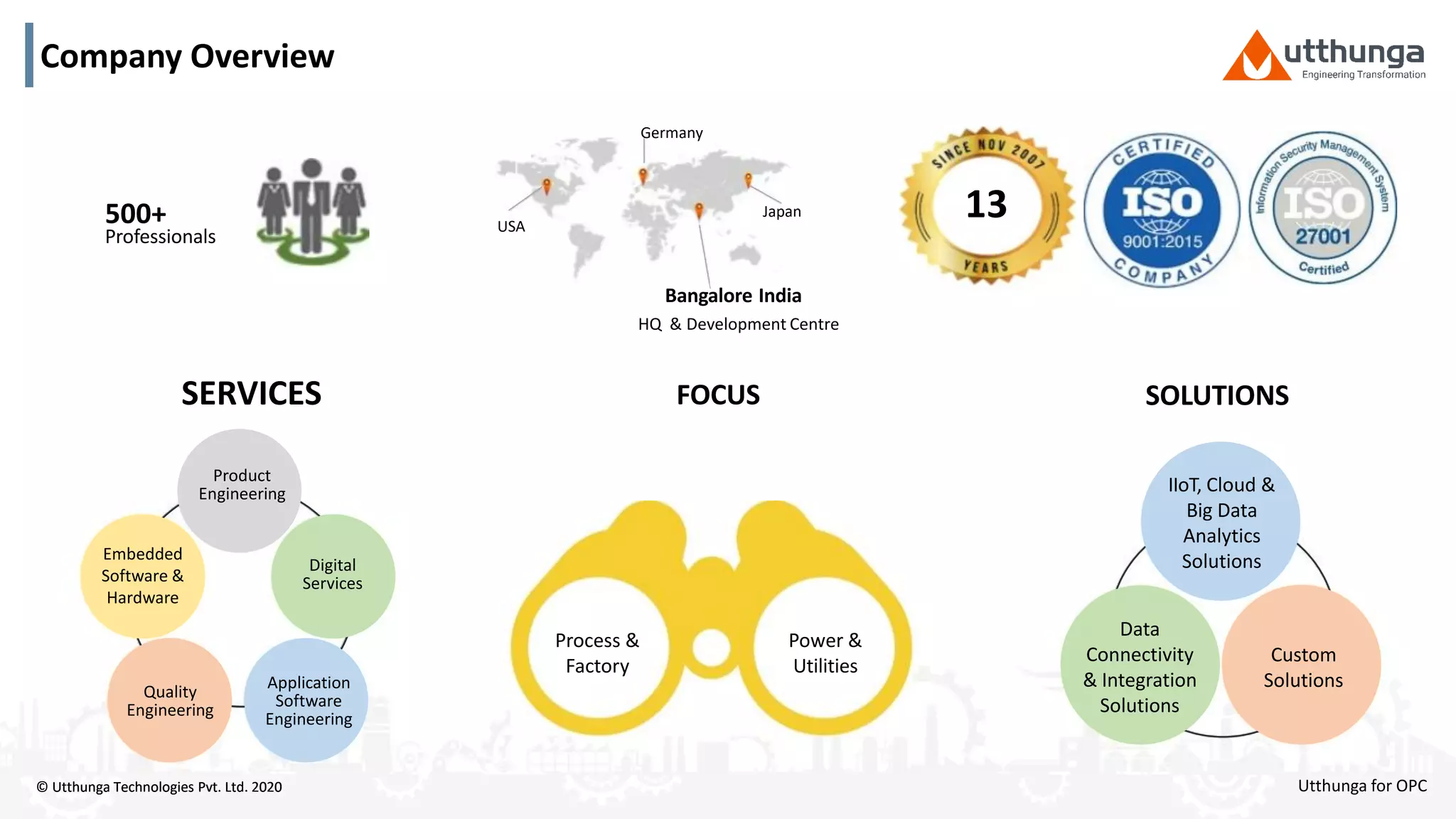
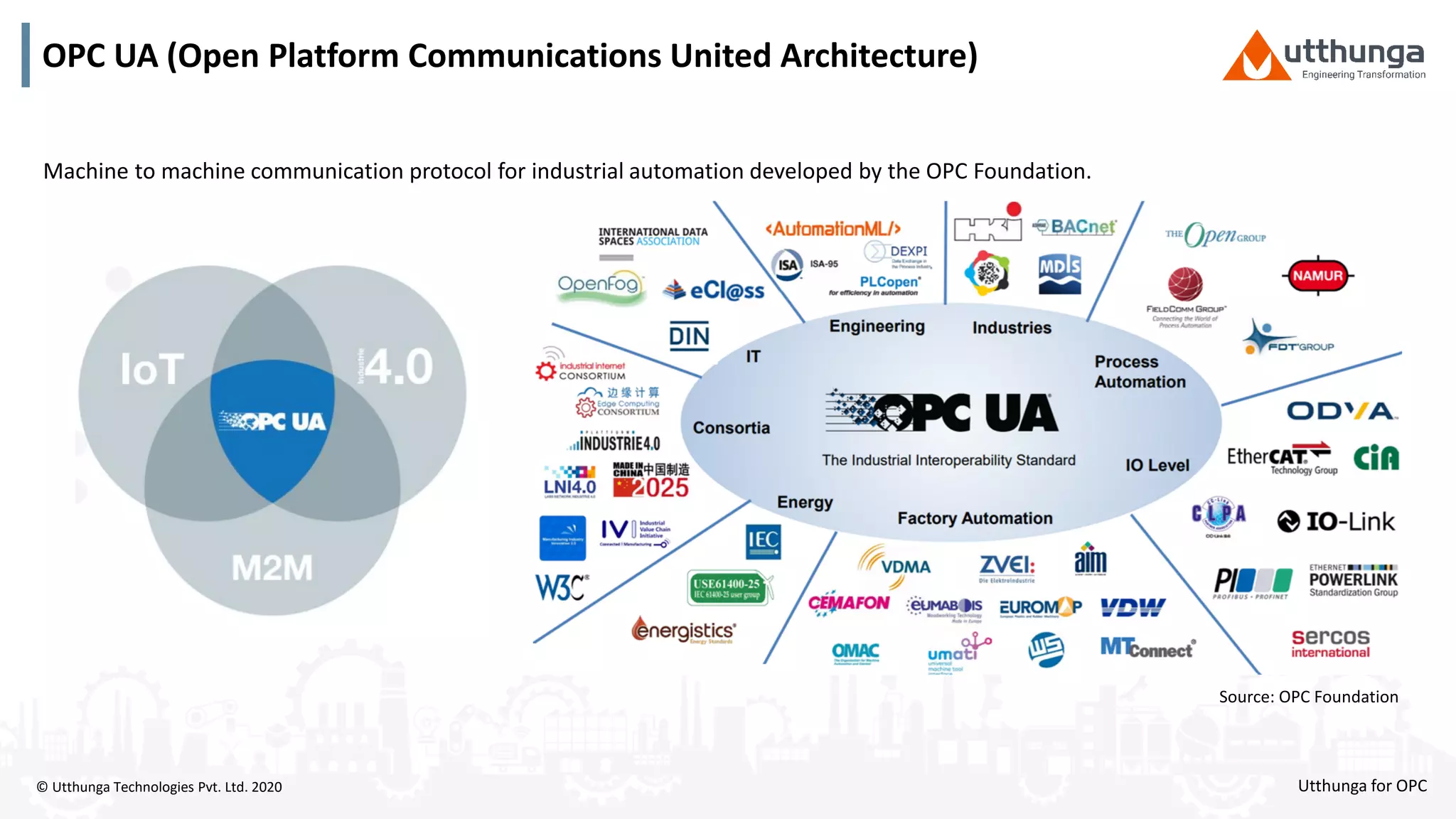
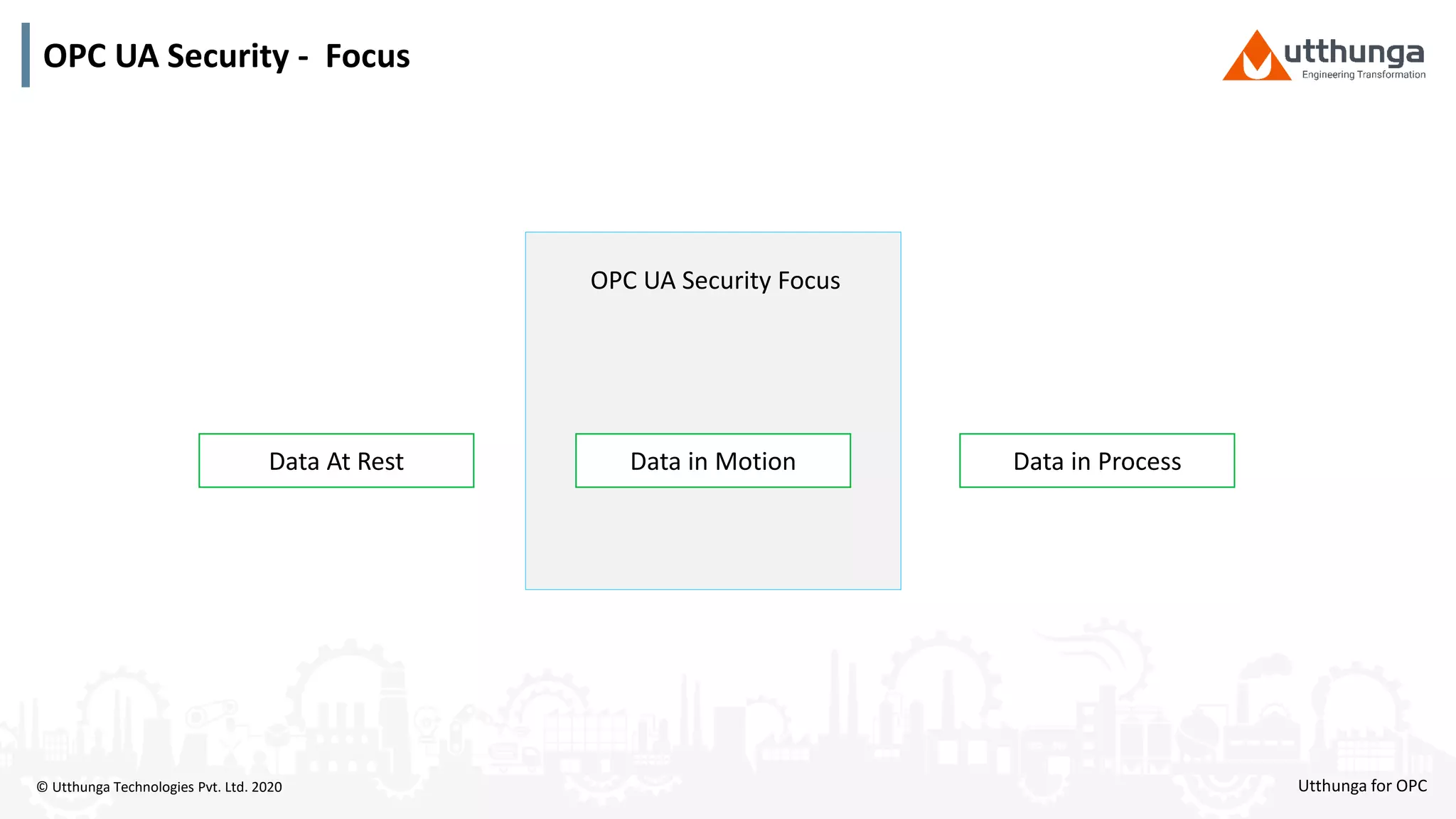
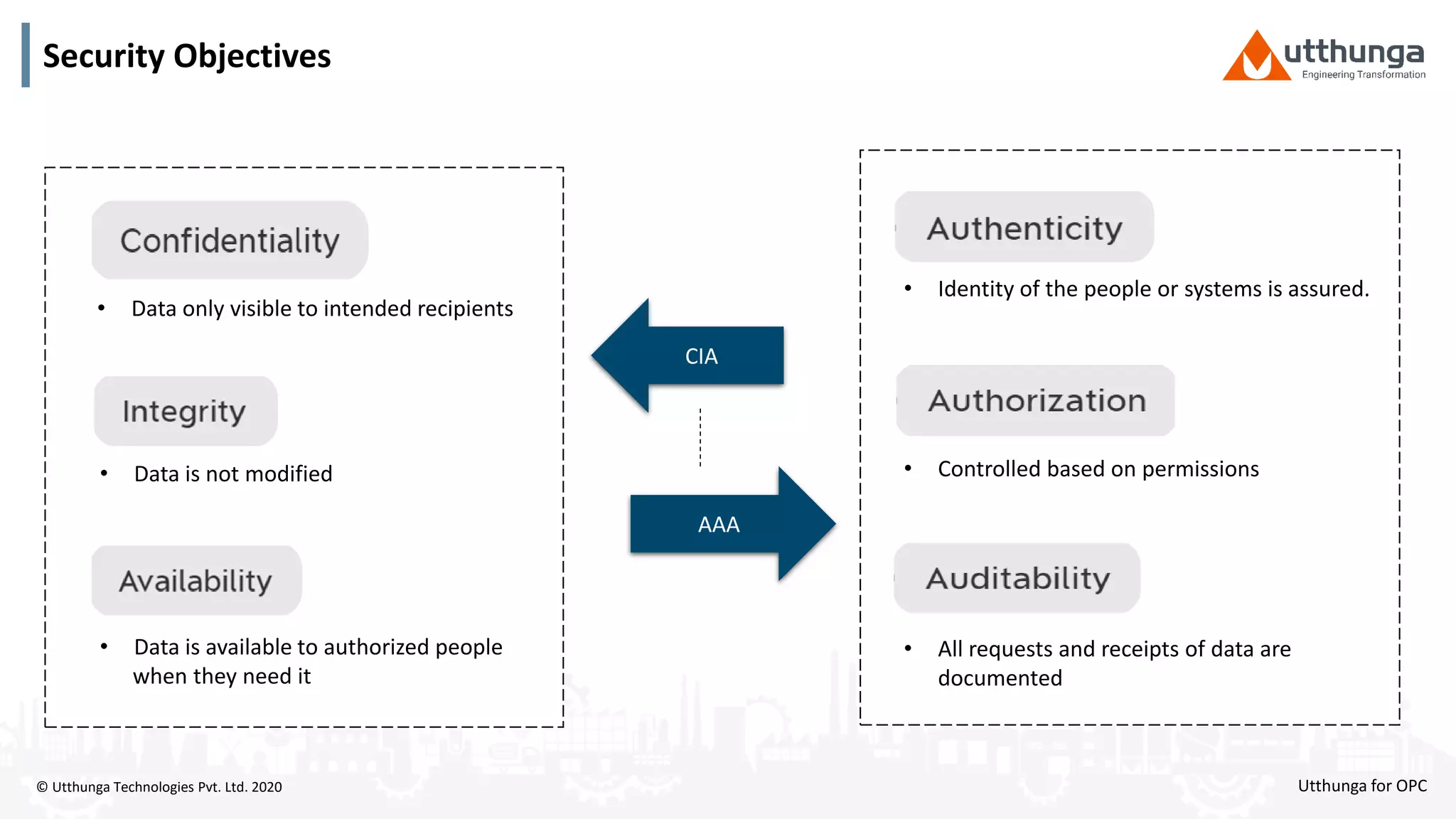
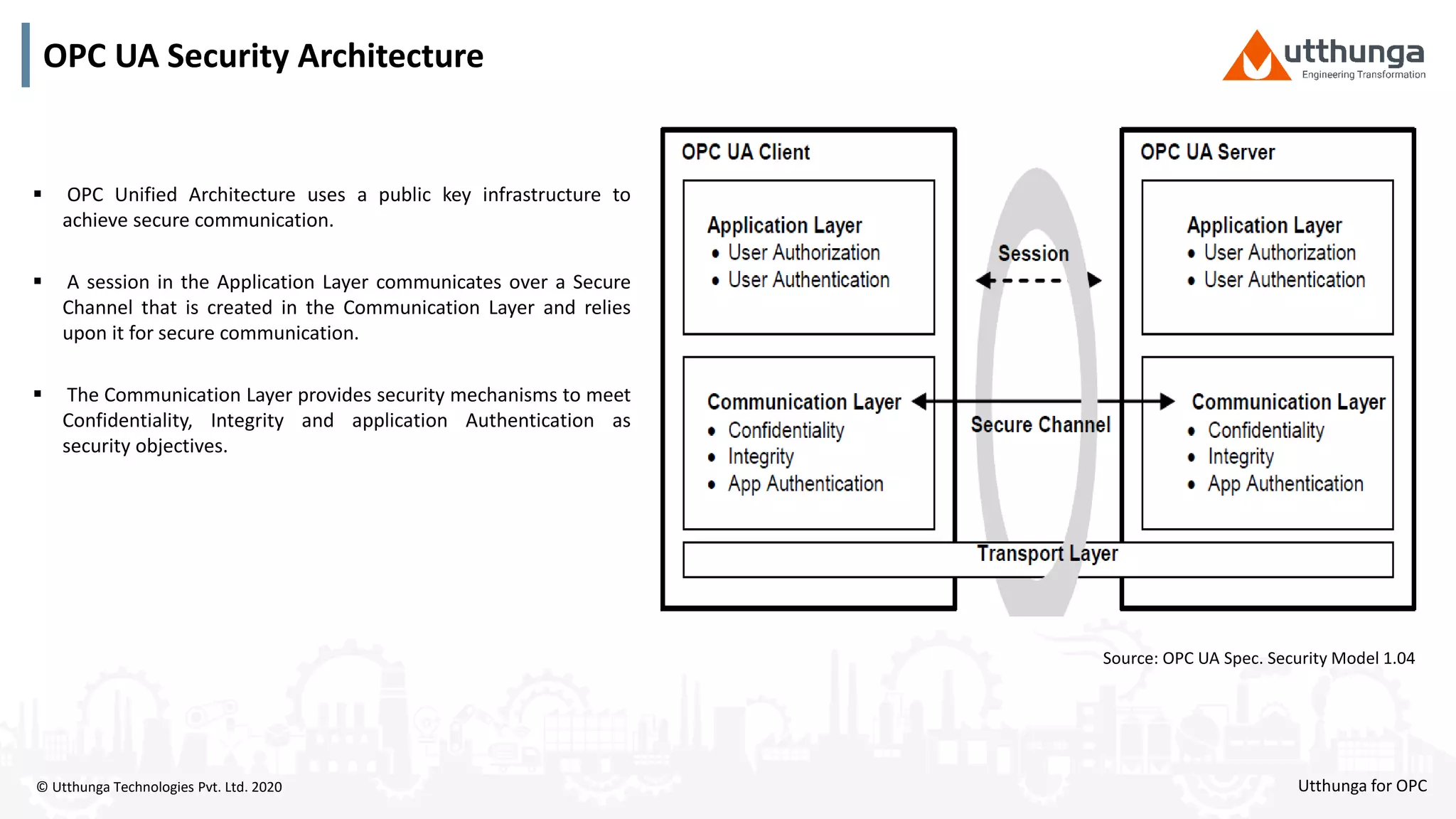
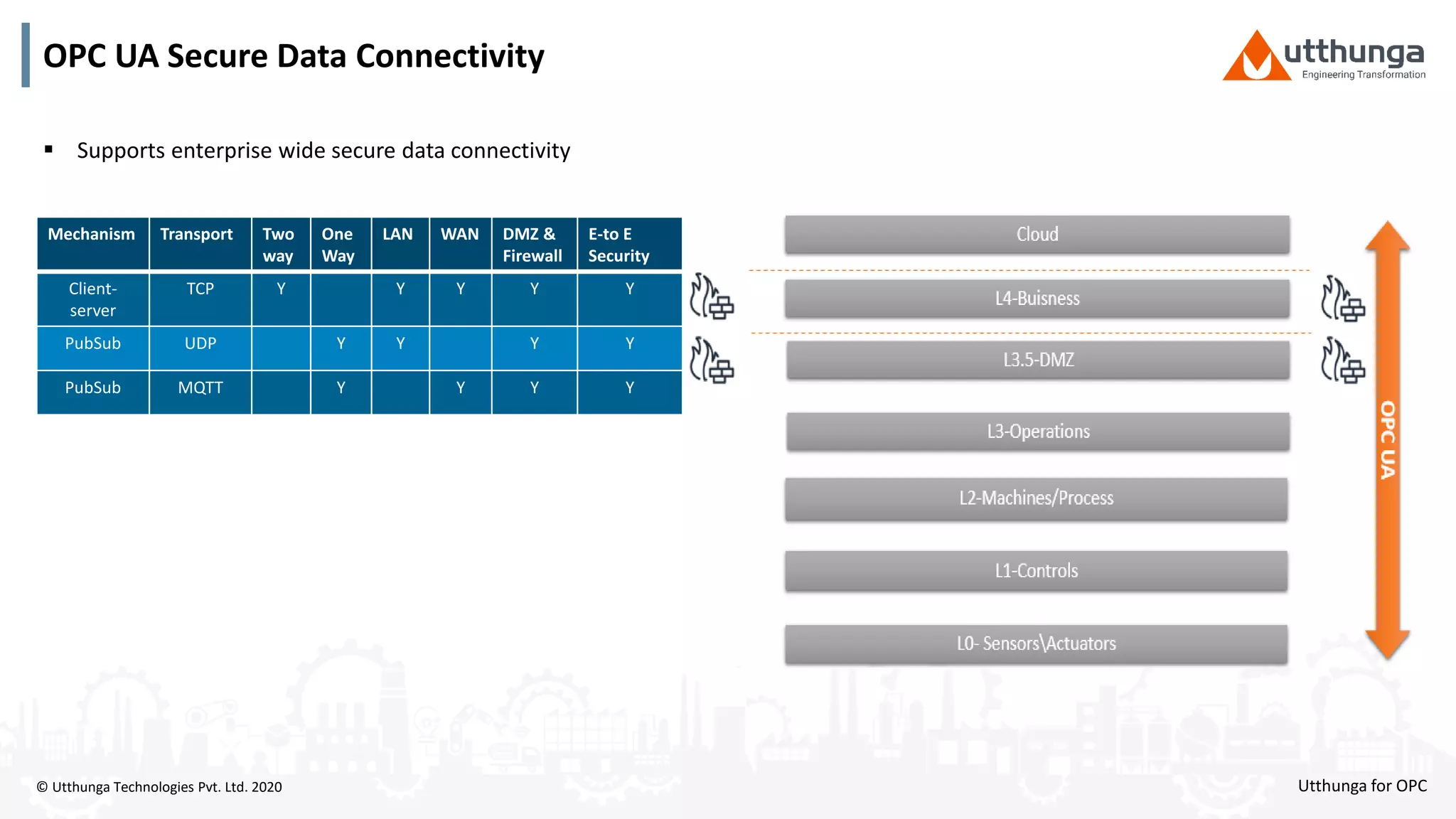
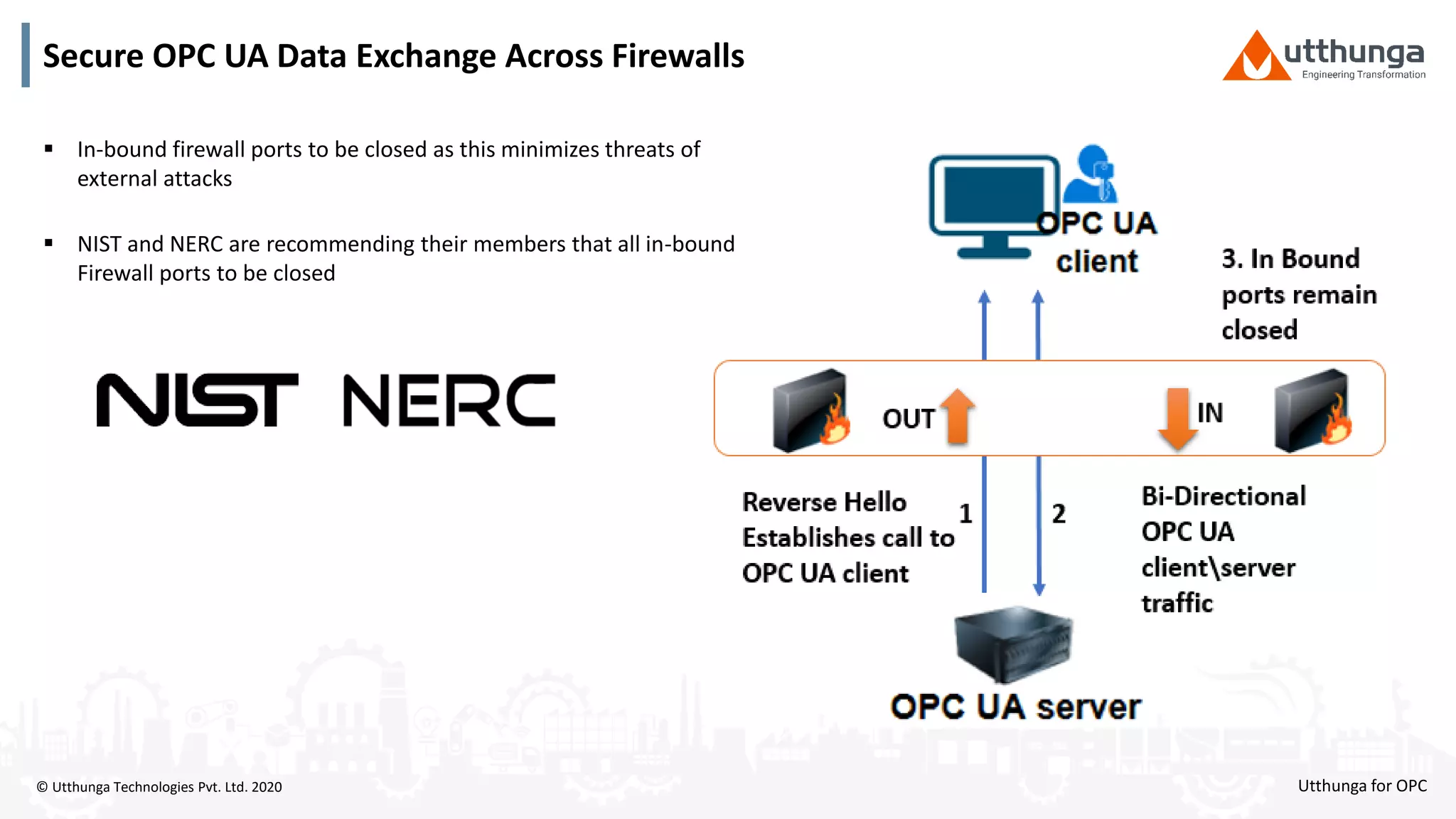
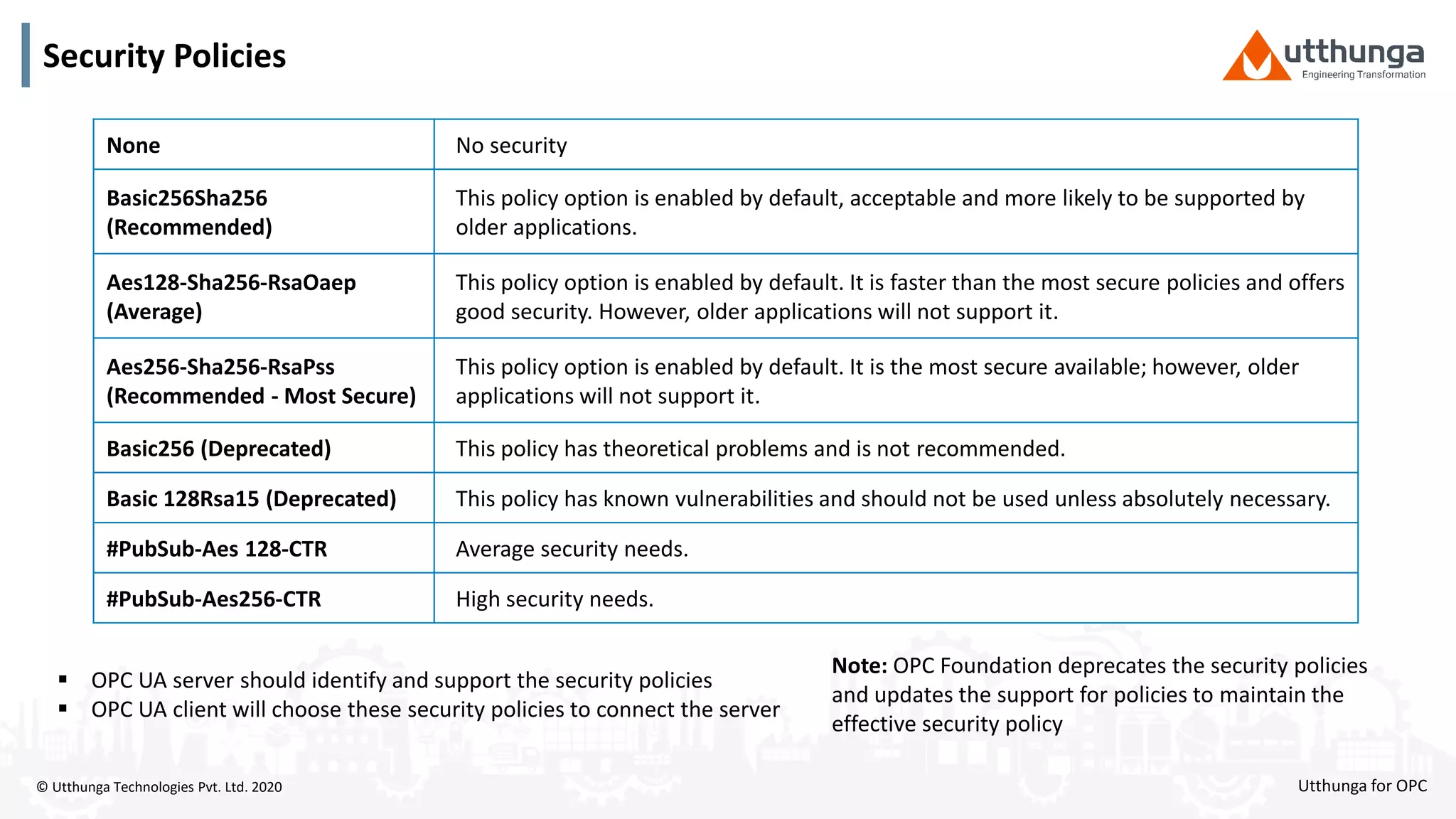
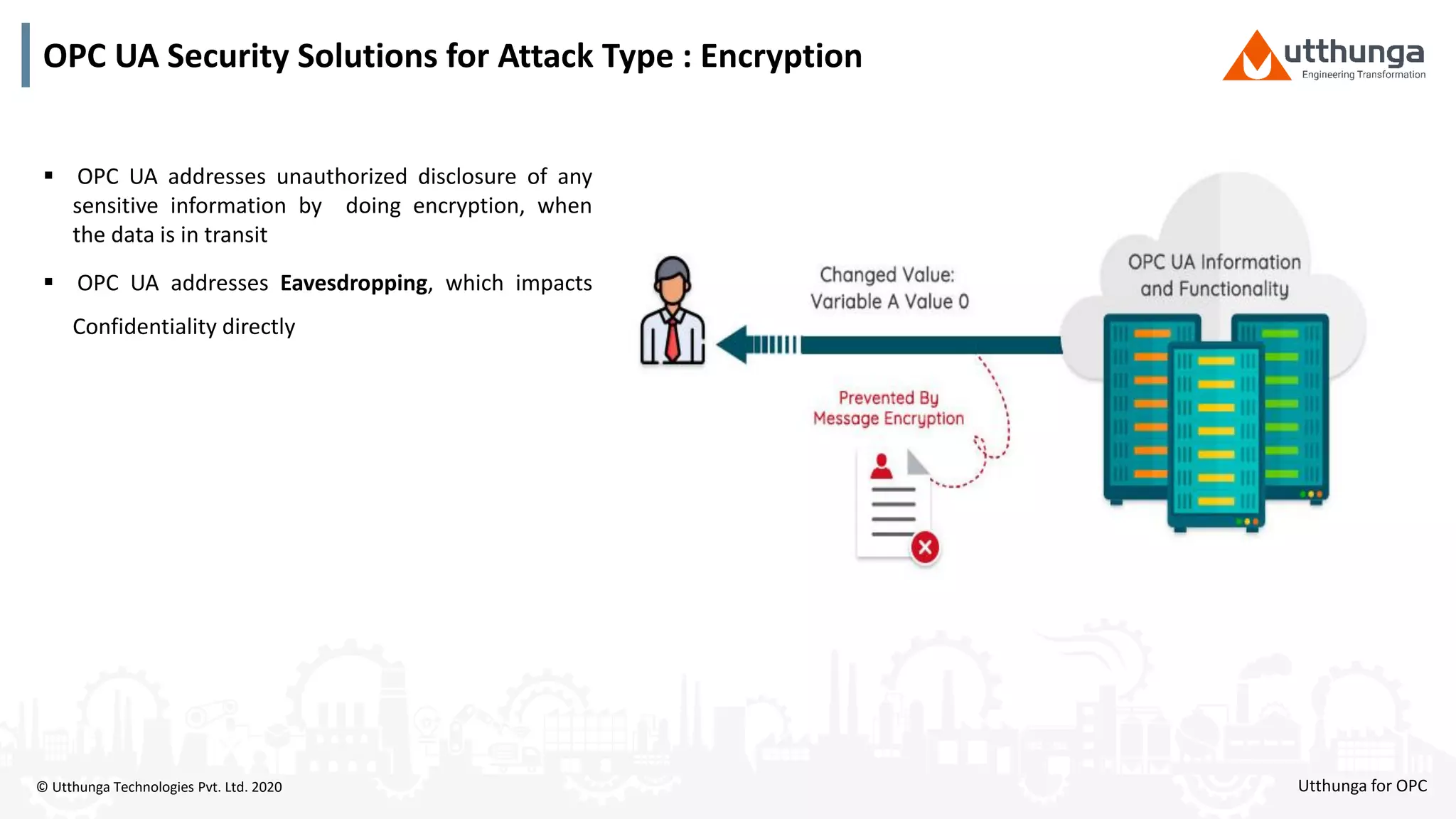
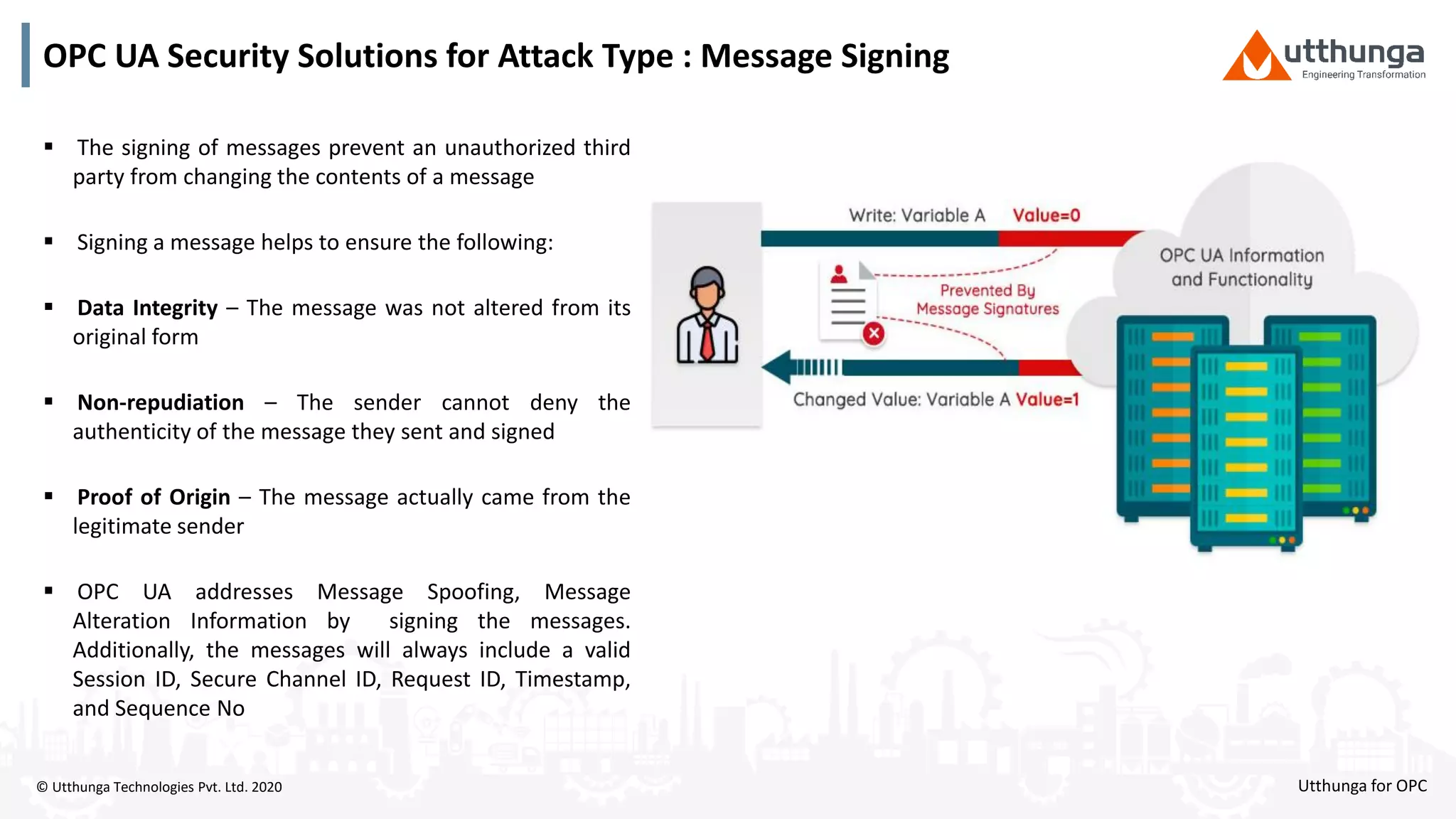
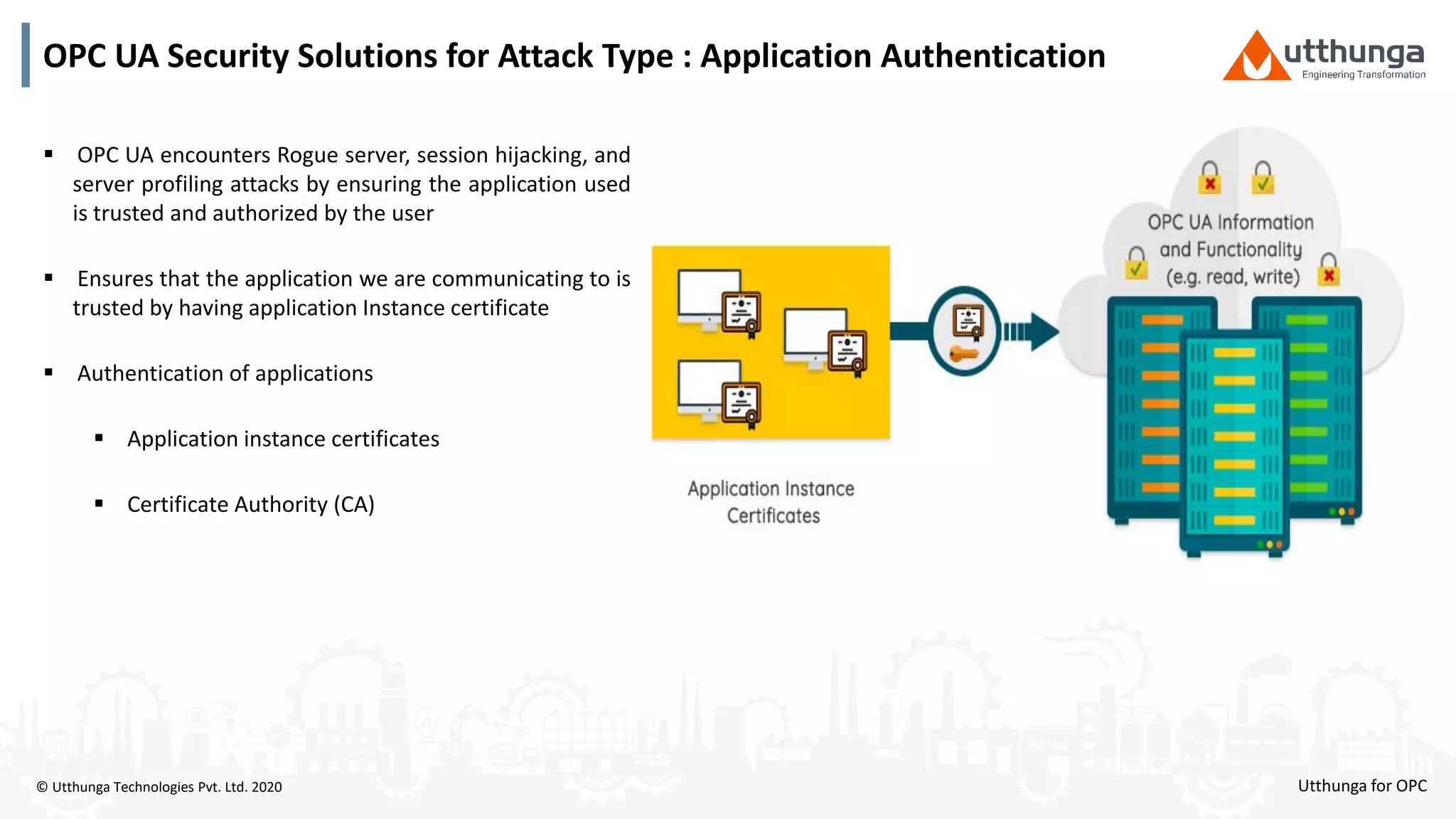
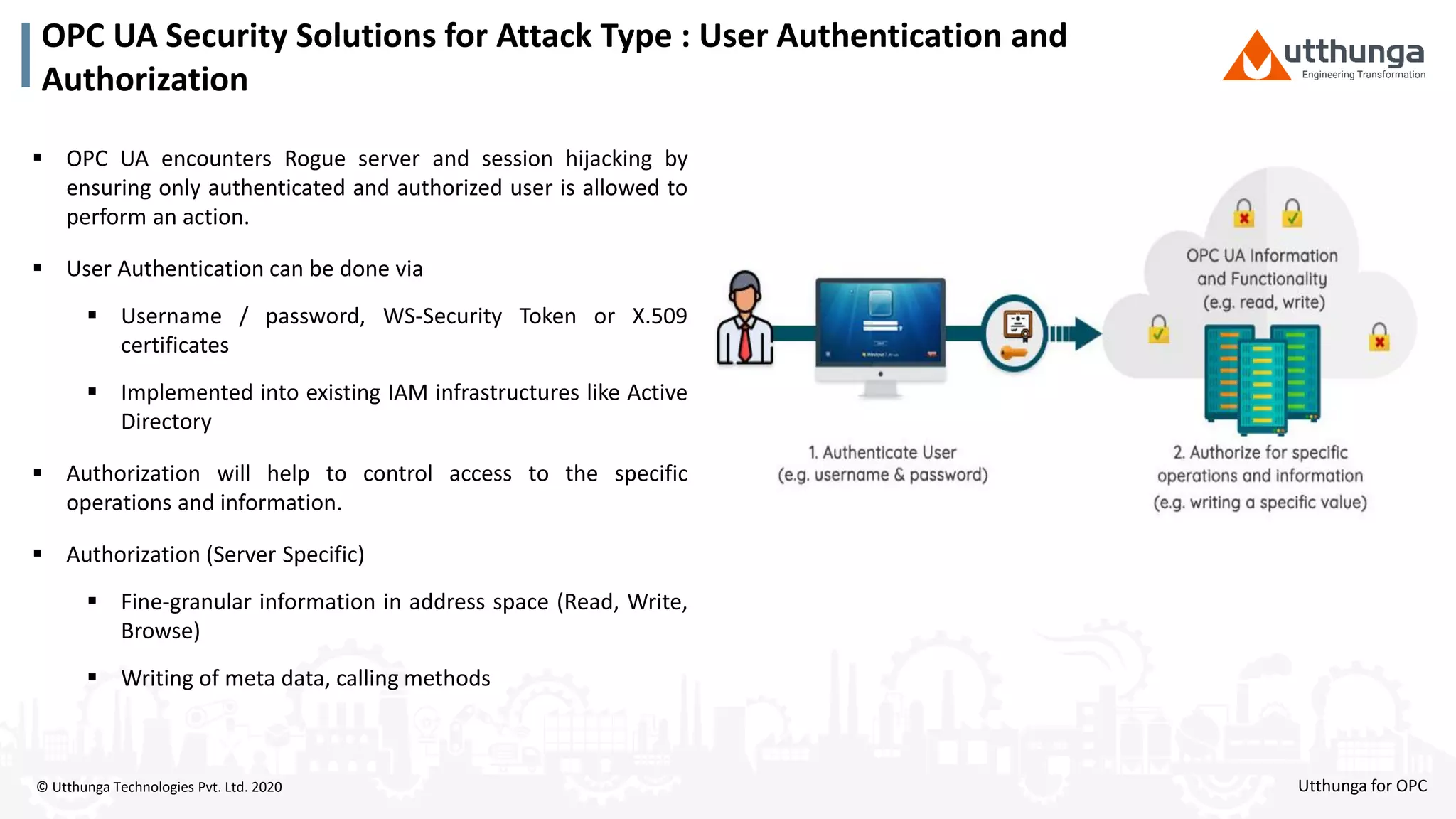
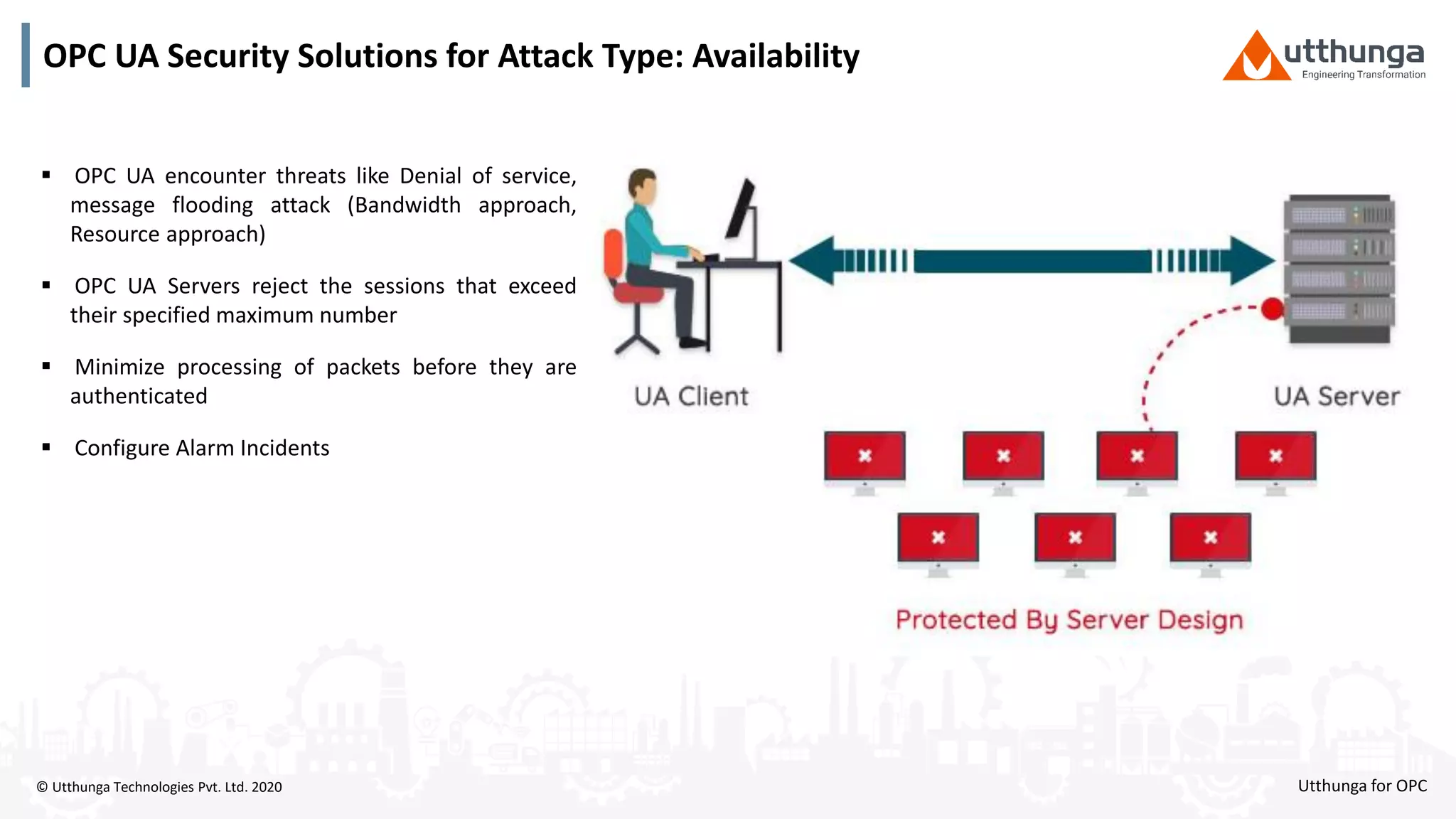
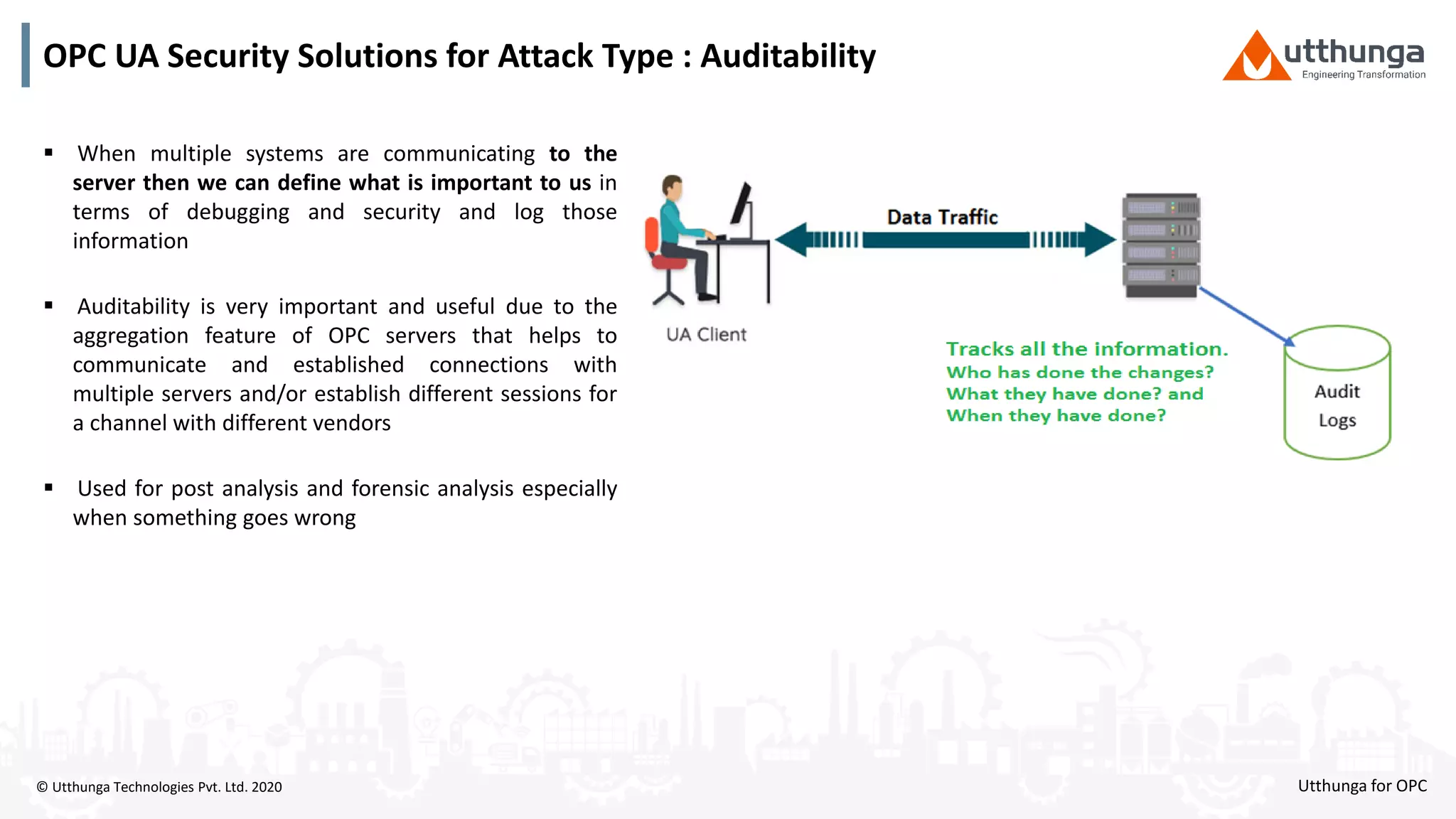
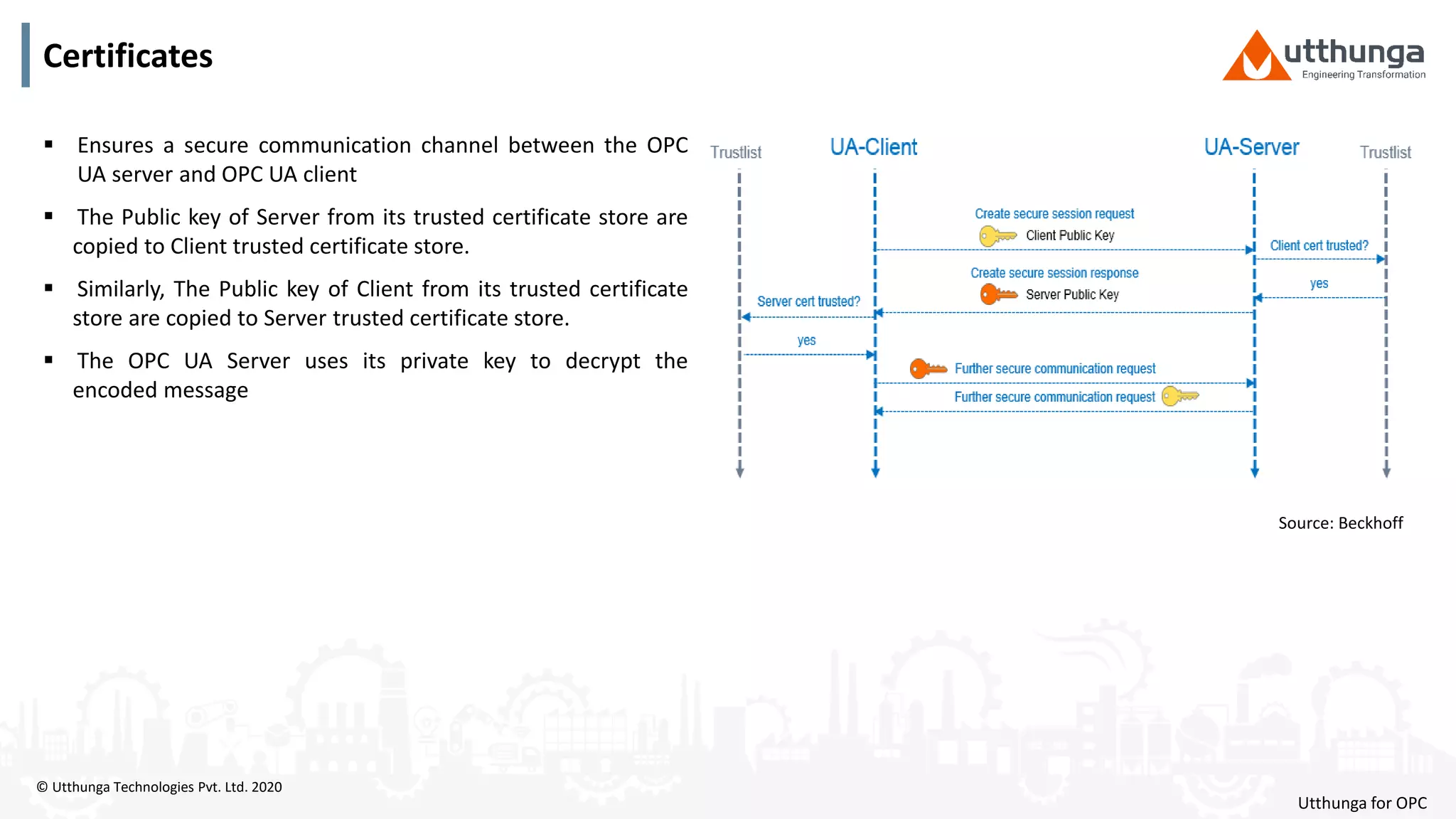
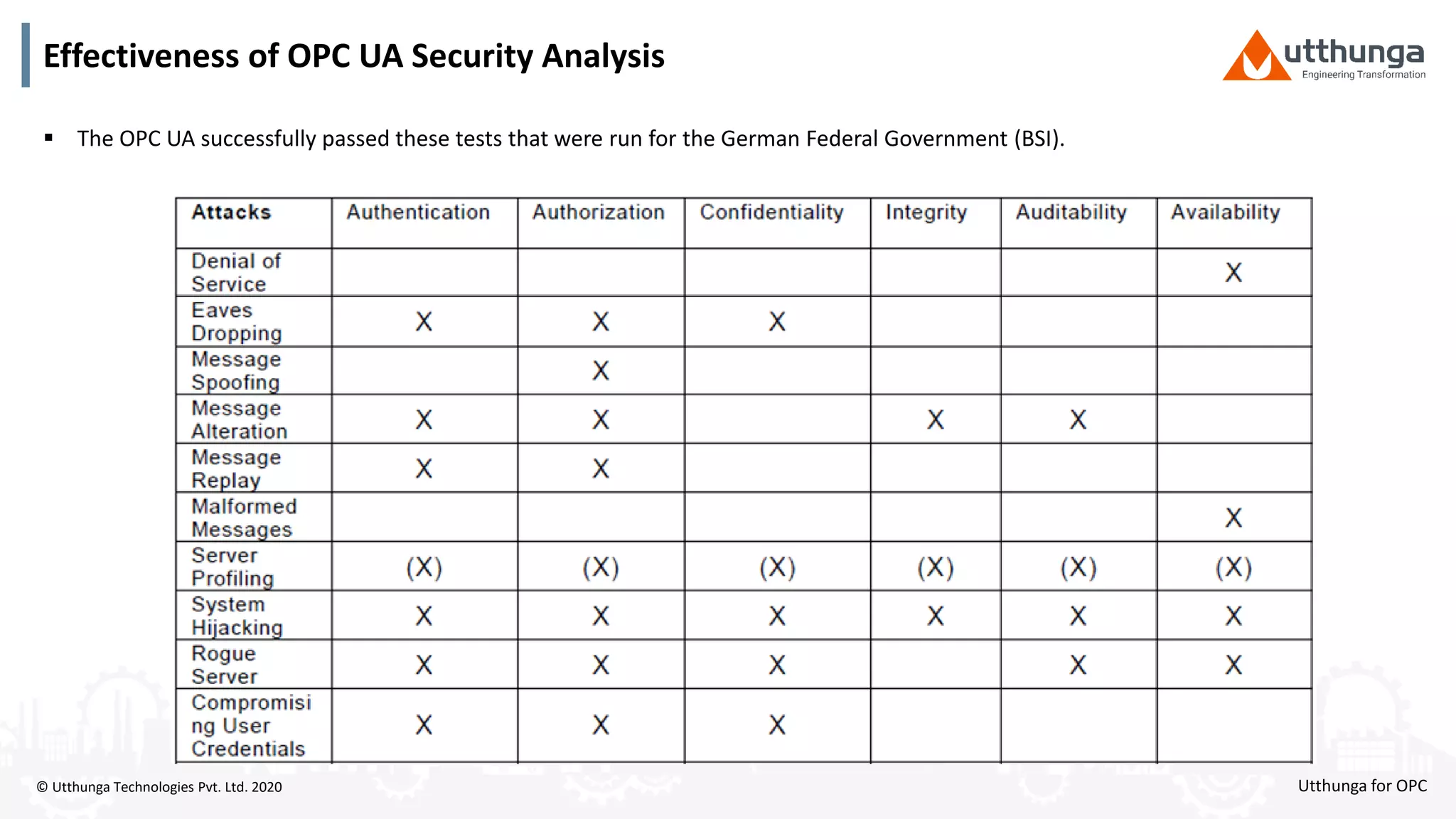
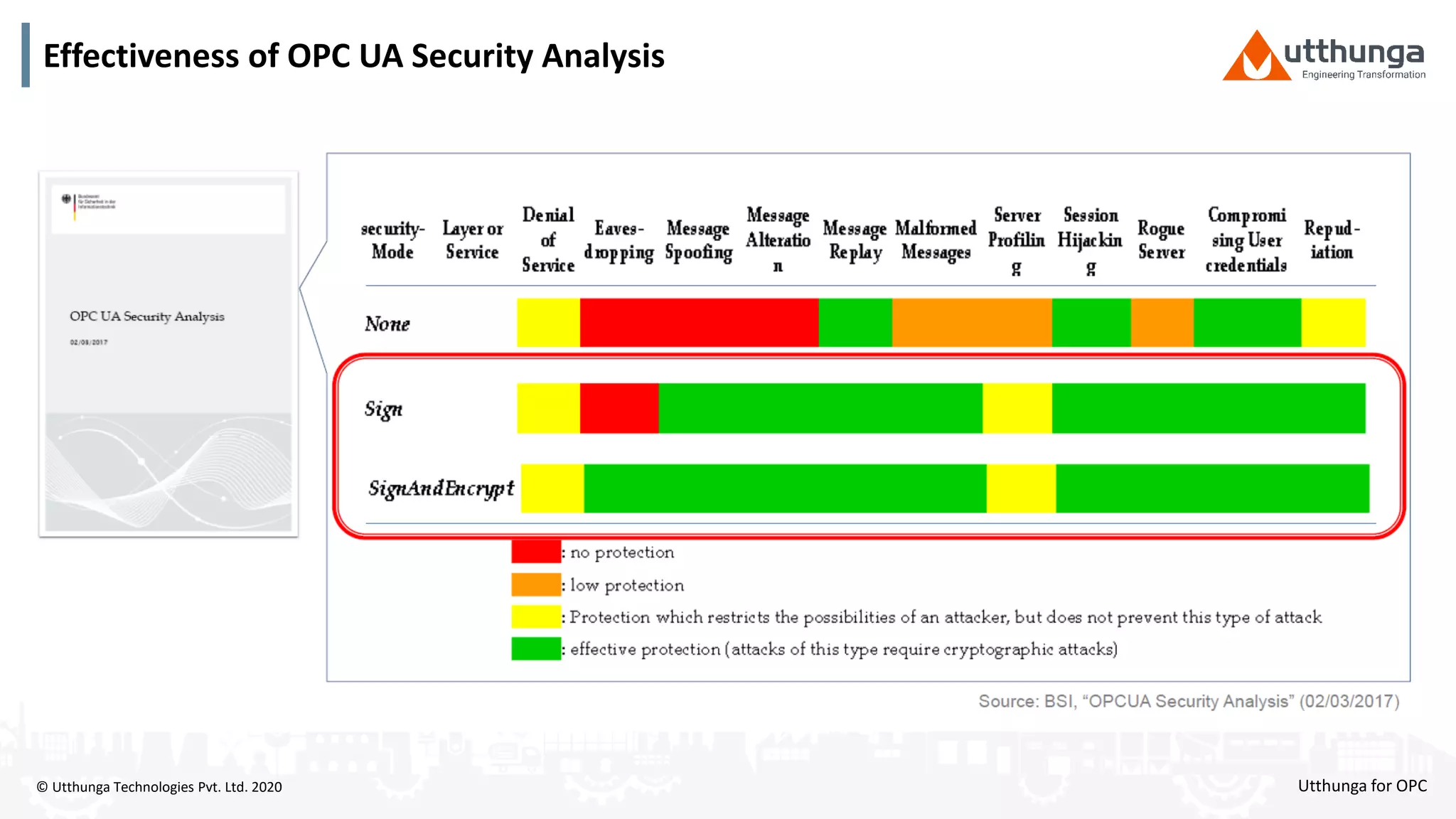
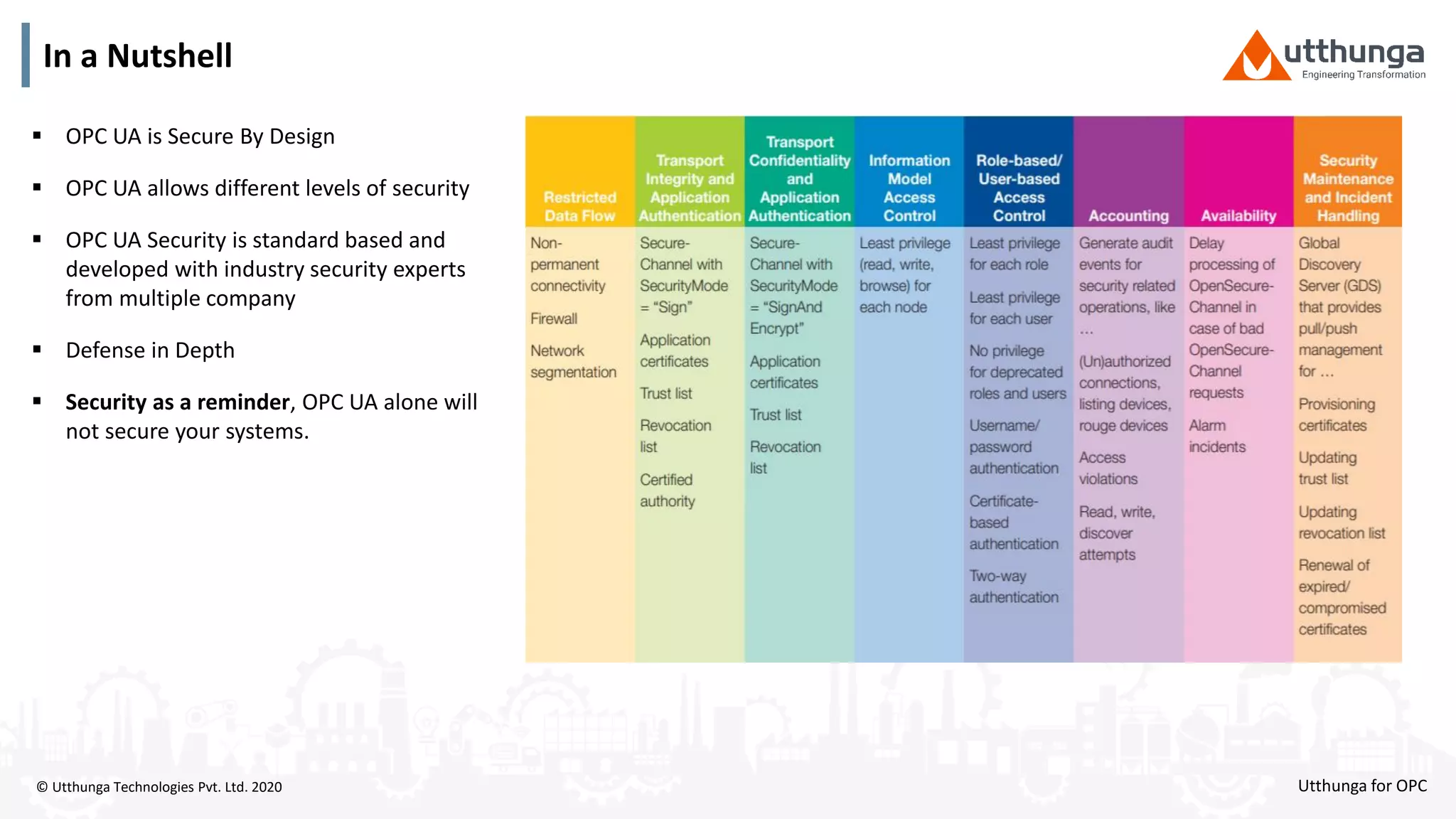
The document provides an overview of OPC UA security, detailing its architecture, security objectives, and various security policies and solutions to protect data integrity and confidentiality. It highlights the role of Utthunga Technologies in securing industrial communication and emphasizes the importance of proper user authentication, encryption, and security governance. Additionally, it offers recommendations for optimizing security practices in both OEMs and end-users while promoting a proactive approach to managing security vulnerabilities.