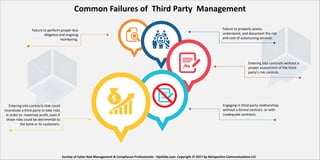
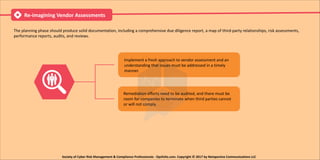
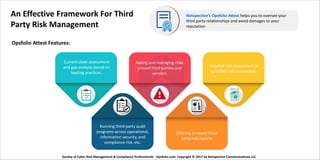
The document discusses the challenges of third-party risk management, highlighting the serious repercussions of data breaches and the importance of conducting thorough due diligence on vendors. It outlines common failures in managing third-party relationships and emphasizes the need for detailed documentation and timely assessments to mitigate risks. The document also introduces 'Opsfolio Attest' as a tool for overseeing third-party relationships and improving risk management practices.