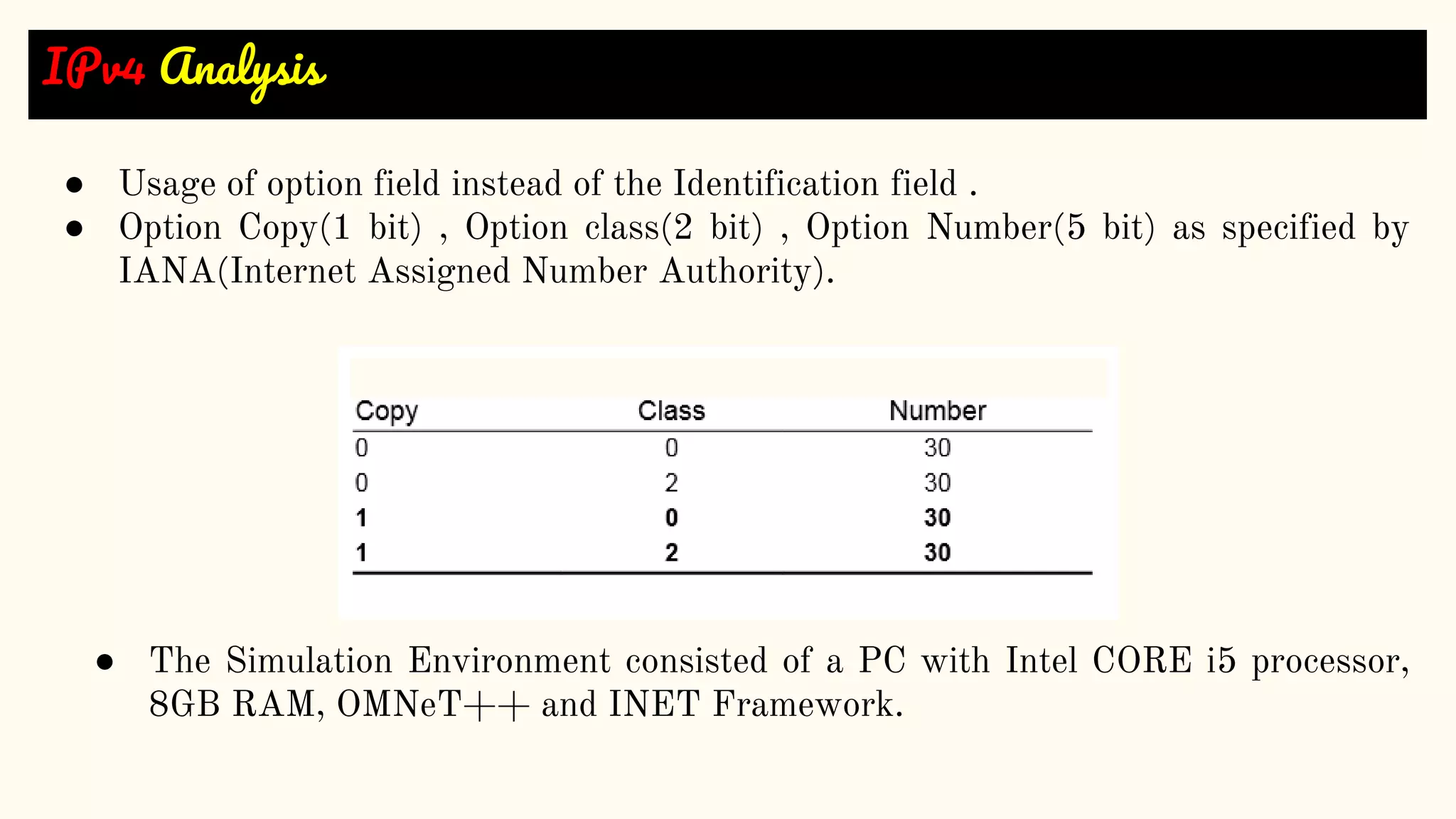
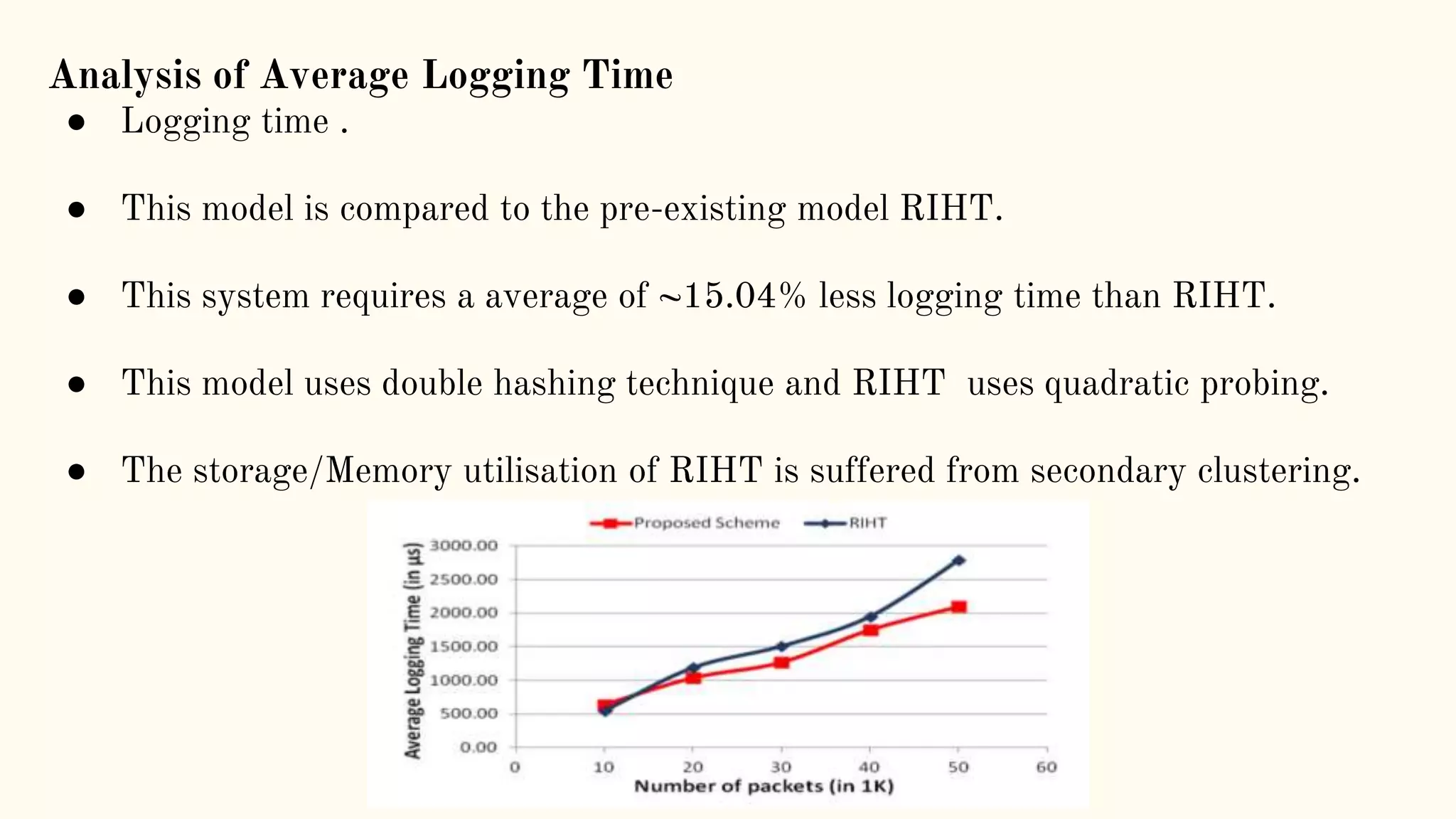
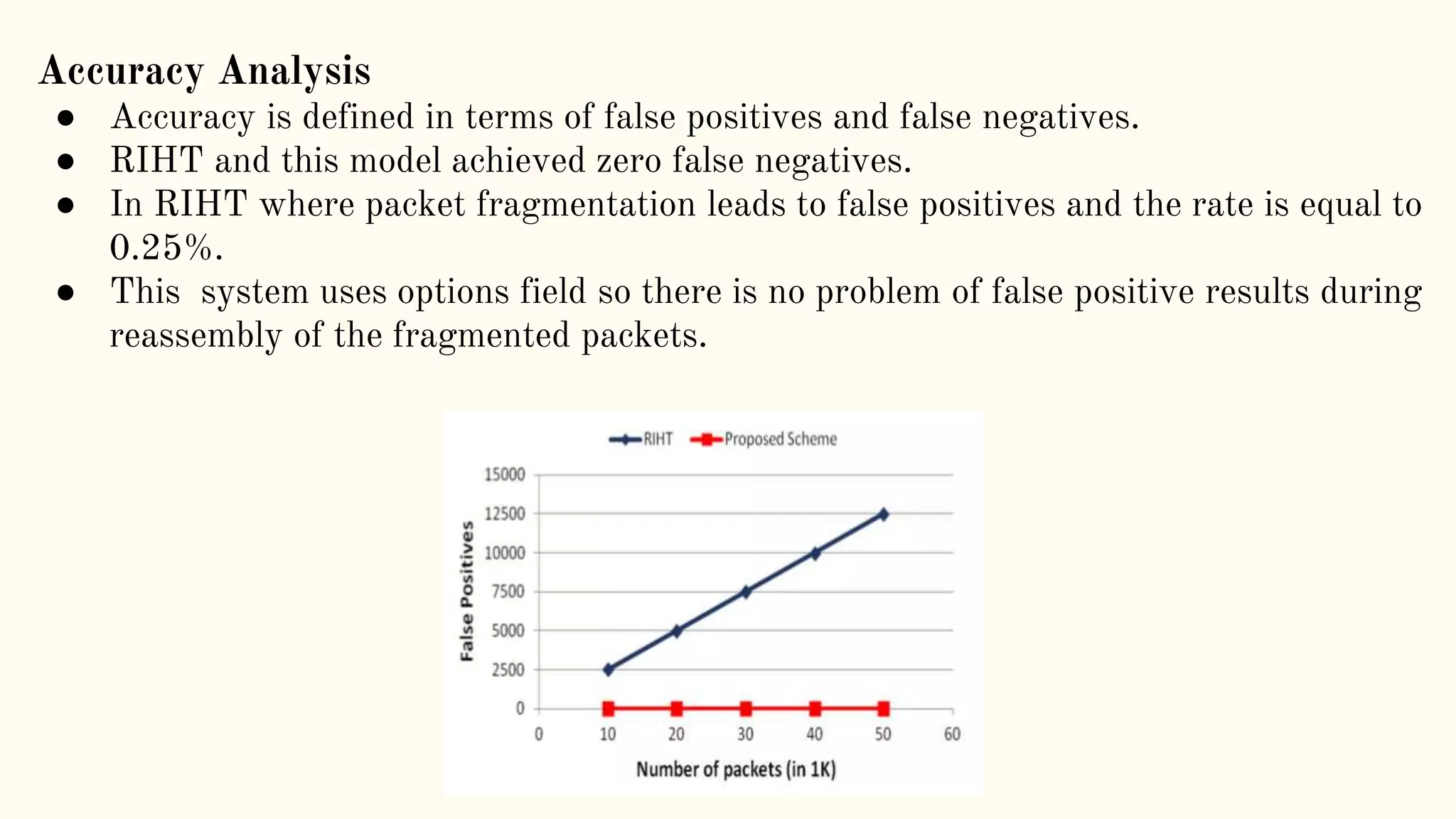
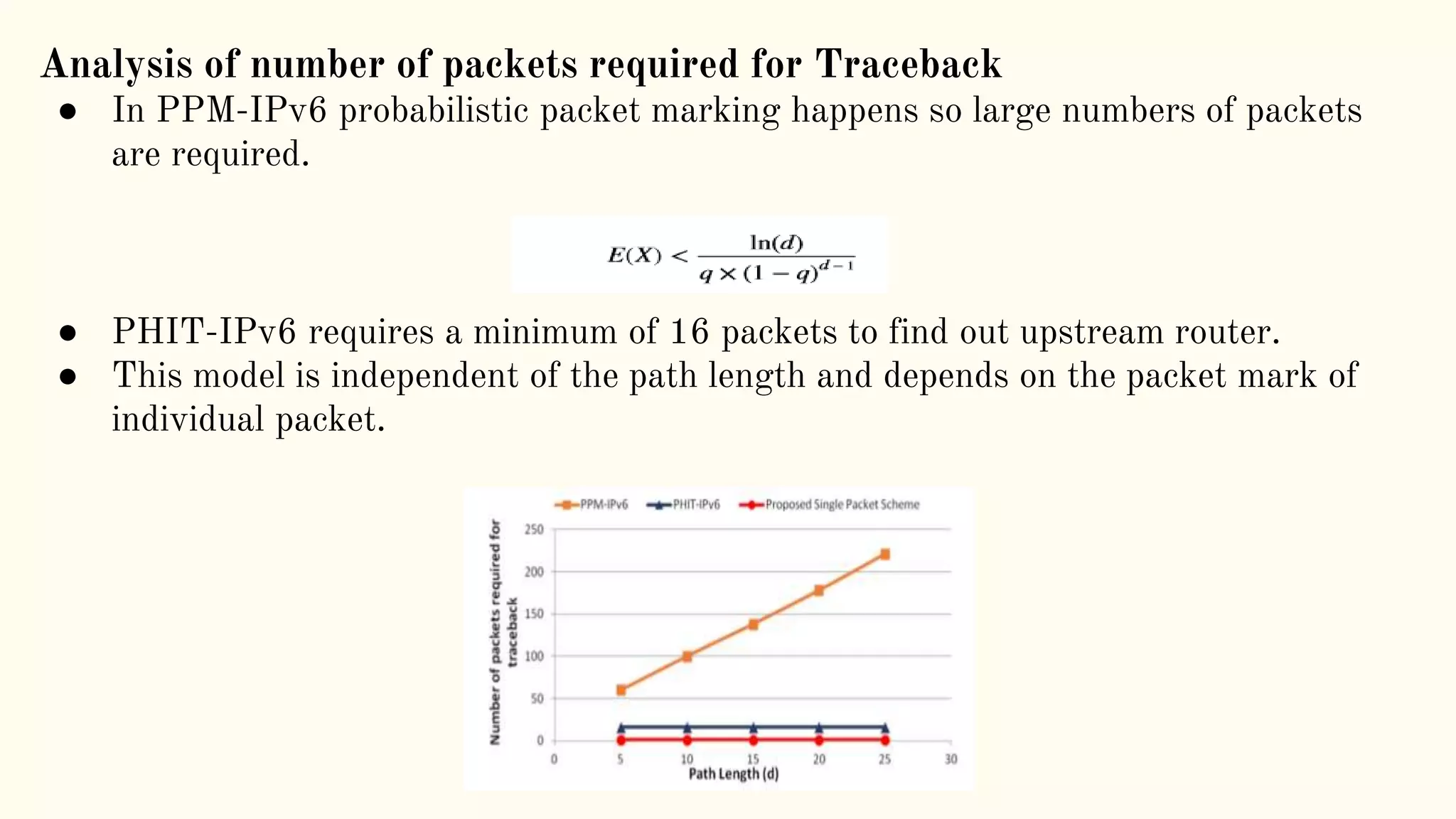
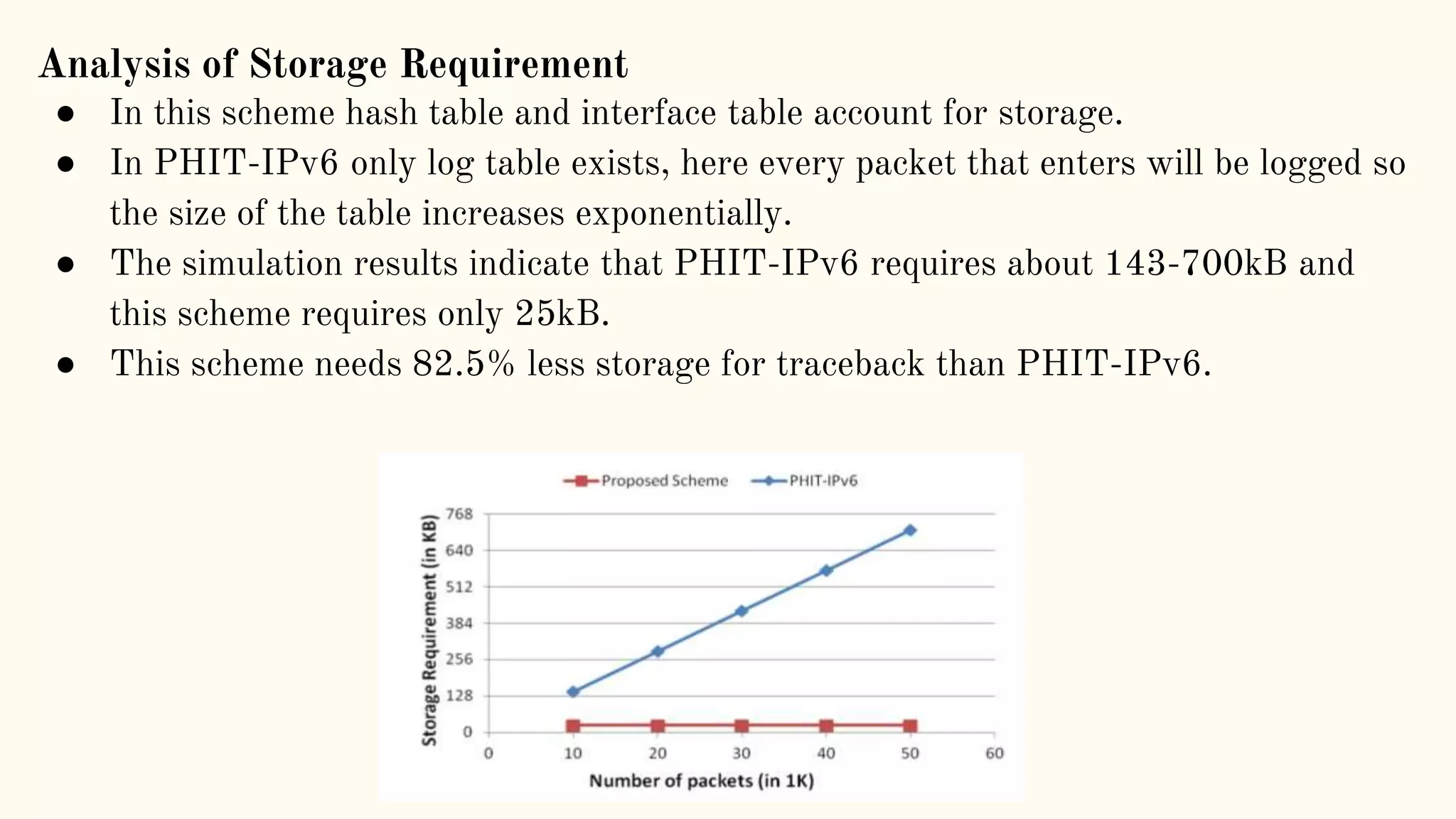
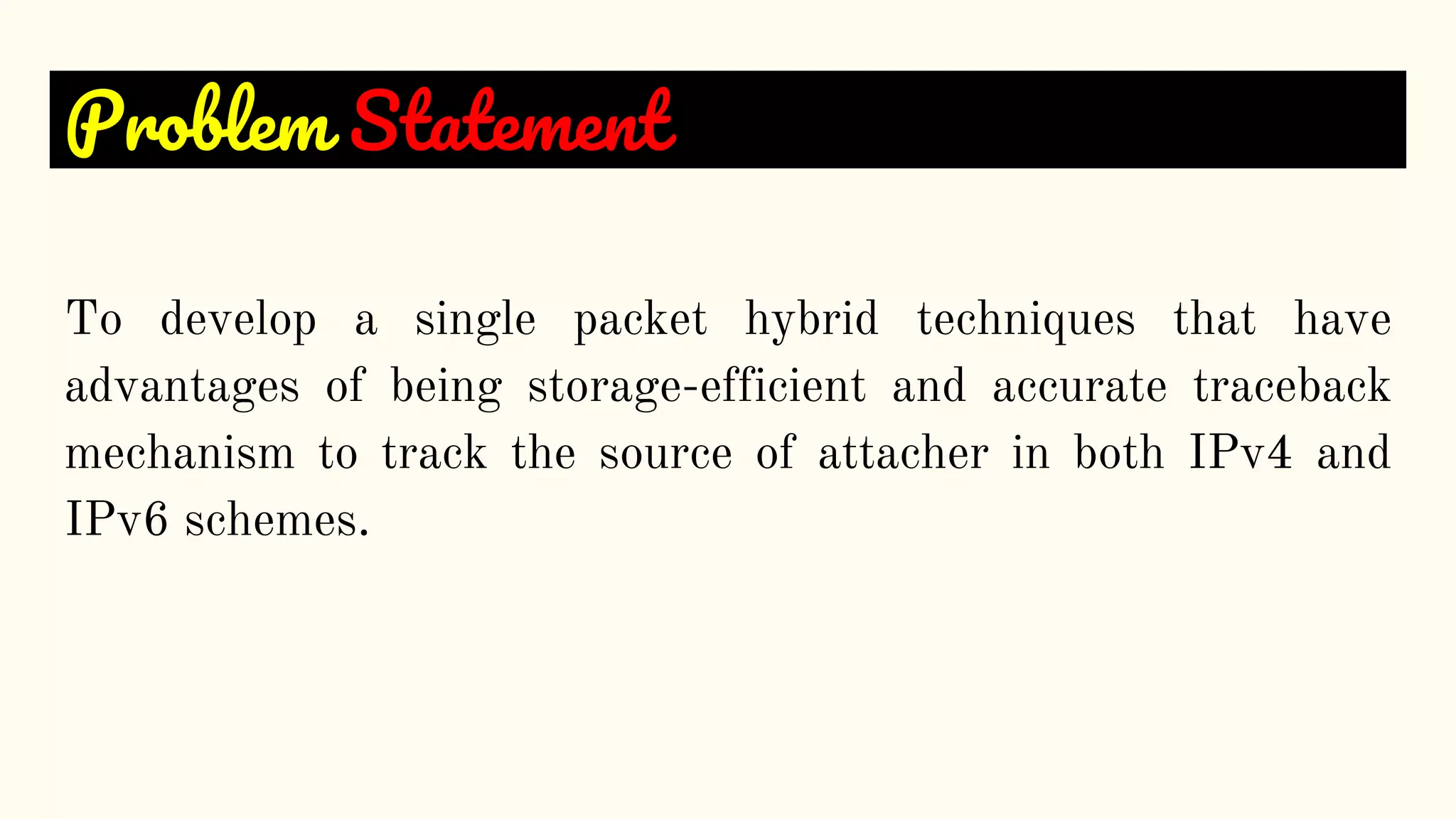
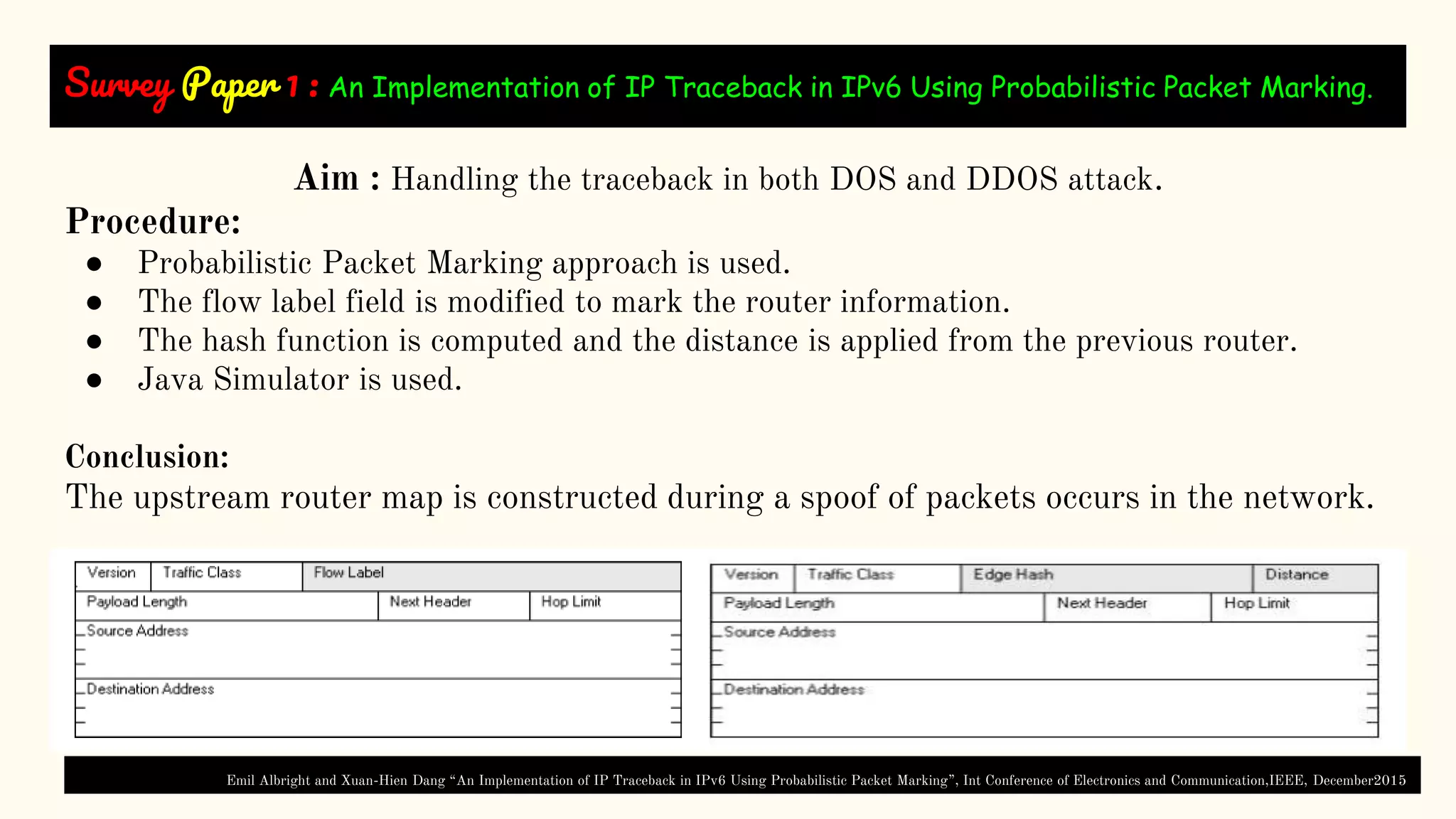
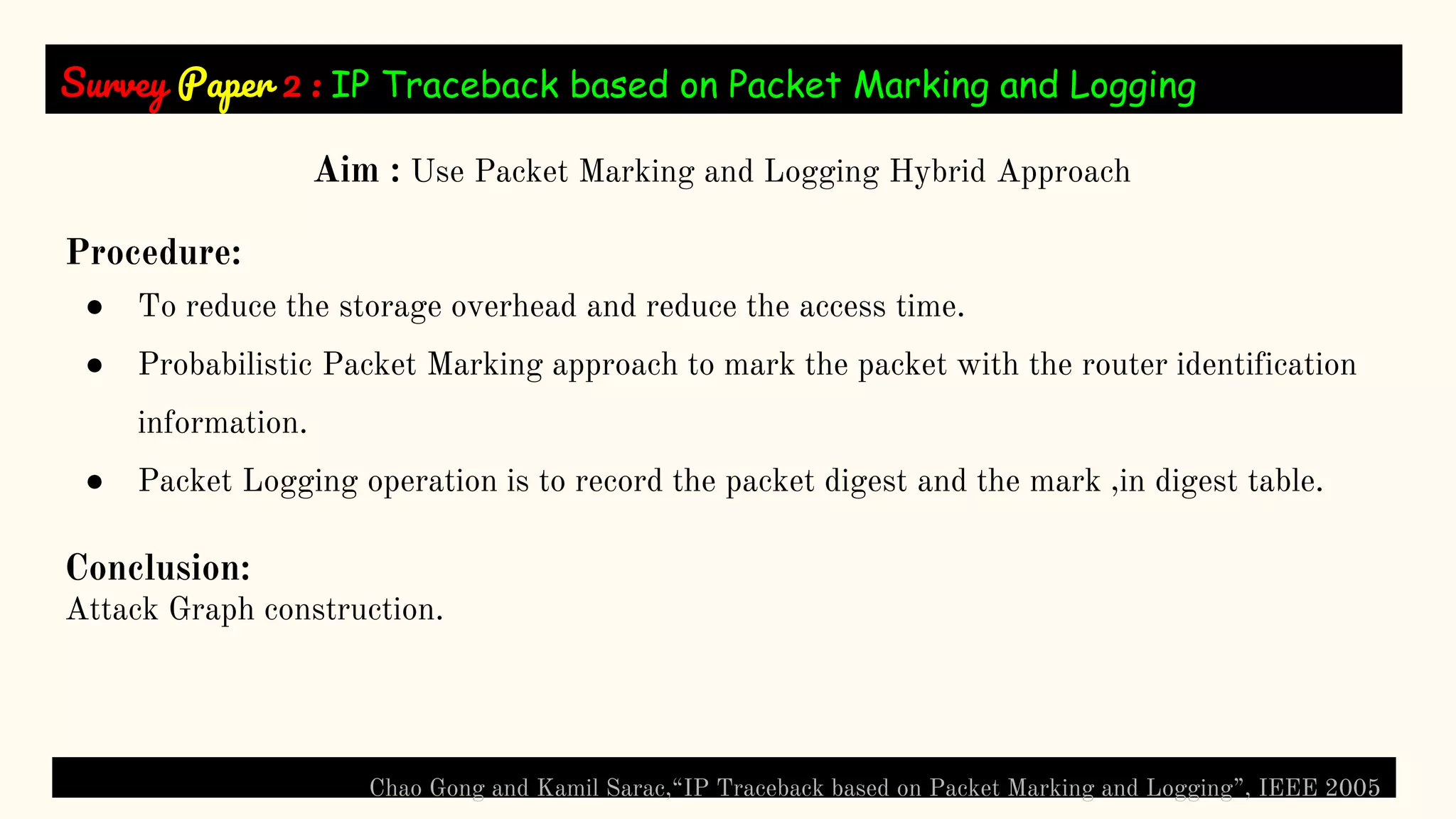
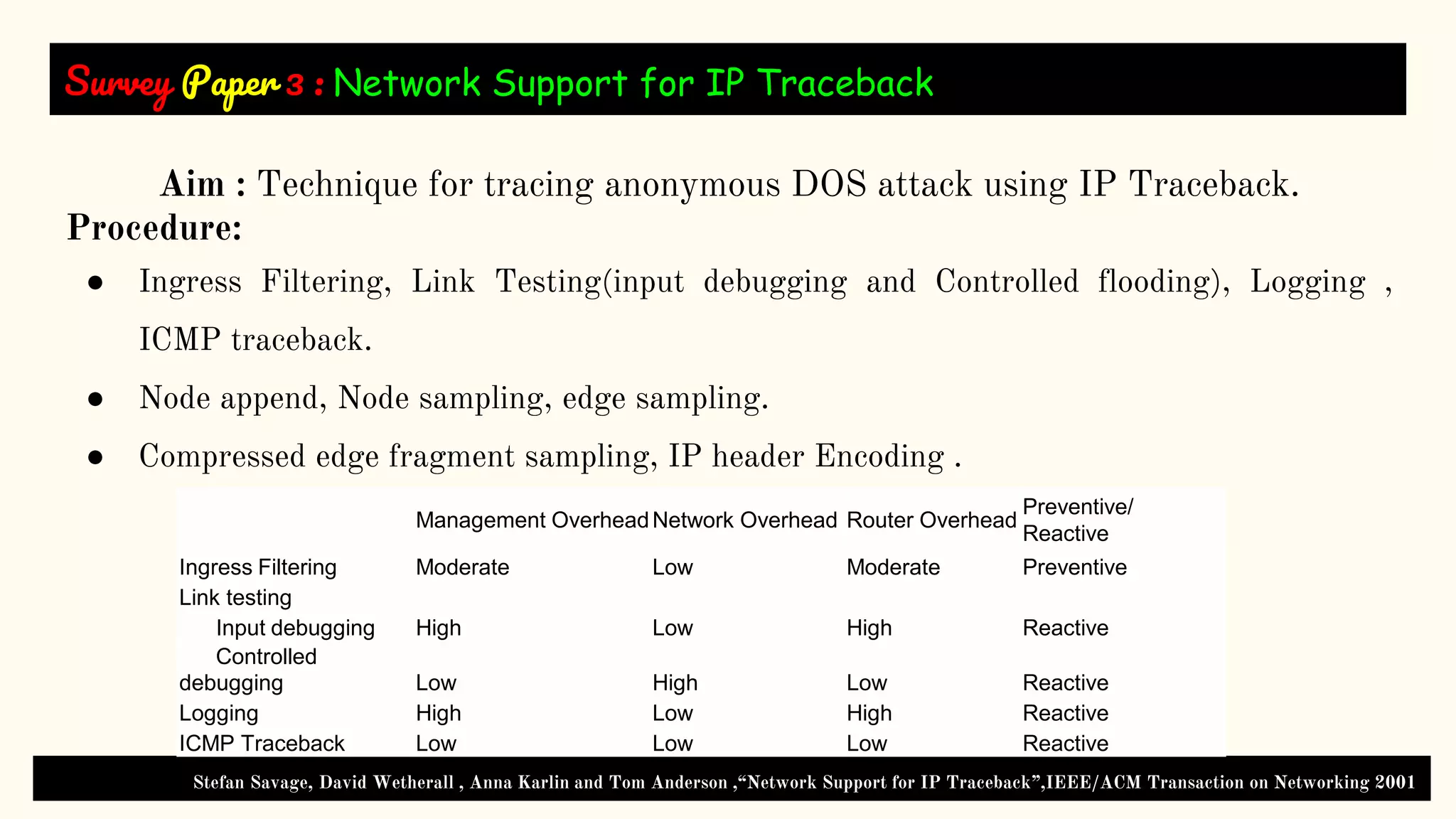
The document presents a technical seminar on a single-packet hybrid IP traceback mechanism applicable to both IPv4 and IPv6 networks, aimed at efficiently tracking the source of DDoS attacks. It reviews various literature on IP traceback methods, proposes a new algorithm for implementation, and compares its performance against existing models, concluding that the new scheme is storage-efficient and significantly reduces logging time. The findings emphasize the importance of recording path information rather than individual packet details to enhance cybersecurity measures.




![MARK_AND_LOG (Pi , UIK)
1. Begin
2. marknew <- Pi.mark X (D(Rk)+1)+UIk+1
3. first <-Pi.mark % m;
4. if marknew > 65535
5. l<- Pi.mark % m;
6. Skip<-1+(Pi.mark % (m-1));
7. Probe<-0;
8. While (HT[l] != null OR HT[l]!=Pi.mark AND Probe<m)
9. Increment probe by 1;
10. L<-(first +probe*skip)%m;
11. End while
12. If HT[l]= null then
13. HT[l]<-Pi.mark;
14. Endif
15. marknew<-l*(D(RK)+1)
16. Endif
17. Pi.mark<-marknew ;
18. Forward packet to next router with packet marked as Pi.mark
19. End
PATH_RECONSTRUCT (marknew)
1. Begin
2. UIk <- markreq%(D(Rk)+1)-1
3. If UIk = -1 then
4. L<- markreq/ (D(Rk)+1)
5. If l!=0 then
6. Set markold to HT[l].mark and UIk to HT[l].UIk
7. CALL PATH_RECONSTRUCT (markold) on adjacent router linked via UIk
8. Else
9. The current router is attacker’s source
router
10. Endif
11. Else
12. Markold<- markreq/(D(Rk)+1)
13. CALL PATH_RECONSTRUCT(markold) on adjacent router linked via UIk
14. Endif
15. end](https://image.slidesharecdn.com/technicalseminarfinal-180509191230/75/Single-packet-hybrid-IP-traceback-for-IPv4-and-IPv6-networks-11-2048.jpg)