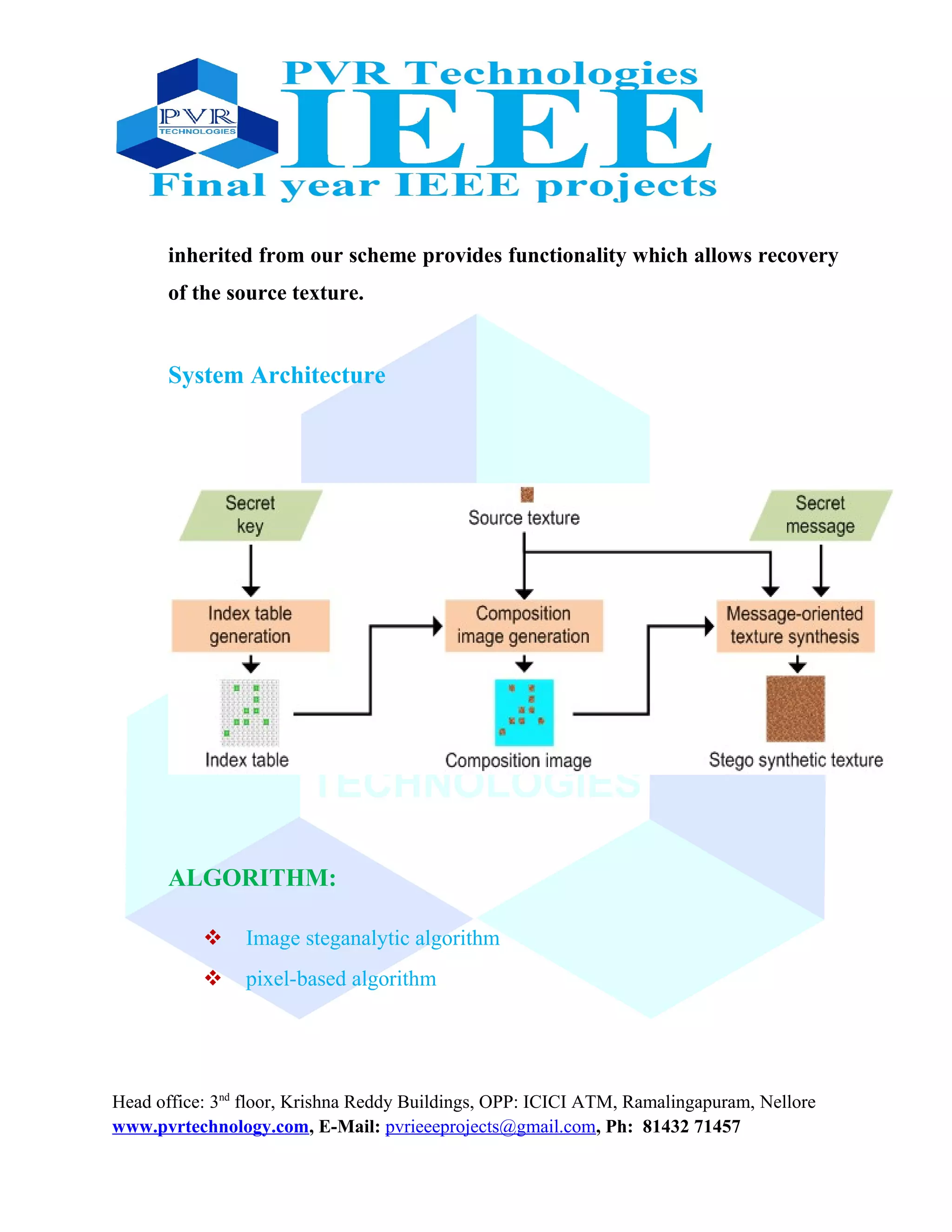
The document proposes a novel steganography approach using reversible texture synthesis. It conceals secret messages by embedding them during a texture synthesis process rather than in an existing cover image. This allows extraction of the secret messages and original source texture. The approach offers high embedding capacity proportional to the stego image size, is difficult to detect through steganalysis, and allows recovery of the source texture. Experimental results verified it can provide variable embedding capacities while producing visually plausible textures that recover the source.