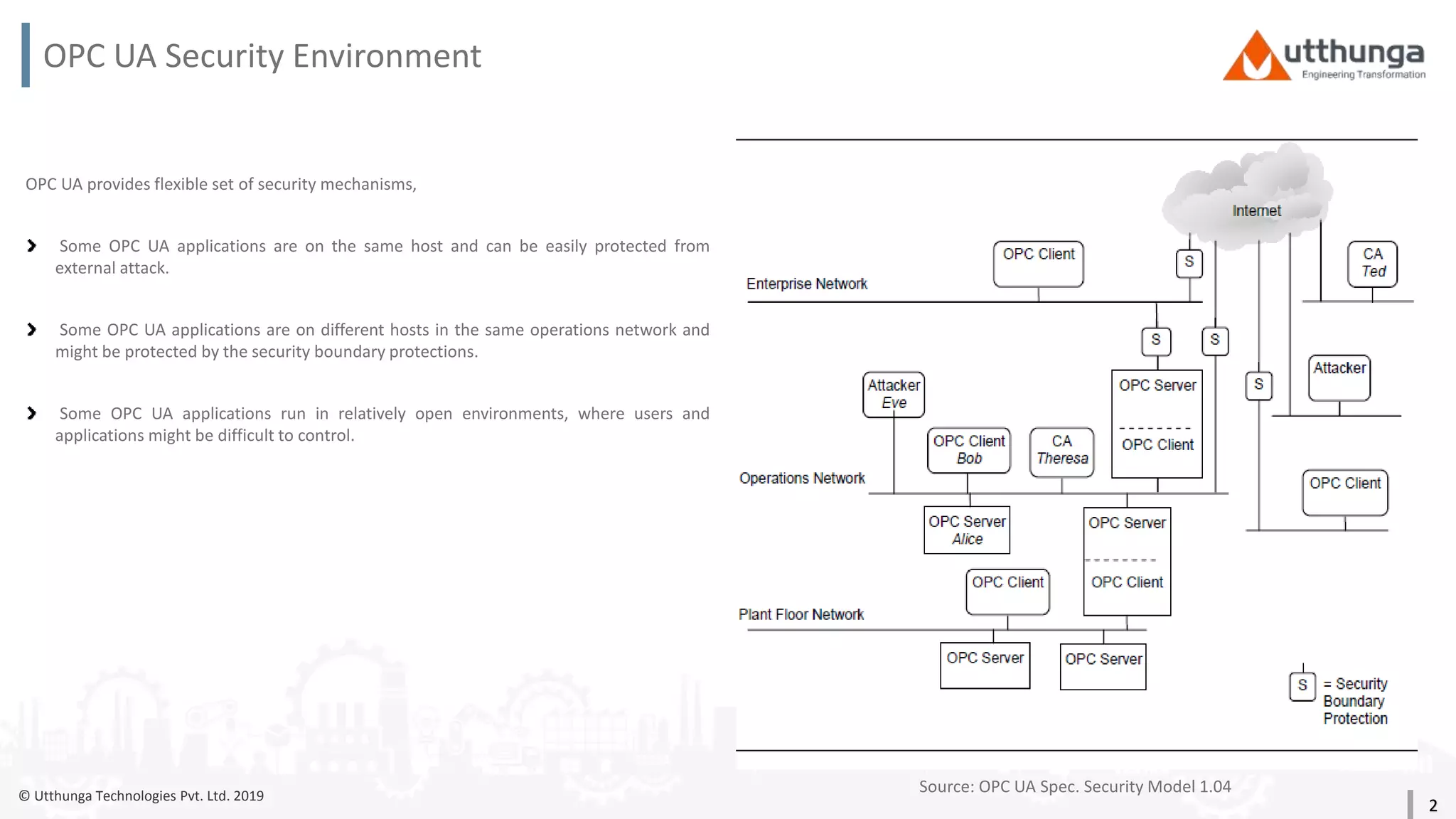
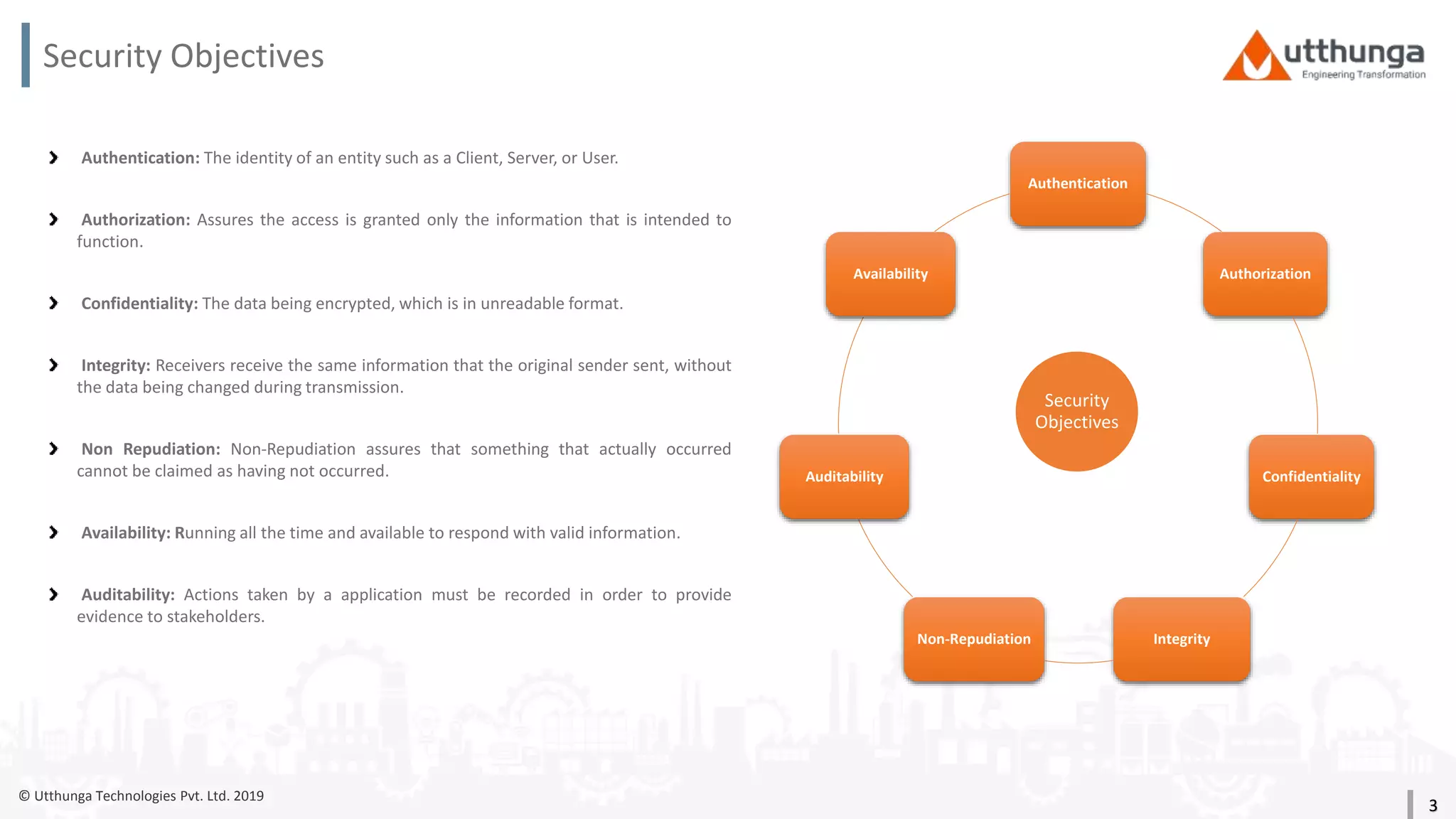
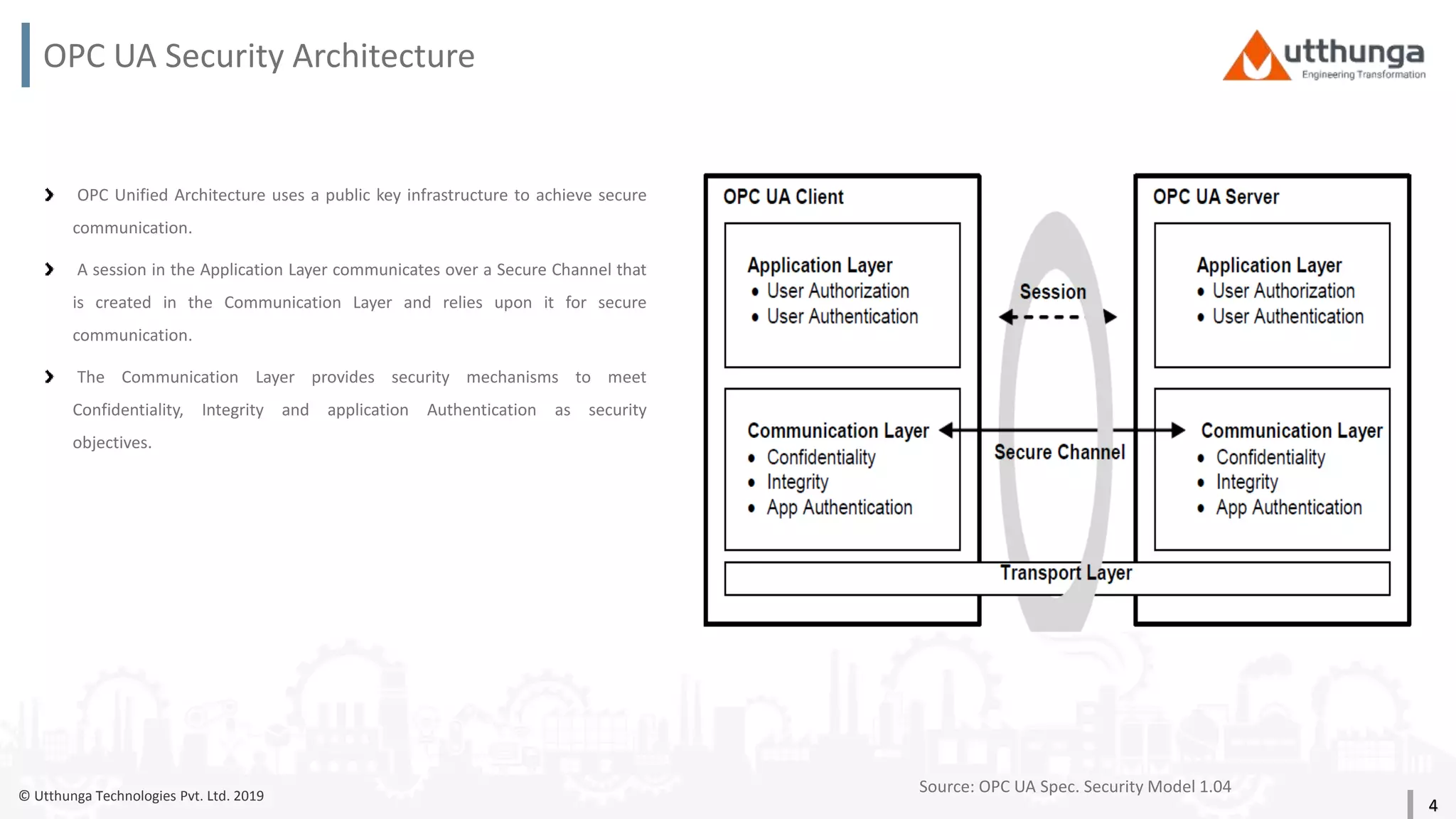
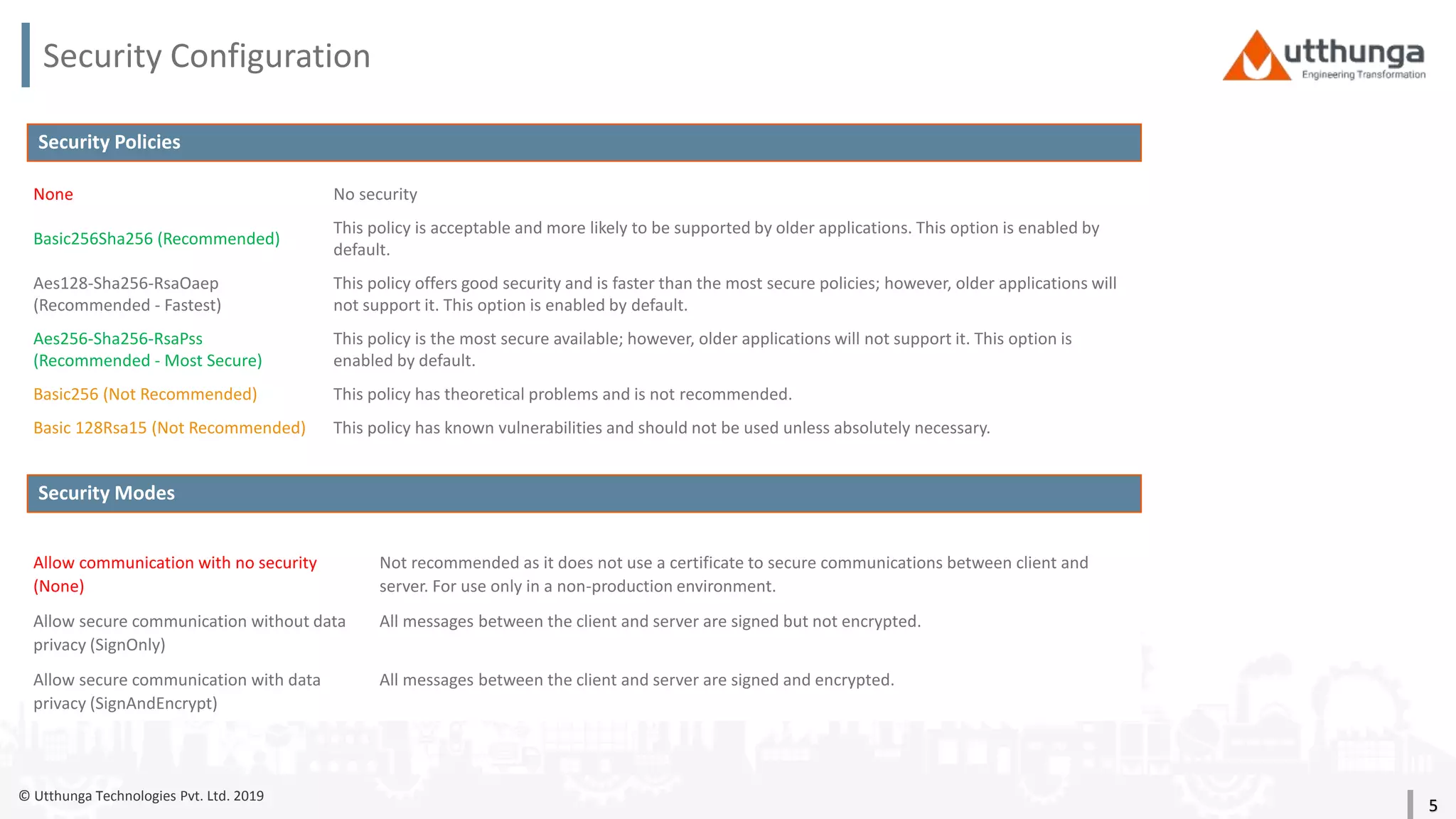
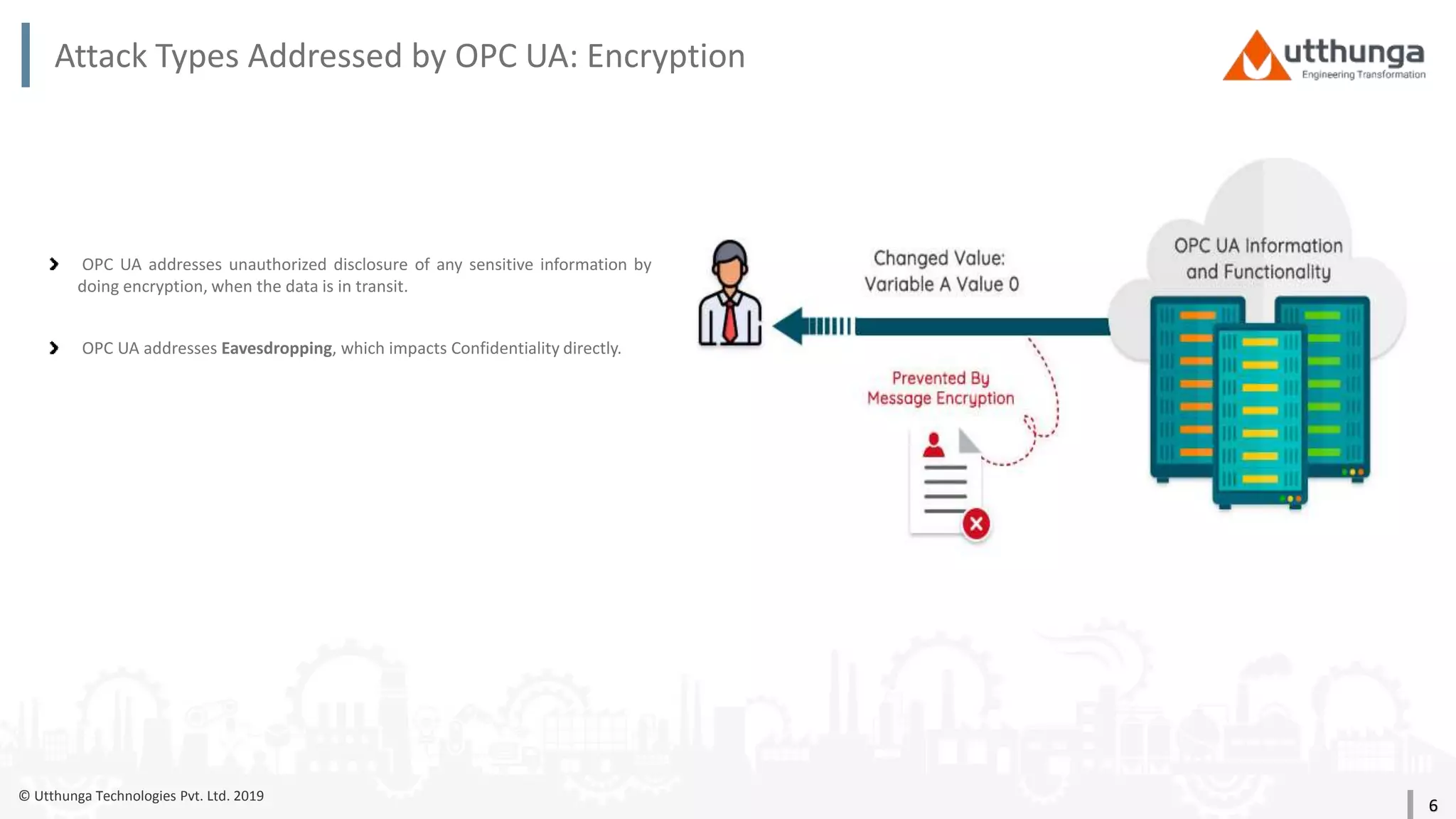
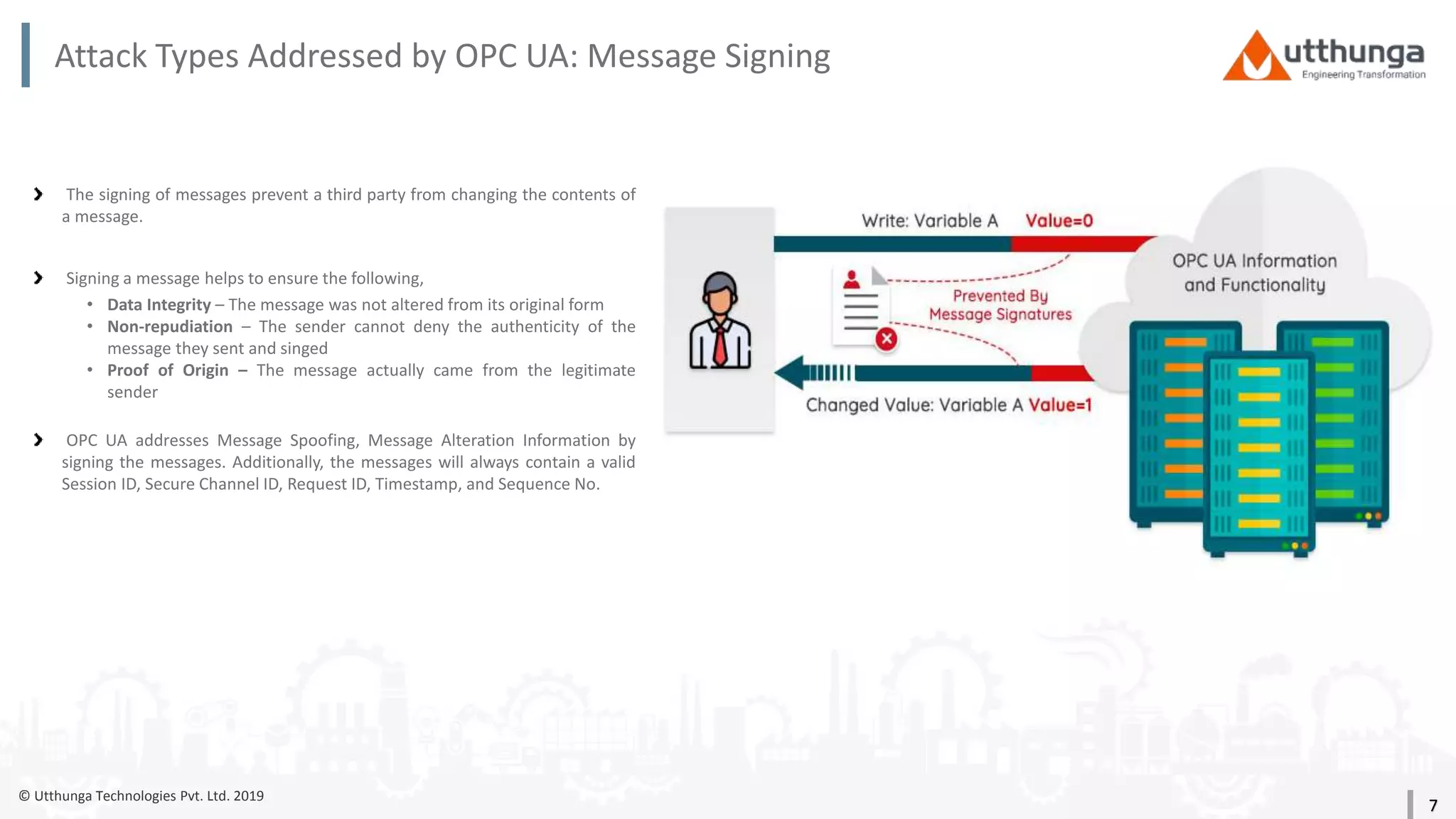
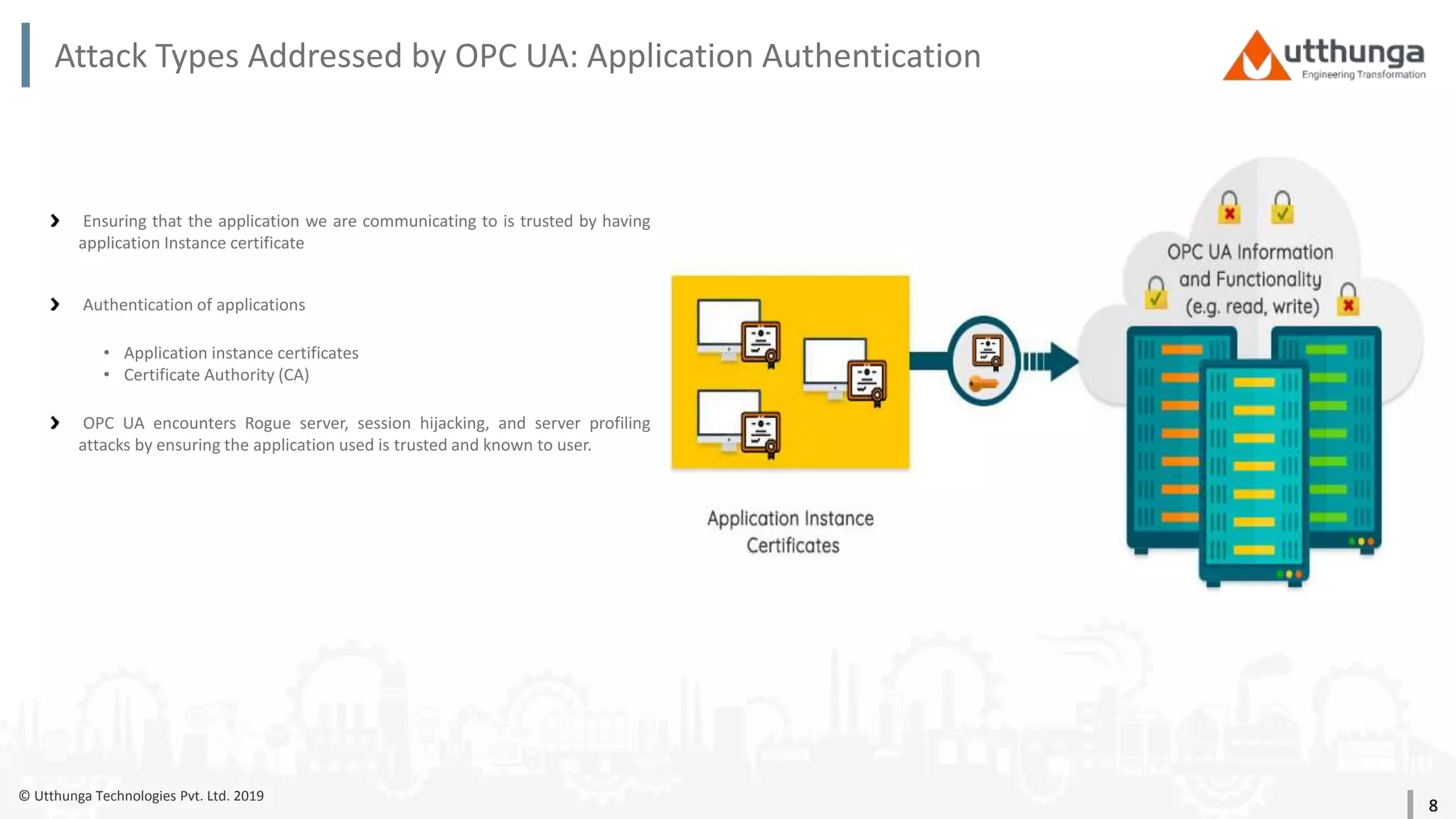
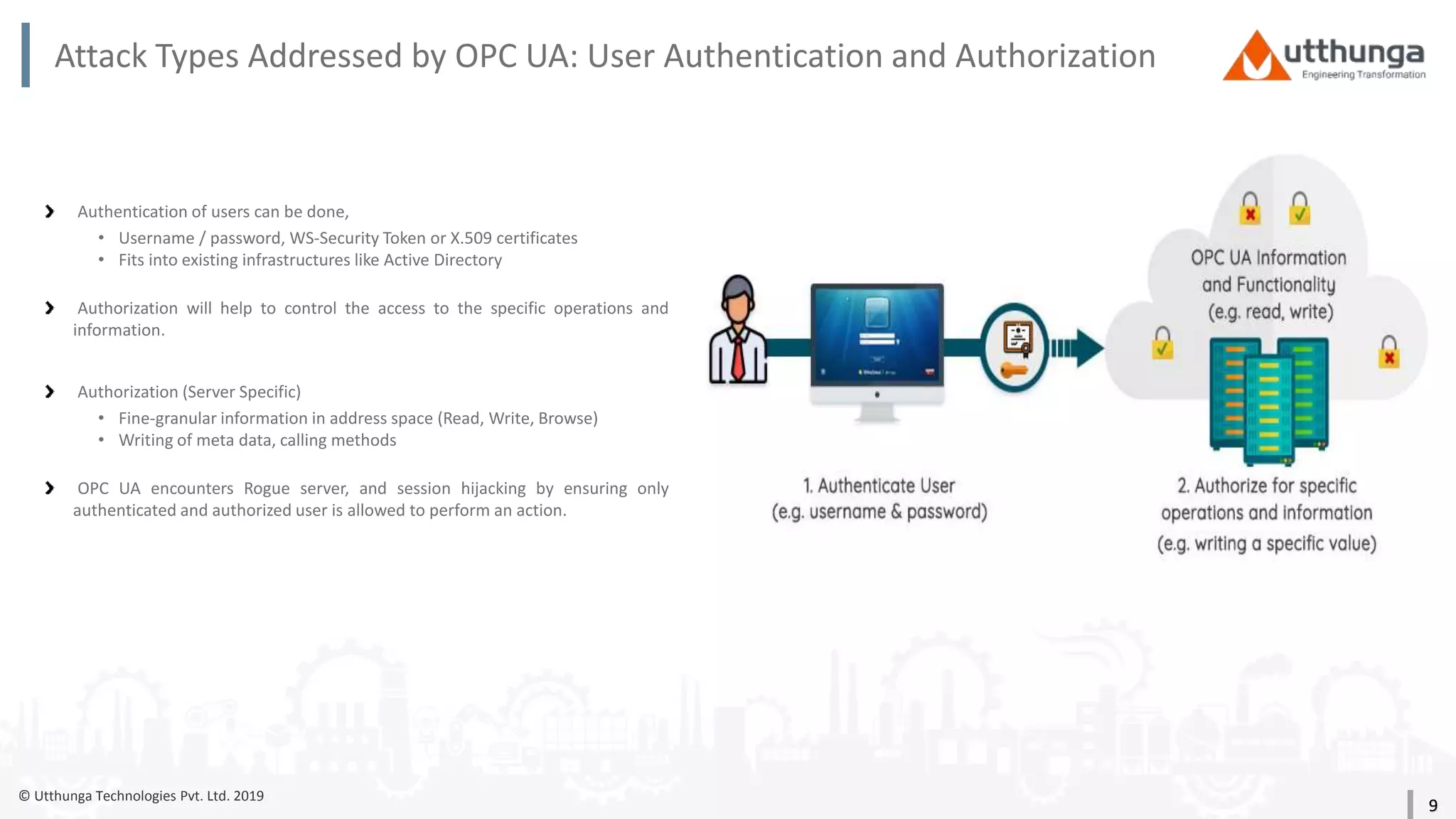
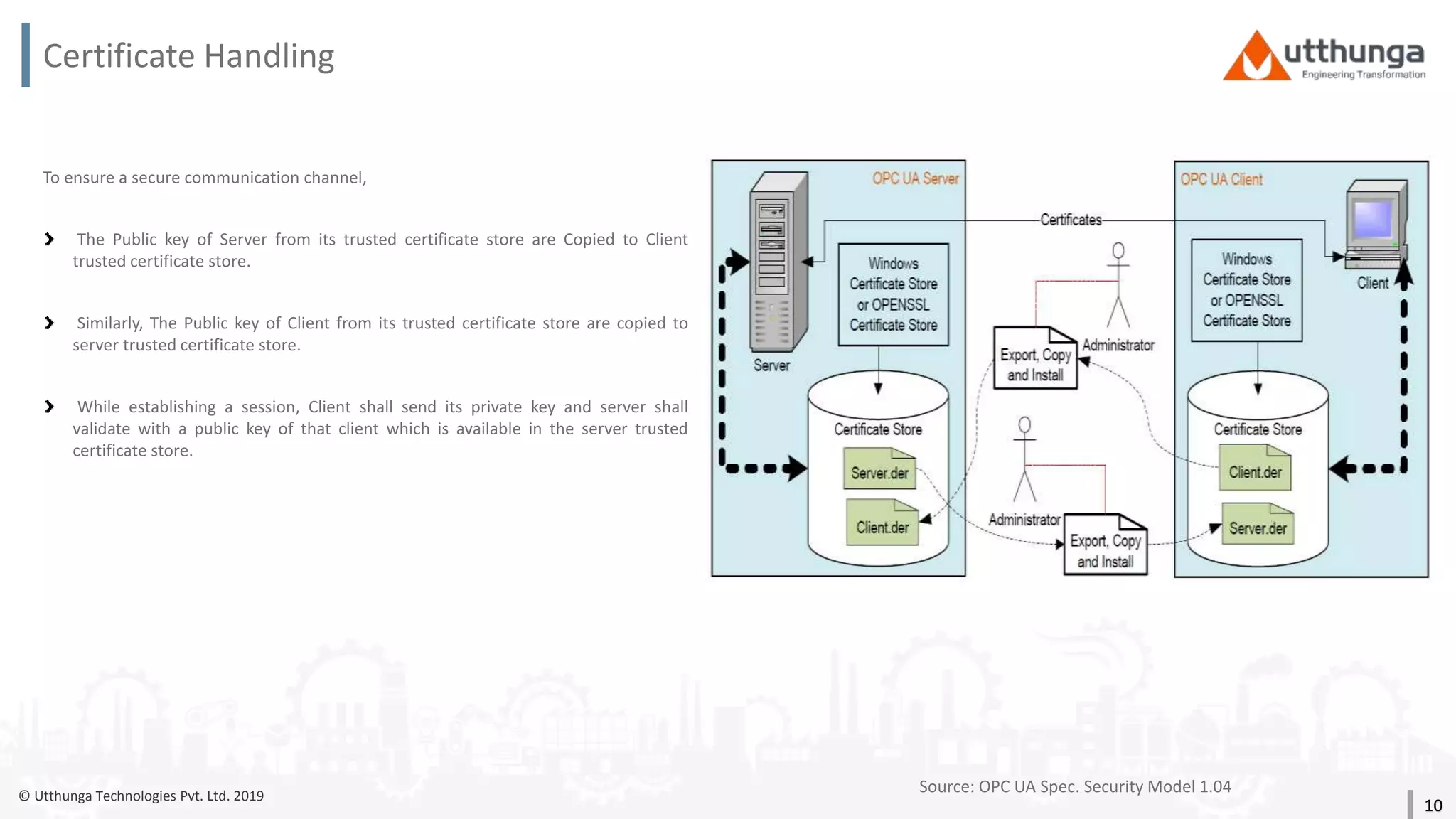
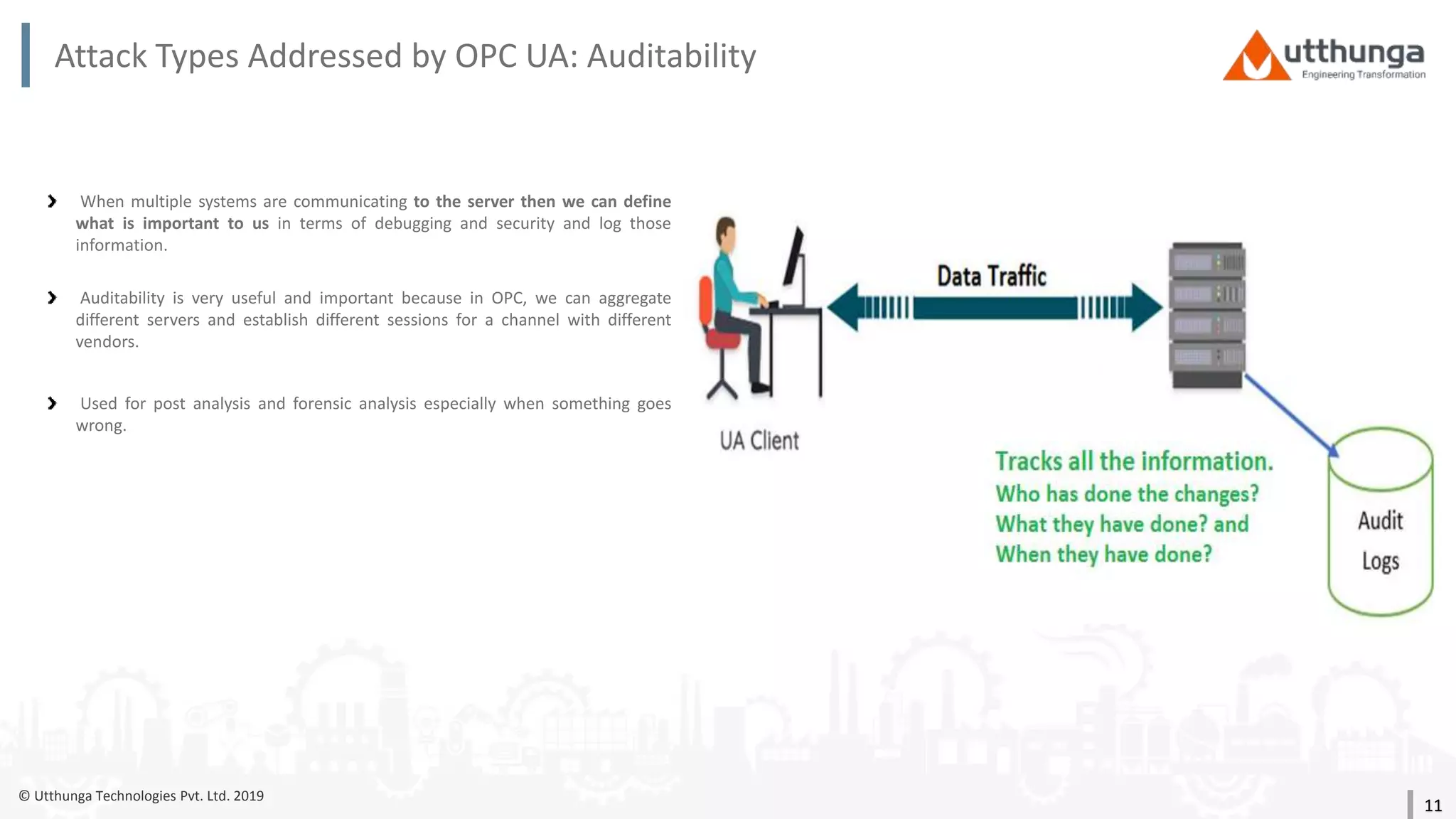
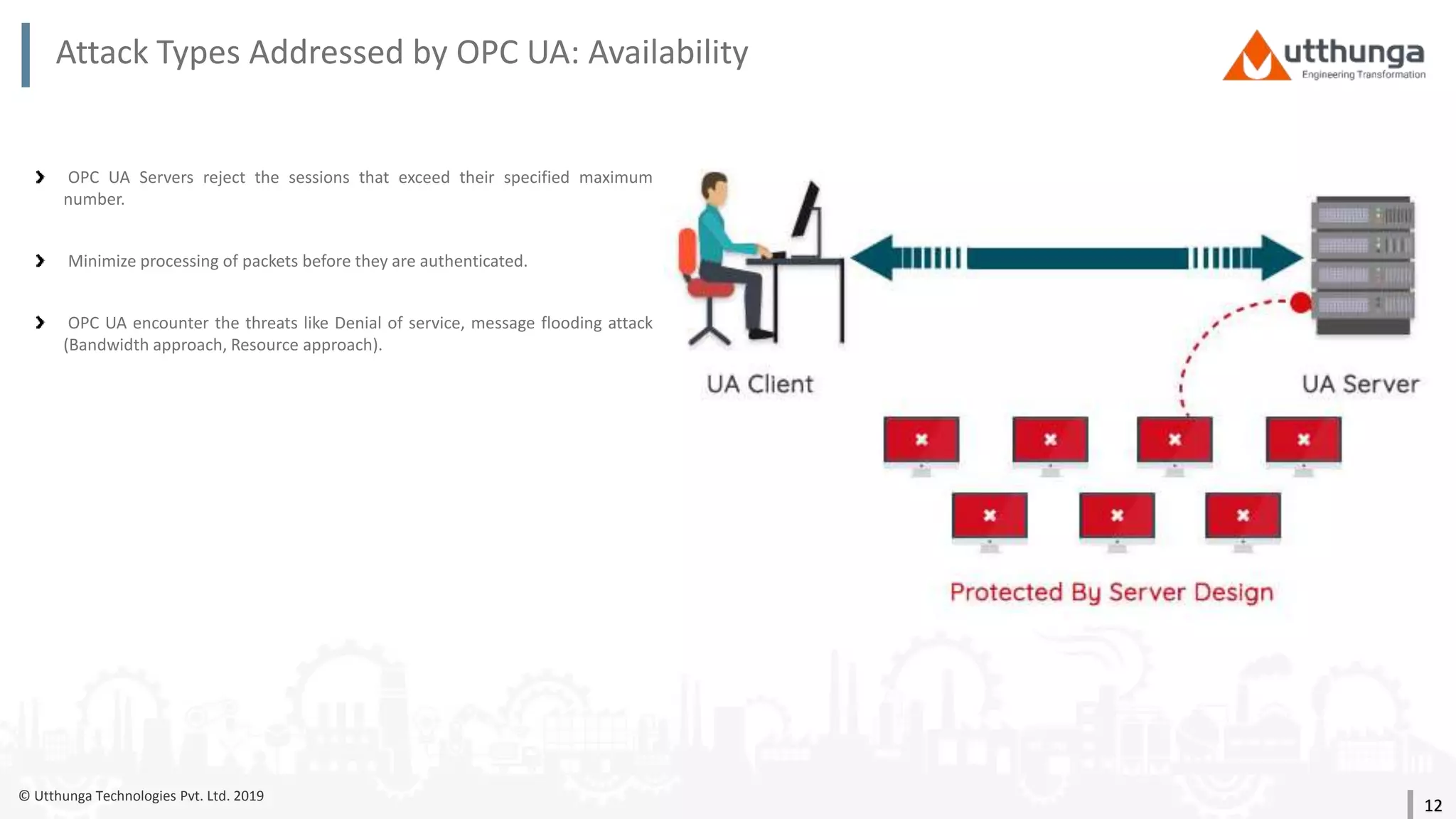
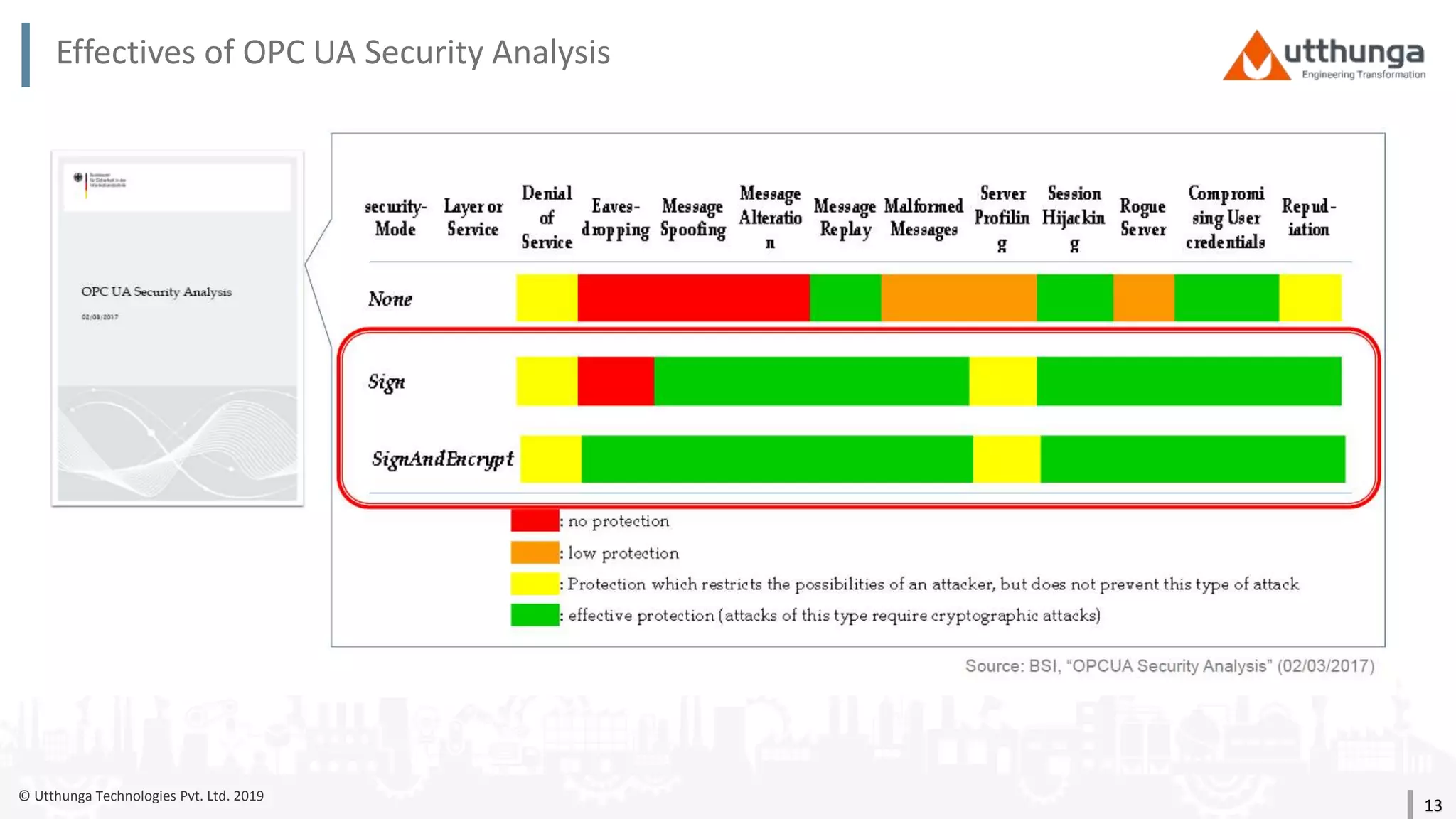
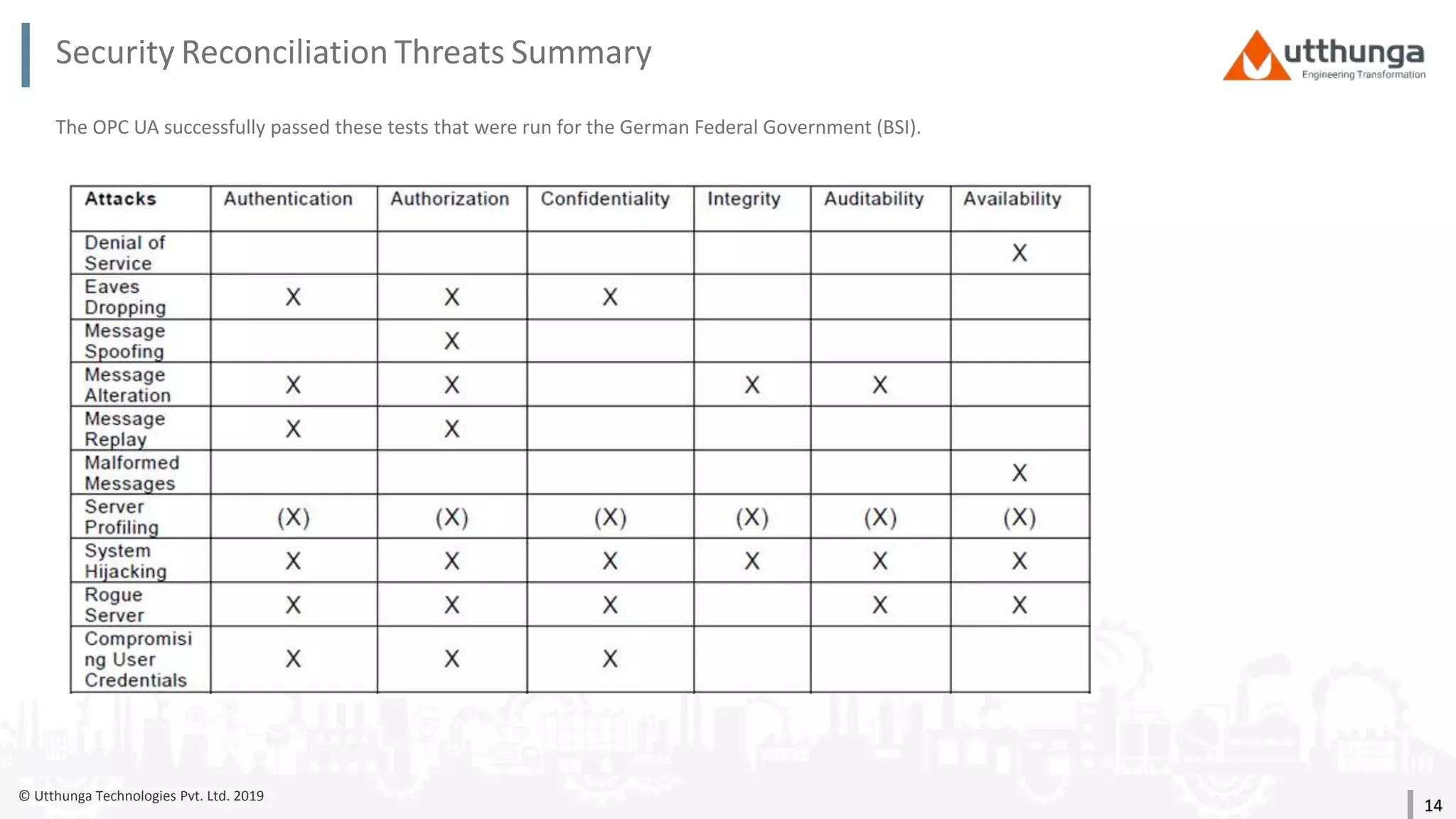
The document provides an overview of security mechanisms in OPC UA, including its security architecture, objectives such as authentication and confidentiality, and attack types addressed like message signing and user authentication. It emphasizes the importance of using specific security policies and recommendations for secure configurations, such as avoiding unencrypted storage of private keys. Furthermore, it highlights that while OPC UA is designed to be secure, additional precautions are necessary for effective system protection.