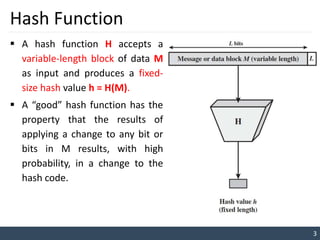
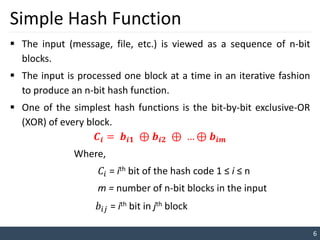
The document discusses hash functions and their applications in message authentication. It defines a hash function as accepting a variable-length input and producing a fixed-size output hash value. A good hash function results in different outputs for any change to the input. The document outlines requirements for hash functions including producing fixed-length outputs, easy computation, and collision resistance. It describes simple hash functions using bitwise XOR of blocks and more secure hash algorithms like Secure Hash Algorithm (SHA).