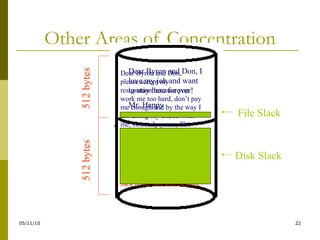
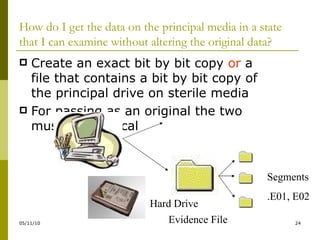
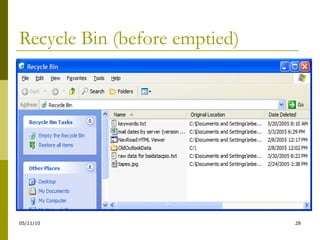
The document outlines sound collection practices for electronically stored information (ESI), emphasizing the need to determine what to collect and the differences between readily accessible and 'not reasonably accessible' data. It discusses the complexities of authenticating ESI, including challenges posed by alterations, digital forensics, and the importance of maintaining a proper chain of custody. Best practices for data collection, including thorough vendor selection and systematic methodologies, are highlighted to ensure data integrity and admissibility in legal contexts.

























![Coleman (Parent) Holdings, Inc v. Morgan Stanley & Co., Inc., 2005 WL 679071 at *4 (Fla.Cir.Ct. Mar. 1, 2005)., subsequent decision, 2005 WL 674885 (Fla.Cir.Ct. Mar. 23, 2005). Morgan Stanley decided to collect electronic documents themselves, using software they developed in-house. [A Morgan Stanley employee] reported that…she and her team had discovered a flaw in the software they had written and that flaw had prevented [Morgan Stanley] from locating all responsive email attachments. [She also] reported that [Morgan Stanley] discovered…that the date-range searches for email users who had a Lotus Notes platform were flawed, so there were at least 7,000 additional e-mail messages that appeared to fall within the scope of [existing orders]... * * * Sanctions! * * * “ DIY” Collection Programs](https://image.slidesharecdn.com/may62010clesoundcollectionpracticesrowbeanpresentation-1273593772474-phpapp01/85/Sound-E-Discovery-Collection-Practices-37-320.jpg)
![THANKS! Seth H. Row [email_address] (503) 222-1812 Michael Bean [email_address] (971) 285-3408 x 201](https://image.slidesharecdn.com/may62010clesoundcollectionpracticesrowbeanpresentation-1273593772474-phpapp01/85/Sound-E-Discovery-Collection-Practices-38-320.jpg)