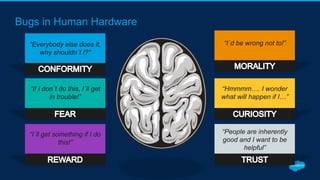
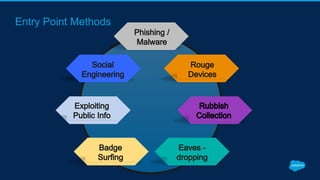
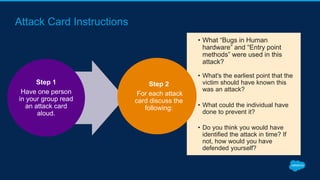
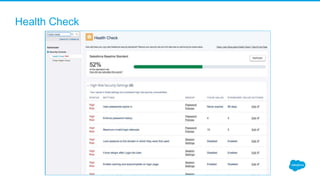
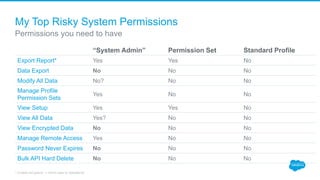
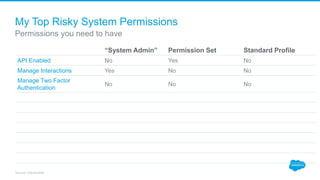
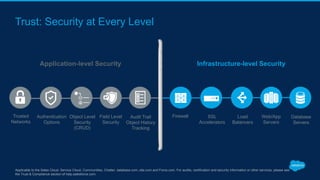
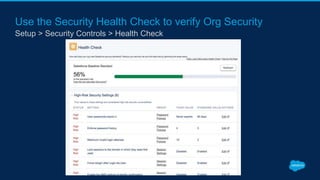
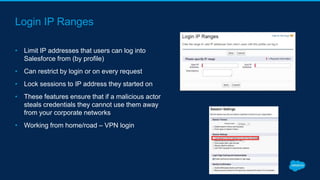
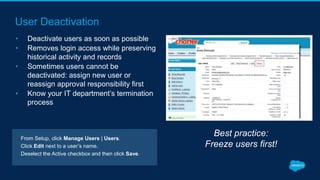
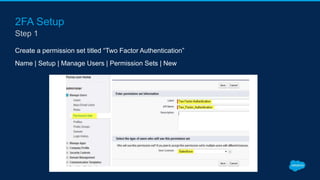
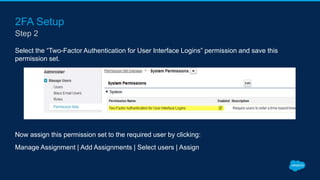
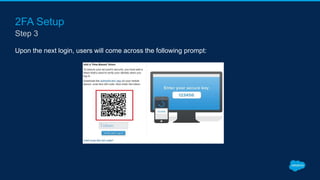
Securing Your Salesforce Org: The Human Factor discusses how the human element is one of the biggest security risks for organizations. It provides guidance on educating employees on secure behaviors like password security, phishing awareness, and only granting minimum necessary access. The presentation also recommends enabling two-factor authentication and login IP ranges to add extra security layers and restrict access. It stresses that effective security requires communication across the organization and ongoing training for users.