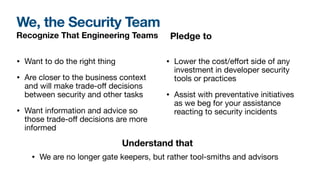
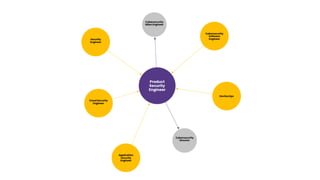
Steven Carlson's talk focuses on sharing experiences in product security and driving change within information security. He emphasizes the importance of collaboration between security teams and engineering to prioritize security throughout the software development process, encouraging knowledge sharing and responsive strategies. Key topics include onboarding, empowering teams, automation, and executive buy-in for effective security practices.