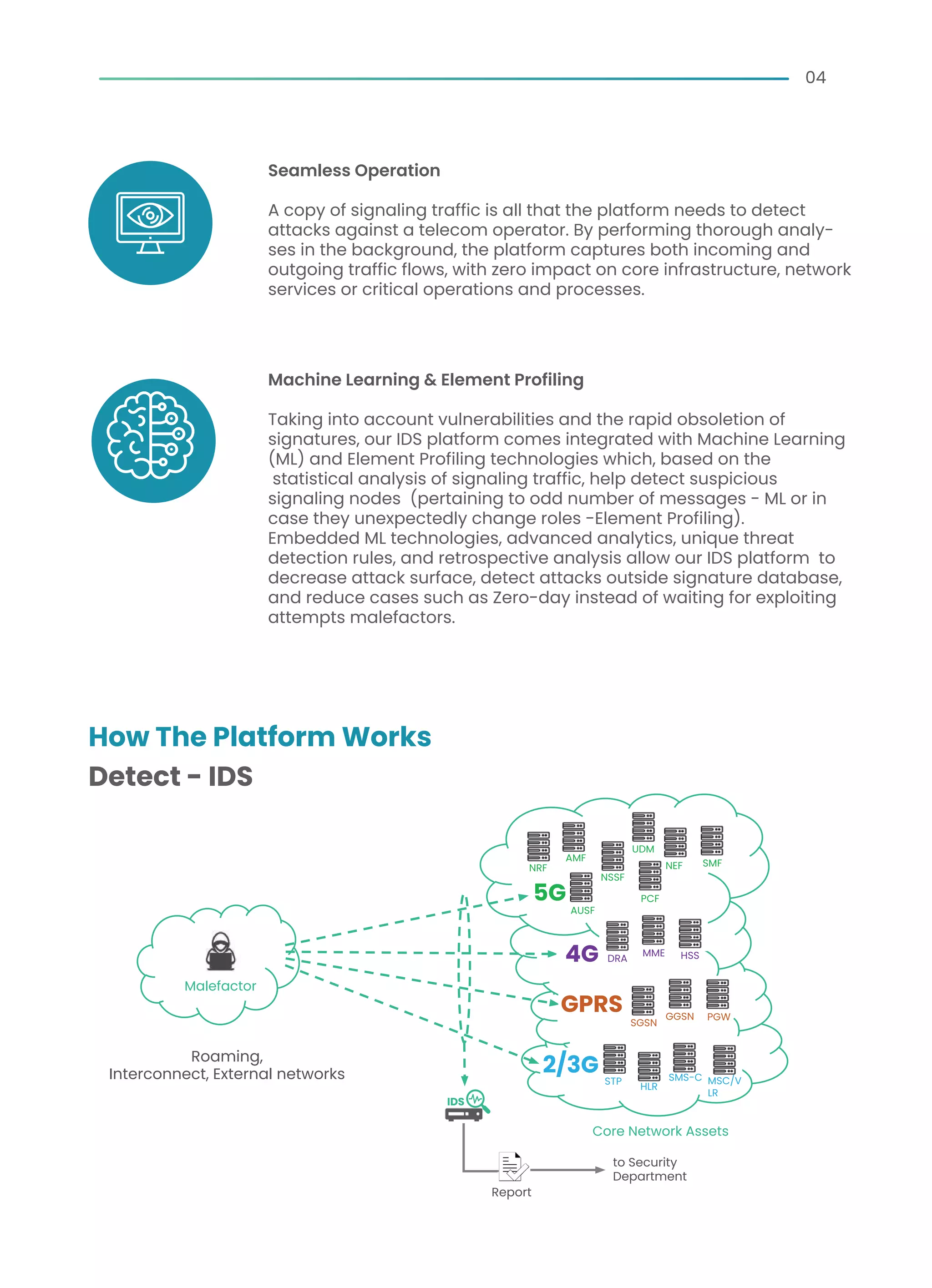
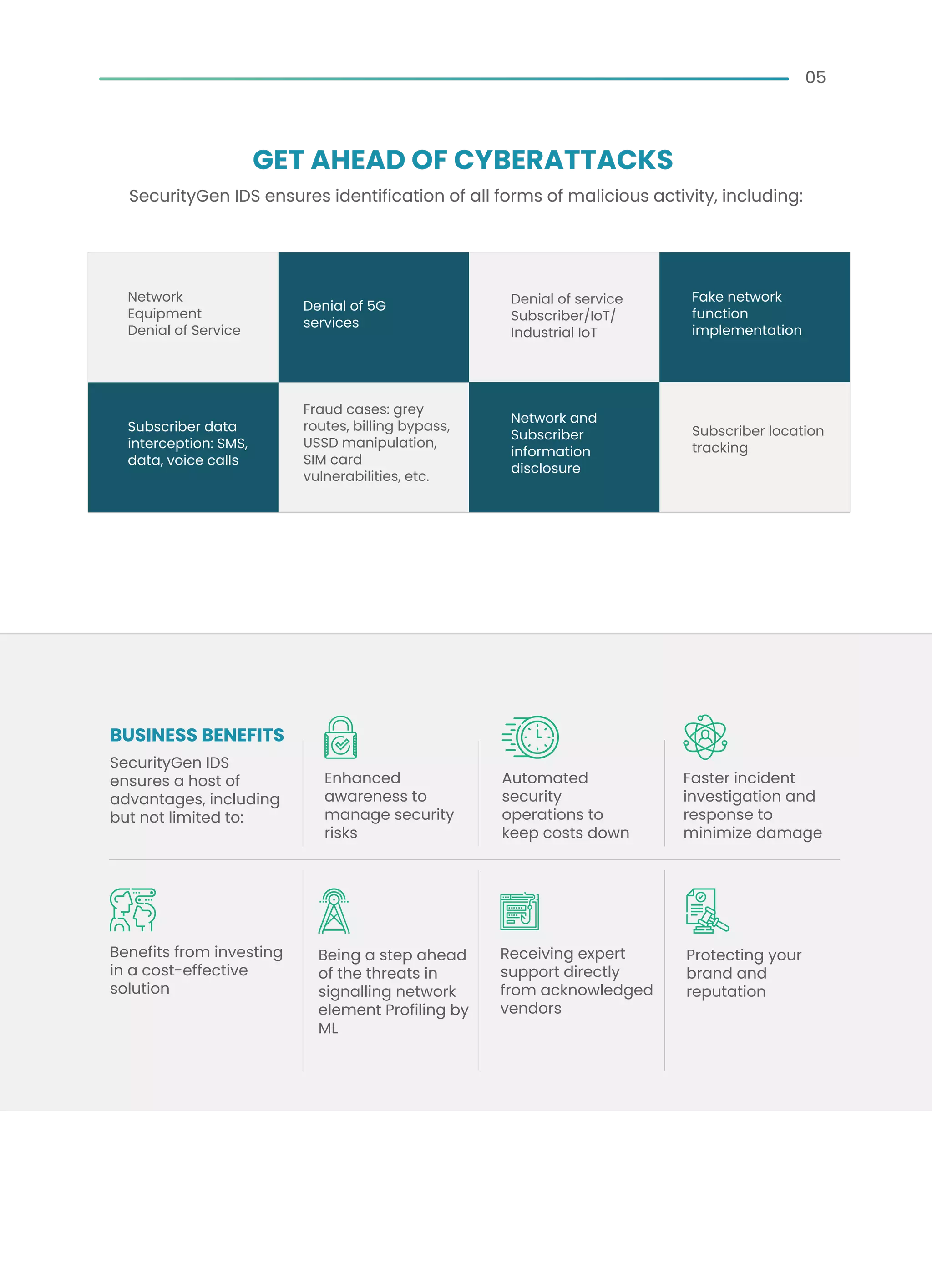
The document outlines the SecurityGen IDS platform, designed to protect telecom operators from cyber threats associated with vulnerable signaling protocols like SS7 and Diameter. It highlights features such as enhanced visibility for threat detection, advanced analytics for incident response, and integration capabilities with existing security systems. SecurityGen IDS offers comprehensive monitoring to prevent hacks, safeguard core networks, and improve overall cybersecurity posture in a rapidly evolving threat landscape.