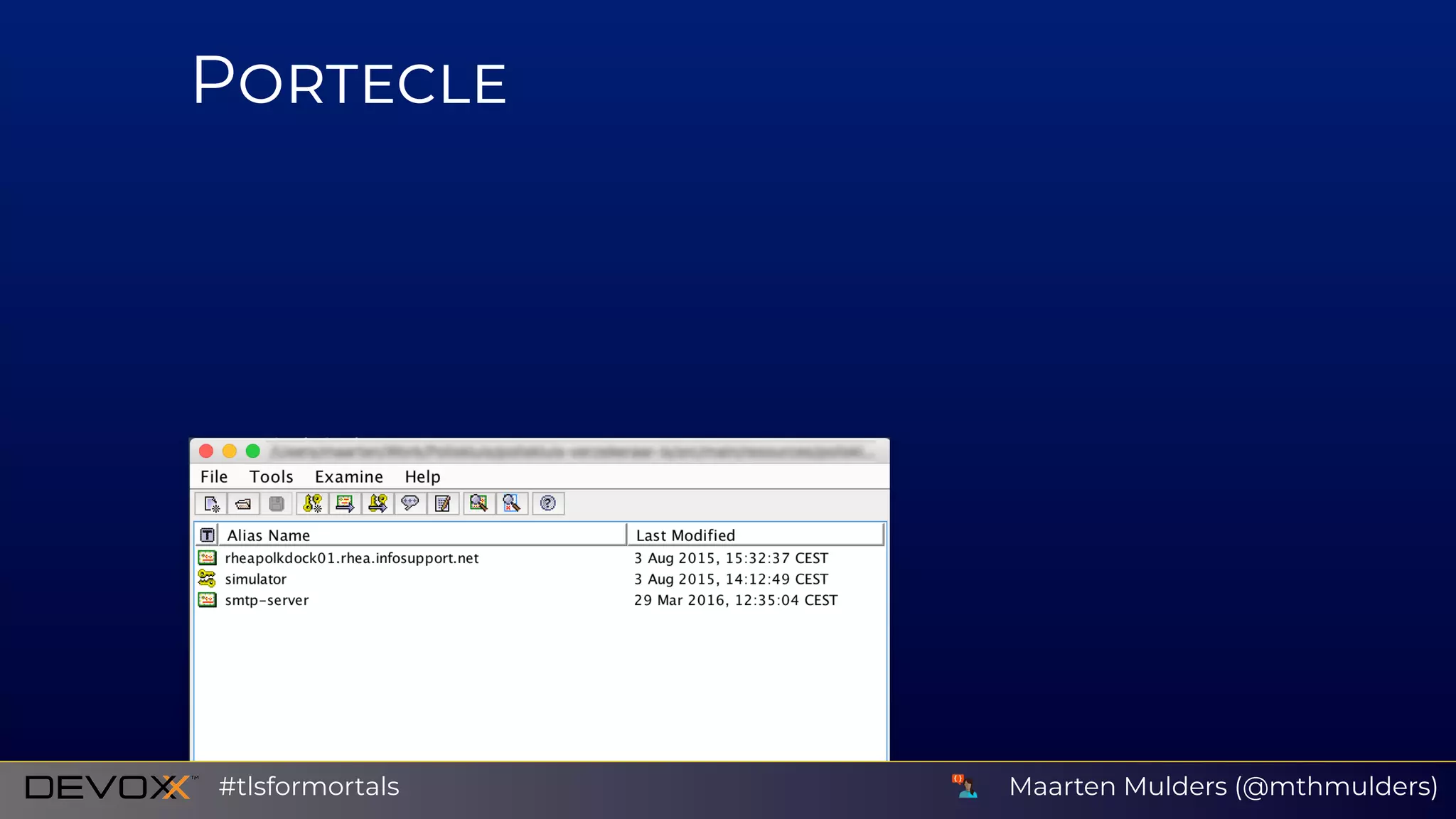
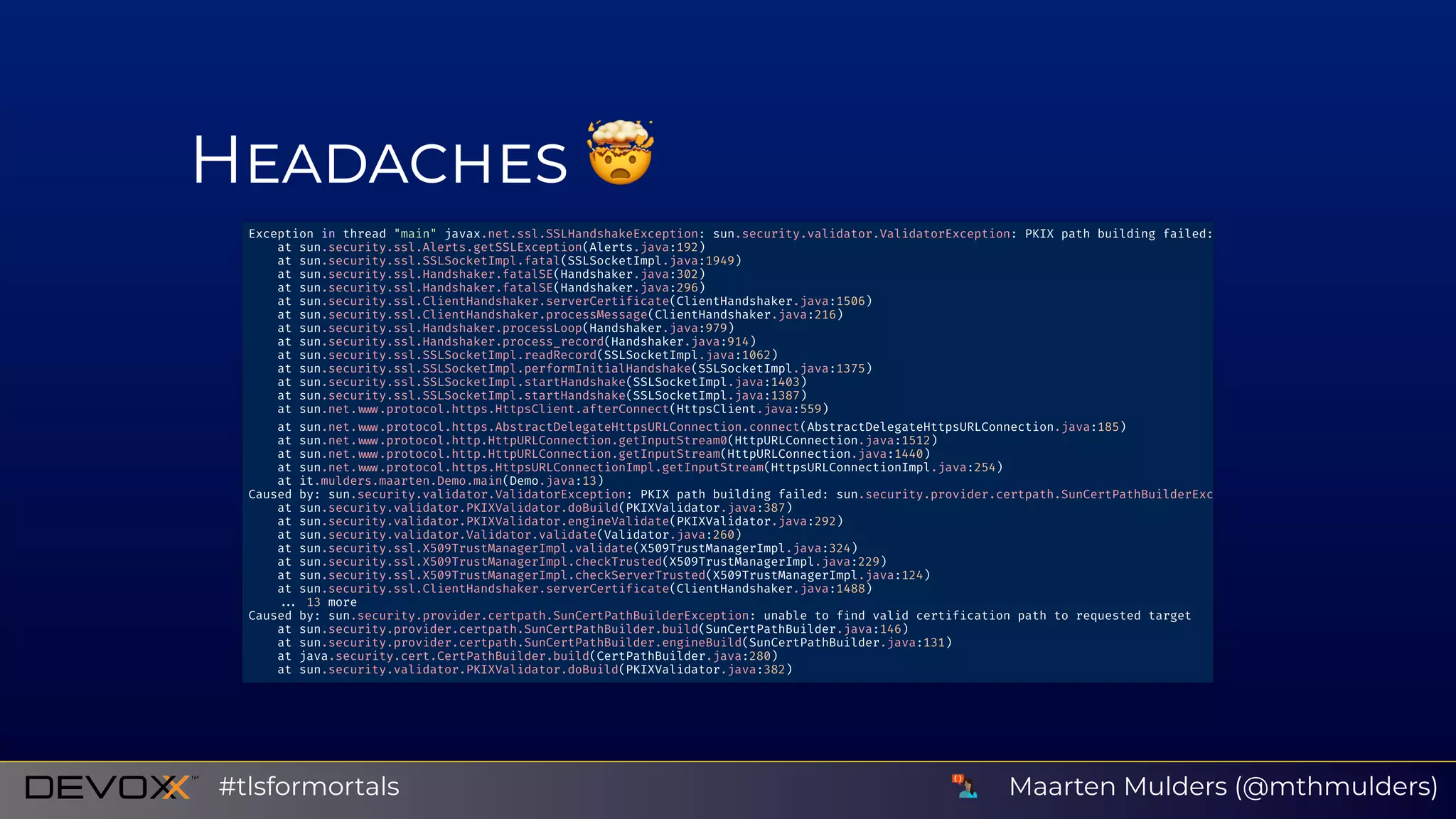
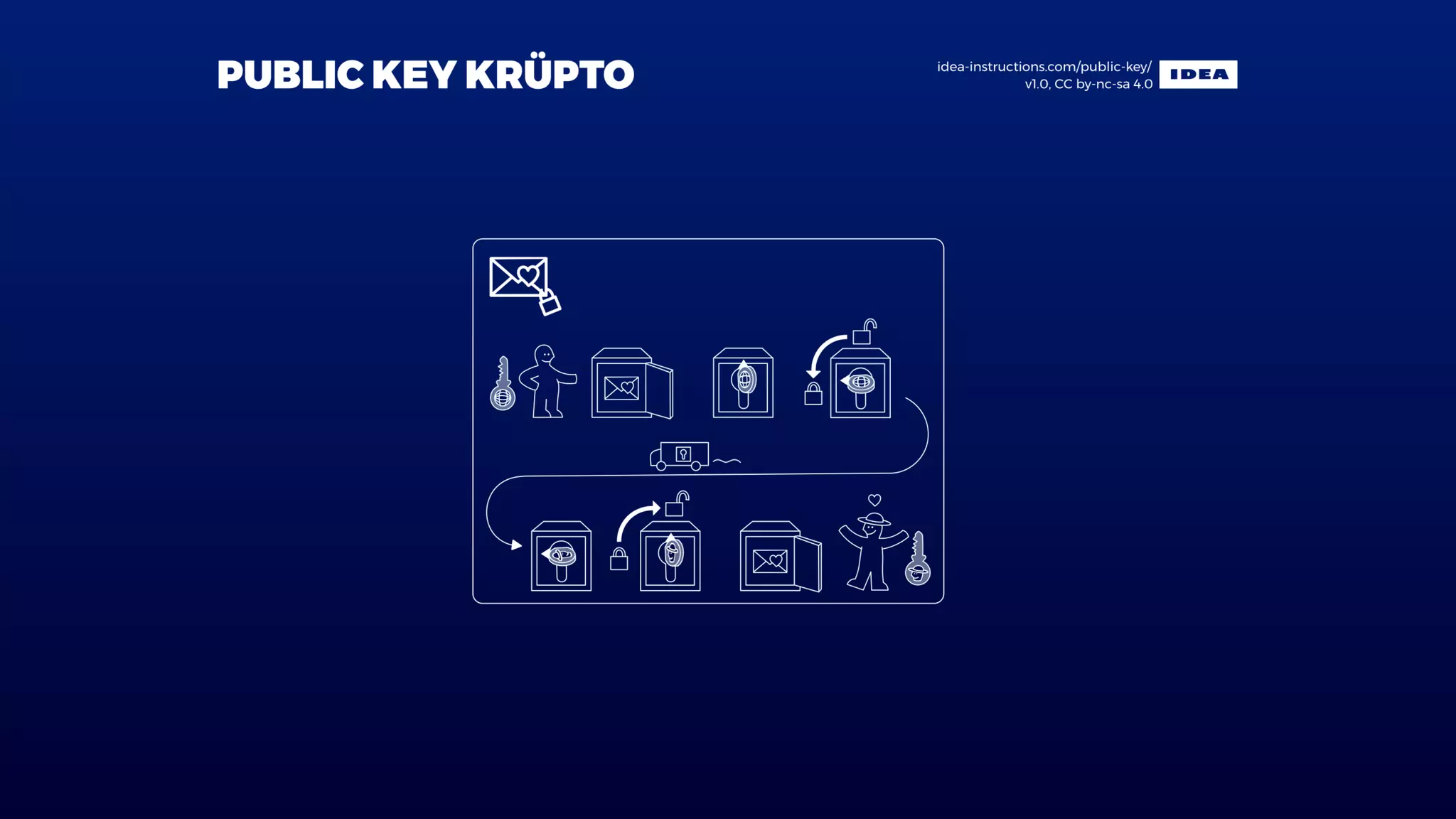
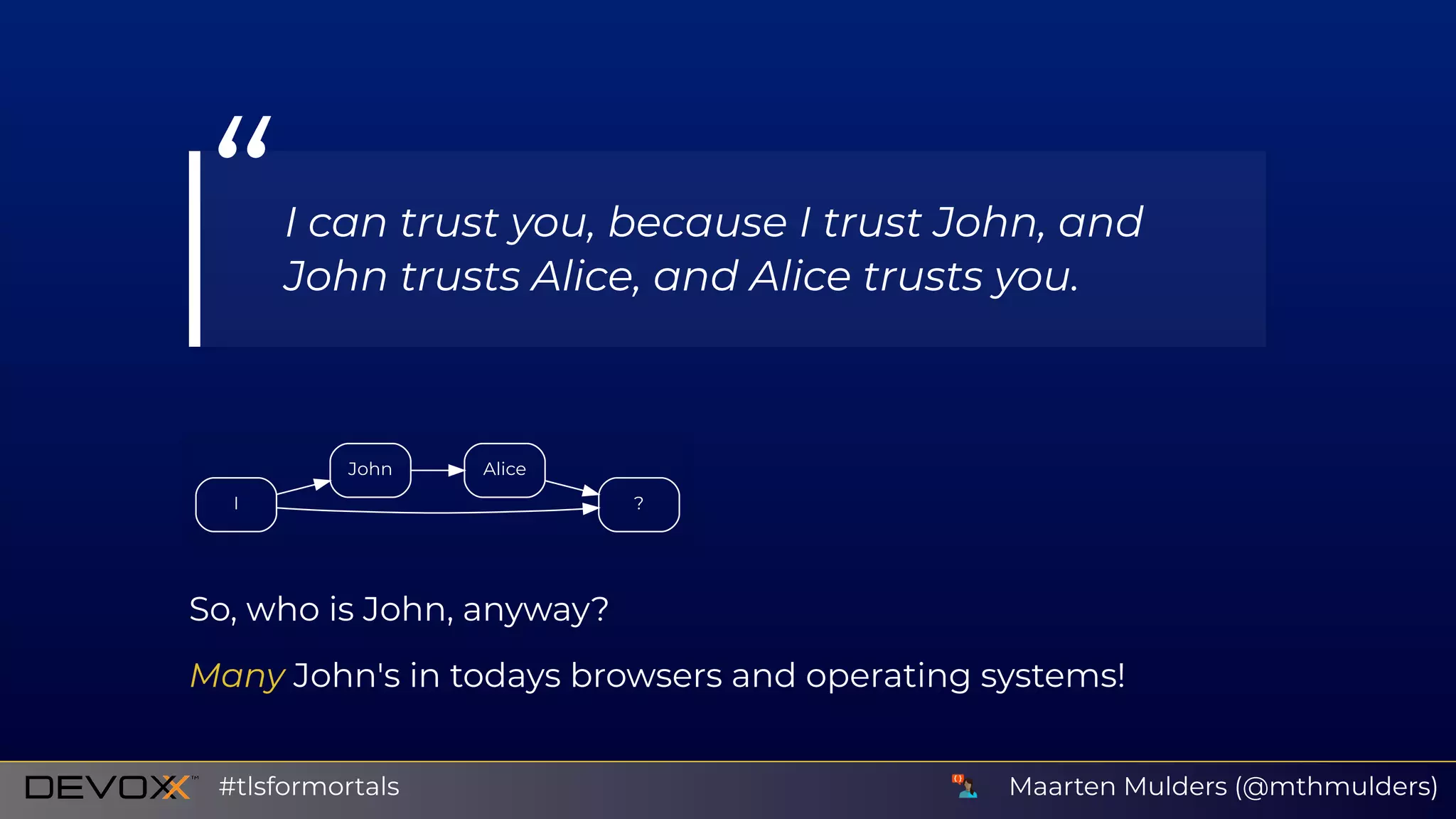
The document discusses issues related to SSL/TLS protocols and certificate validation errors, specifically highlighting a javax.net.ssl.SSLHandshakeException occurring due to a failure to build a valid certification path. It covers key concepts in public/private key encryption, signing certificates, and the roles of certificate authorities. Additionally, it emphasizes security best practices, including recommendations to avoid SSL and trust only valid certificates.





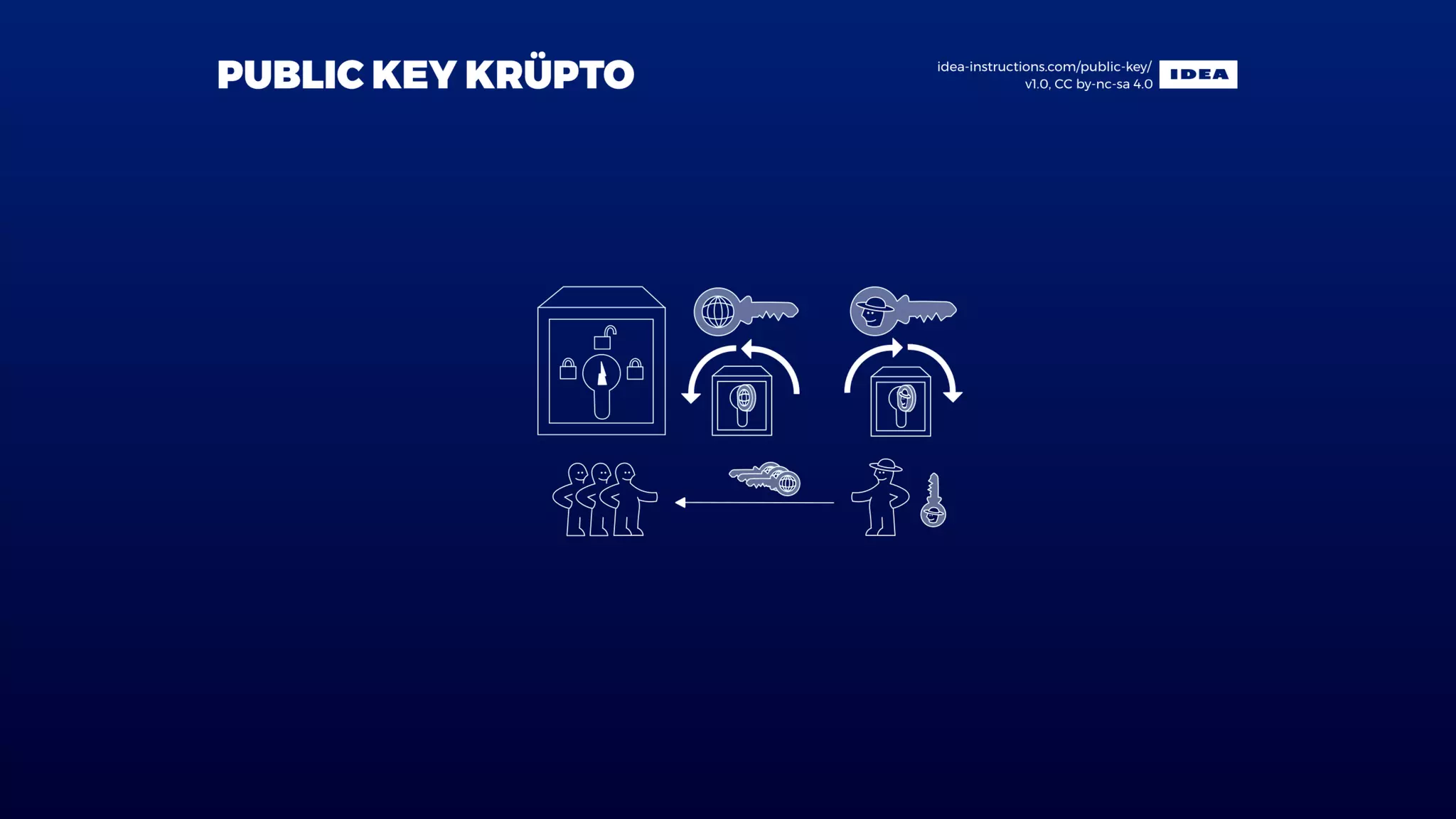
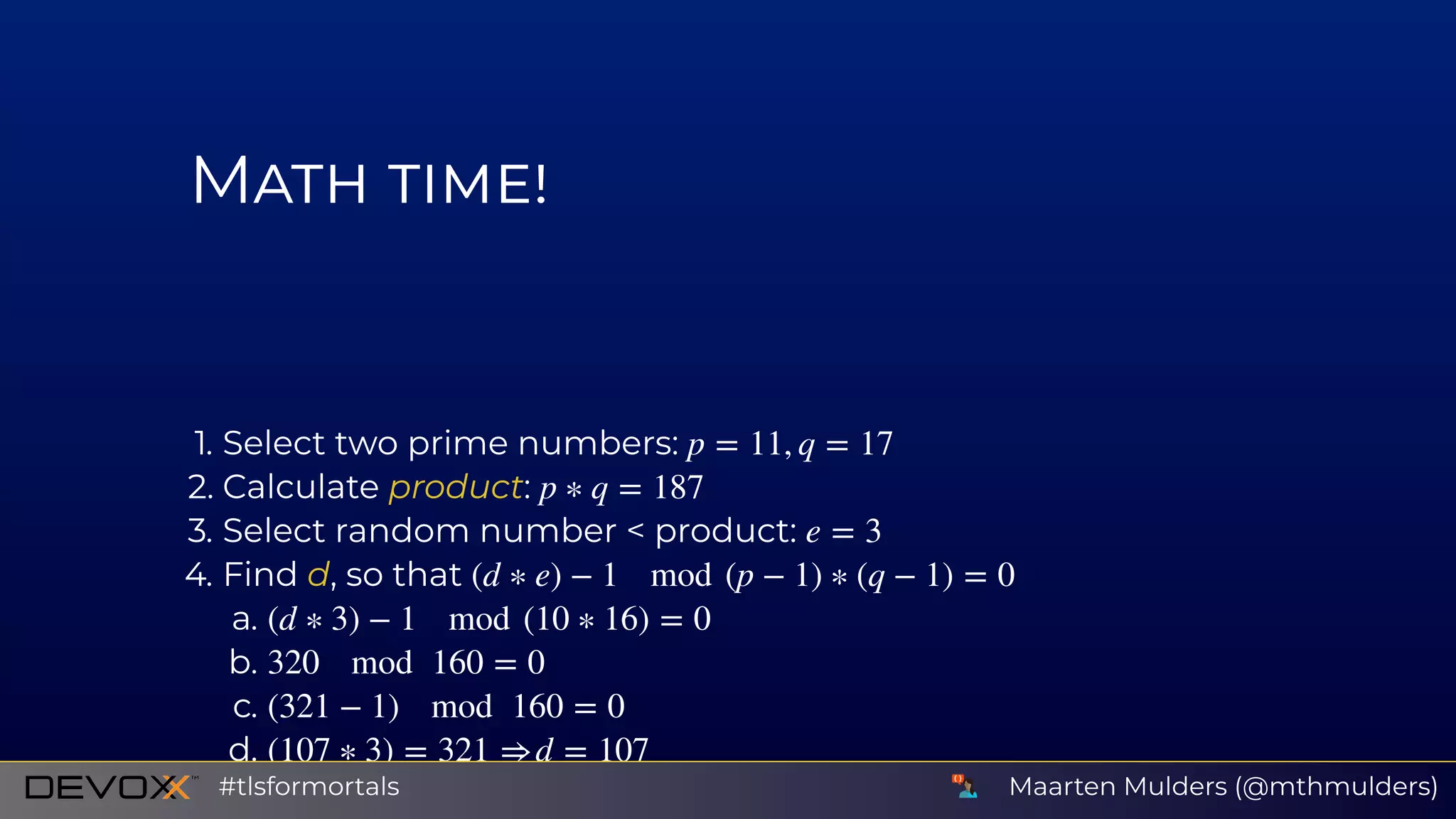
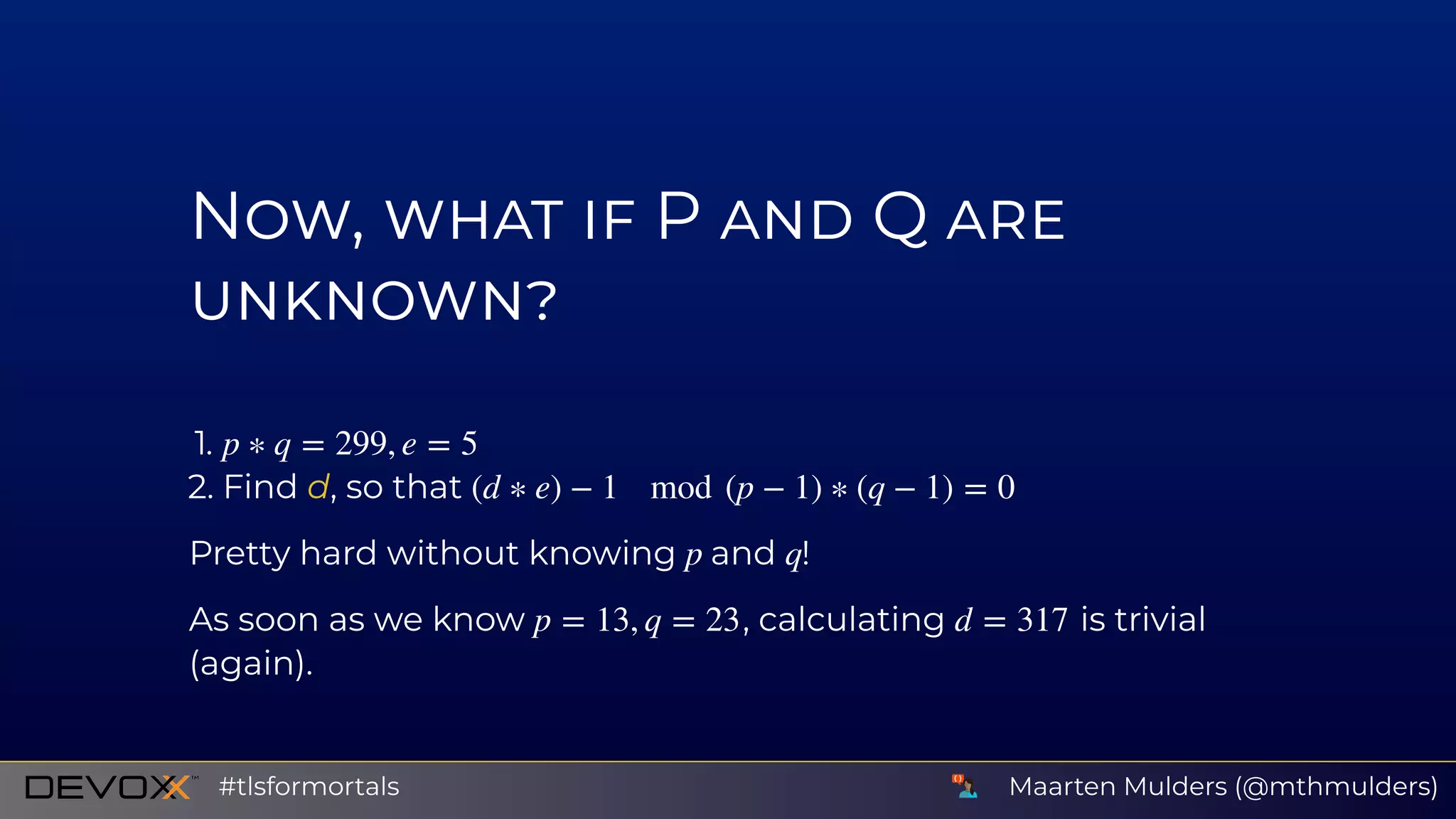

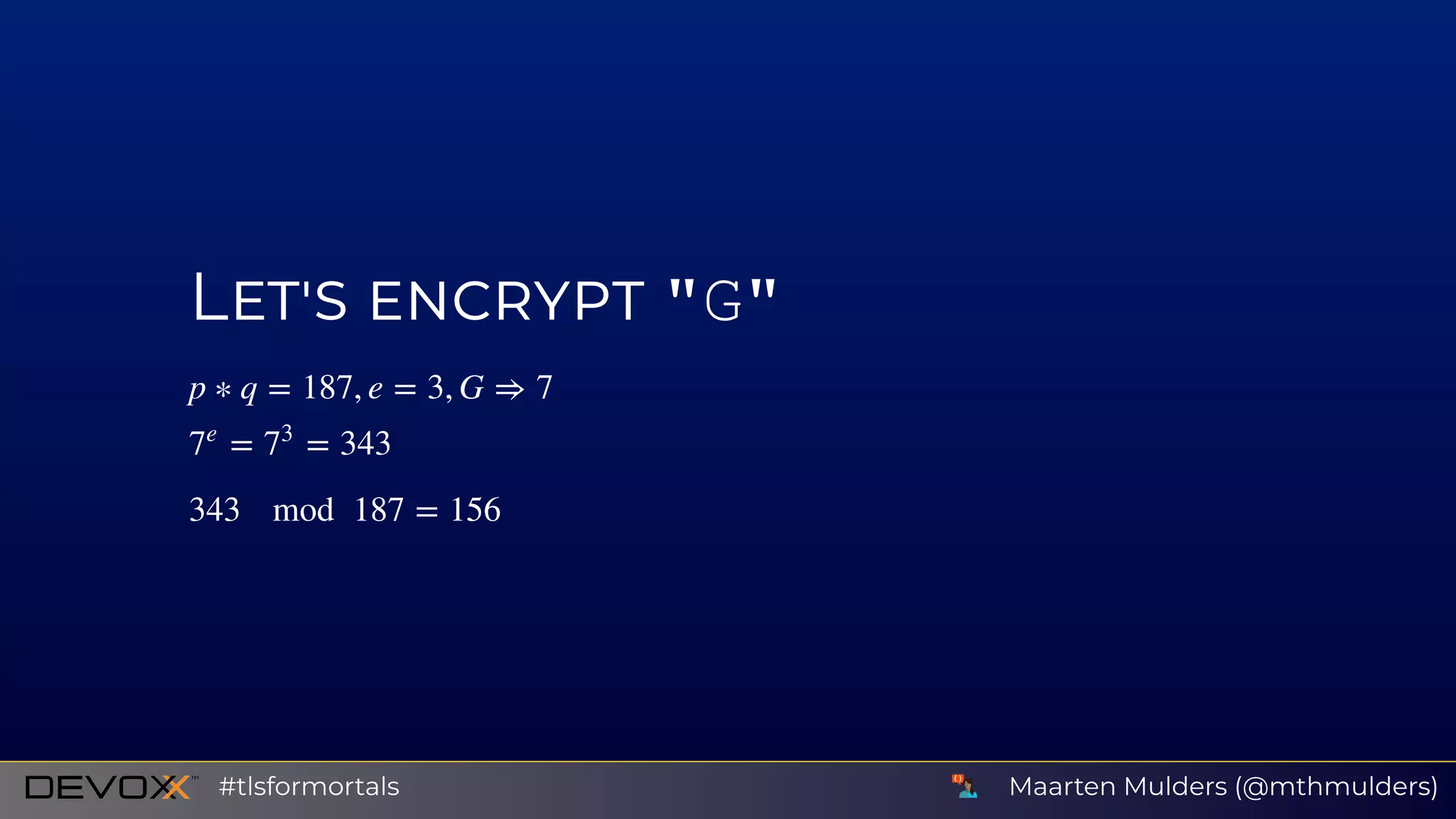


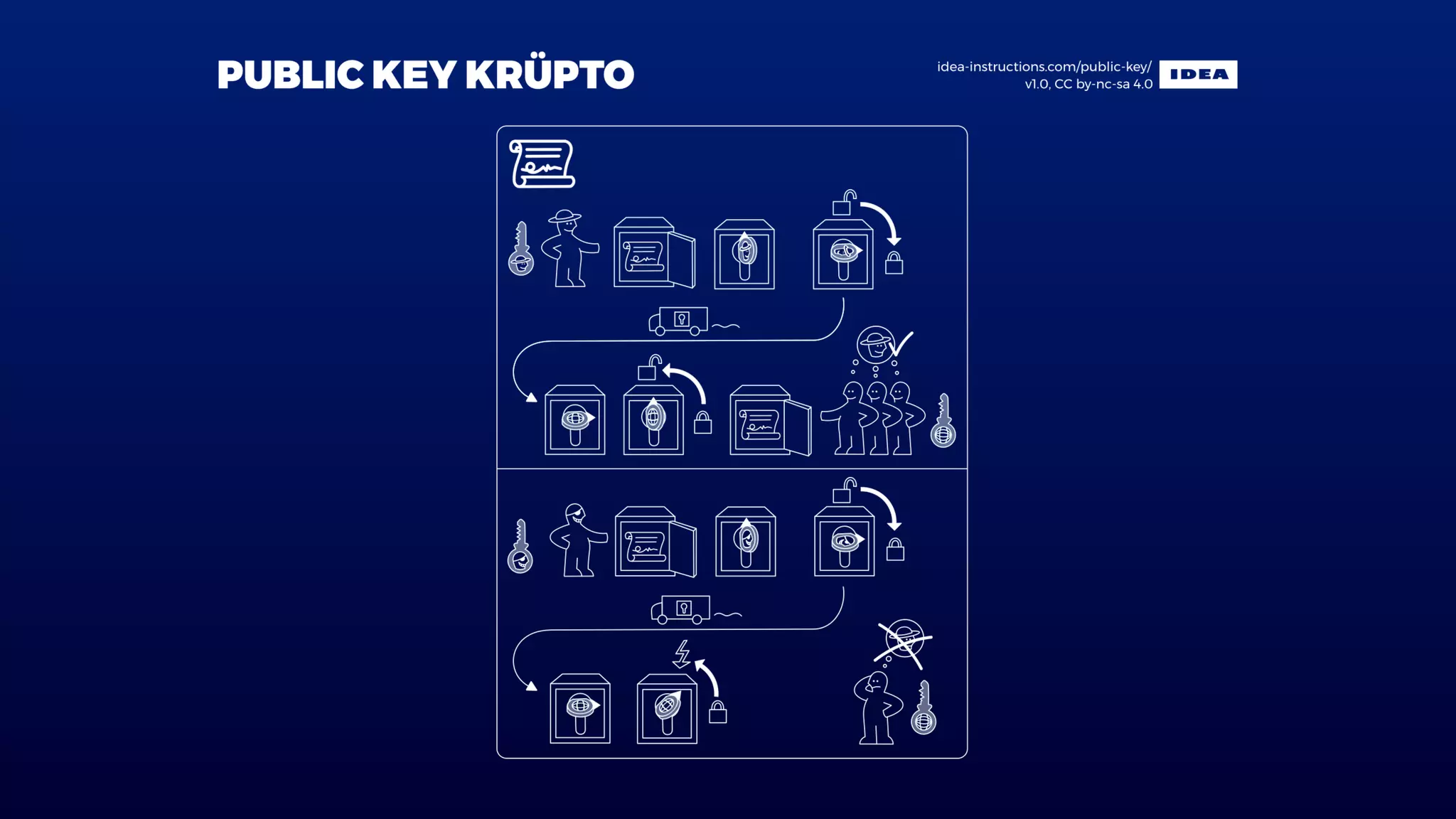
![A signature is a mathematical relationship between a message
, a private key and a public key .
It consists of two functions:
1. signing function
2. verifying function
So, given and and knowing , we can tell if is indeed signed
by .
x sk pk
t = f (sk, x)
[accept, reject] = g(pk, t, x)
x t pk x
sk
Maarten Mulders (@mthmulders)#tlsformortals](https://image.slidesharecdn.com/ssl-tls-for-mortals-191107111233/75/SSL-TLS-for-Mortals-Devoxx-24-2048.jpg)






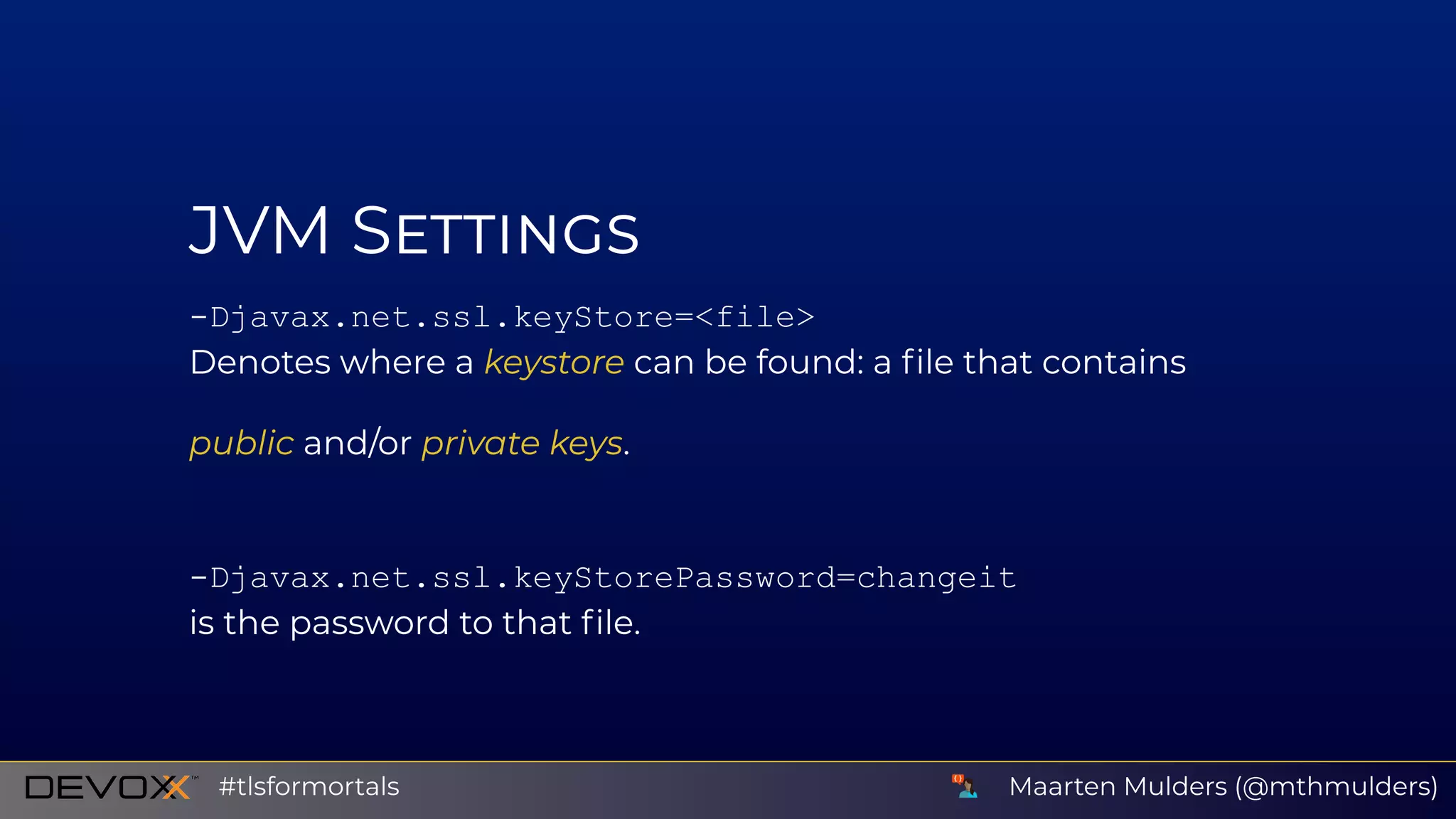
![JVM S
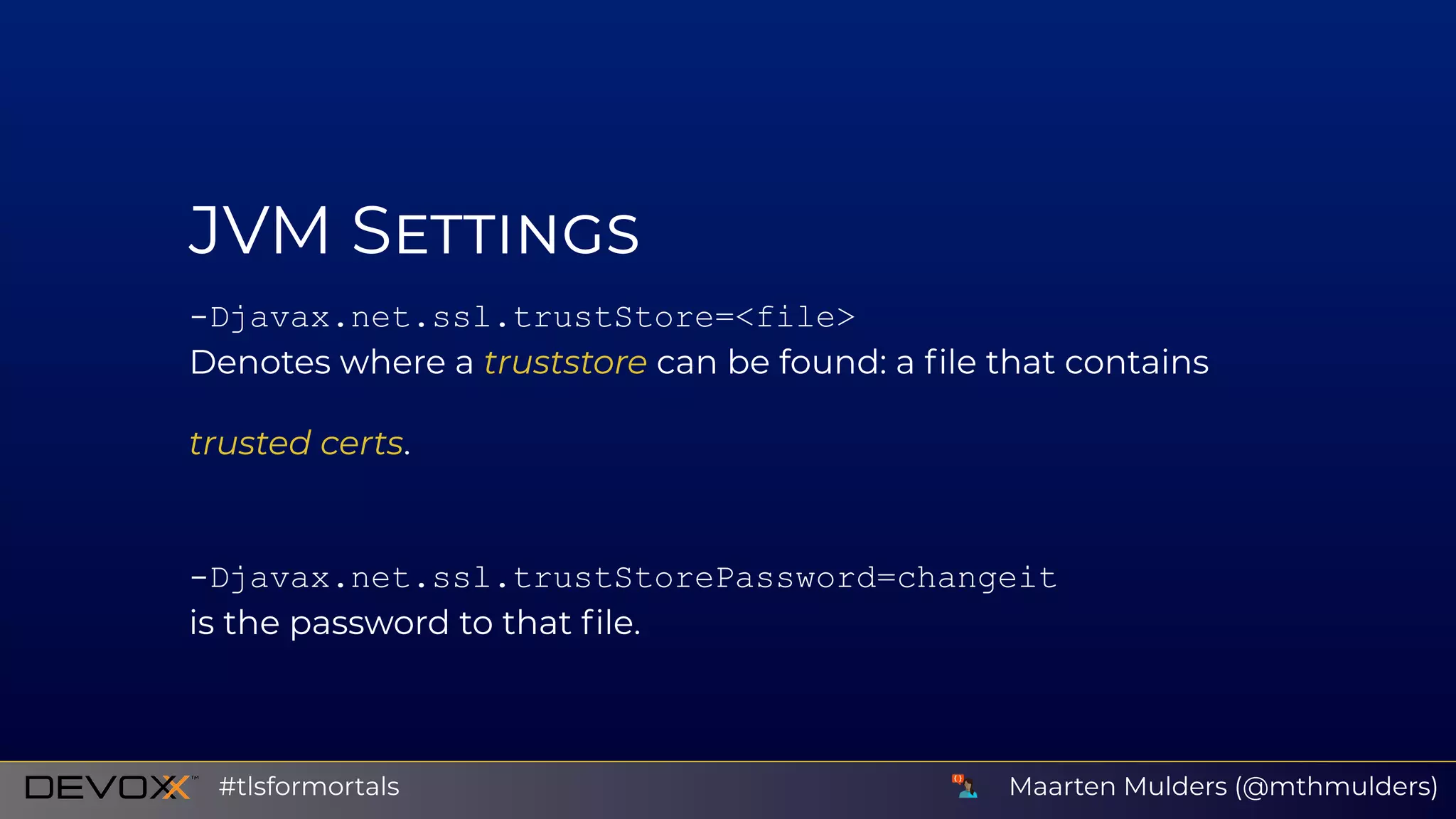
Djavax.net.debug=ssl[:flag]
Include debug logging for TLS handshake and connections.
Additional flags:
record session sessioncache pluggability plaintext
handshake defaultctx keymanager data packet
keygen sslctx trustmanager verbose
Maarten Mulders (@mthmulders)#tlsformortals](https://image.slidesharecdn.com/ssl-tls-for-mortals-191107111233/75/SSL-TLS-for-Mortals-Devoxx-38-2048.jpg)