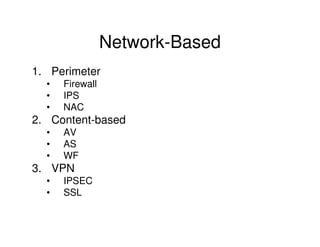
This document discusses how to secure various IT assets including those located in main and DR data centers, internal and outsourced workstations, and data in transit. It describes network-based security methods like firewalls, IPS, and NAC. It also covers host-based security of operating systems, applications, and data on servers and workstations. The document advocates for encryption, log management, vulnerability management, and WAN optimization to enhance security and performance.