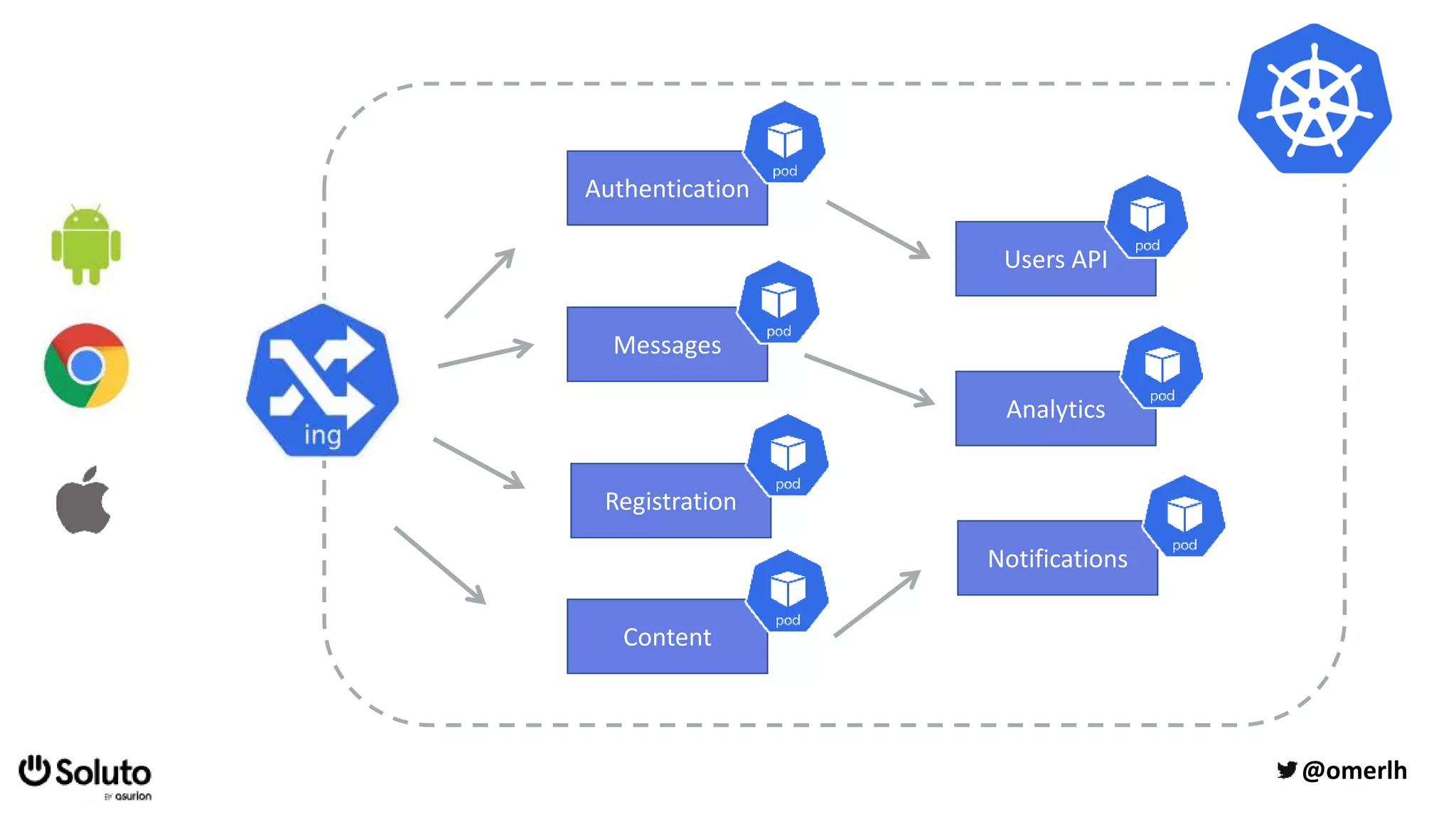
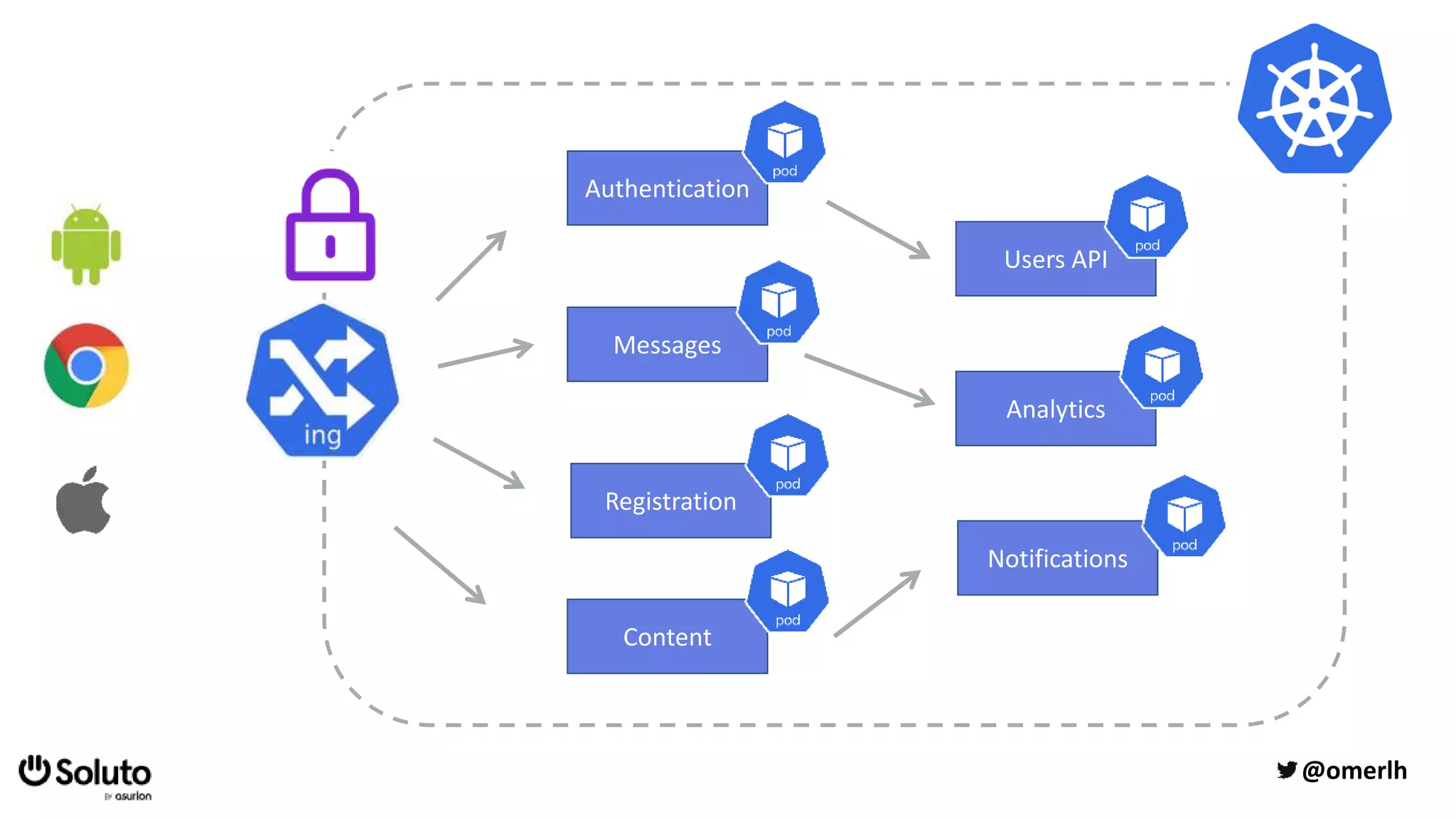
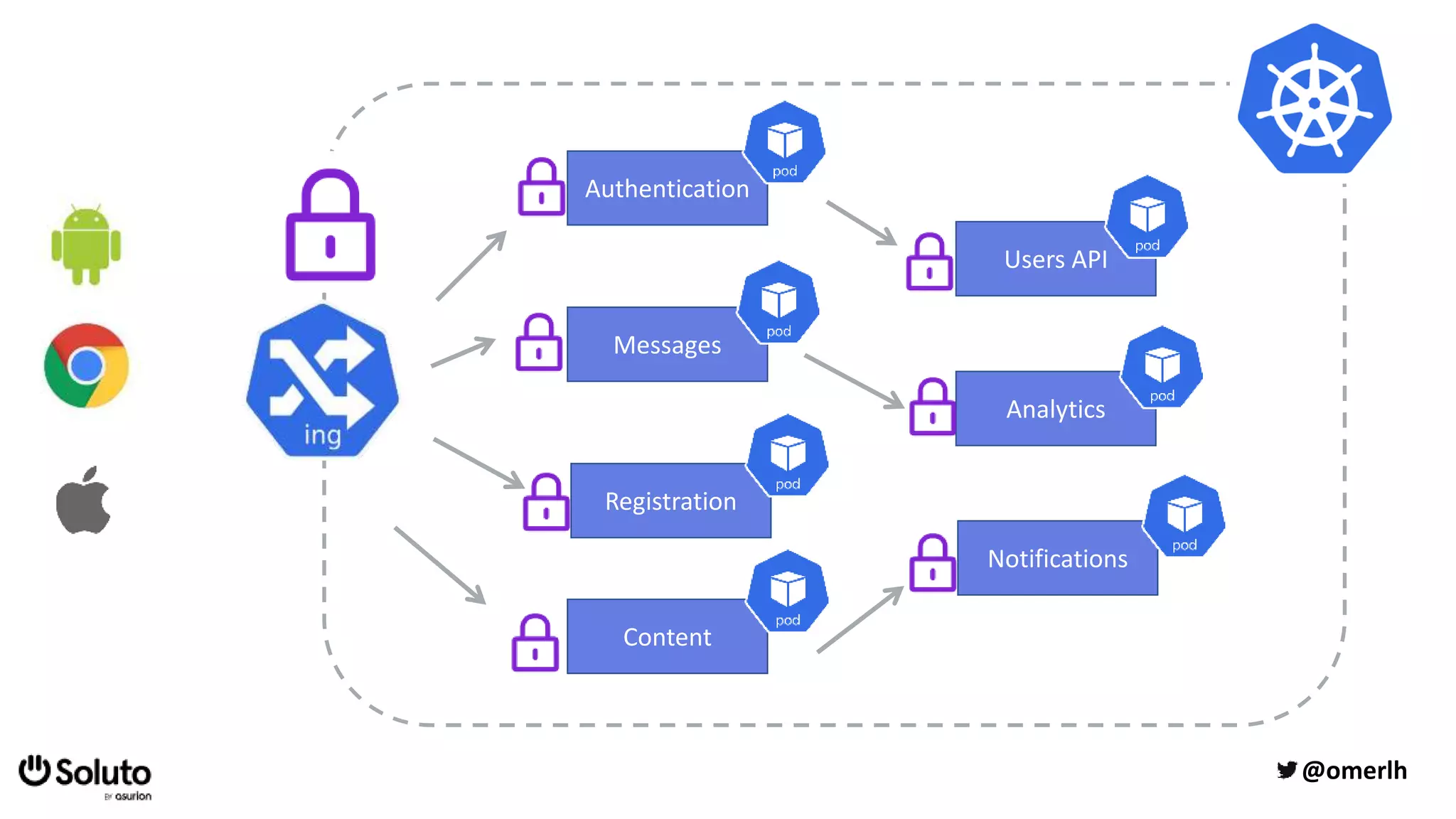
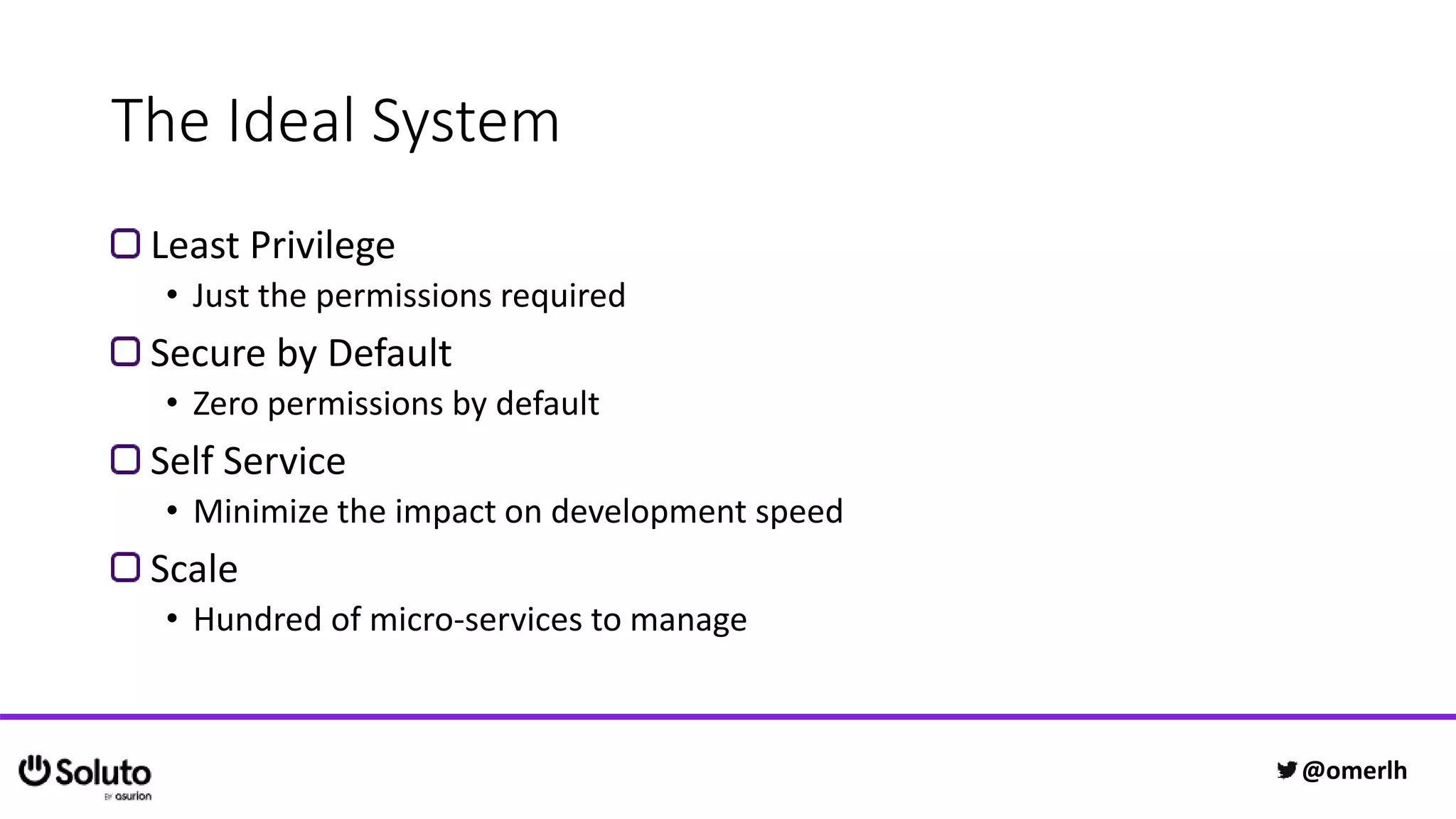
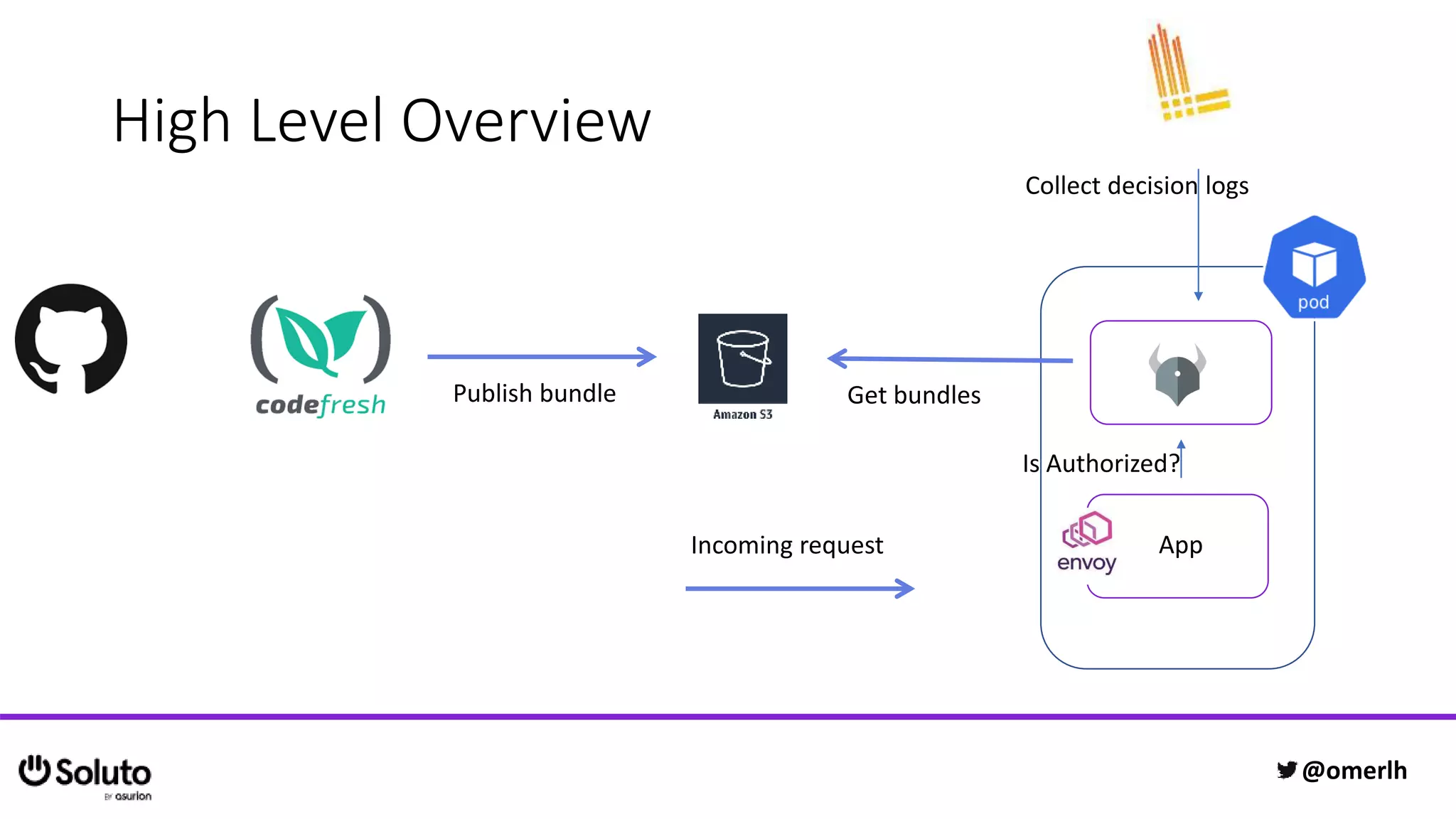
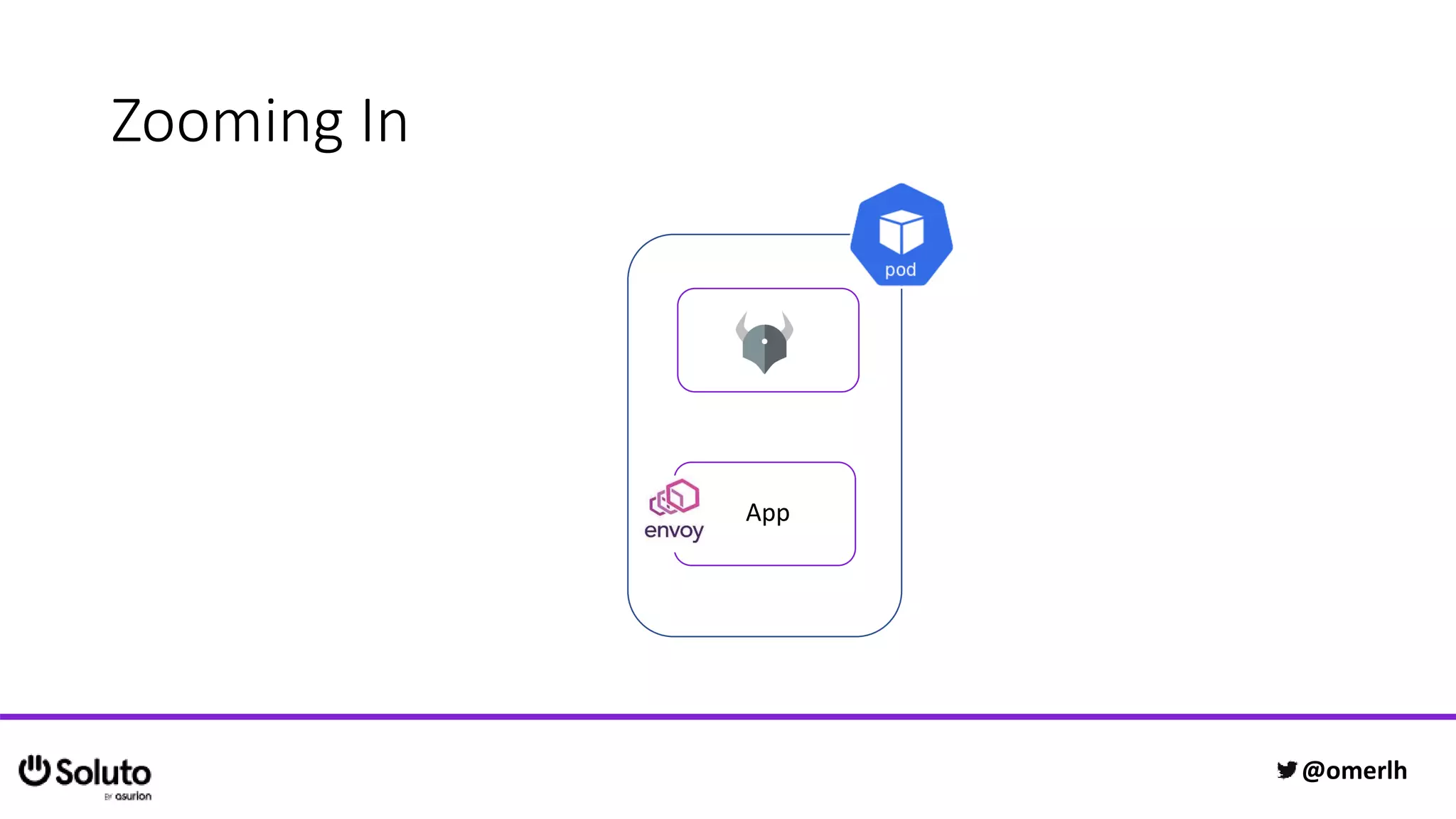
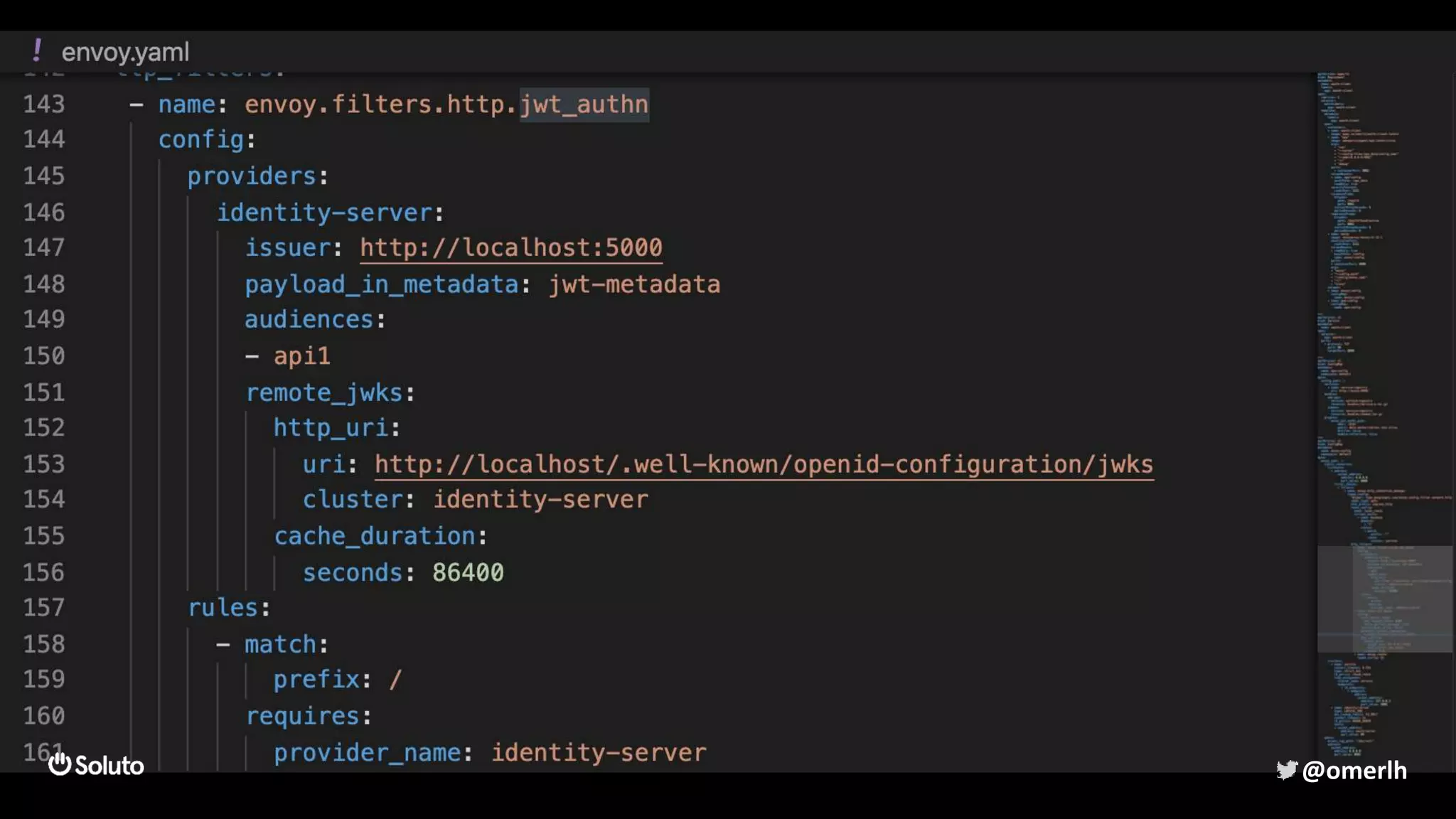
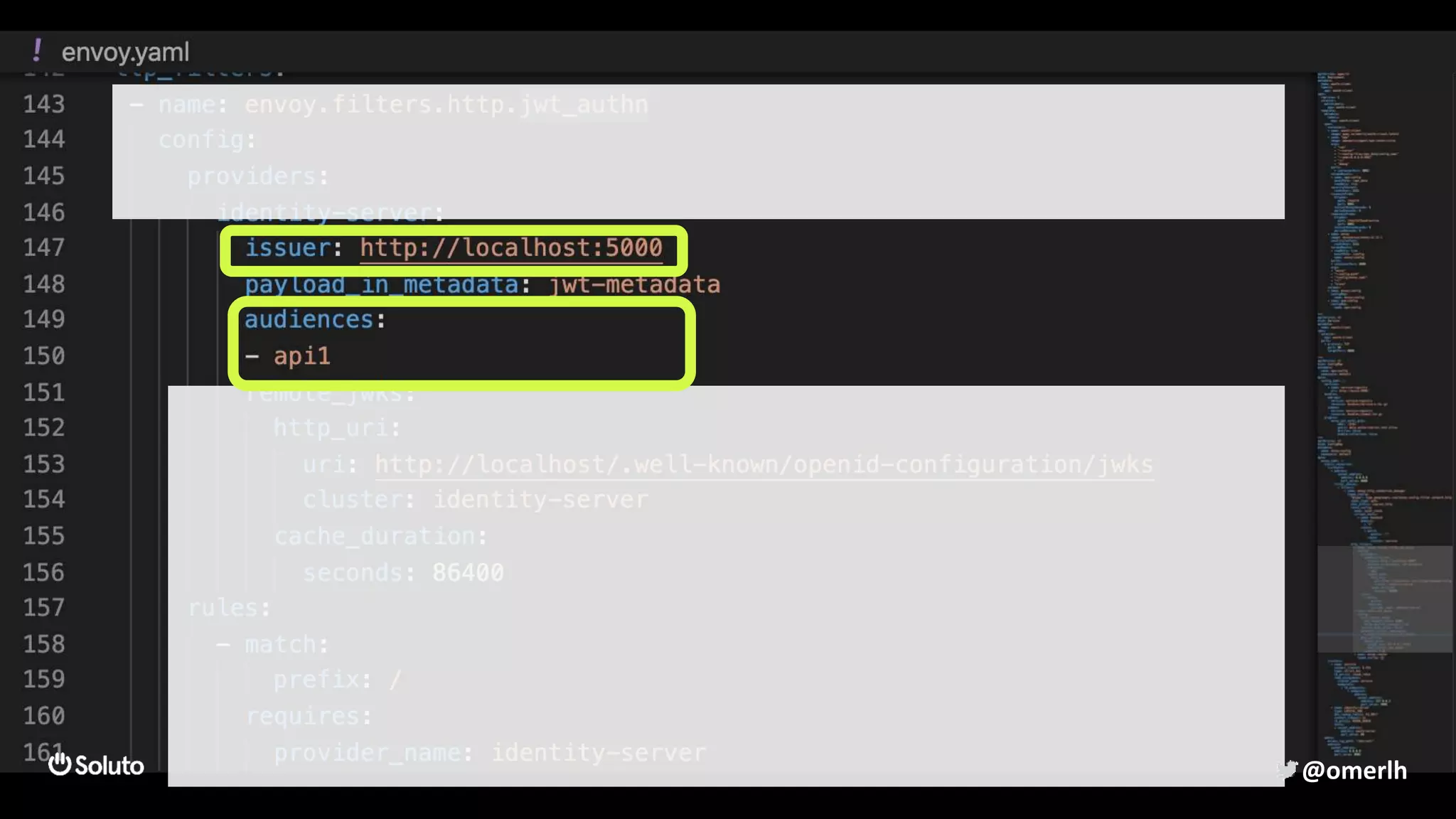
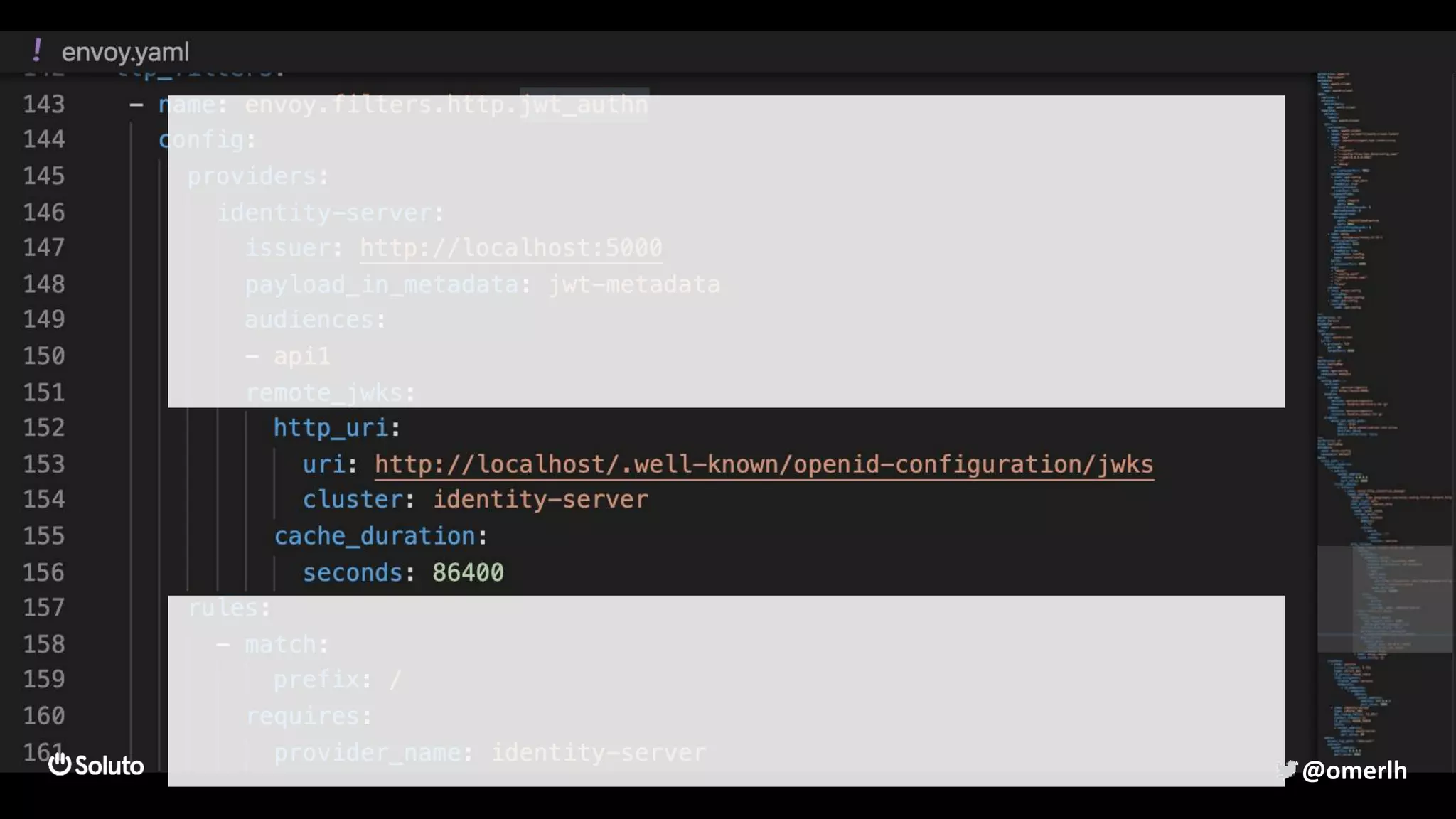
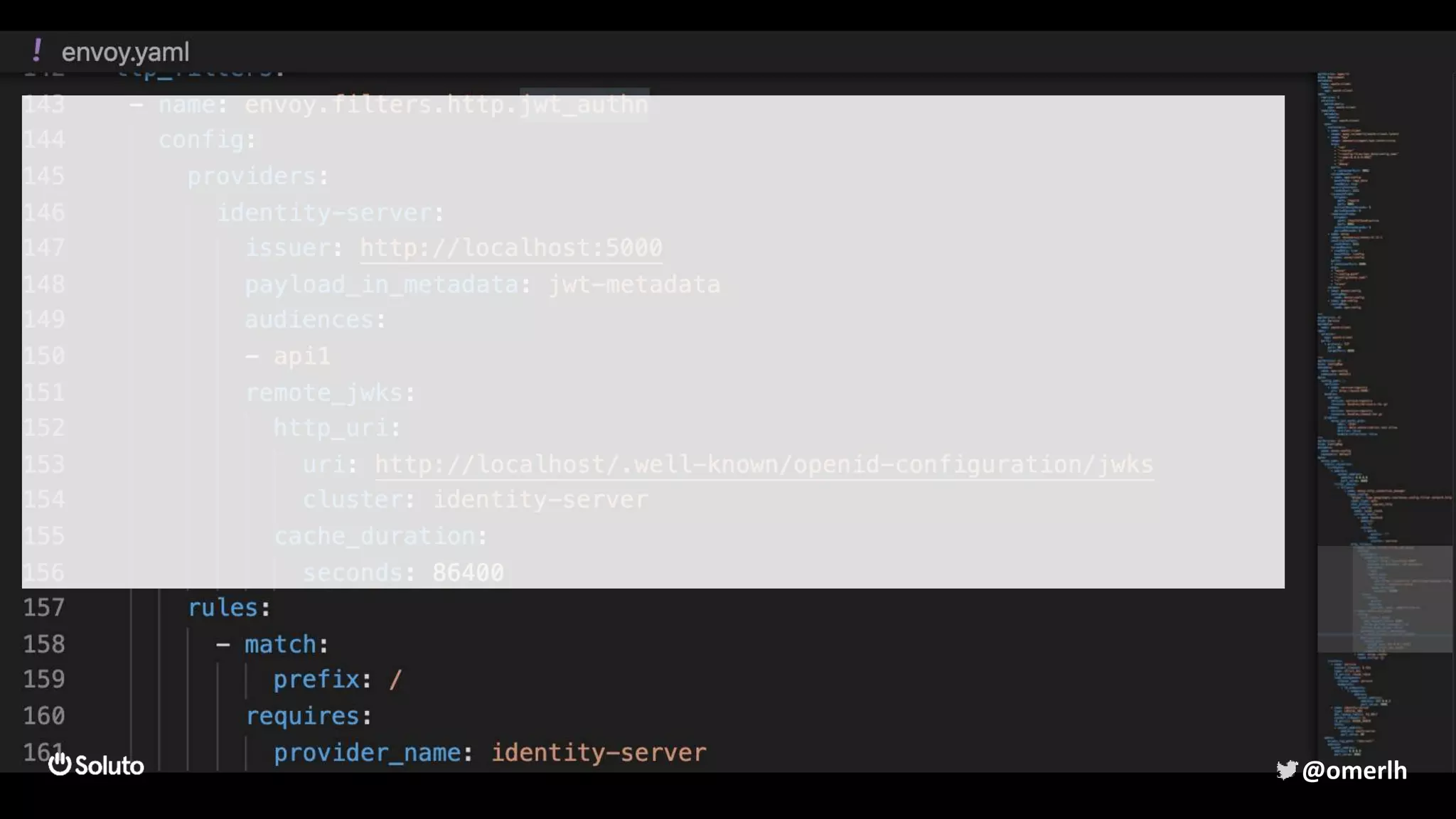
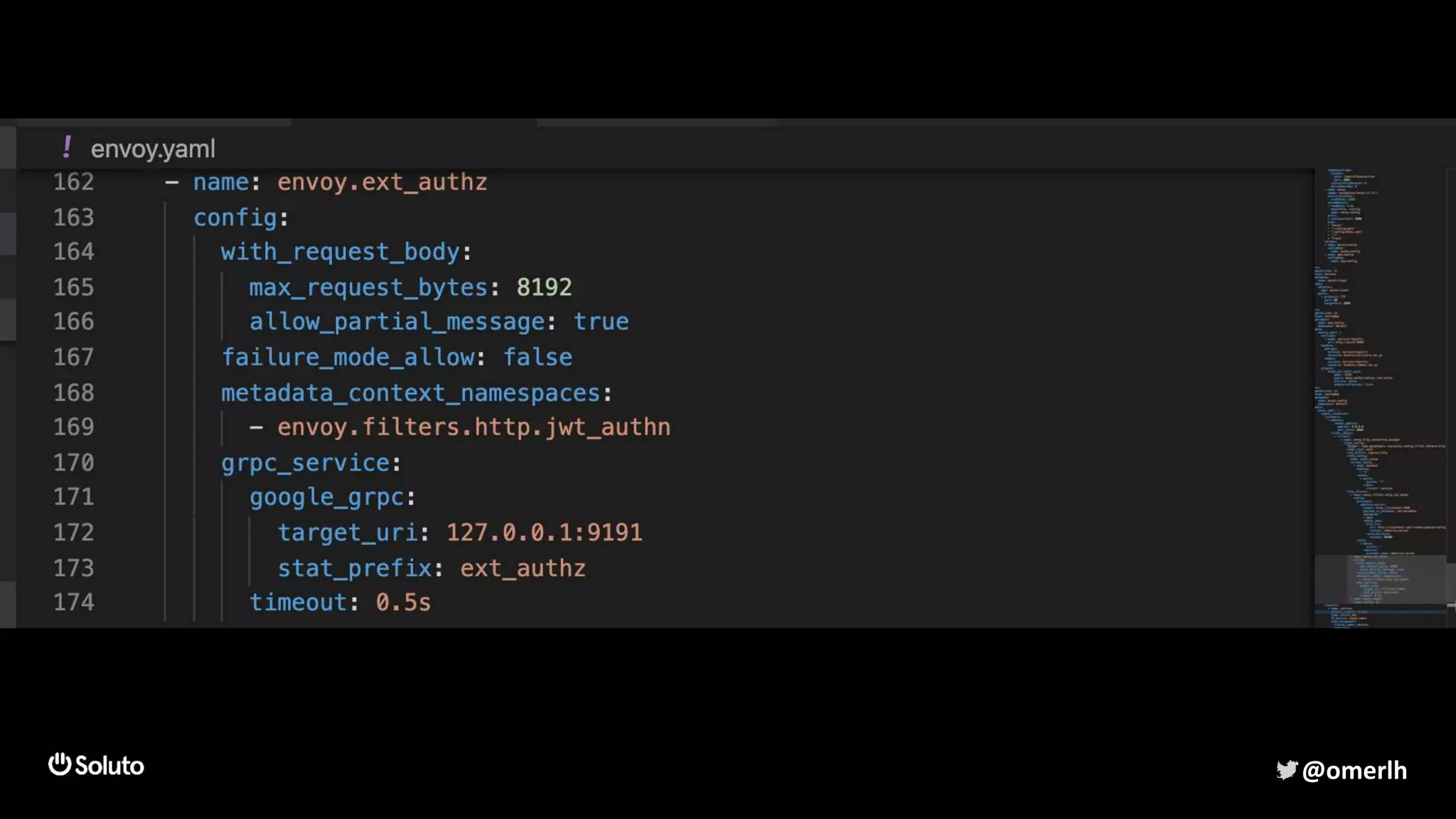
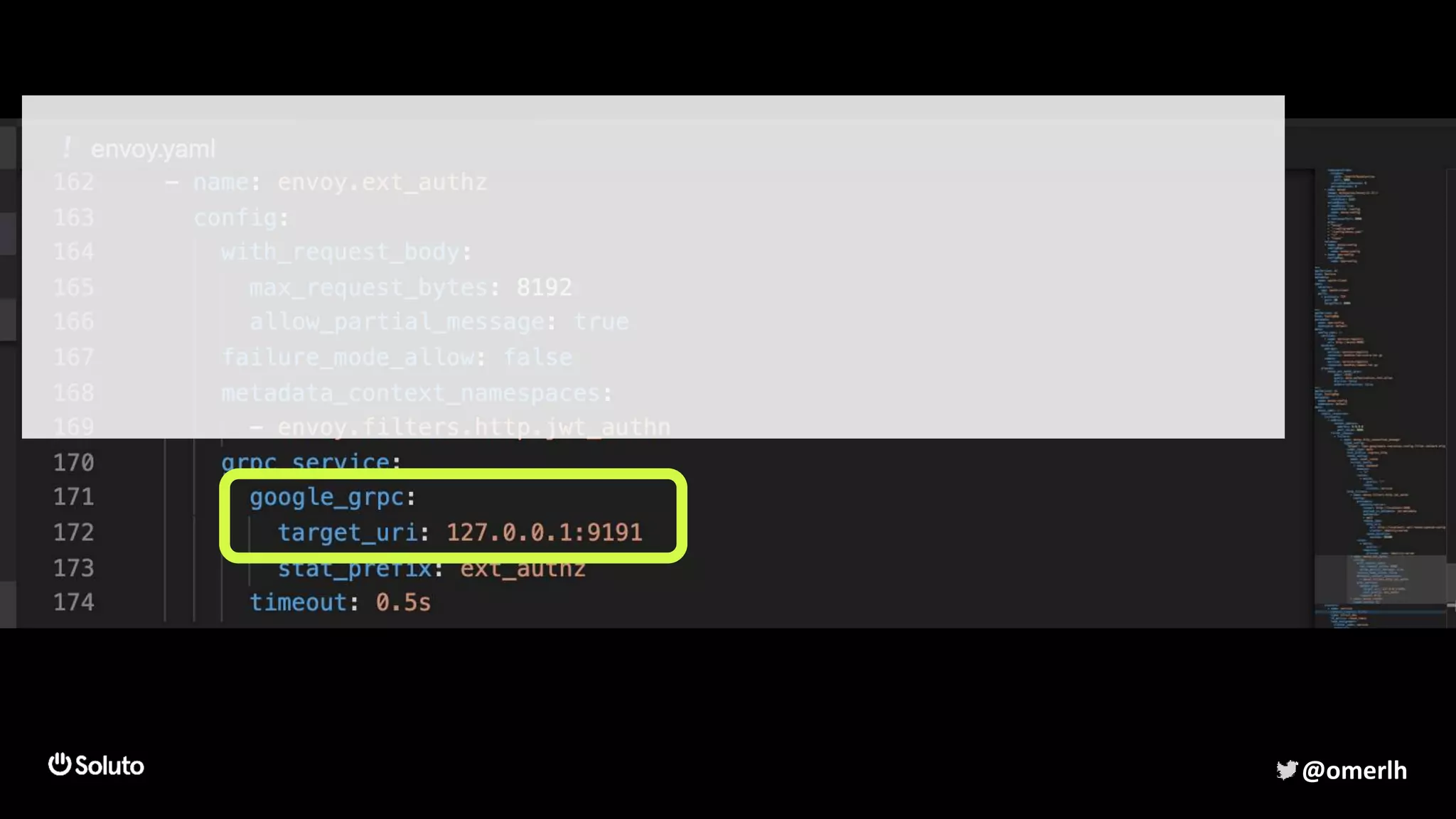
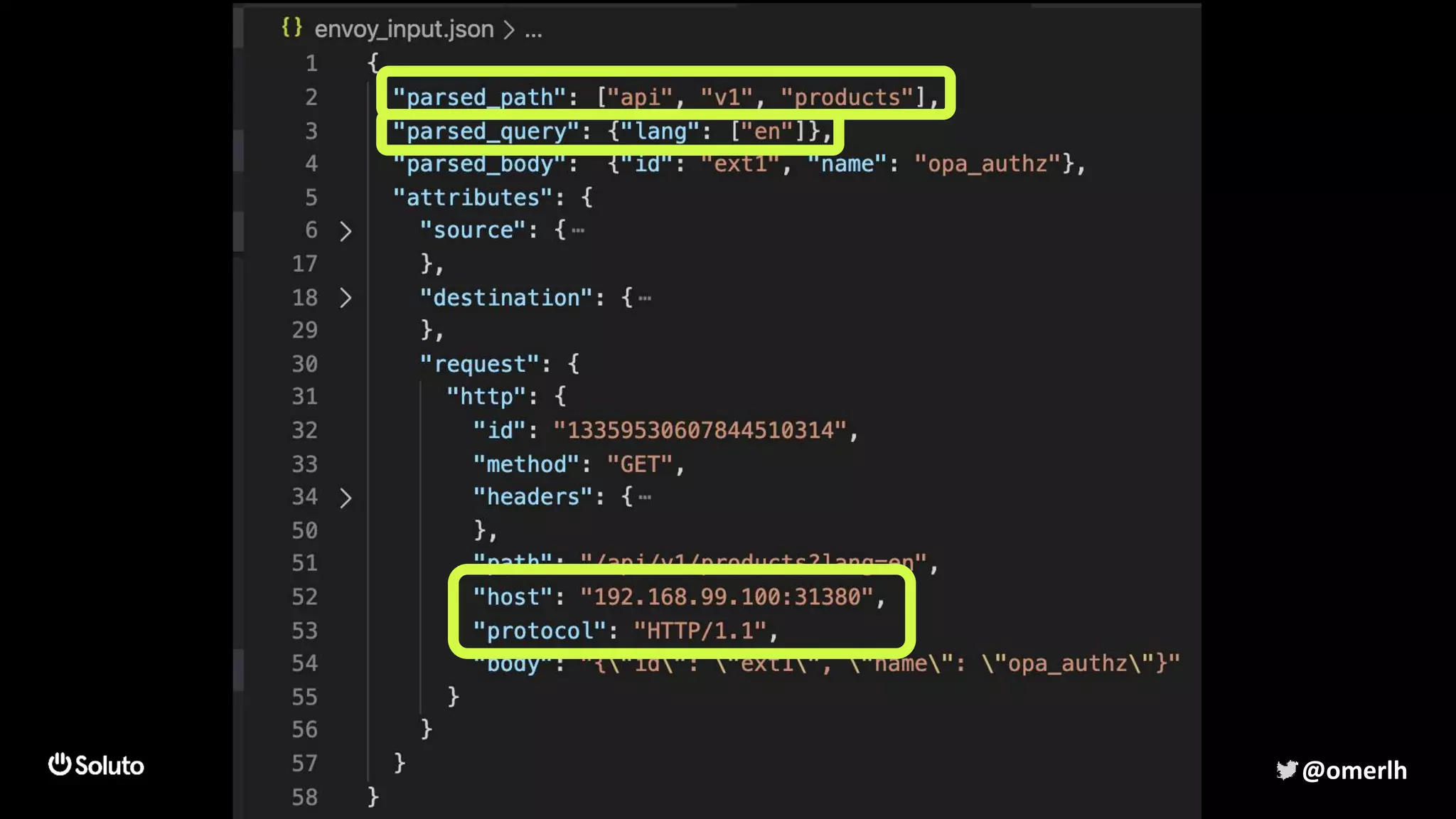
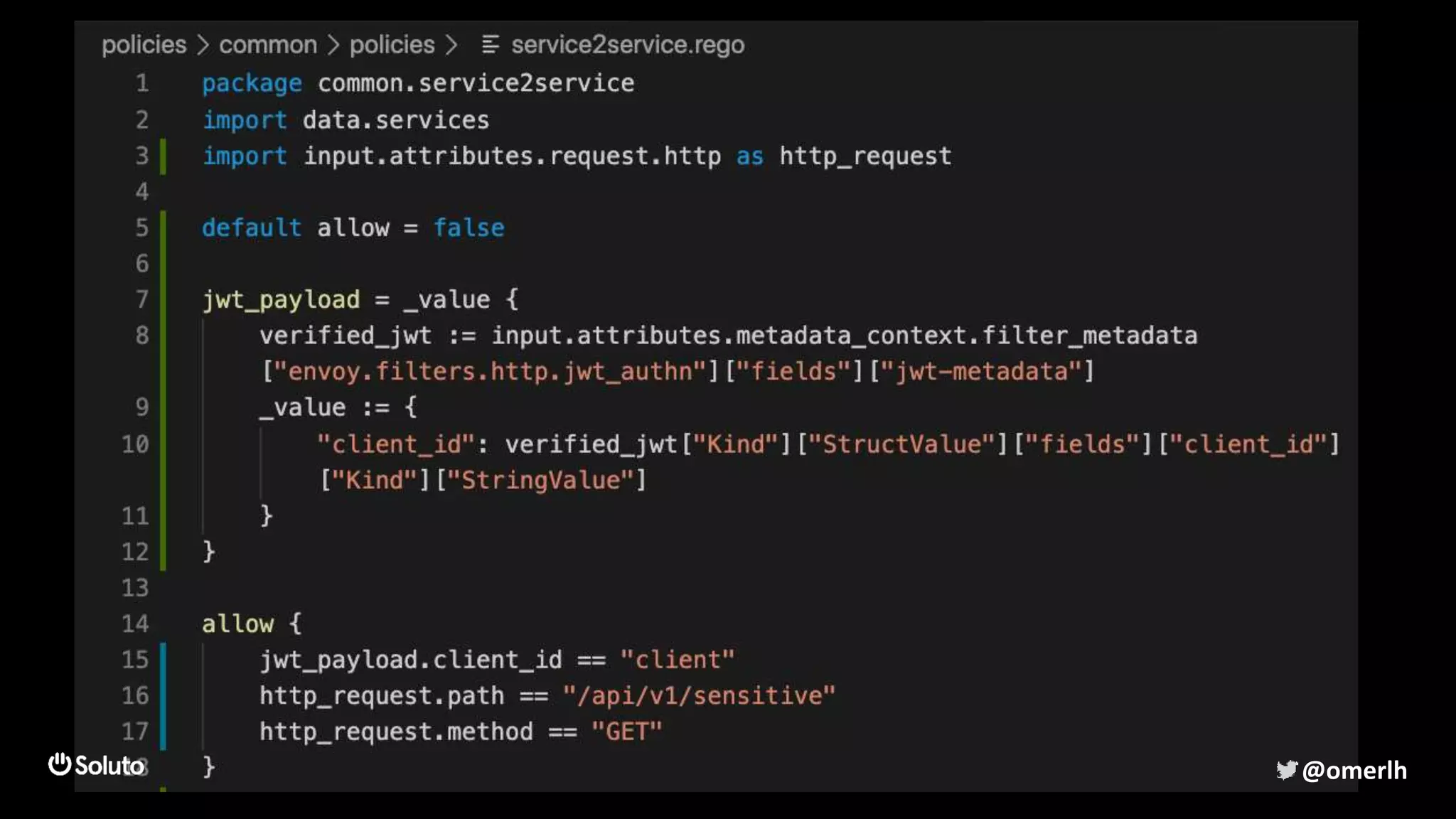
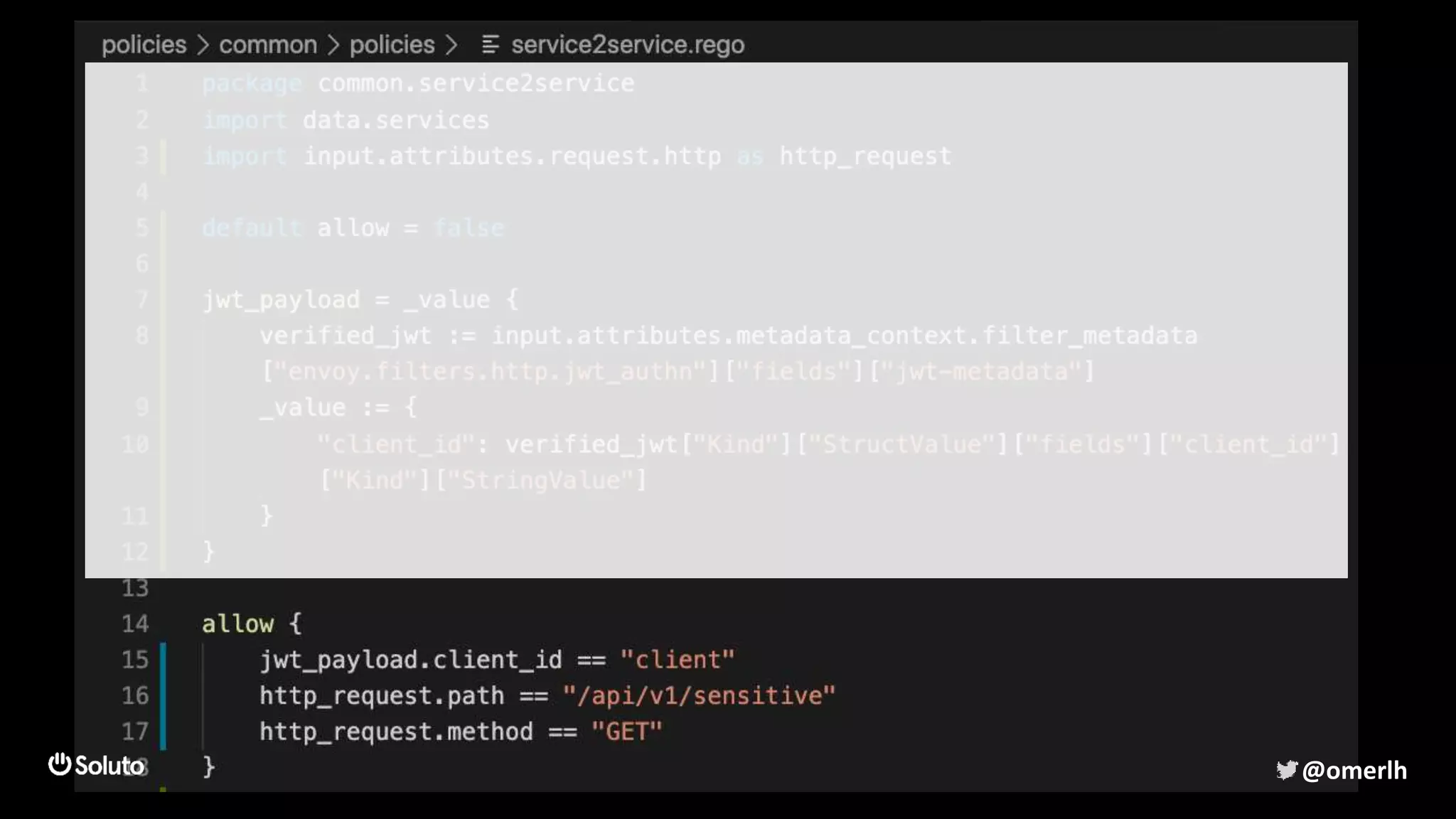
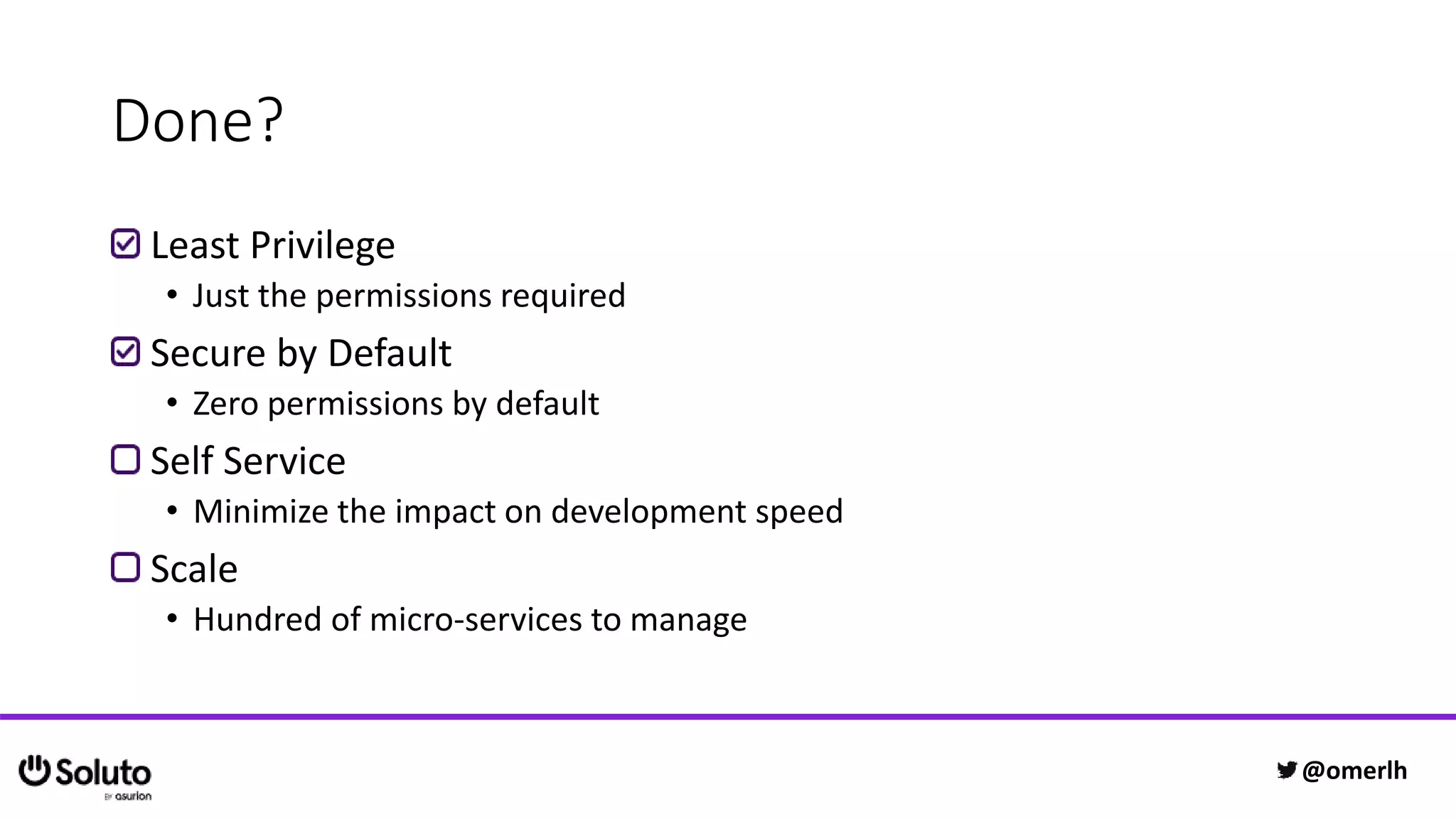
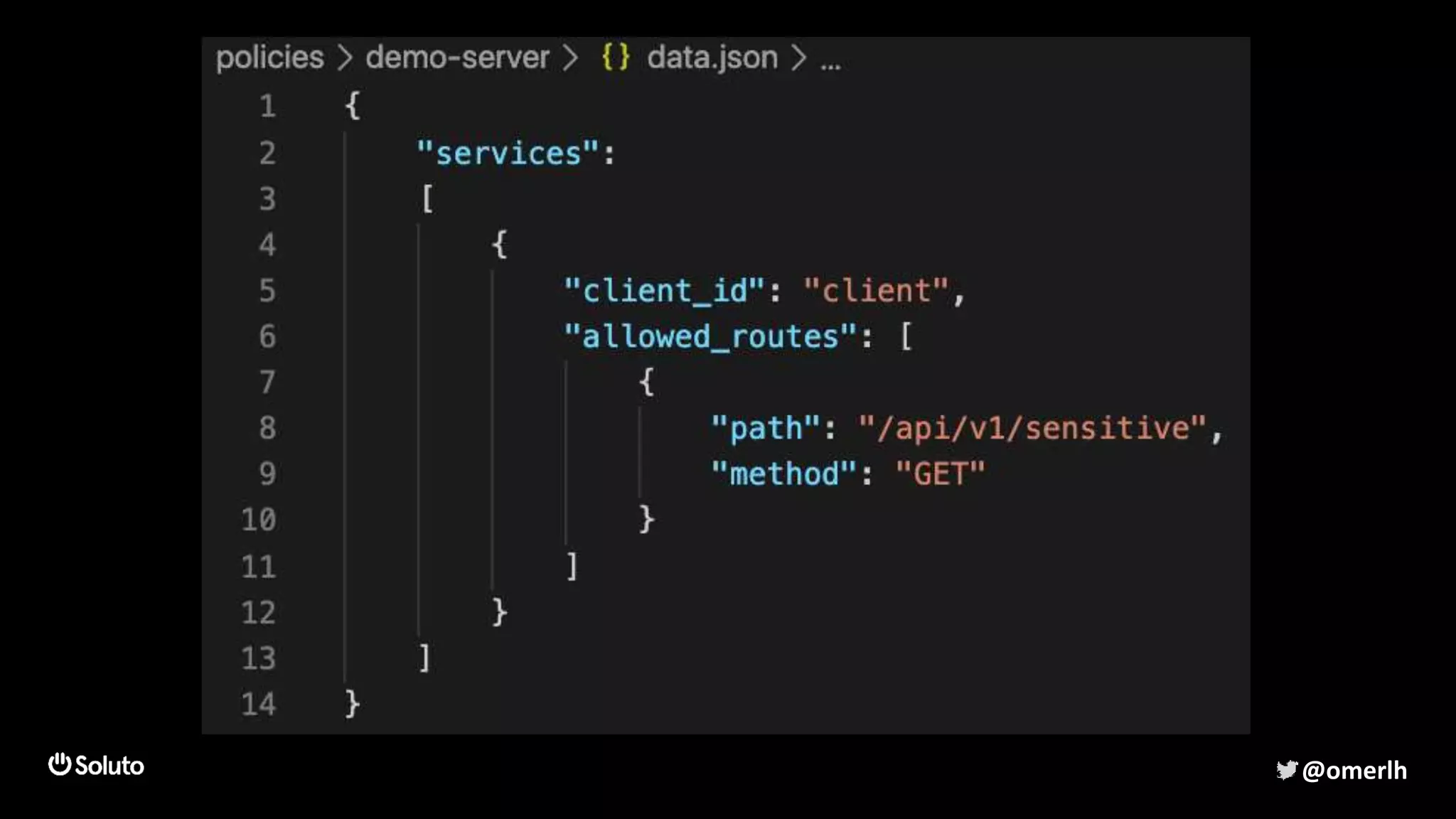
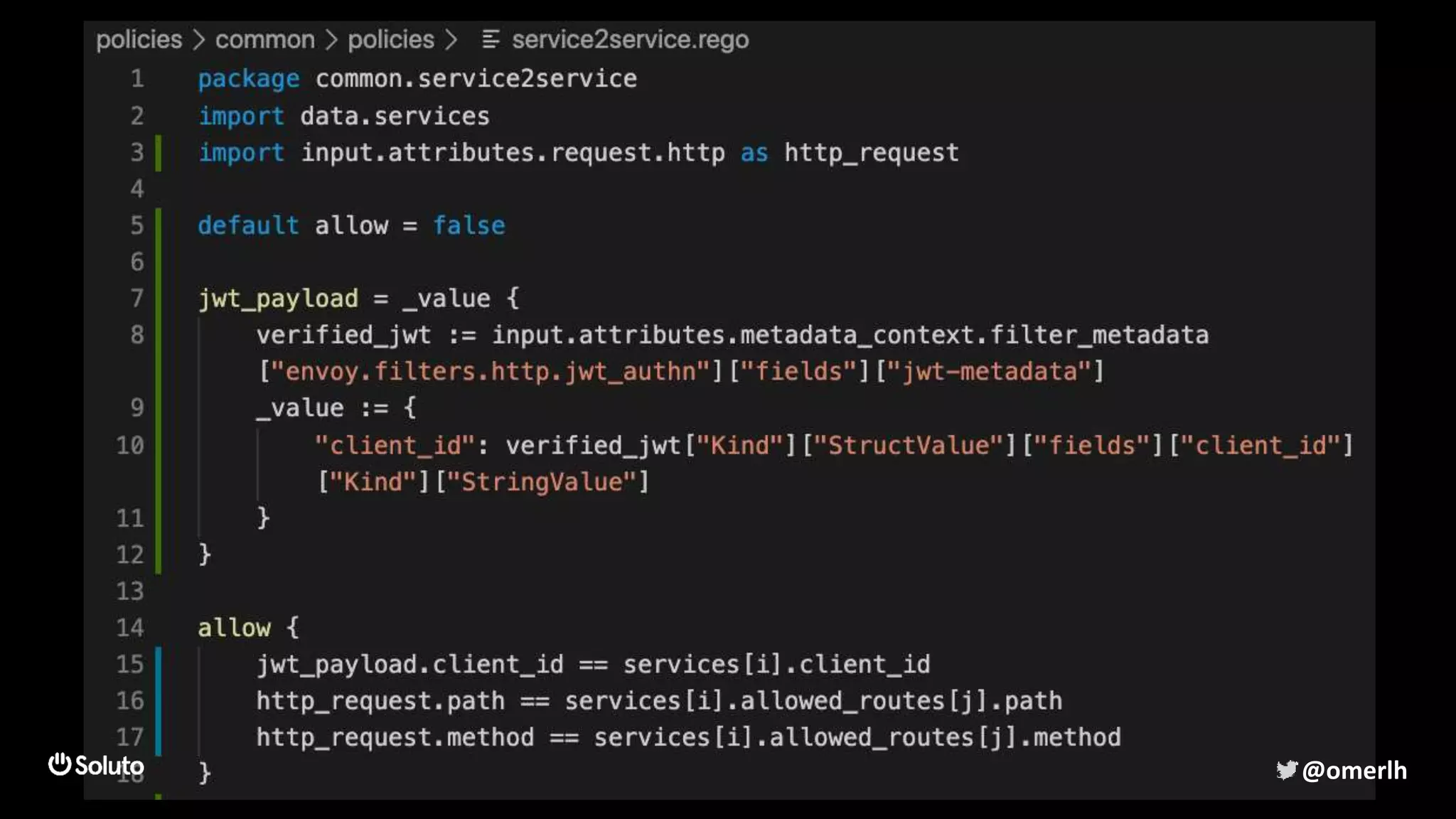
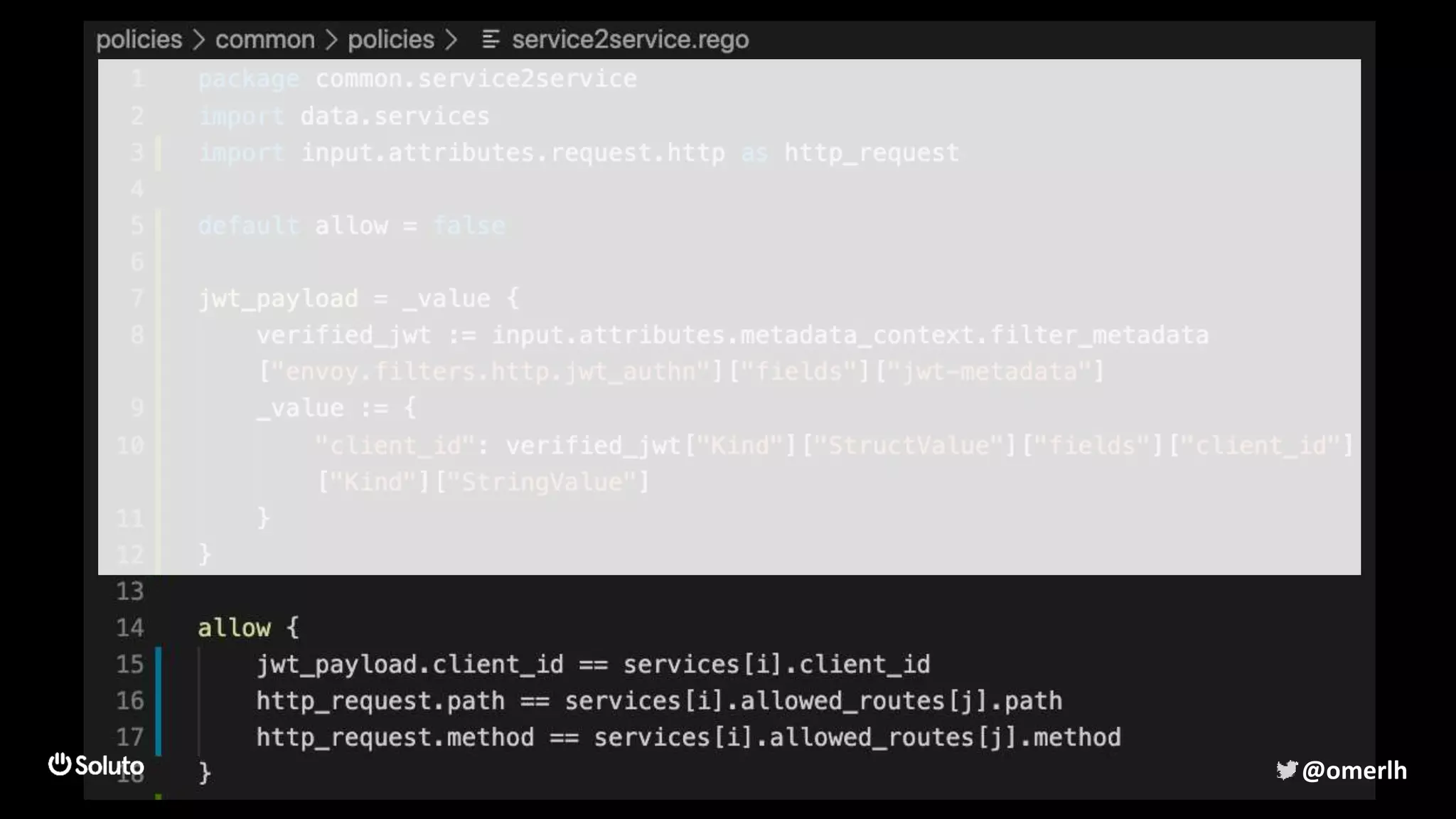
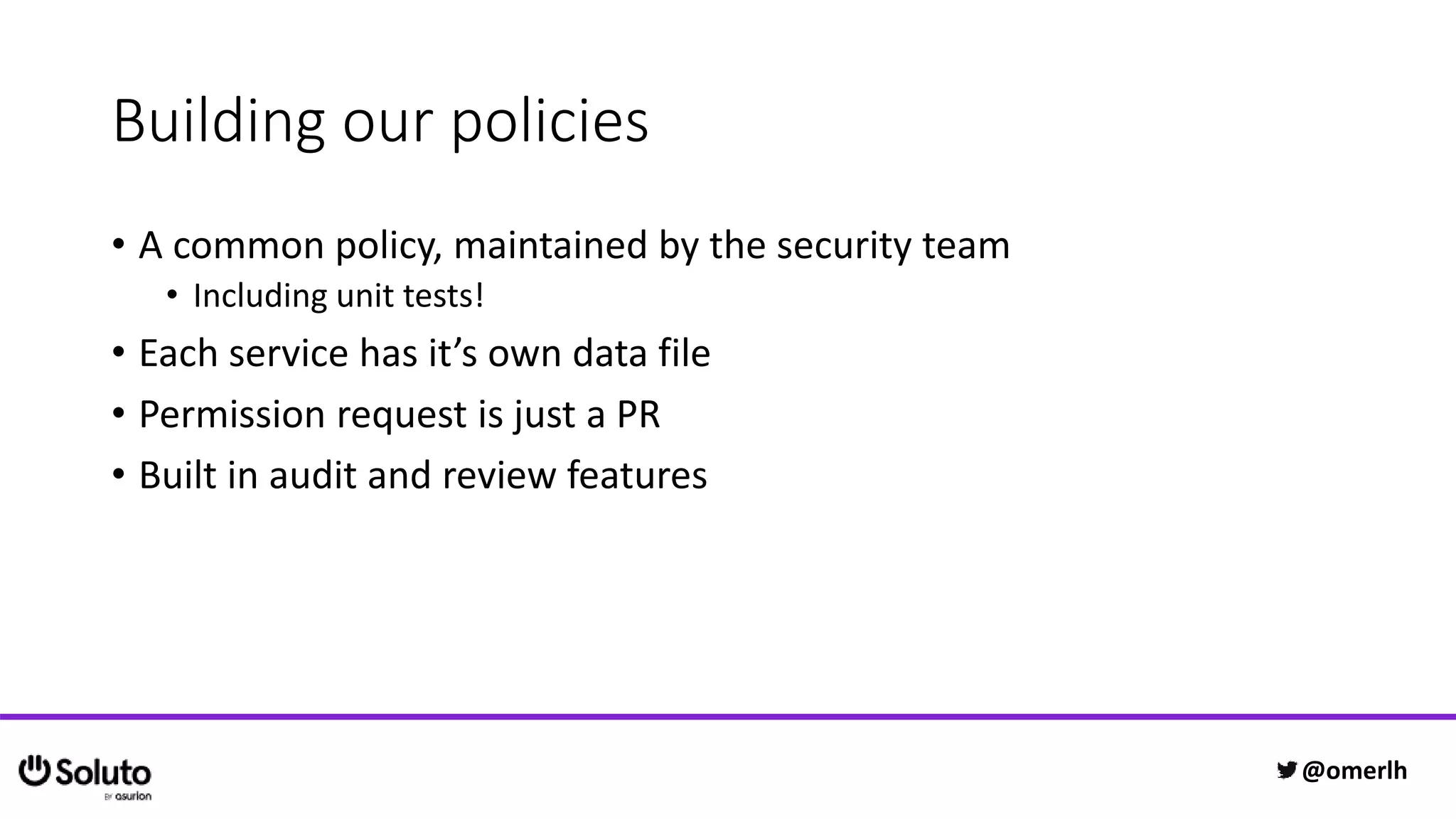
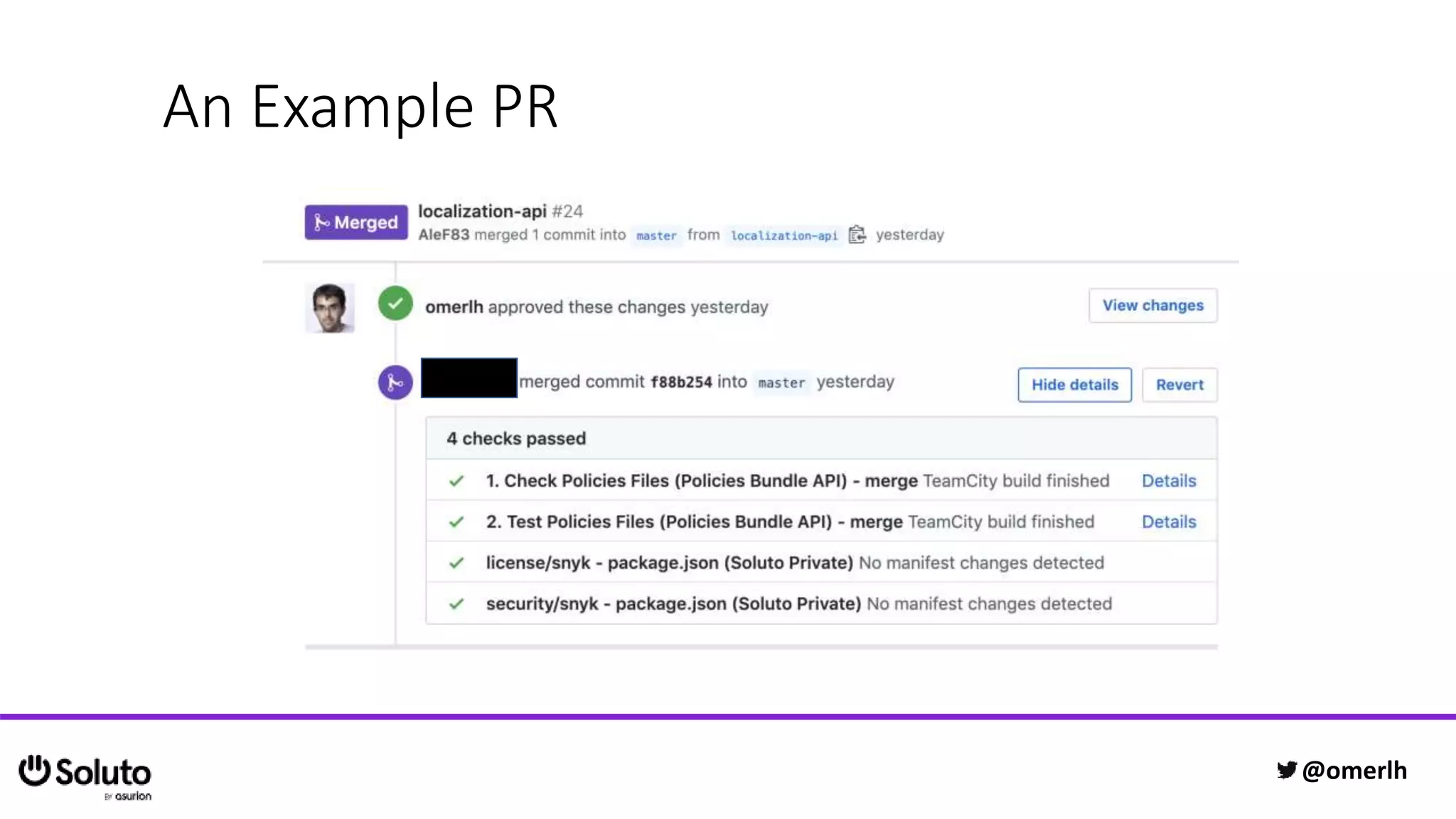
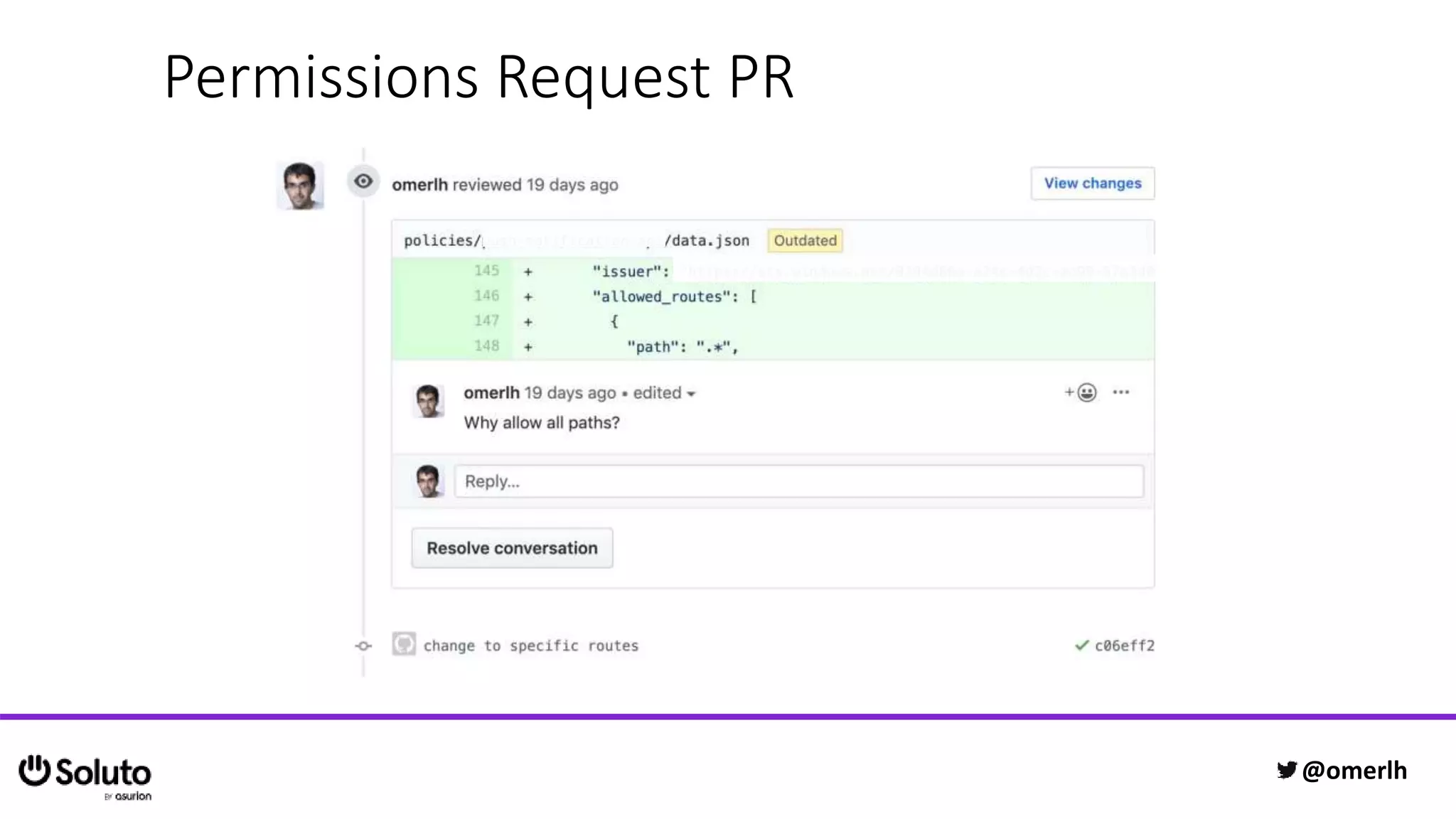
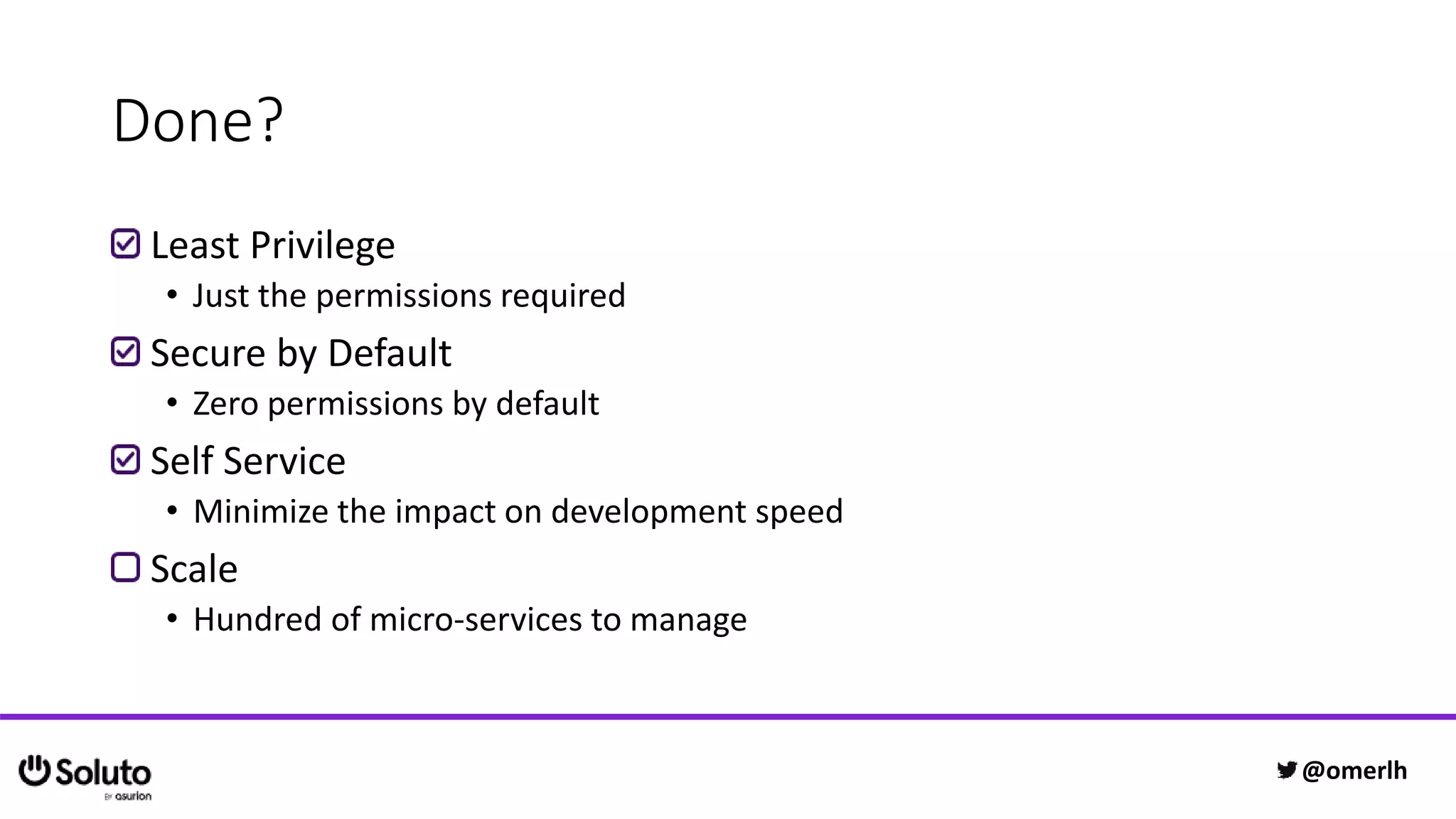
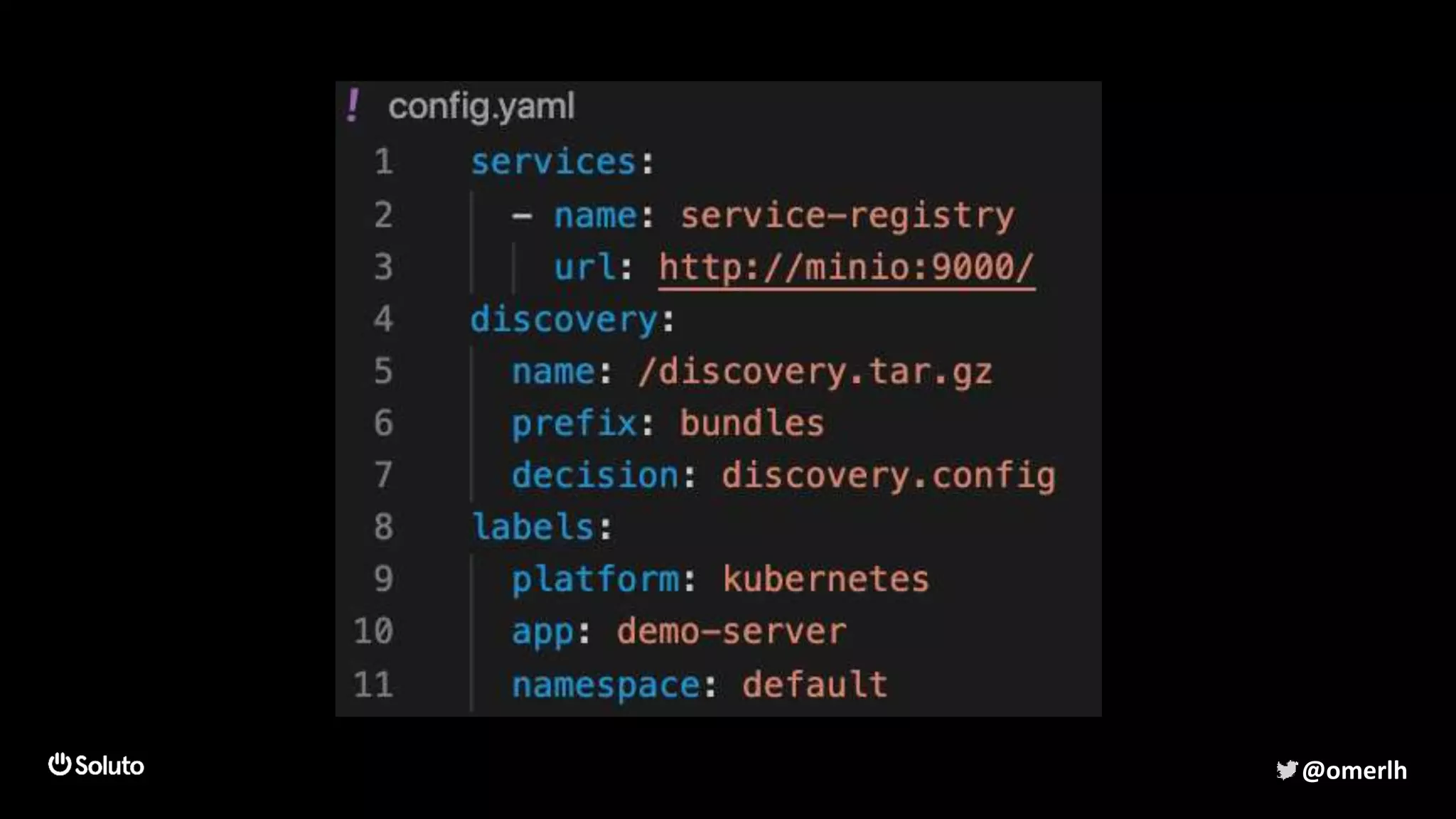
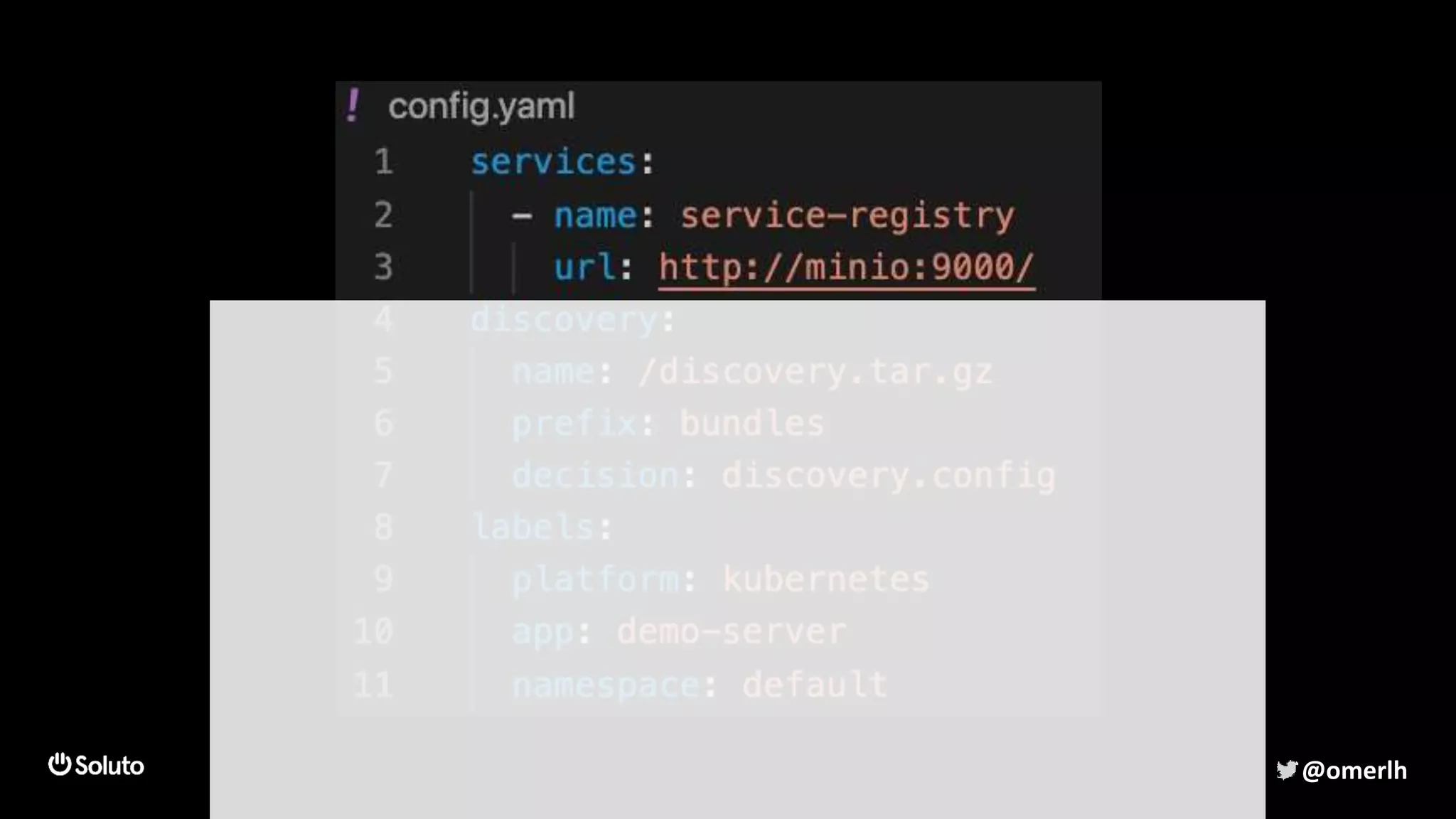
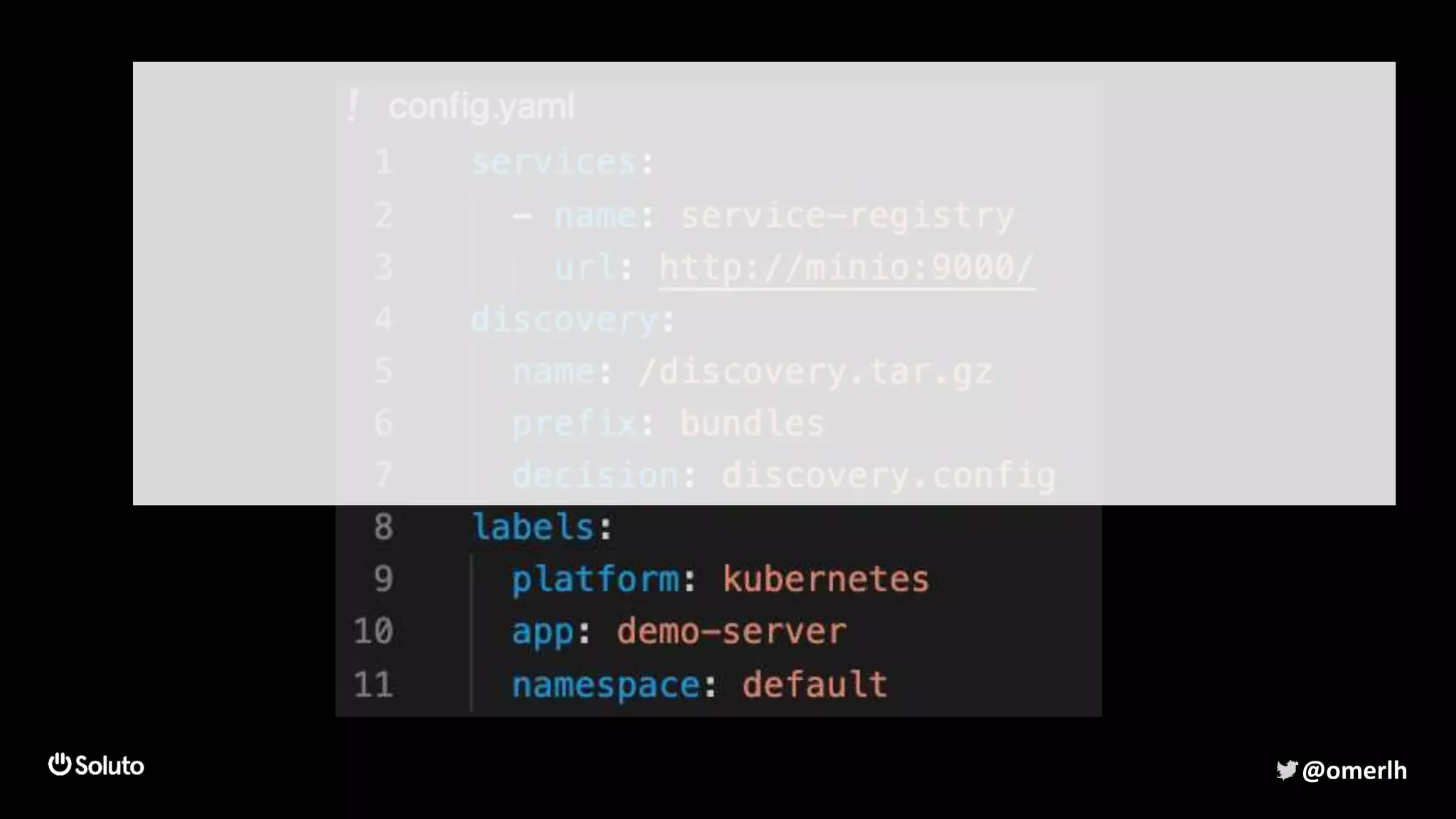
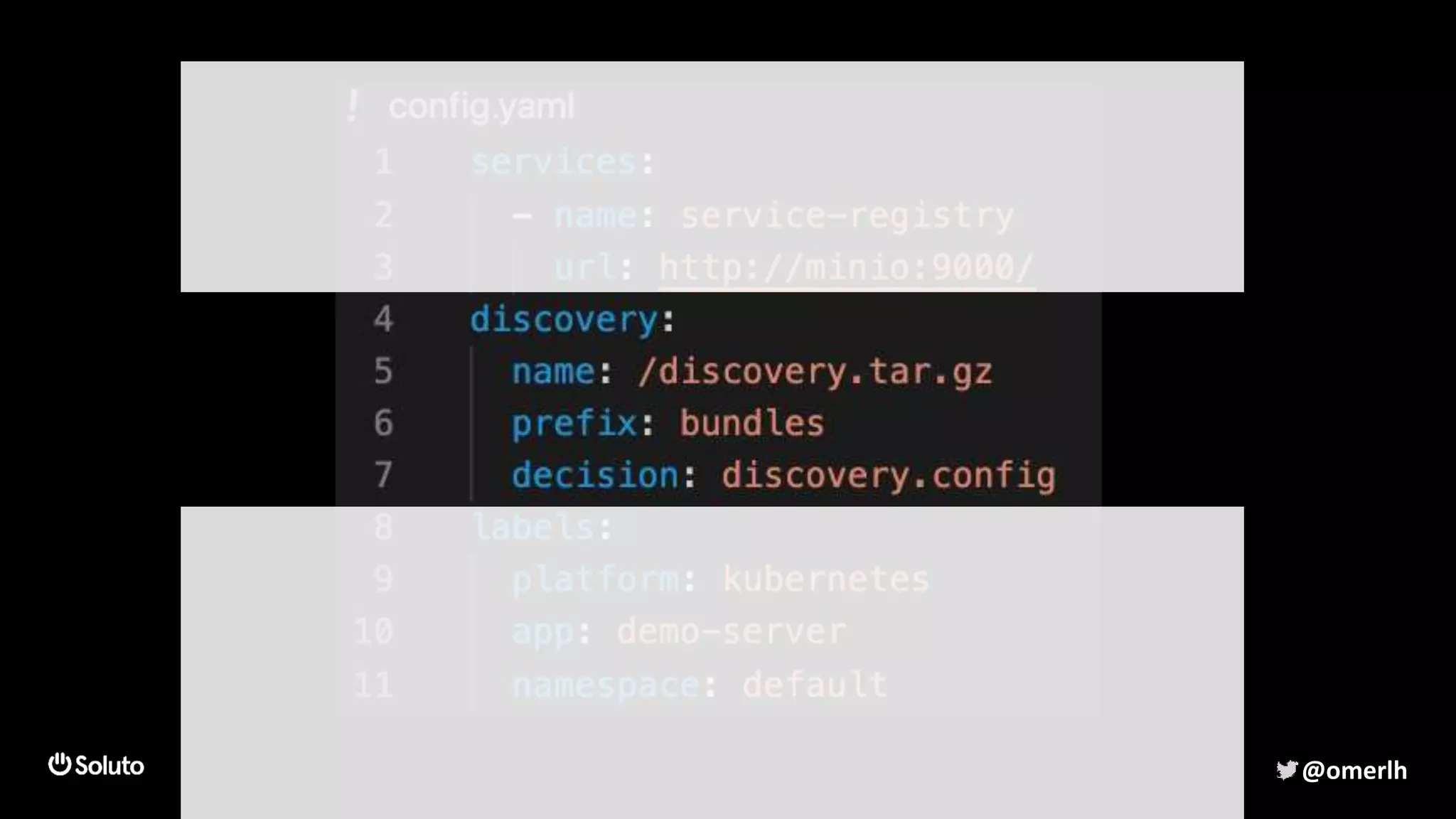
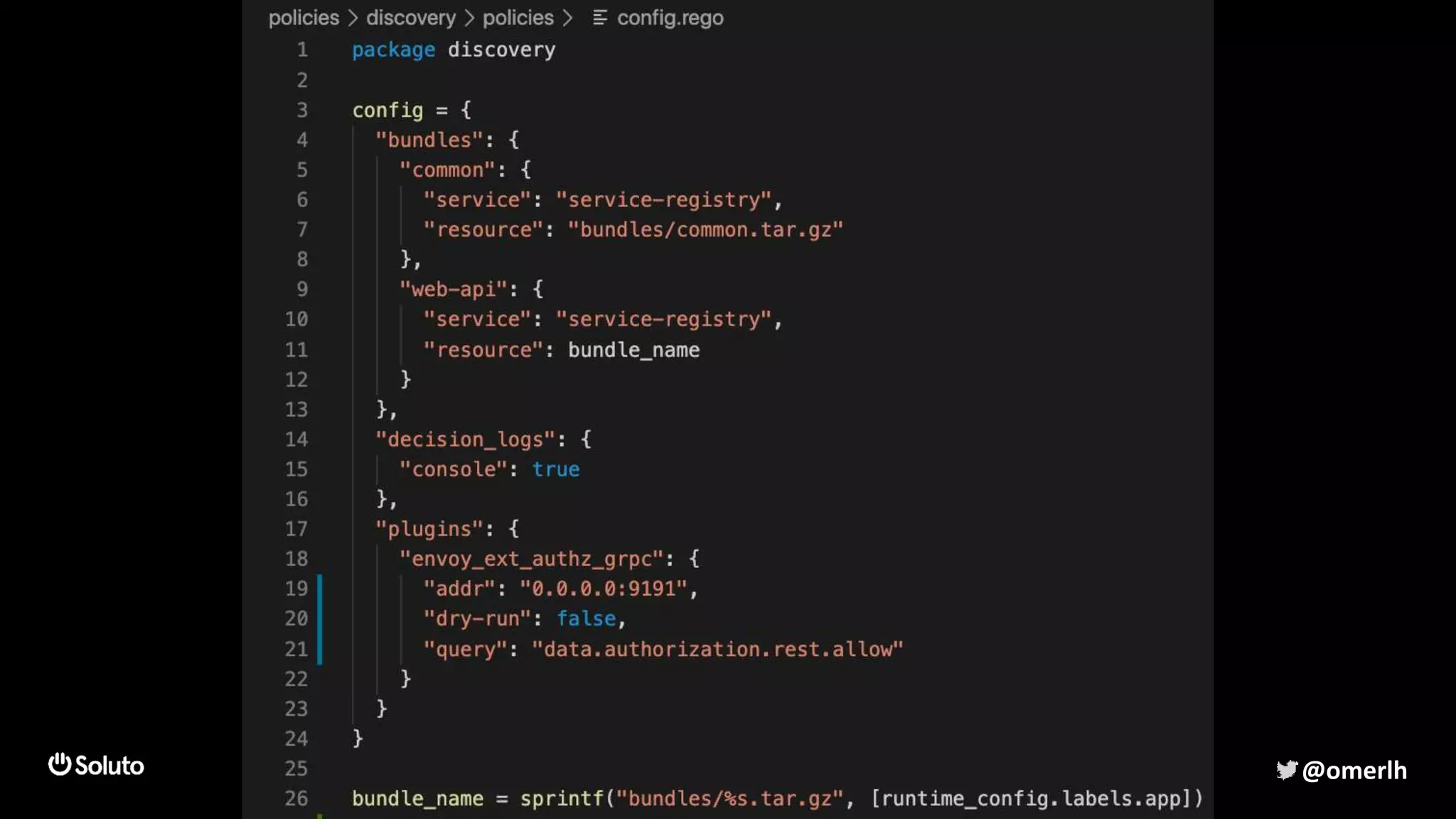
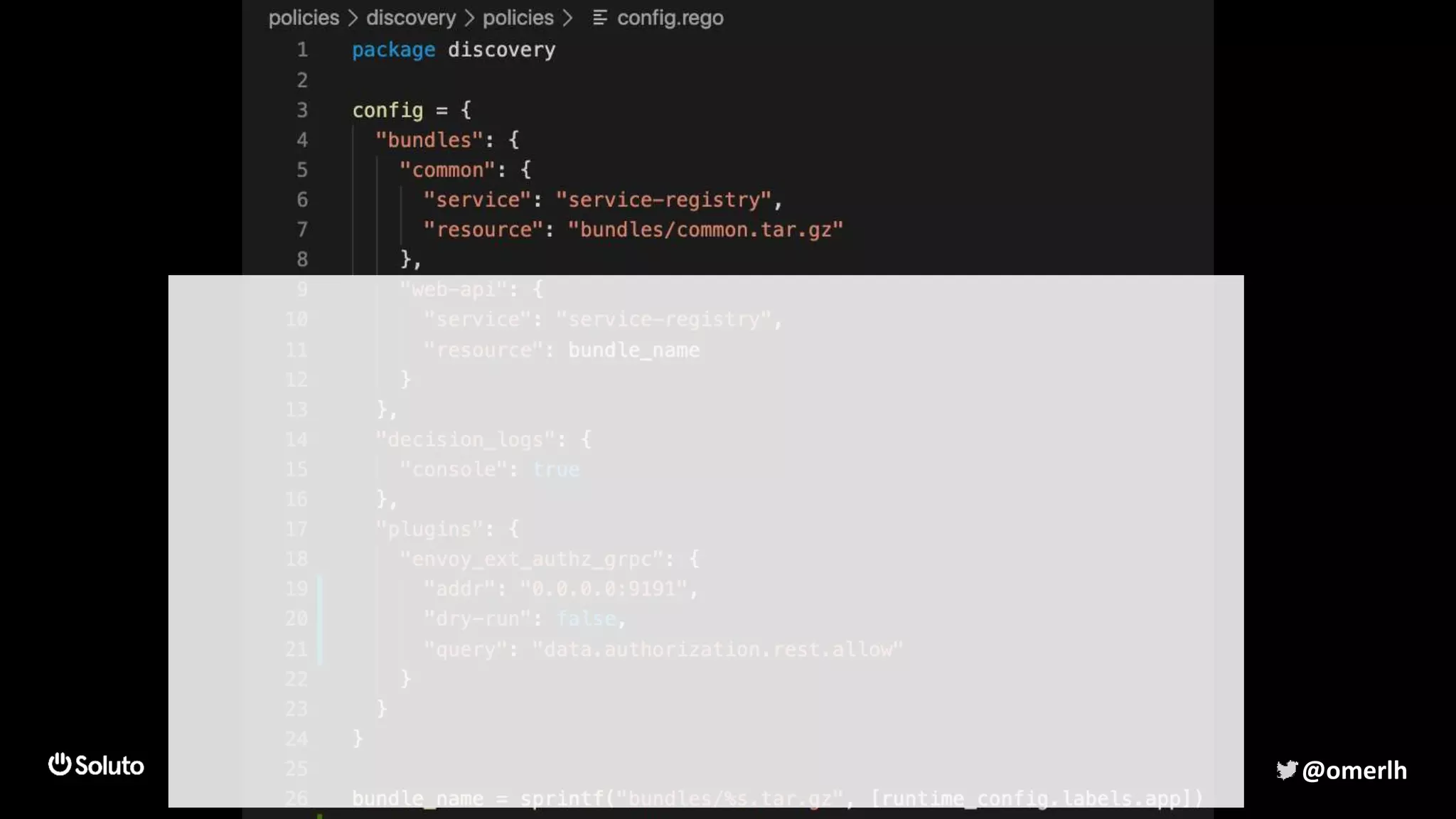
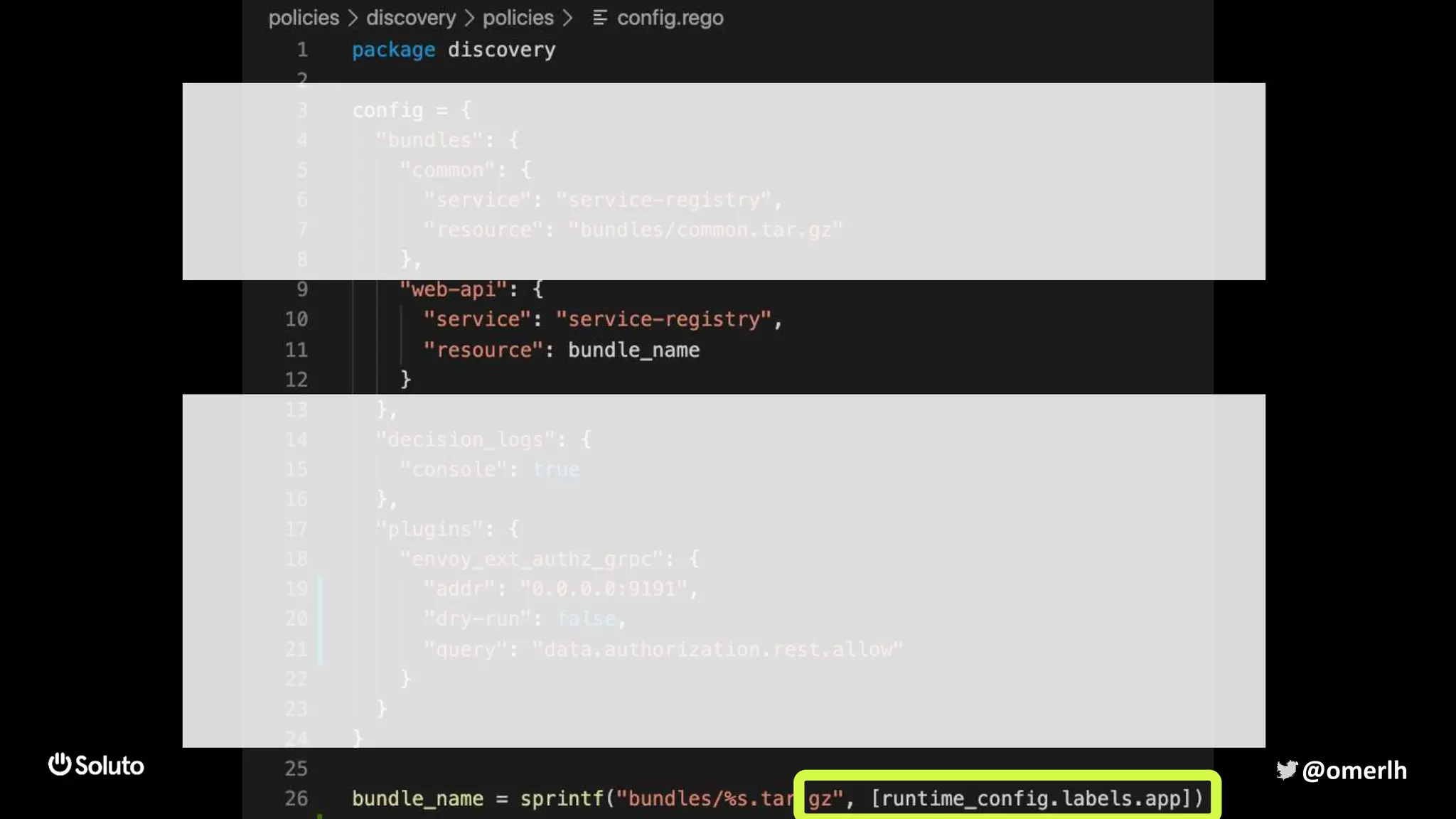
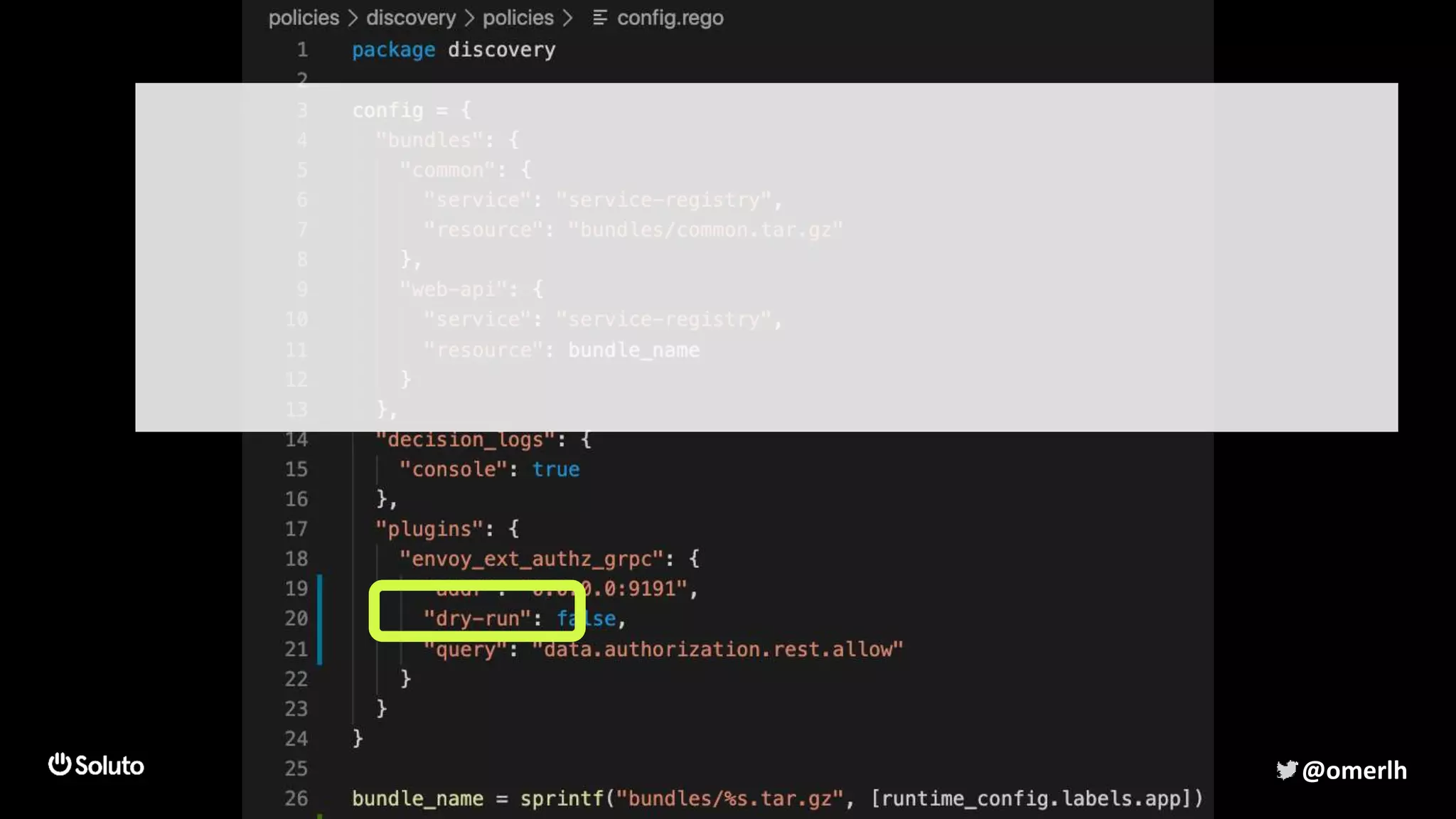
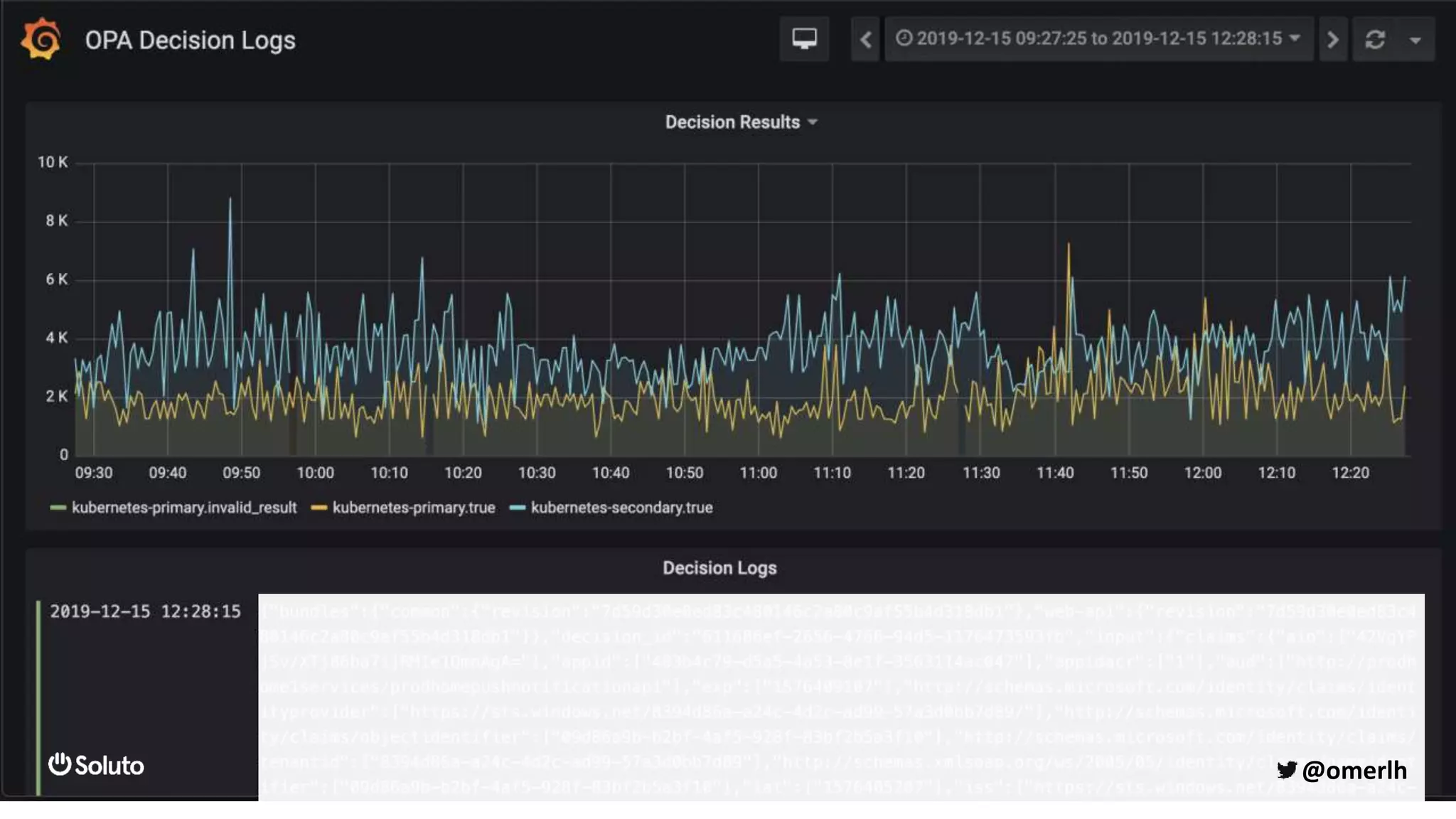
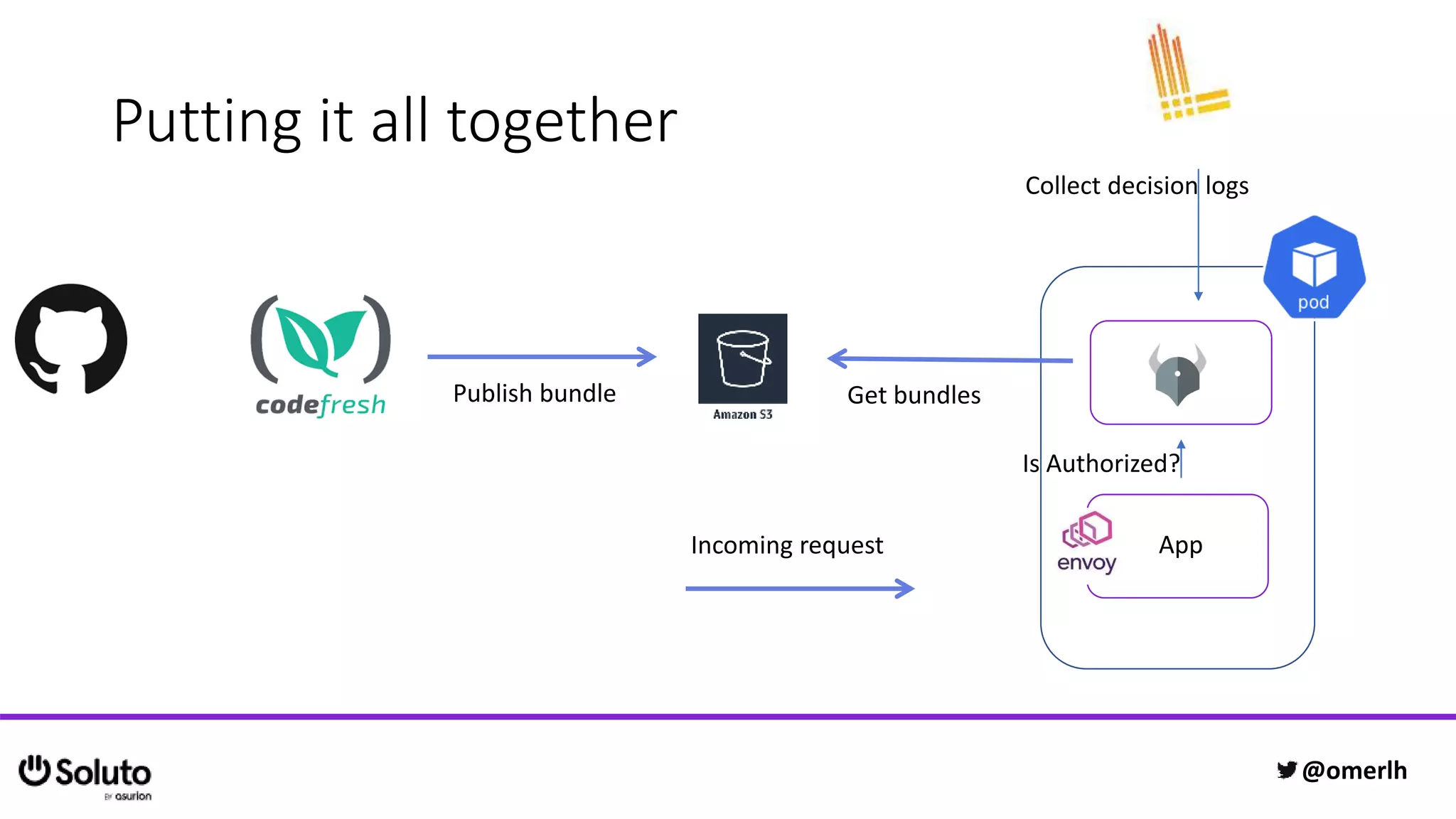
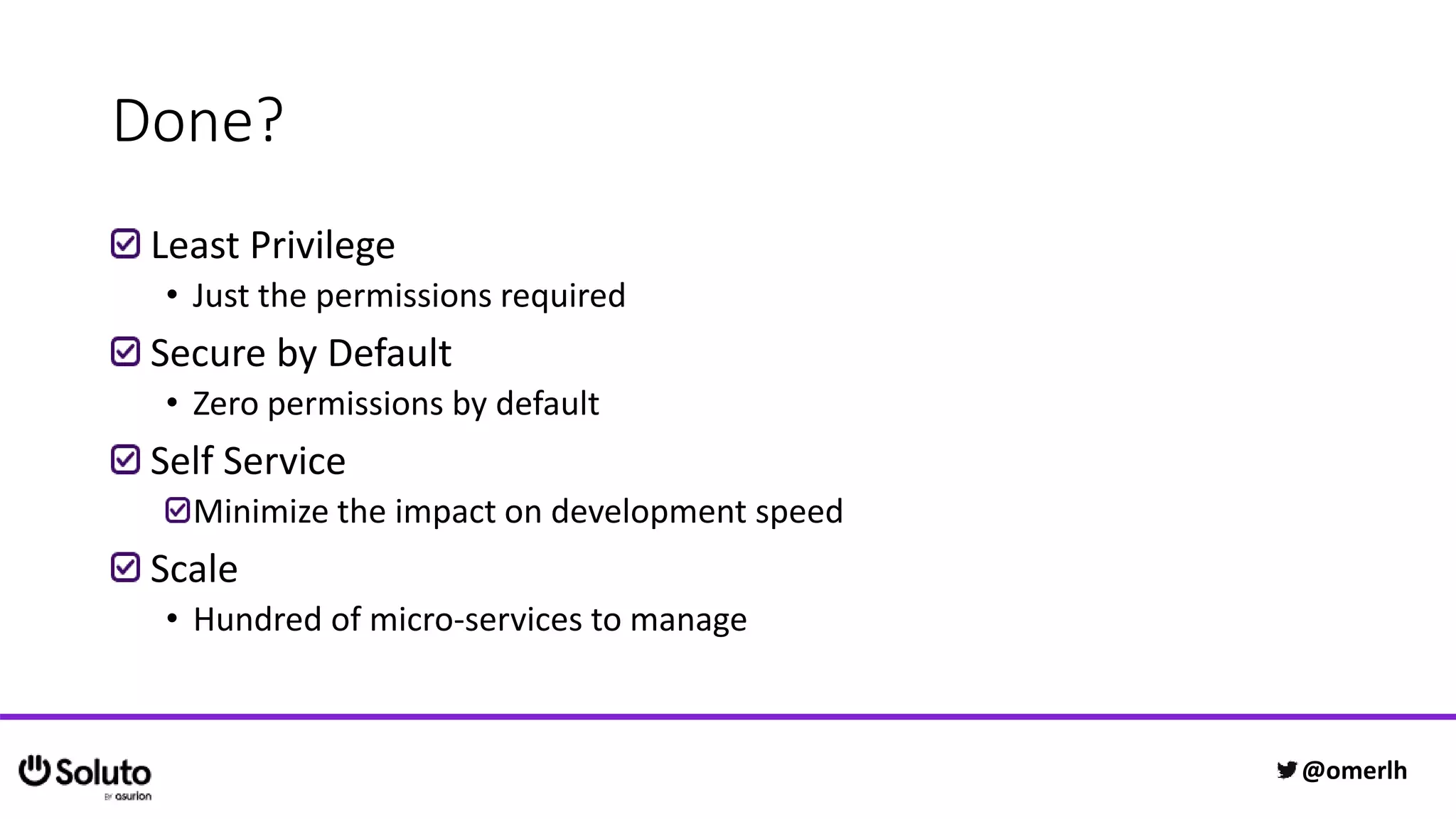
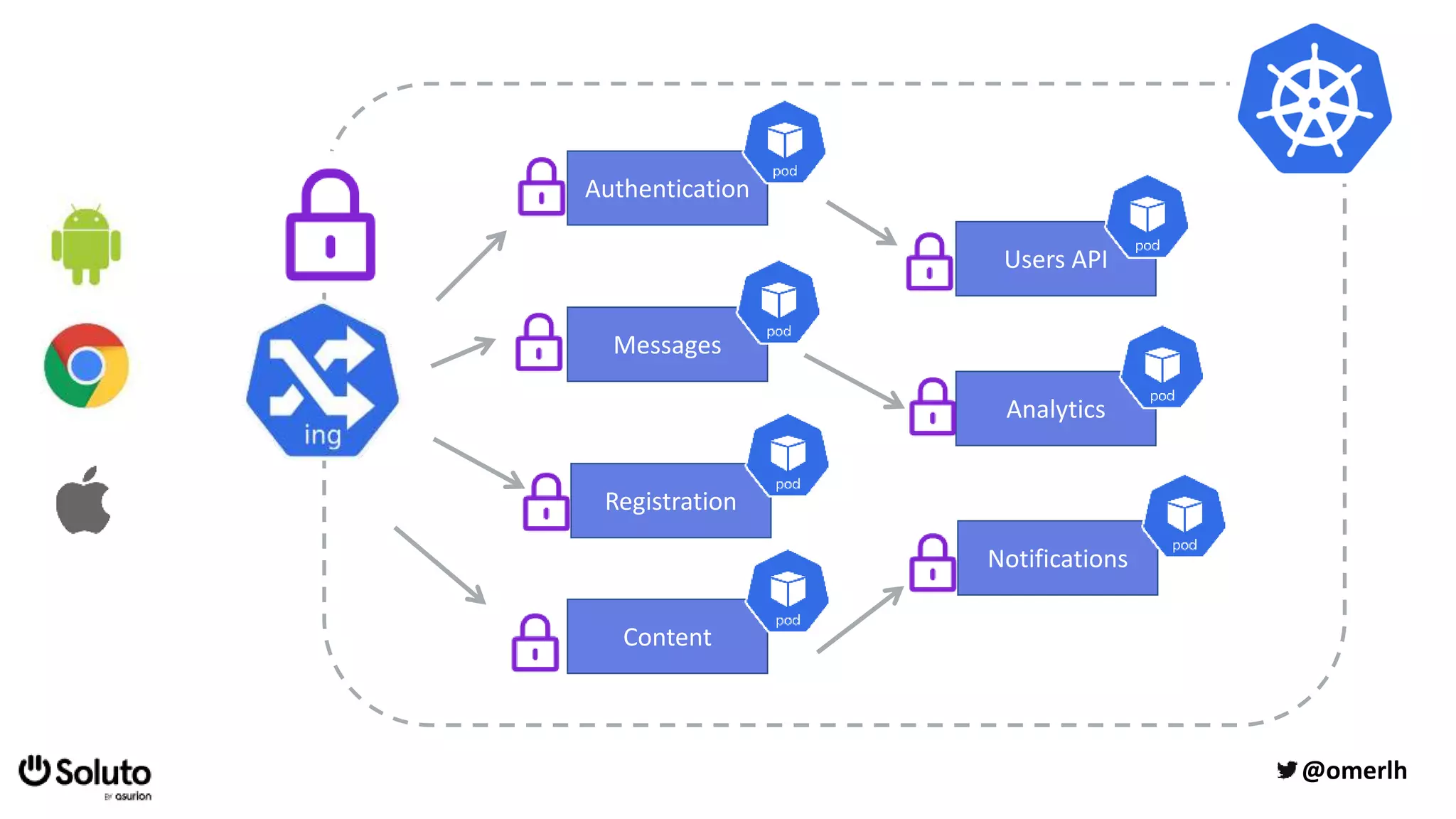
The document discusses building a scalable authorization system that ensures trust across microservices using a zero-trust approach and least privilege principles. It highlights key components like the Envoy proxy and Open Policy Agent (OPA) for managing authentication and authorization, as well as the importance of audit logs and decision logging. The focus is on enabling developers to implement secure policies while minimizing the impact on development speed and complexity.