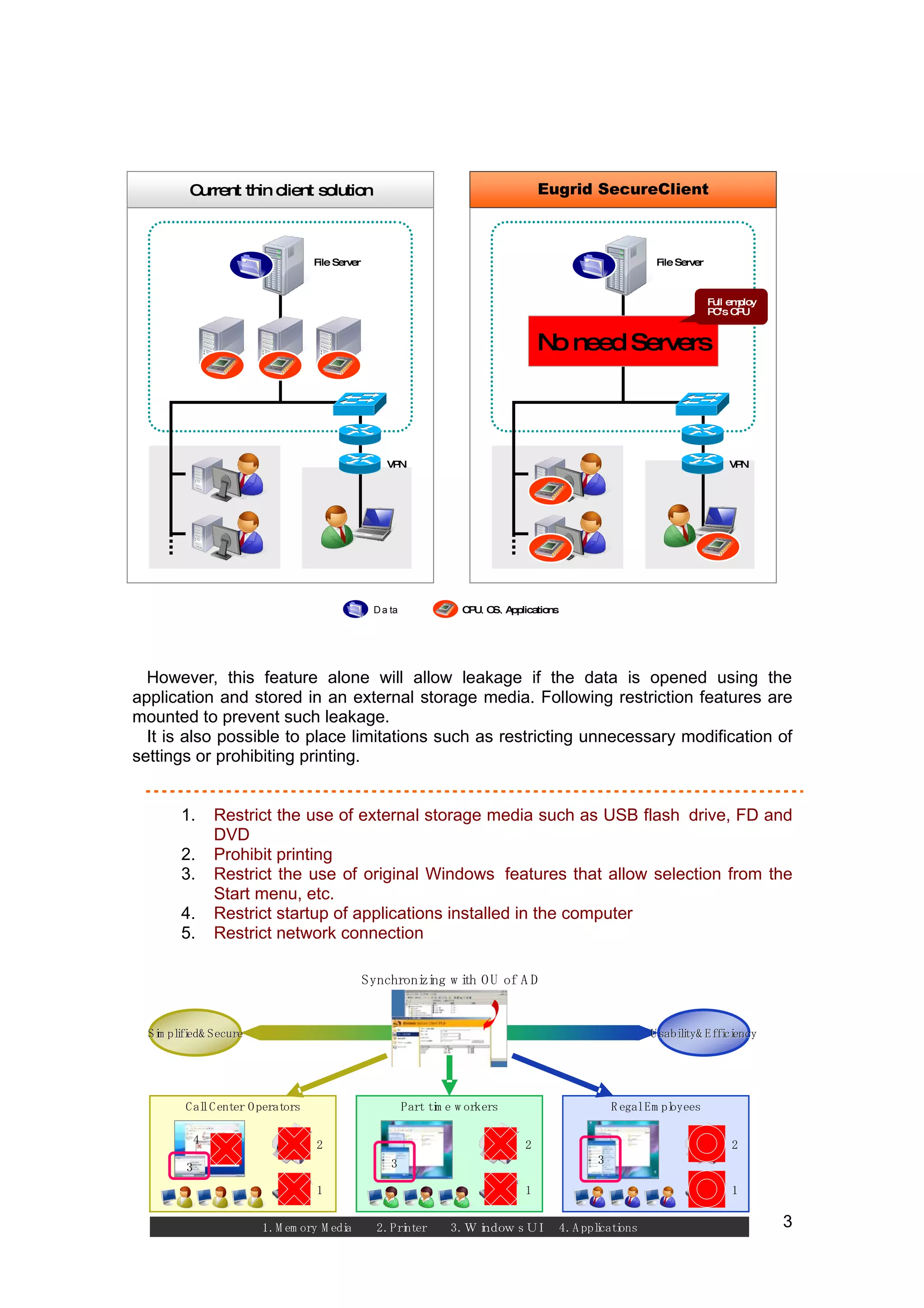
1. Eugrid SecureClient is a thin client solution that provides high security without requiring new hardware or modifications to existing computers. It utilizes write protection and virtual redirection to prevent data from being saved locally.
2. The solution redirects data to centralized servers while allowing normal computer usage. Various restrictions can also be applied to control data access and security levels.
3. A mobile option allows secure access to data outside the company using a USB flash drive, preventing data leakage even if the laptop is lost or stolen.