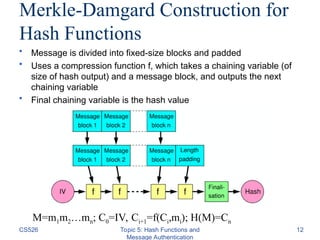
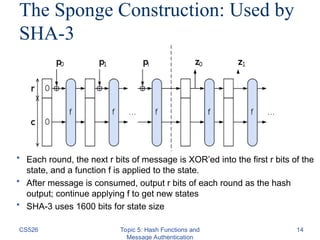
The document discusses cryptographic hash functions and message authentication, highlighting their importance for data integrity and source authentication. It describes various hash functions, their security requirements, and methods for ensuring message integrity, including the use of Message Authentication Codes (MAC). Key concepts such as one-wayness, collision resistance, and the construction of MAC using hash functions are also covered, along with the latest advancements in hash algorithms like SHA-3.




![Hash Functions
• A hash function maps a message of an arbitrary length to
a m-bit output
– output known as the fingerprint or the message digest
• What is an example of hash functions?
– Give a hash function that maps Strings to integers in [0,2^{32}-1]
• Cryptographic hash functions are hash functions with
additional security requirements
CS526 Topic 5: Hash Functions and
Message Authentication
5](https://image.slidesharecdn.com/526topic05-241001050308-f3534aa4/85/SHA-New-Revised-Version-SHA-512-Syllabus-Module-3-5-320.jpg)













![CS526 Topic 5: Hash Functions and
Message Authentication
21
HMAC: Constructing MAC from
Cryptographic Hash Functions
• K+
is the key padded (with 0) to B bytes, the
input block size of the hash function
• ipad = the byte 0x36 repeated B times
• opad = the byte 0x5C repeated B times.
HMACK[M] = Hash[(K+
opad) || Hash[(K+
ipad)||M)]]
At high level, HMACK[M] = H(K || H(K || M))](https://image.slidesharecdn.com/526topic05-241001050308-f3534aa4/85/SHA-New-Revised-Version-SHA-512-Syllabus-Module-3-21-320.jpg)

