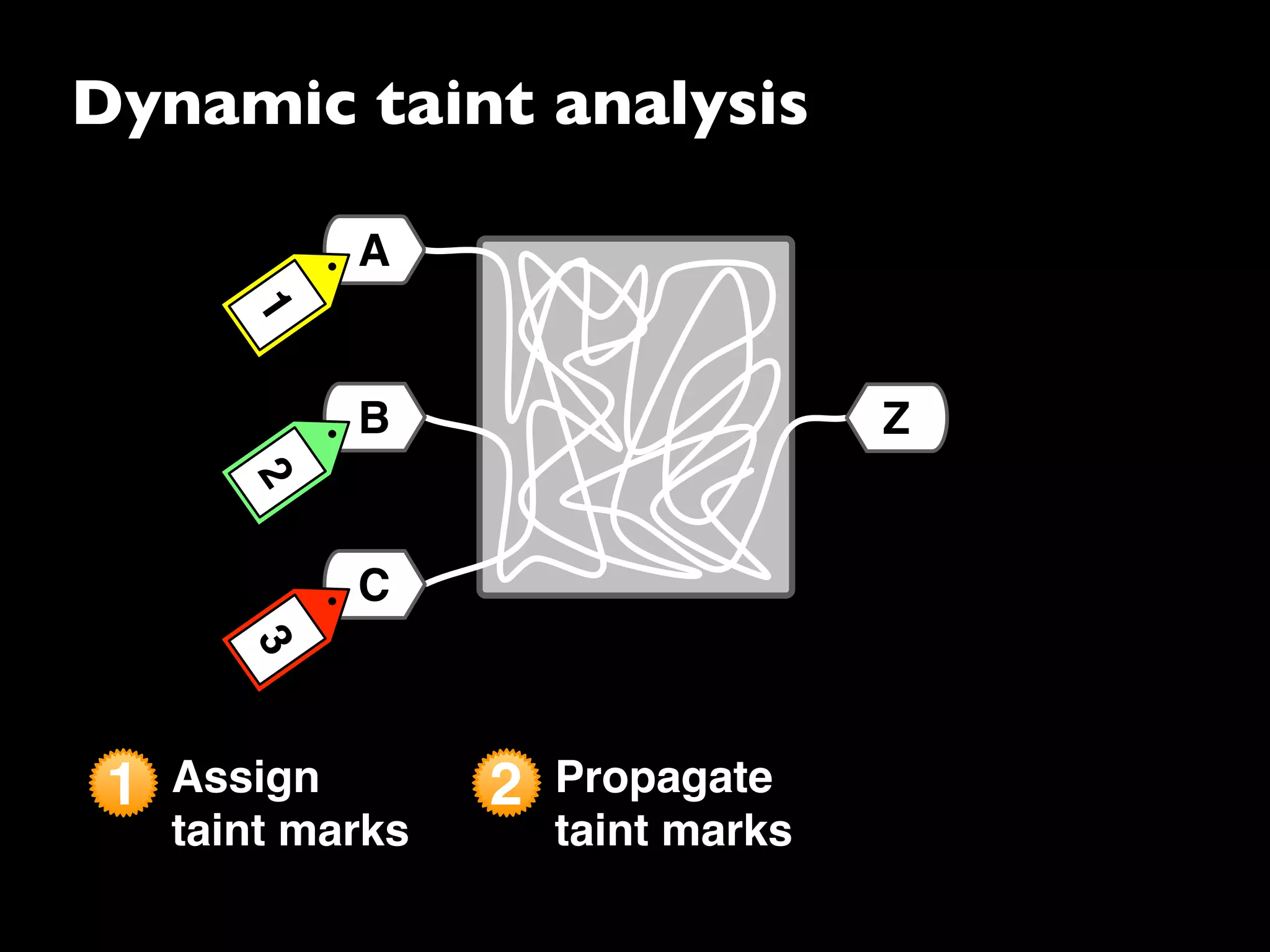
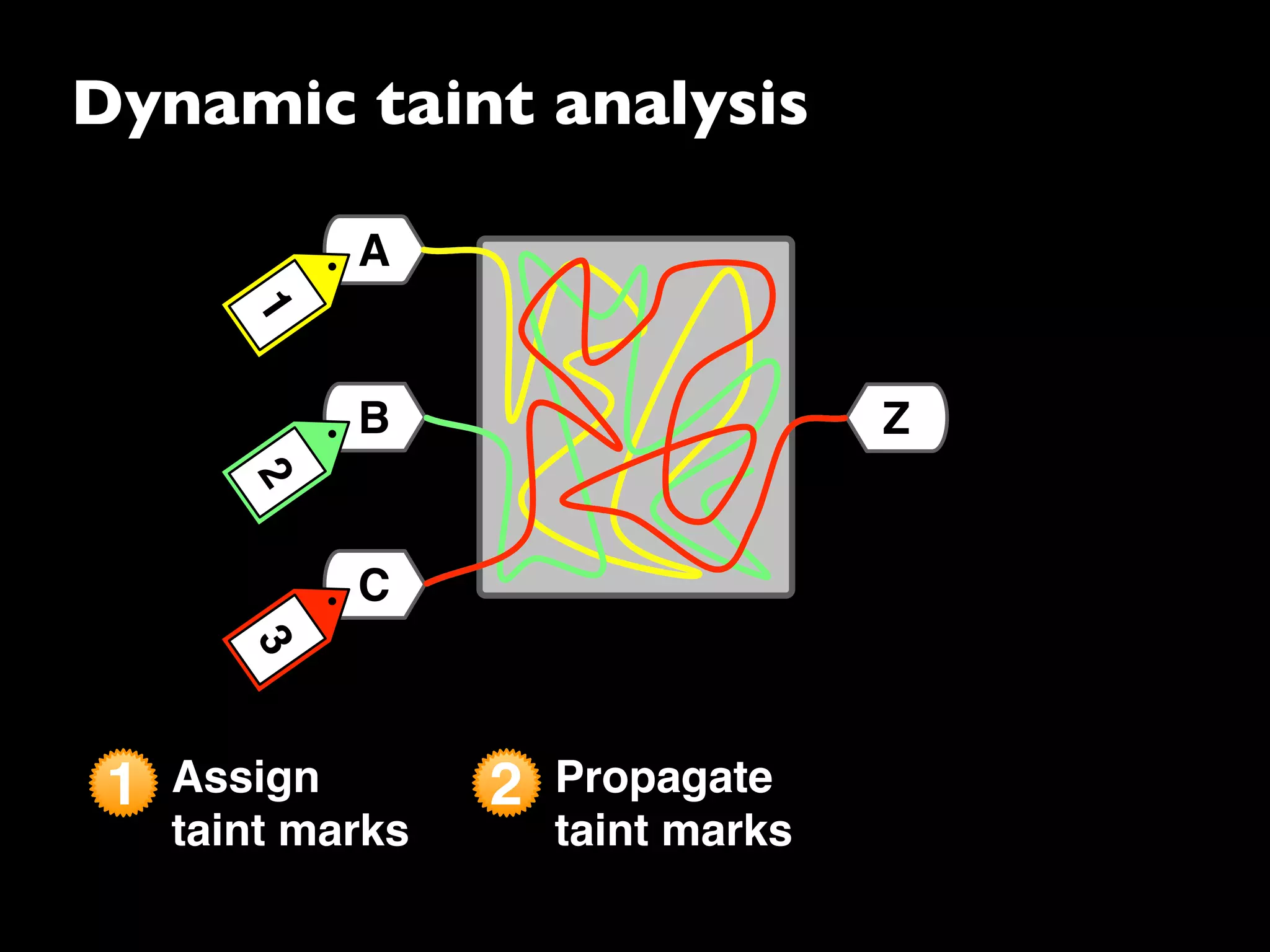
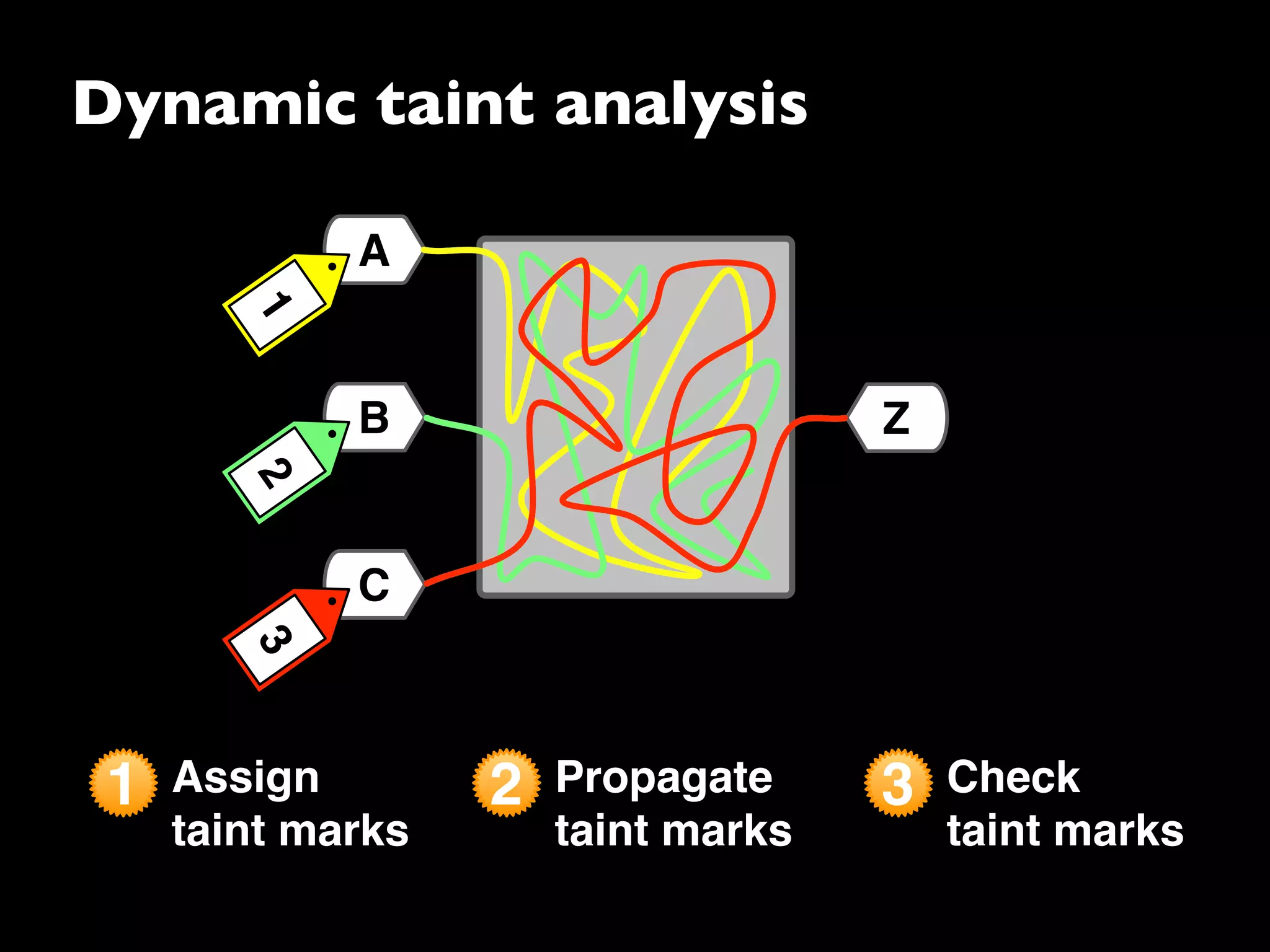
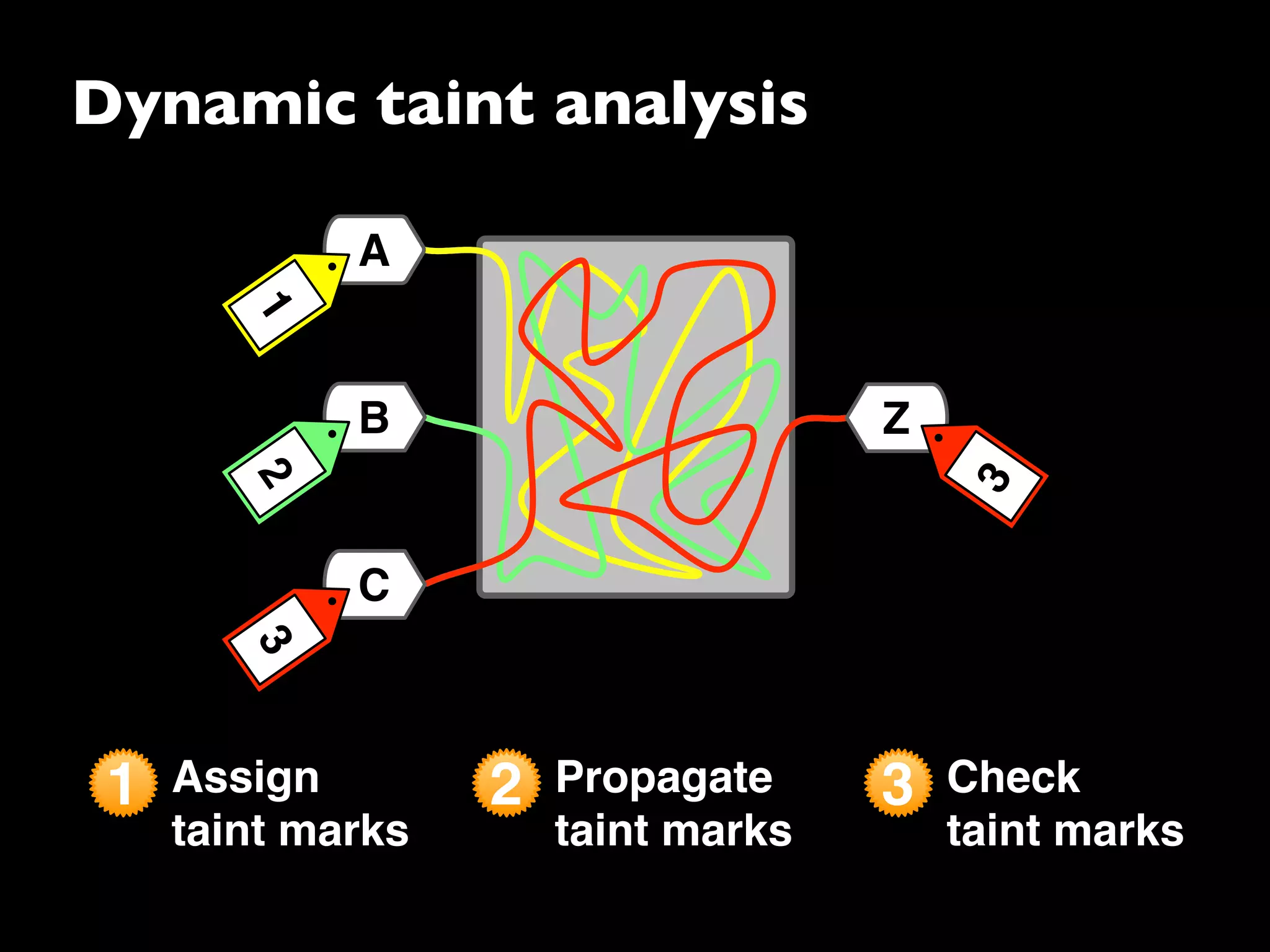
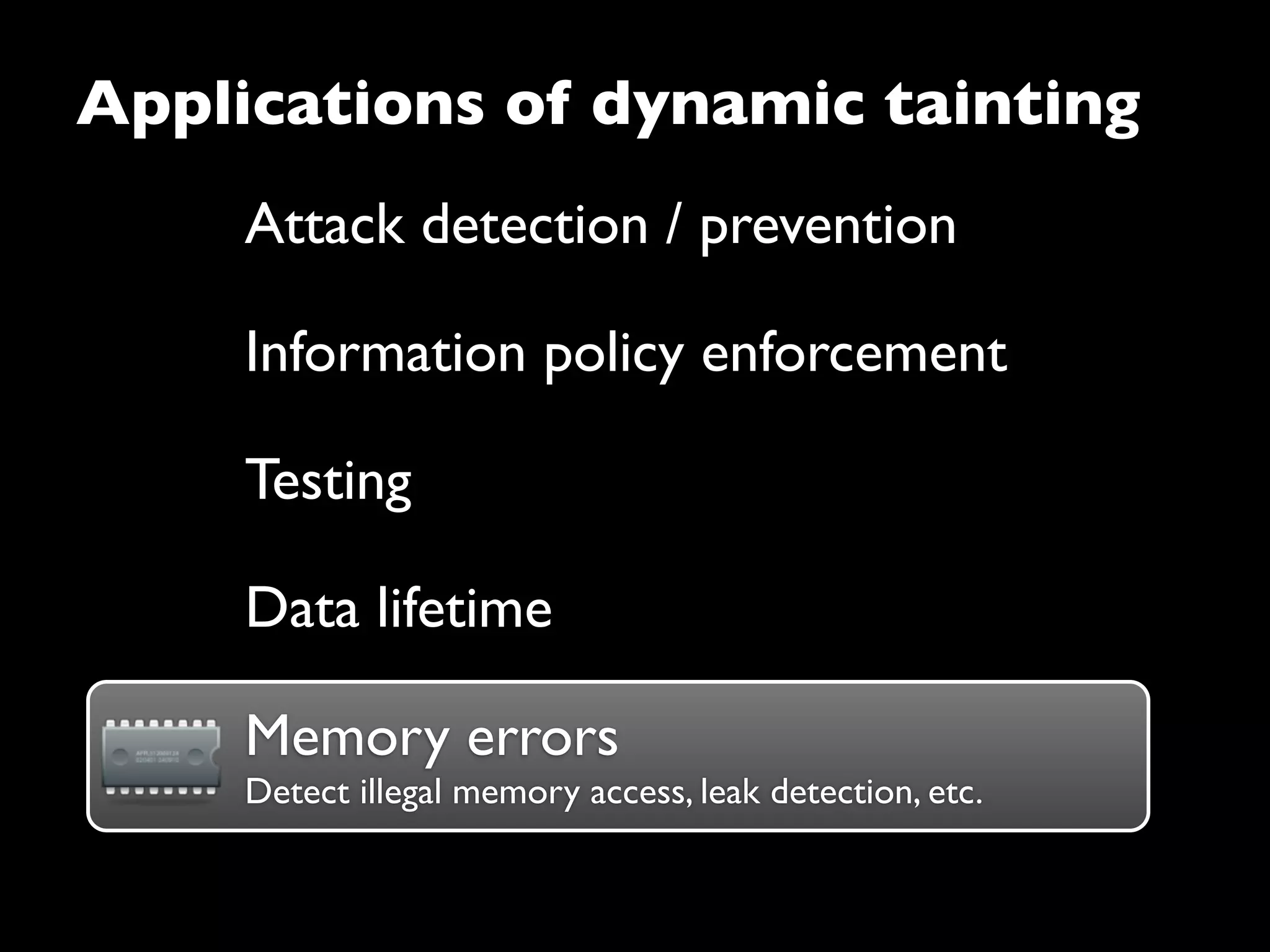
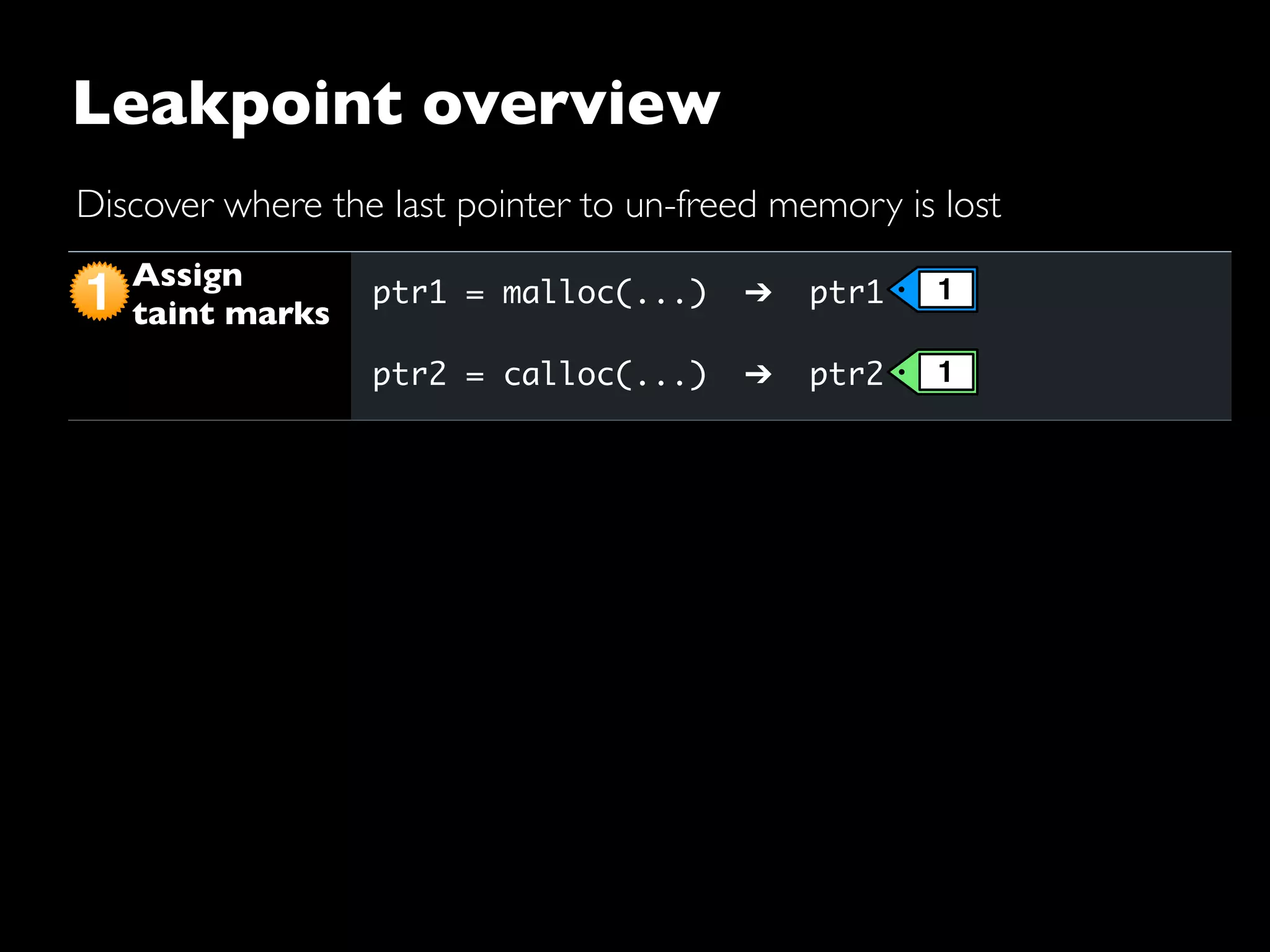
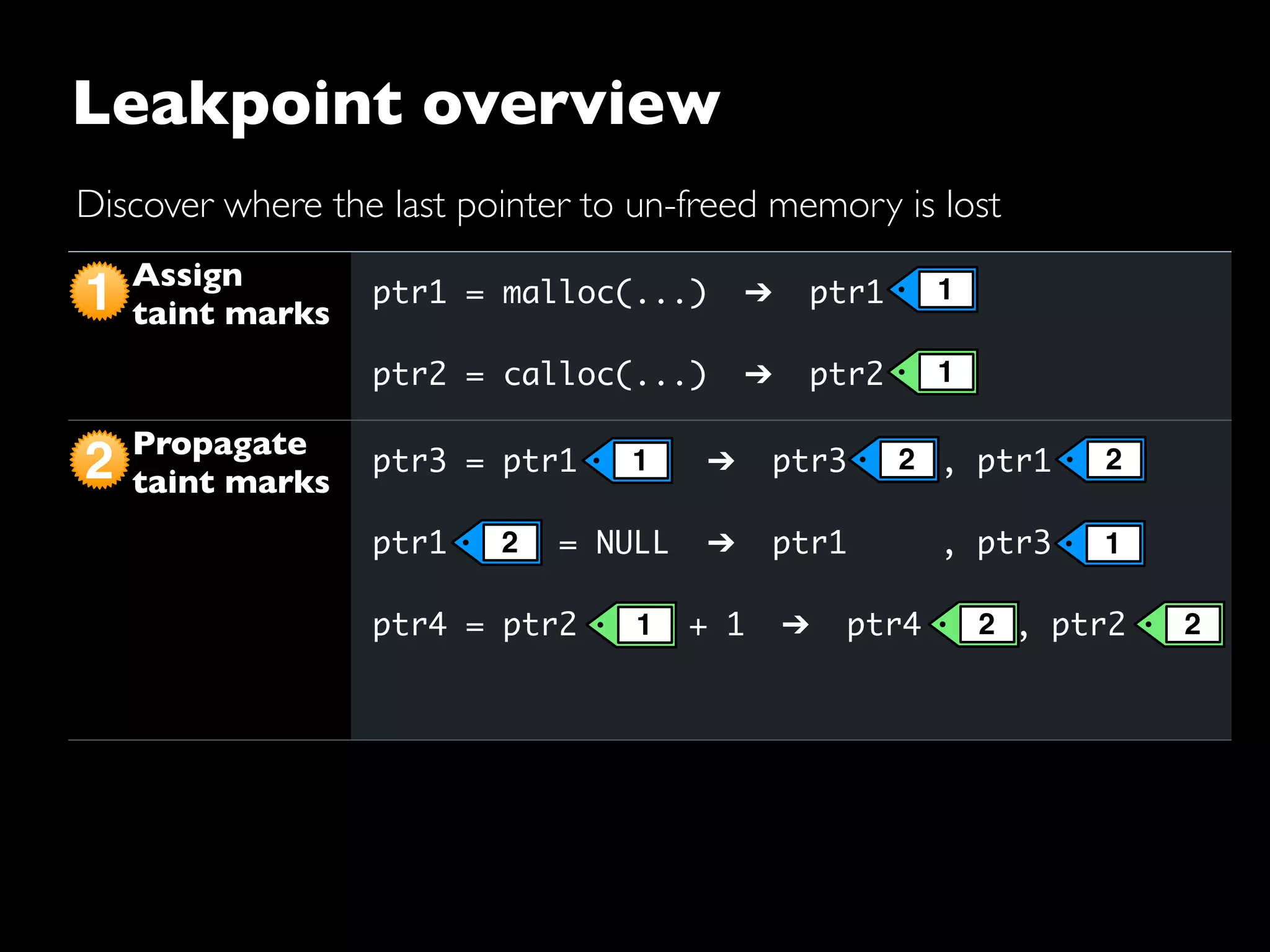
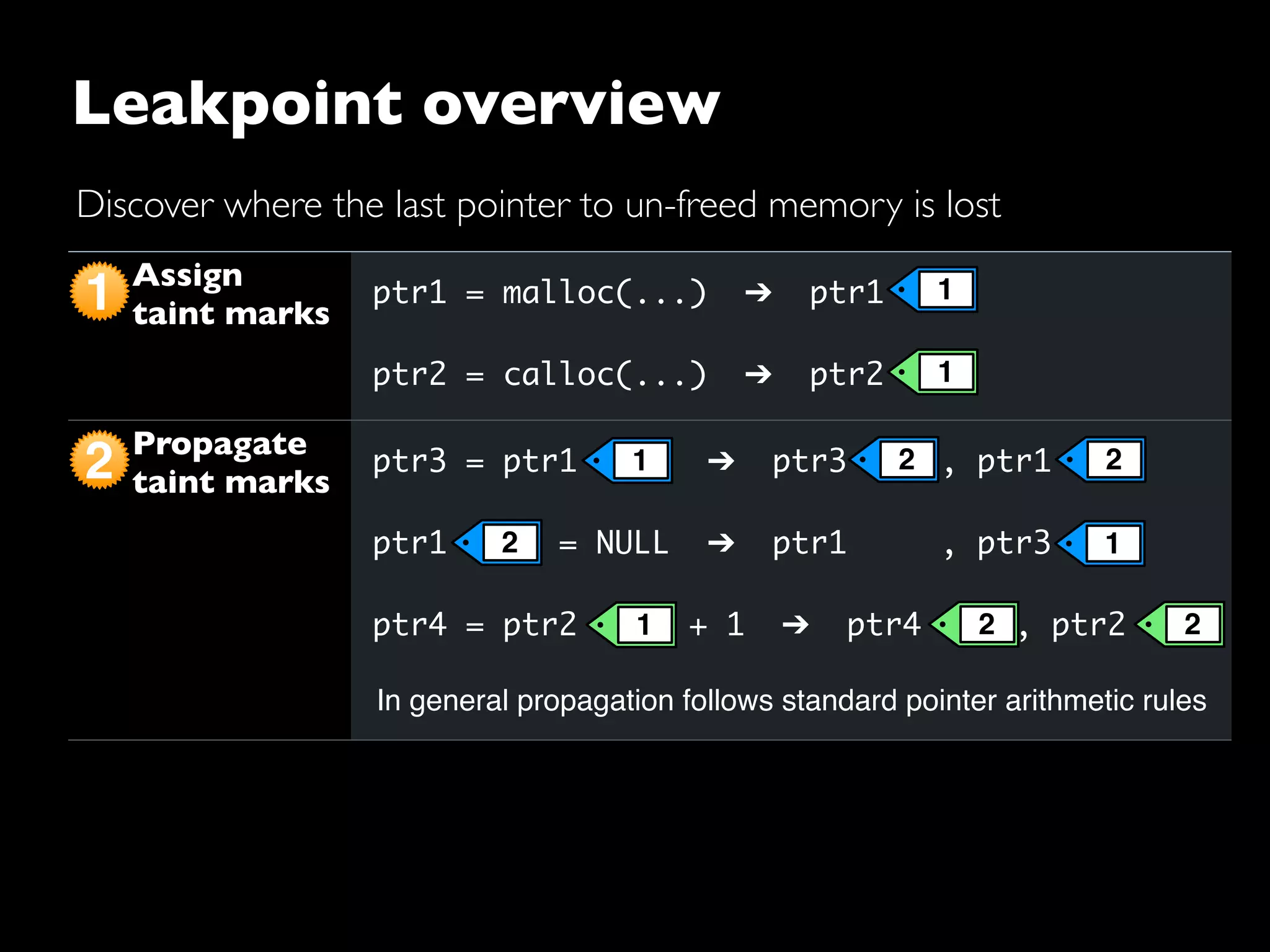
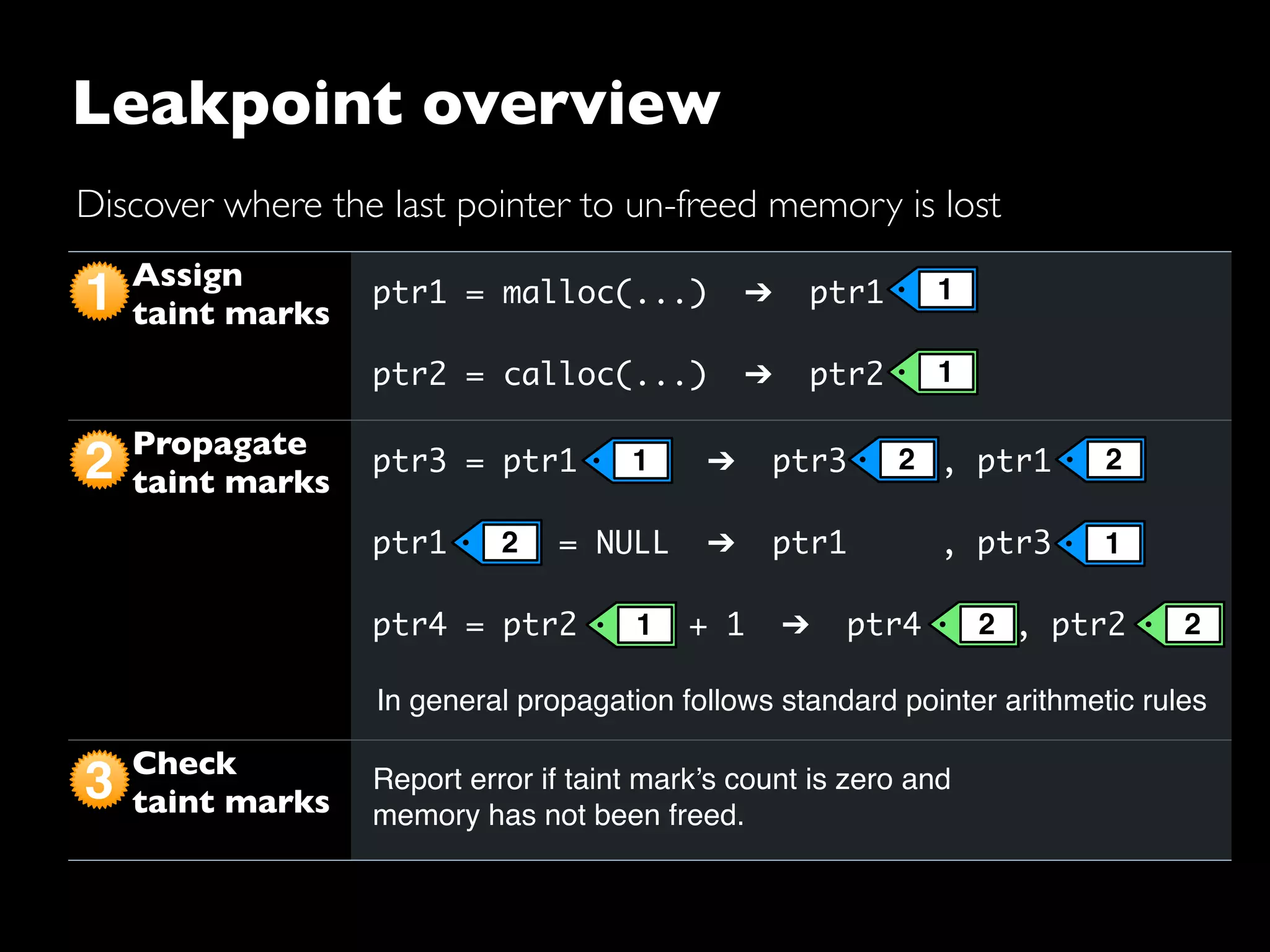
The document discusses advanced dynamic analysis techniques for leak detection. It describes how dynamic taint analysis works by assigning taint marks, propagating those marks, and checking the marks. This allows detecting where memory was allocated but not freed. The document outlines an implementation of leak detection as a Valgrind tool that intercepts memory functions and instruments instructions. It summarizes the current status of handling different languages and platforms. Future work ideas include improving the leakpoint tool and collaborating with Apple on new analysis techniques based on the experiences gained.






![Detecting leaks is easy, fixing them is hard
@interface Container:NSObject {
id _object;
}
@end
@implementation Container
- (void) dealloc {
//[_object release];
[super dealloc];
}
- (void) setObject:(id)obj {
[_object release];
_object = [obj retain];
}
@end](https://image.slidesharecdn.com/apple2008-130605203300-phpapp02/75/Advanced-Dynamic-Analysis-for-Leak-Detection-Apple-Internship-2008-22-2048.jpg)
![Detecting leaks is easy, fixing them is hard
@interface Container:NSObject {
id _object;
}
@end
@implementation Container
- (void) dealloc {
//[_object release];
[super dealloc];
}
- (void) setObject:(id)obj {
[_object release];
_object = [obj retain];
}
@end
Container *create() {
Container *c =
[[Container alloc] init];
NSObject *o =
[[NSObject alloc] init];
[c setObject:o];
[o release];
return c;
}
int main(...) {
Container *c = create();
…
[c release];
}](https://image.slidesharecdn.com/apple2008-130605203300-phpapp02/75/Advanced-Dynamic-Analysis-for-Leak-Detection-Apple-Internship-2008-23-2048.jpg)
![Detecting leaks is easy, fixing them is hard
@interface Container:NSObject {
id _object;
}
@end
@implementation Container
- (void) dealloc {
//[_object release];
[super dealloc];
}
- (void) setObject:(id)obj {
[_object release];
_object = [obj retain];
}
@end
Container *create() {
Container *c =
[[Container alloc] init];
NSObject *o =
[[NSObject alloc] init];
[c setObject:o];
[o release];
return c;
}
int main(...) {
Container *c = create();
…
[c release];
}
leaks:
This object is leaked](https://image.slidesharecdn.com/apple2008-130605203300-phpapp02/75/Advanced-Dynamic-Analysis-for-Leak-Detection-Apple-Internship-2008-24-2048.jpg)
![@interface Container:NSObject {
id _object;
}
@end
@implementation Container
- (void) dealloc {
[super dealloc];
}
- (void) setObject:(id)obj {
[_object release];
_object = [obj retain];
}
@end
Container *create() {
Container *c =
[[Container alloc] init];
NSObject *o =
[[NSObject alloc] init];
[c setObject:o];
[o release];
return c;
}
int main(...) {
Container *c = create();
…
[c release];
}
Detecting leaks is easy, fixing them is easier](https://image.slidesharecdn.com/apple2008-130605203300-phpapp02/75/Advanced-Dynamic-Analysis-for-Leak-Detection-Apple-Internship-2008-30-2048.jpg)
![@interface Container:NSObject {
id _object;
}
@end
@implementation Container
- (void) dealloc {
[super dealloc];
}
- (void) setObject:(id)obj {
[_object release];
_object = [obj retain];
}
@end
Container *create() {
Container *c =
[[Container alloc] init];
NSObject *o =
[[NSObject alloc] init];
[c setObject:o];
[o release];
return c;
}
int main(...) {
Container *c = create();
…
[c release];
}
leakpoint:
This object is leaked
Detecting leaks is easy, fixing them is easier](https://image.slidesharecdn.com/apple2008-130605203300-phpapp02/75/Advanced-Dynamic-Analysis-for-Leak-Detection-Apple-Internship-2008-31-2048.jpg)
![@interface Container:NSObject {
id _object;
}
@end
@implementation Container
- (void) dealloc {
[super dealloc];
}
- (void) setObject:(id)obj {
[_object release];
_object = [obj retain];
}
@end
Container *create() {
Container *c =
[[Container alloc] init];
NSObject *o =
[[NSObject alloc] init];
[c setObject:o];
[o release];
return c;
}
int main(...) {
Container *c = create();
…
[c release];
}
leakpoint:
Last reference was lost here
leakpoint:
This object is leaked
Detecting leaks is easy, fixing them is easier](https://image.slidesharecdn.com/apple2008-130605203300-phpapp02/75/Advanced-Dynamic-Analysis-for-Leak-Detection-Apple-Internship-2008-32-2048.jpg)
![@interface Container:NSObject {
id _object;
}
@end
@implementation Container
- (void) dealloc {
[super dealloc];
}
- (void) setObject:(id)obj {
[_object release];
_object = [obj retain];
}
@end
Container *create() {
Container *c =
[[Container alloc] init];
NSObject *o =
[[NSObject alloc] init];
[c setObject:o];
[o release];
return c;
}
int main(...) {
Container *c = create();
…
[c release];
}
[_object release];
leakpoint:
Last reference was lost here
leakpoint:
This object is leaked
Detecting leaks is easy, fixing them is easier](https://image.slidesharecdn.com/apple2008-130605203300-phpapp02/75/Advanced-Dynamic-Analysis-for-Leak-Detection-Apple-Internship-2008-33-2048.jpg)

![Lost pointer to 0x1C93AC0 (16 bytes)
allocated at:
at calloc+105
by _internal_class_createInstanceFromZone+149
by _internal_class_createInstance+31
by +[NSObject allocWithZone:]+155 (NSObject.m:445)
by +[NSObject alloc]+41 (NSObject.m:432)
by create+97 (main.m:29)
by main+17 (main.m:38)
leaked at:
at free+103
by _internal_object_dispose+81
by NSDeallocateObject+223 (NSObject.m:207)
by -[Container dealloc]+53 (container.m:13)
by main+43 (main.m:40)
Leakpoint implementation
• Implemented as aValgrind tool (www.valgrind.org)
■ intercept libc memory management functions
■ instrument binary instructions to perform propagation](https://image.slidesharecdn.com/apple2008-130605203300-phpapp02/75/Advanced-Dynamic-Analysis-for-Leak-Detection-Apple-Internship-2008-35-2048.jpg)
![leaks
Lost pointer to 0x1C93AC0 (16 bytes)
allocated at:
at calloc+105
by _internal_class_createInstanceFromZone+149
by _internal_class_createInstance+31
by +[NSObject allocWithZone:]+155 (NSObject.m:445)
by +[NSObject alloc]+41 (NSObject.m:432)
by create+97 (main.m:29)
by main+17 (main.m:38)
leaked at:
at free+103
by _internal_object_dispose+81
by NSDeallocateObject+223 (NSObject.m:207)
by -[Container dealloc]+53 (container.m:13)
by main+43 (main.m:40)
Leakpoint implementation
• Implemented as aValgrind tool (www.valgrind.org)
■ intercept libc memory management functions
■ instrument binary instructions to perform propagation](https://image.slidesharecdn.com/apple2008-130605203300-phpapp02/75/Advanced-Dynamic-Analysis-for-Leak-Detection-Apple-Internship-2008-36-2048.jpg)
![leakpoint
leaks
Lost pointer to 0x1C93AC0 (16 bytes)
allocated at:
at calloc+105
by _internal_class_createInstanceFromZone+149
by _internal_class_createInstance+31
by +[NSObject allocWithZone:]+155 (NSObject.m:445)
by +[NSObject alloc]+41 (NSObject.m:432)
by create+97 (main.m:29)
by main+17 (main.m:38)
leaked at:
at free+103
by _internal_object_dispose+81
by NSDeallocateObject+223 (NSObject.m:207)
by -[Container dealloc]+53 (container.m:13)
by main+43 (main.m:40)
Leakpoint implementation
• Implemented as aValgrind tool (www.valgrind.org)
■ intercept libc memory management functions
■ instrument binary instructions to perform propagation](https://image.slidesharecdn.com/apple2008-130605203300-phpapp02/75/Advanced-Dynamic-Analysis-for-Leak-Detection-Apple-Internship-2008-37-2048.jpg)





![A real leak?: _NSImageMalloc
void *_NSImageMalloc(NSZone* zone, size_t size) {
// allocate storage aligned to 32 bytes. we do this by
// allocating an extra 32 bytes, finding the address in the proper
// location and storing the delta in one of the previous 32 bytes.
void *unaligned = NSZoneMalloc(zone, size + BITMAP_DATA_ALIGNMENT);
if(unaligned != NULL) {
uintptr_t aligned = ((uintptr_t)unaligned + BITMAP_DATA_ALIGNMENT)
& ~(BITMAP_DATA_ALIGNMENT - 1);
(unsigned char*)aligned[-1] = aligned - (uintptr_t) unaligned;
return (void*)aligned;
}
else {
return NULL;
}
}](https://image.slidesharecdn.com/apple2008-130605203300-phpapp02/75/Advanced-Dynamic-Analysis-for-Leak-Detection-Apple-Internship-2008-47-2048.jpg)