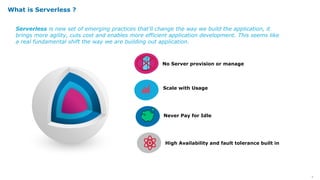
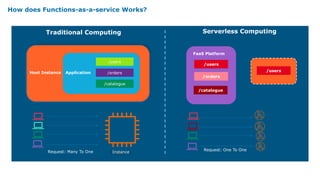
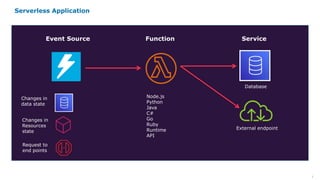
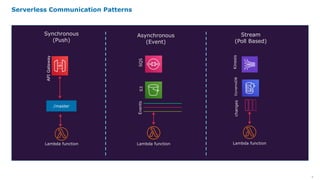
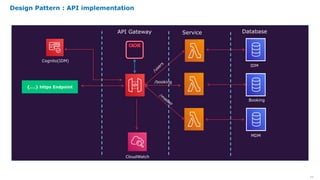
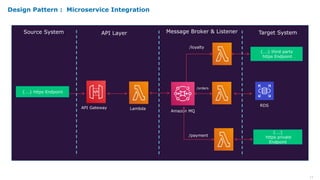
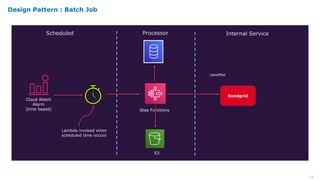
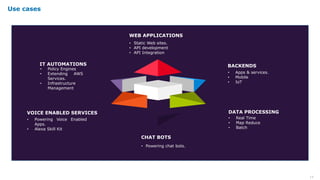
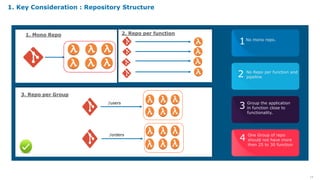
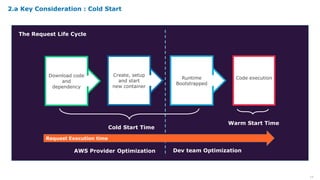
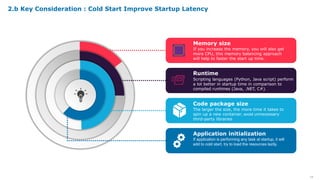
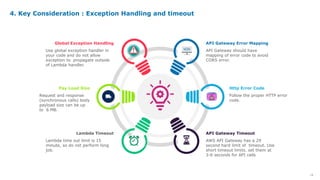
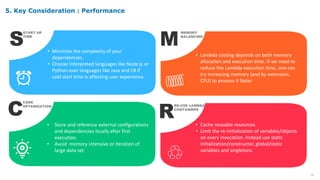
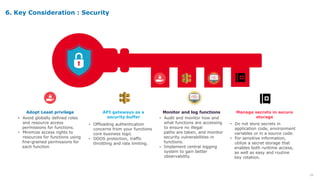
Serverless computing provides several key benefits including no need to provision or manage servers, automatic scaling with usage, only paying for resources used, and built-in high availability and fault tolerance. Some common use cases for serverless include backend services and apps, data processing, voice and chat bots, and web applications. When building serverless applications, developers should consider factors like repository structure, cold starts, package size and dependencies, timeouts and errors, performance optimization, and security practices.