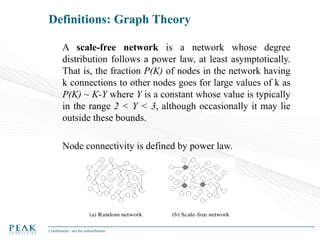
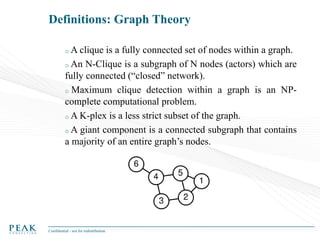
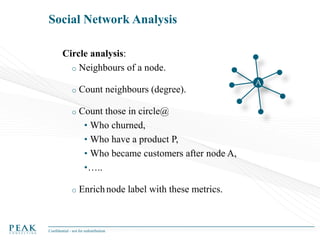
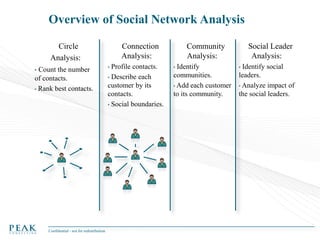
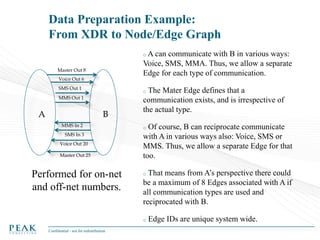
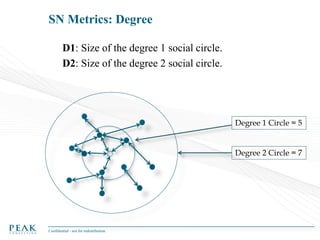
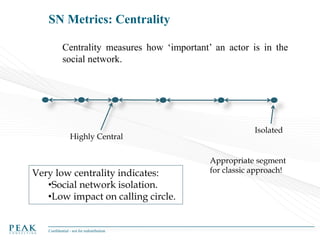
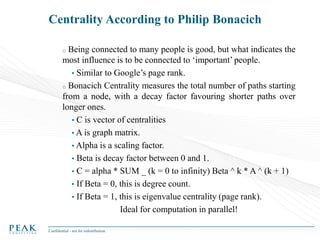
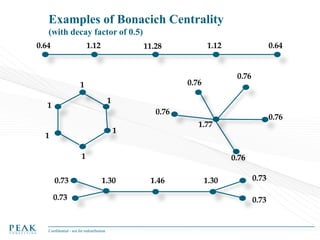
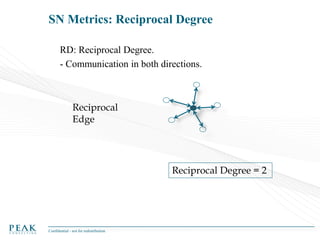
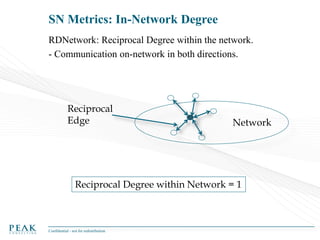
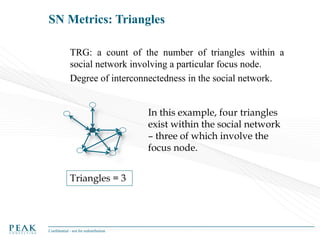
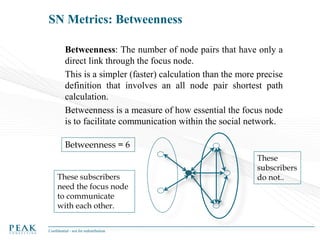
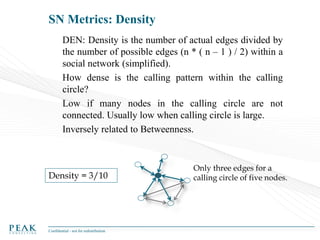
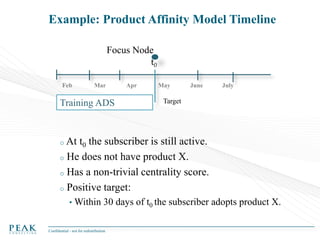
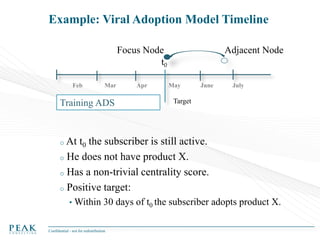
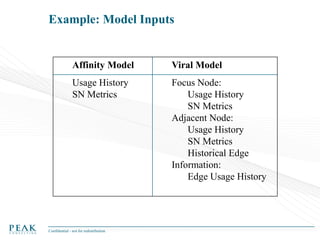
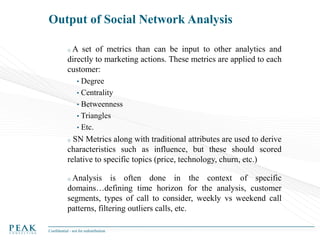
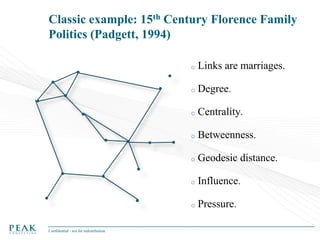
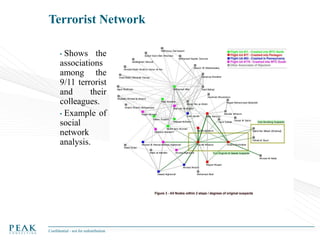
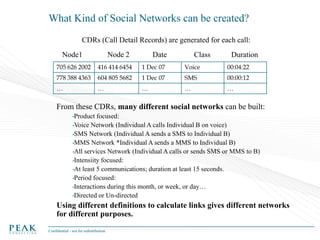
Social Network Analysis: Practical Uses and Implementation is a presentation that discusses social network analysis and its practical applications. It introduces key concepts such as social networks, social network analysis, roles in social networks, and graph theory. It also covers metrics and implementations of social network analysis, including calculating metrics from social networks and recommended approaches involving data preparation, metric calculation, model creation and scoring, and measurement. The presentation provides an overview of how social network analysis can be a useful tool for understanding relationships and influence.