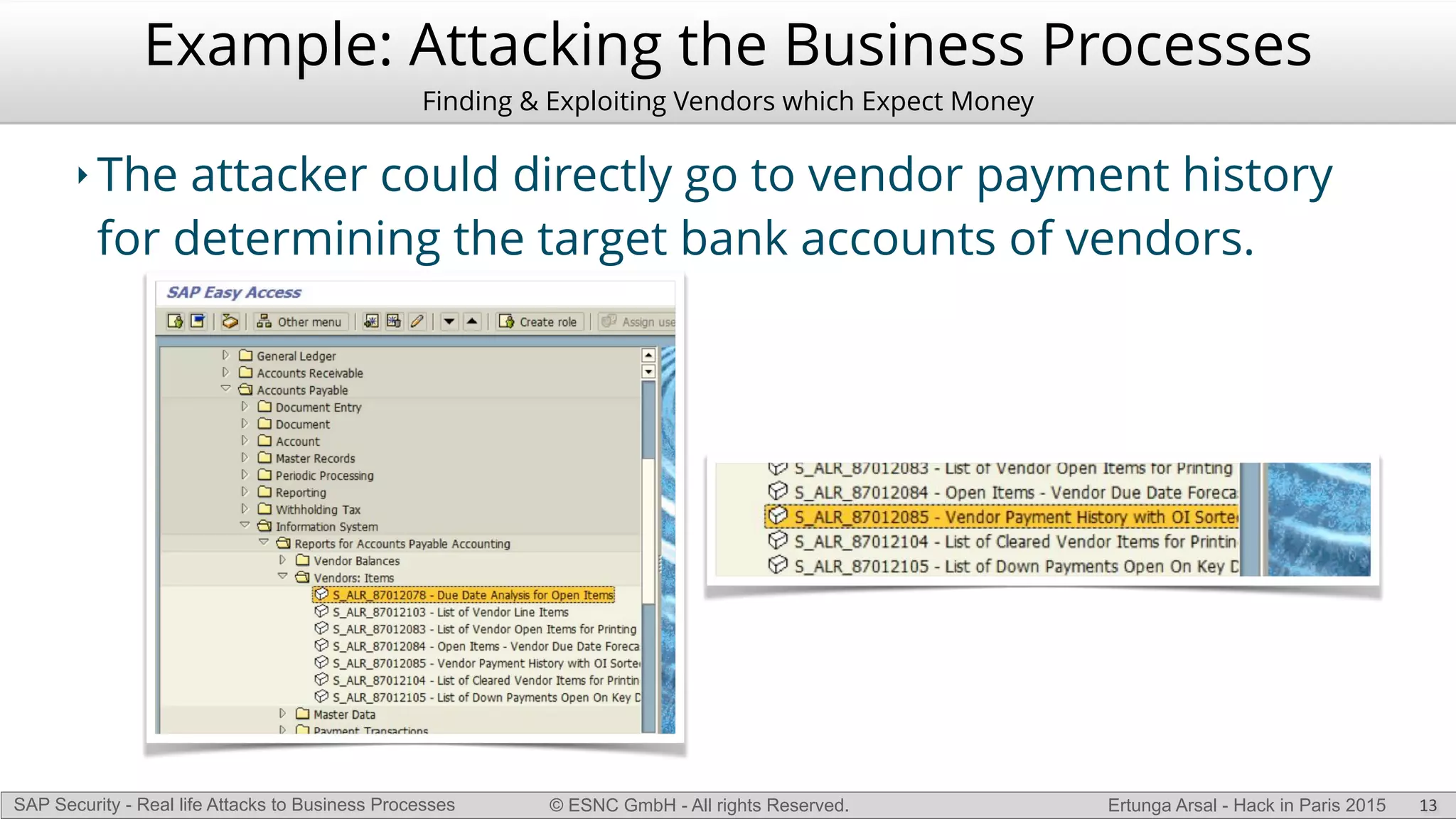
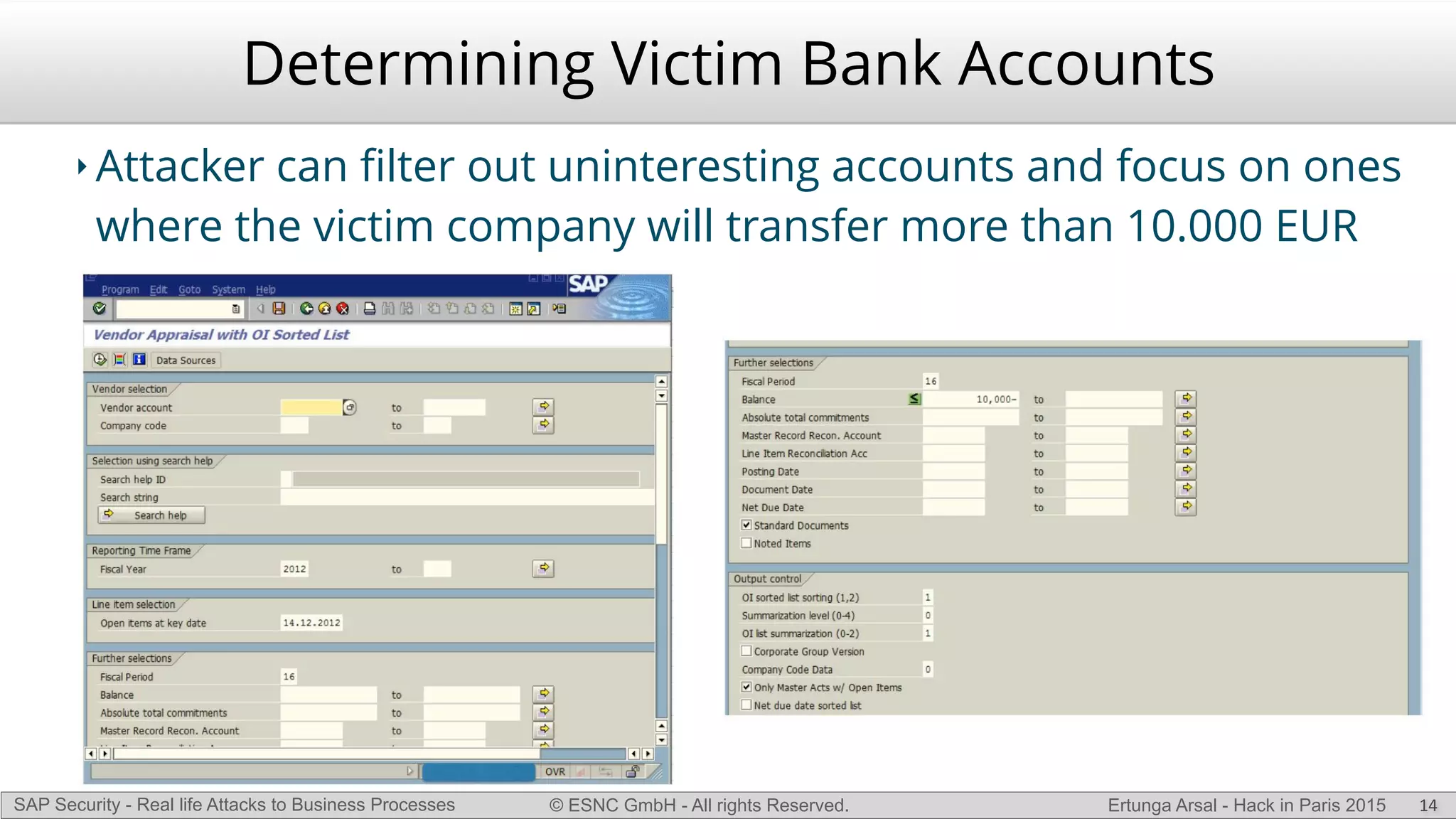
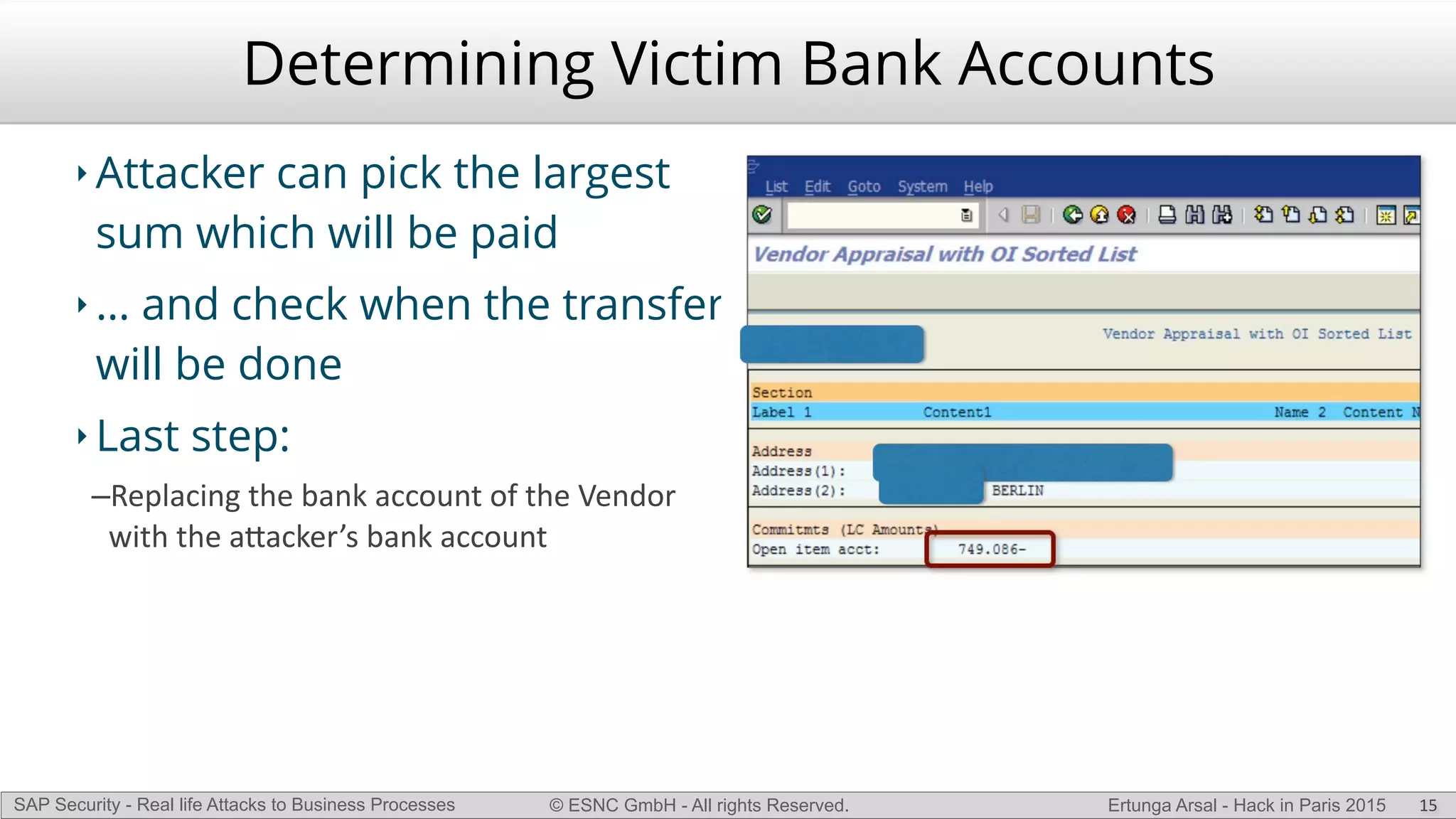
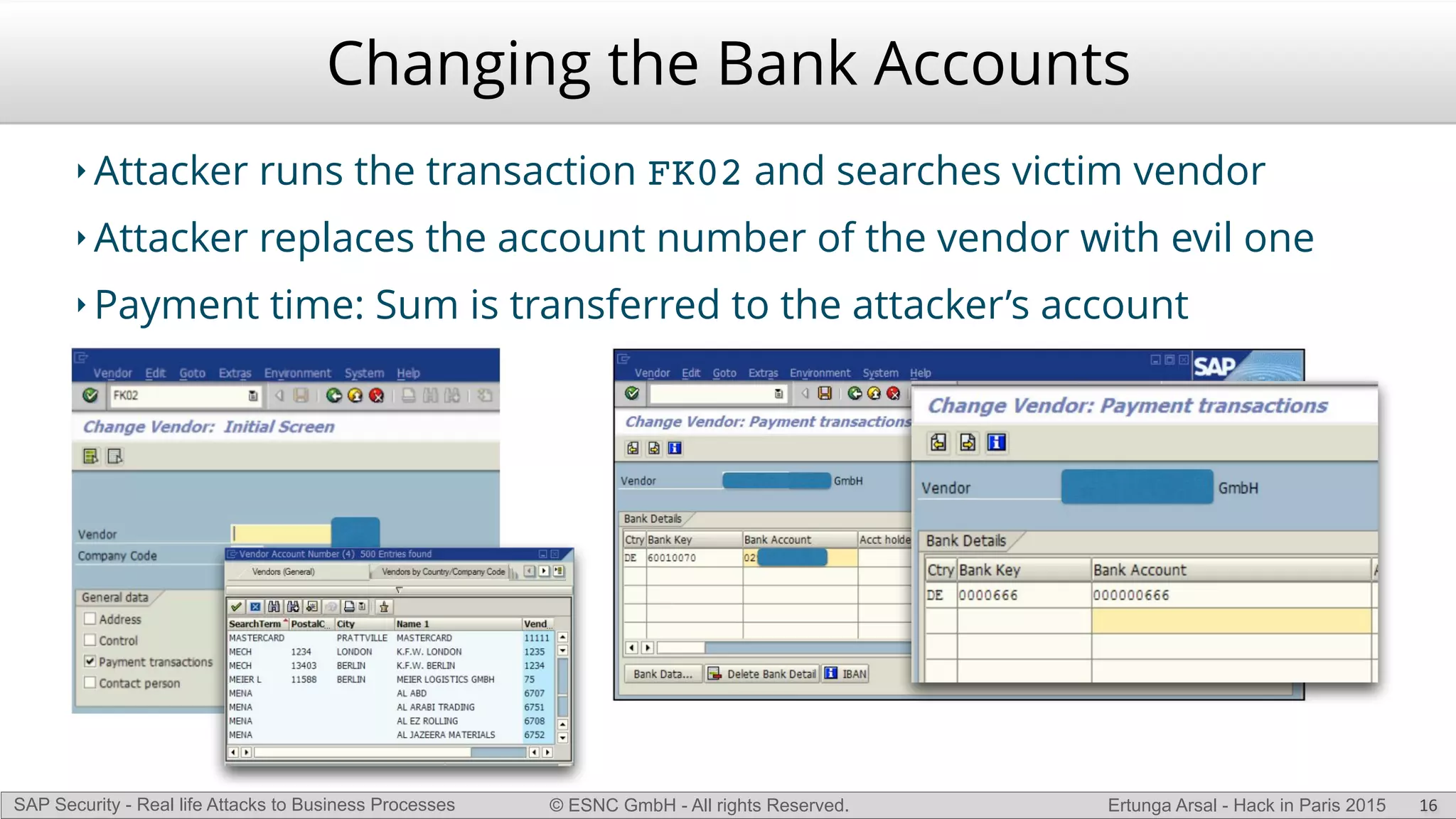
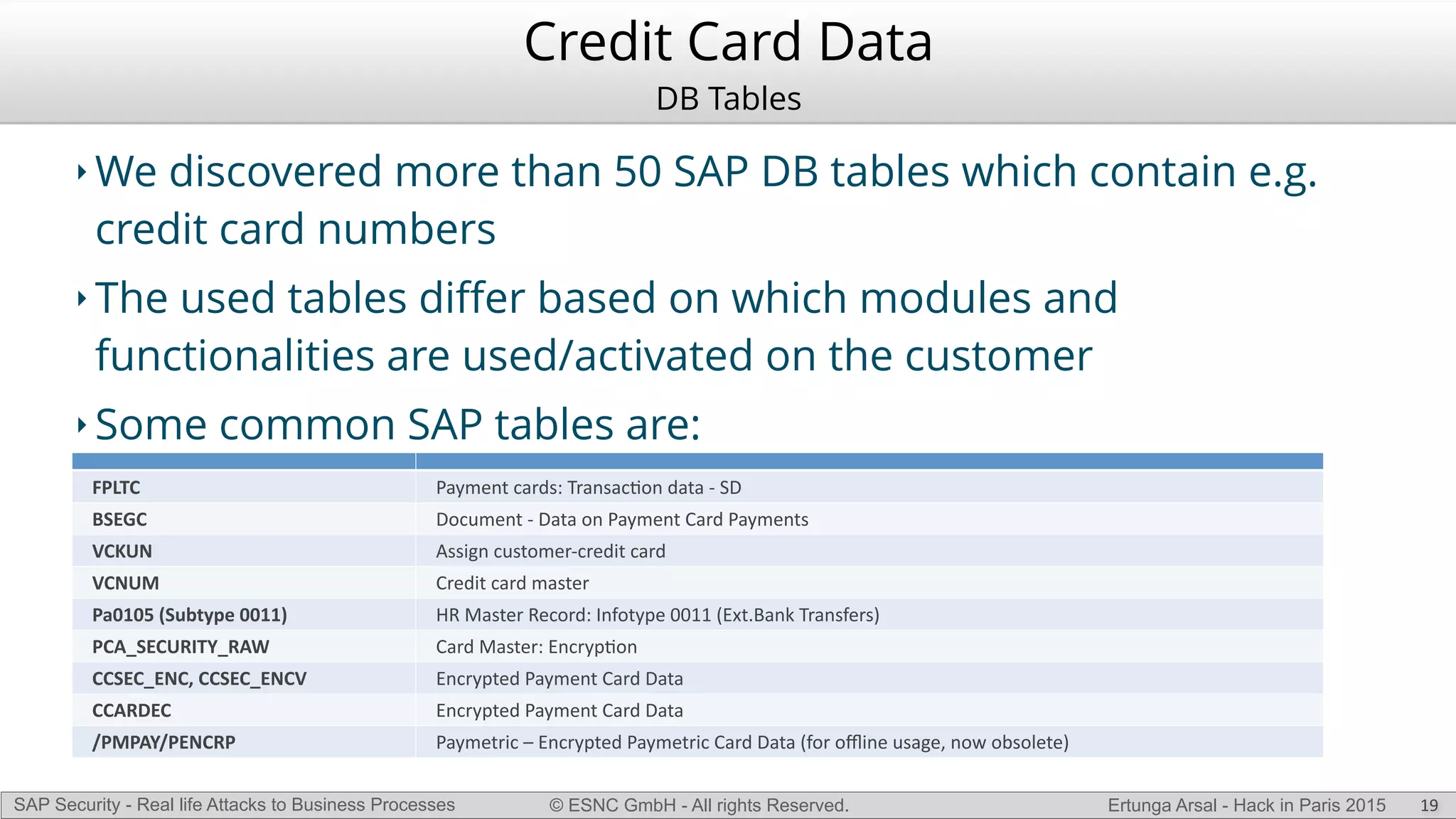
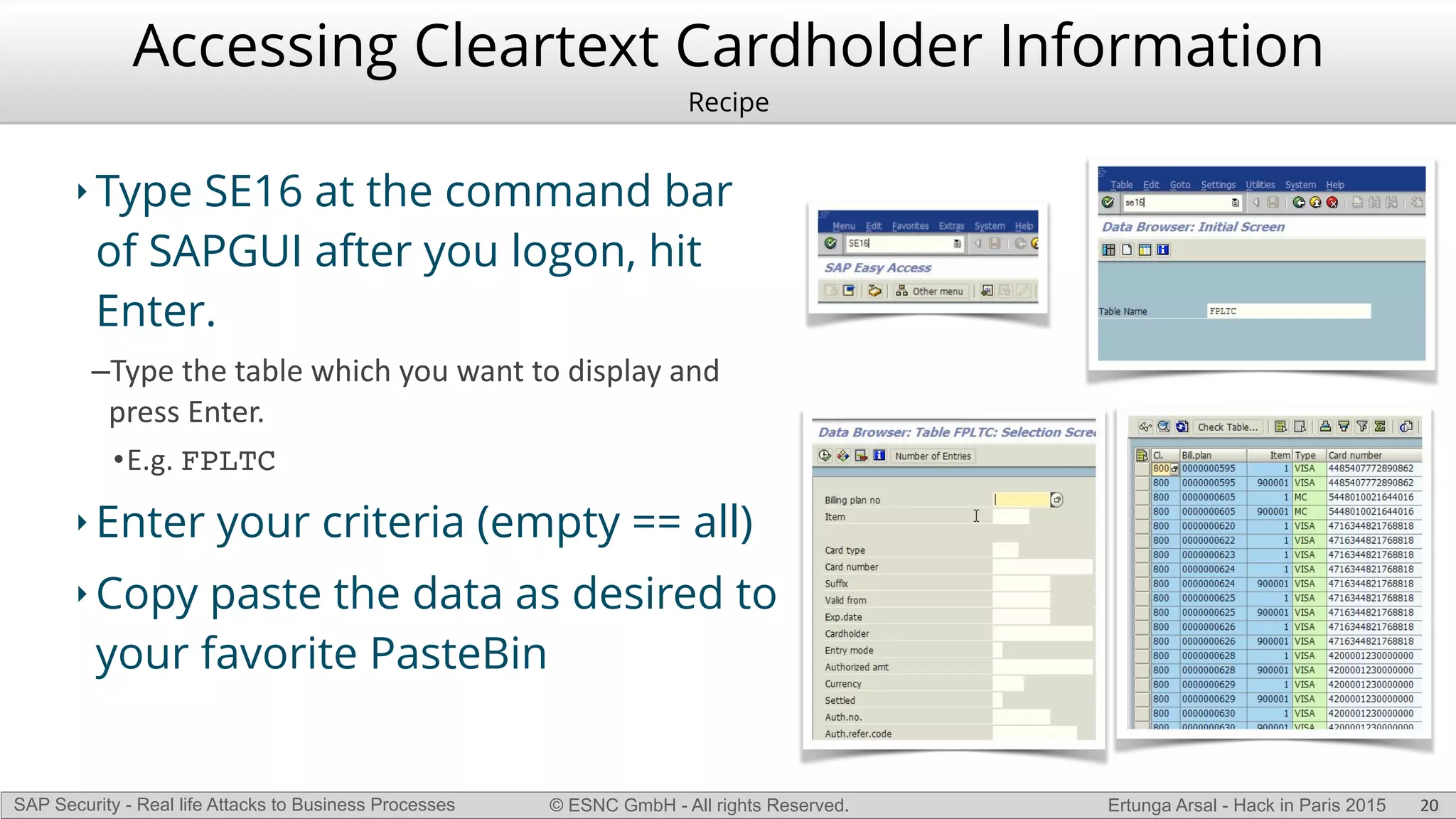
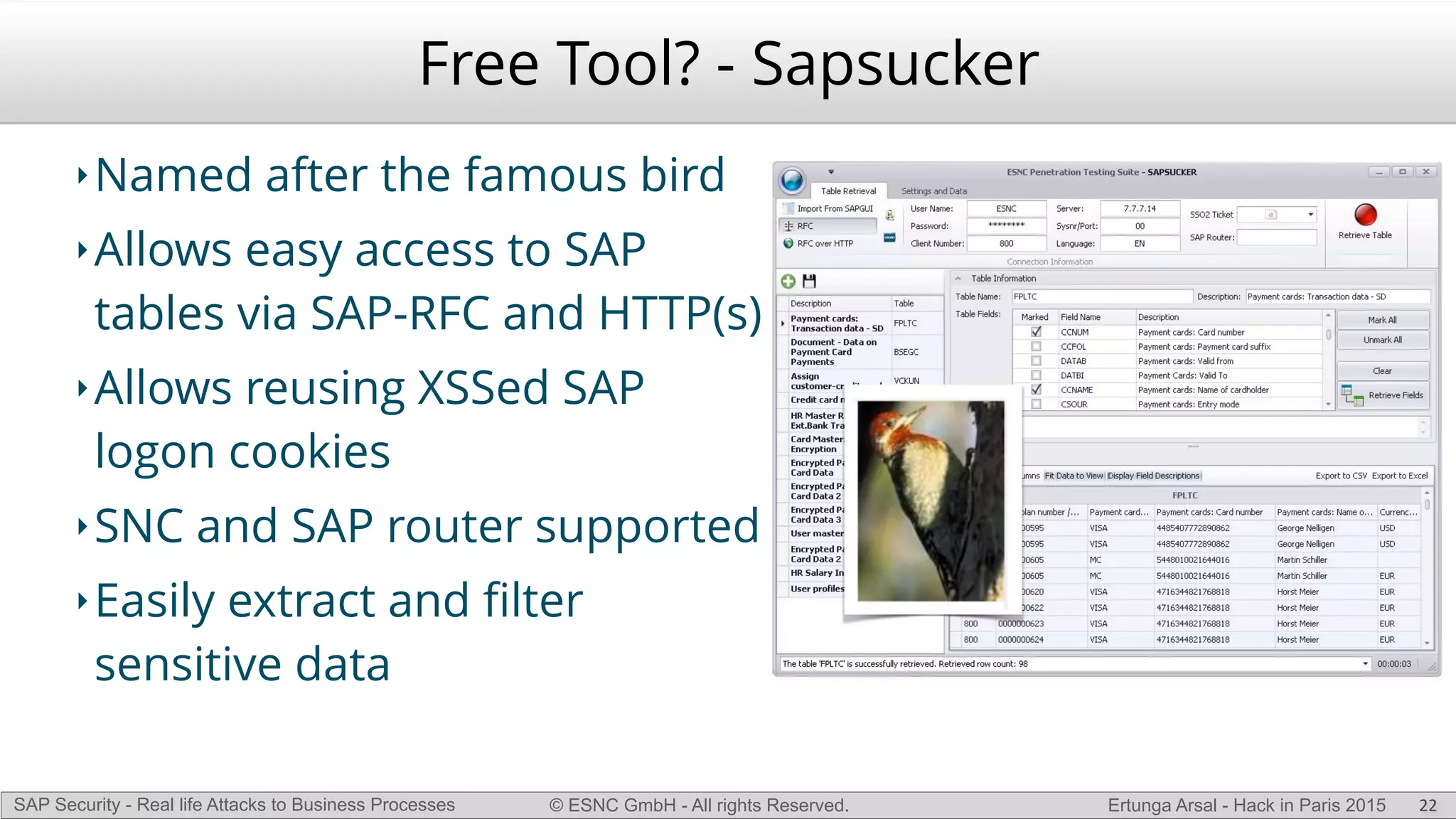
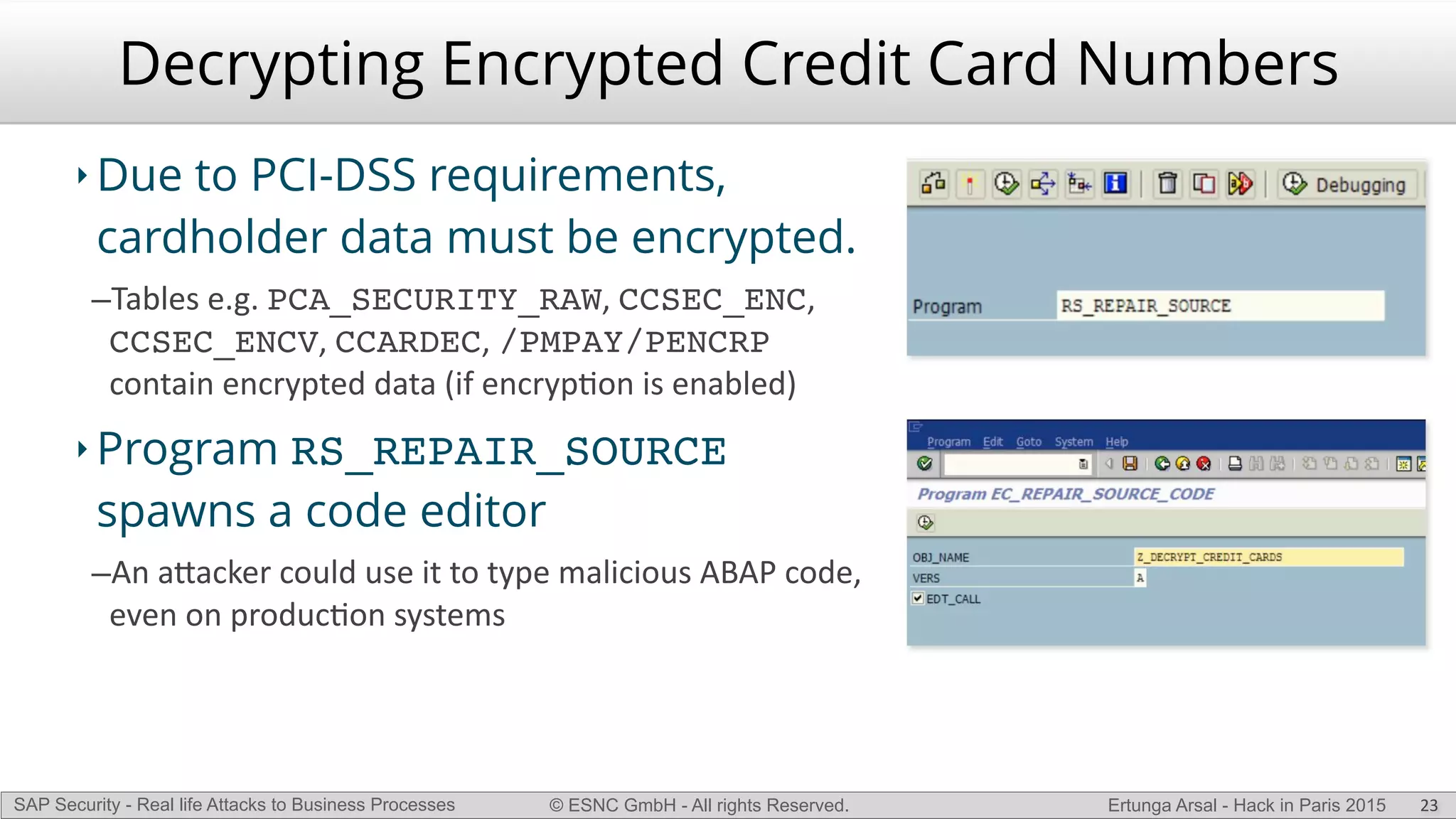
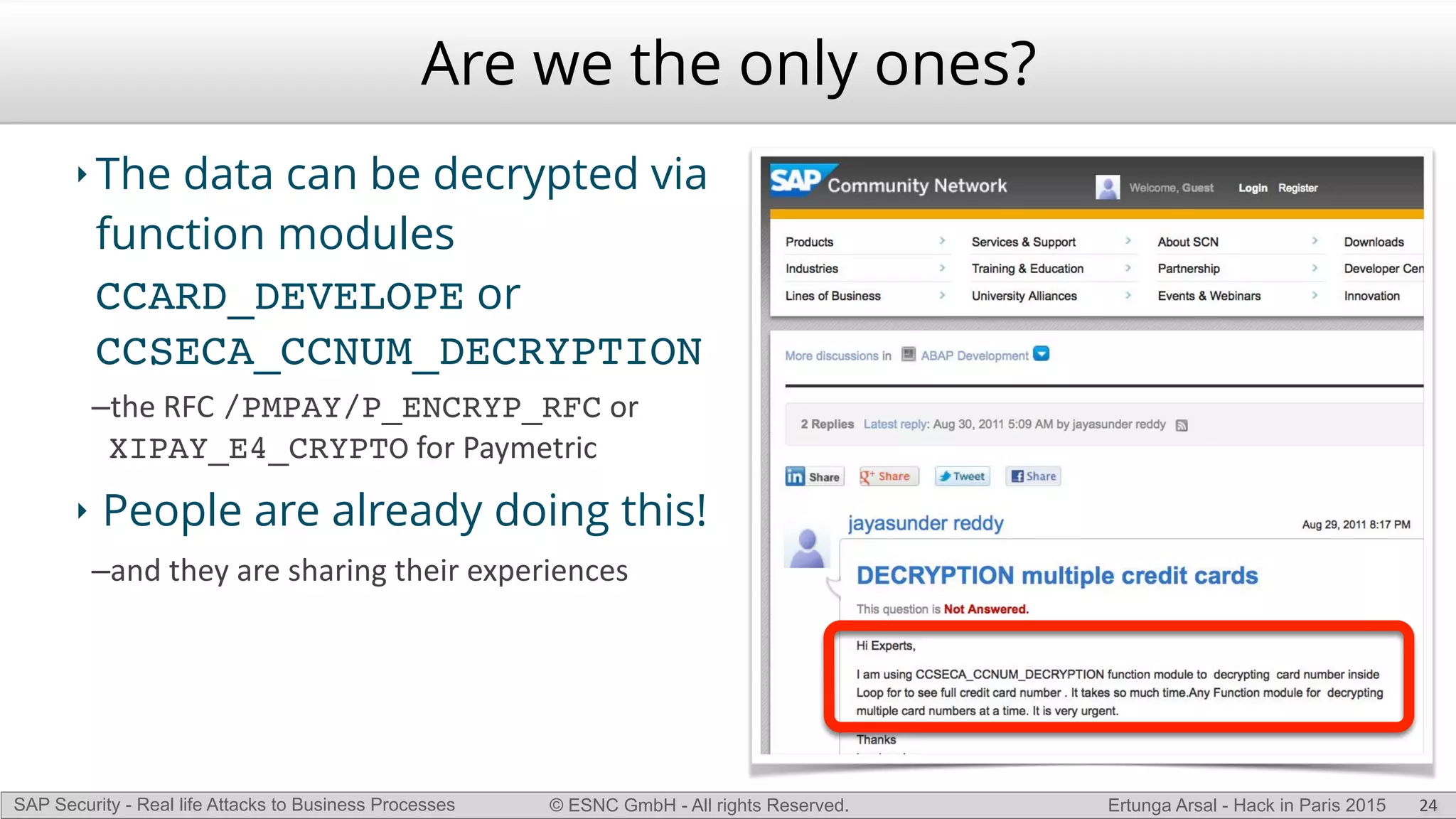
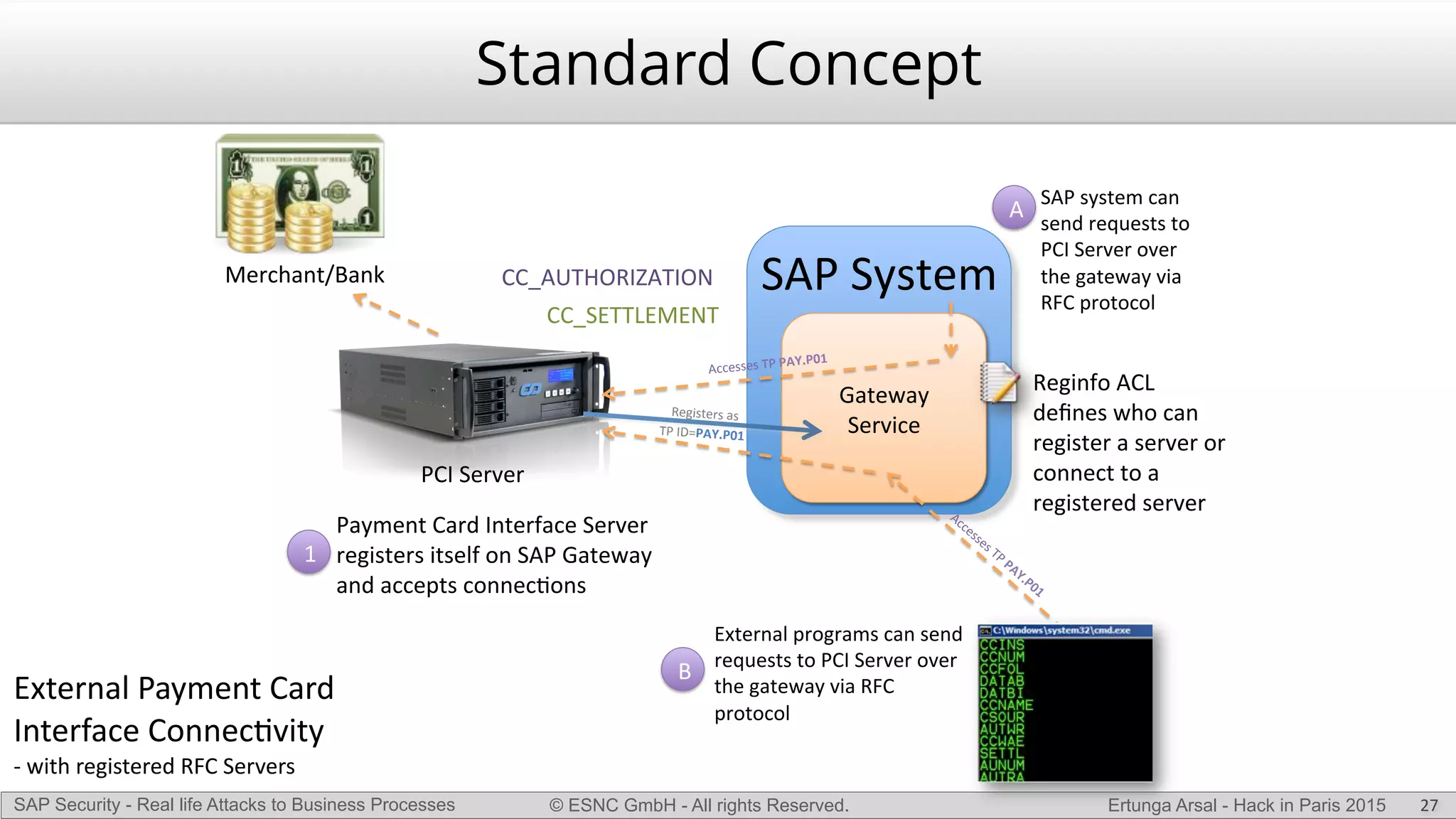
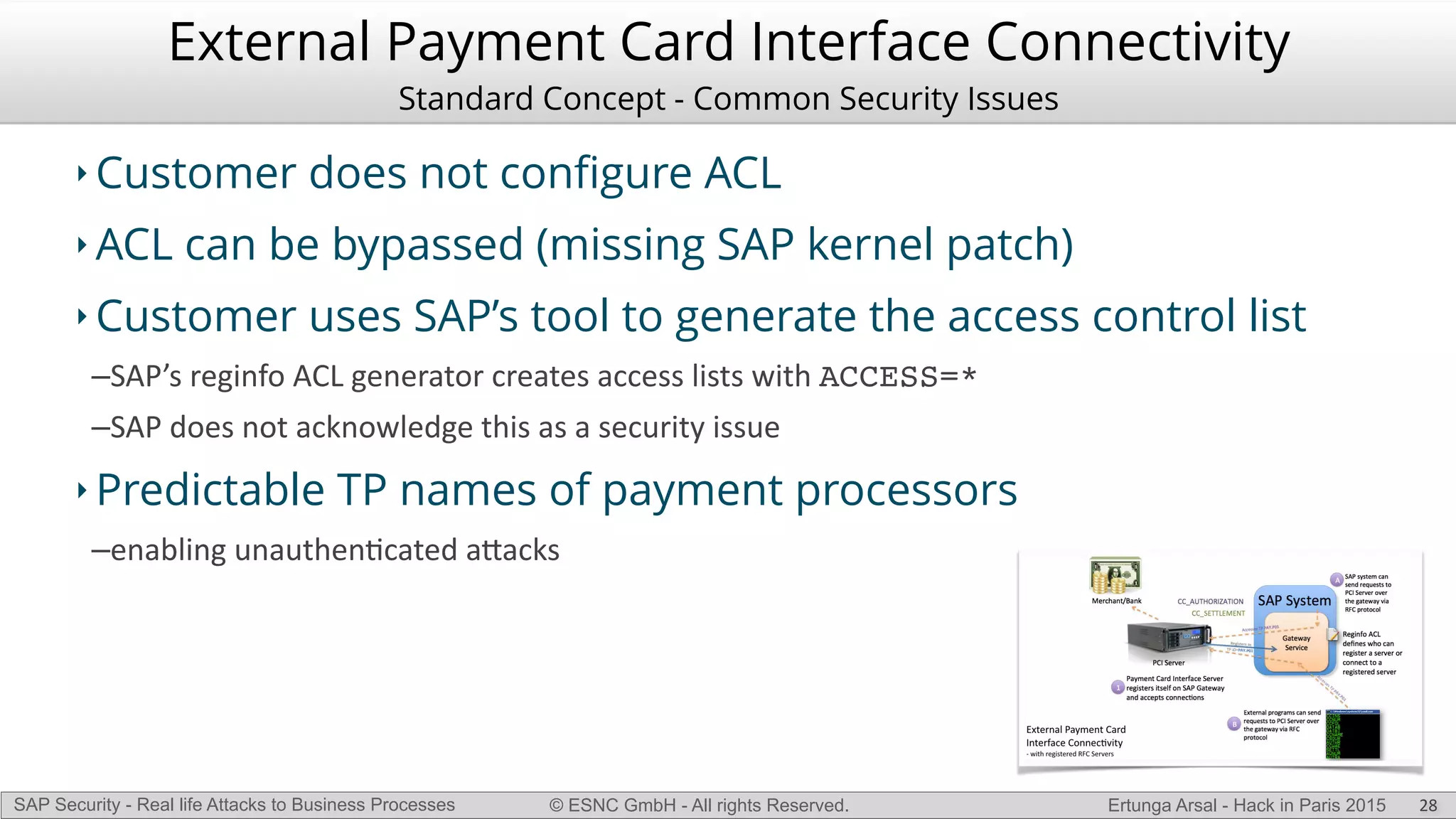
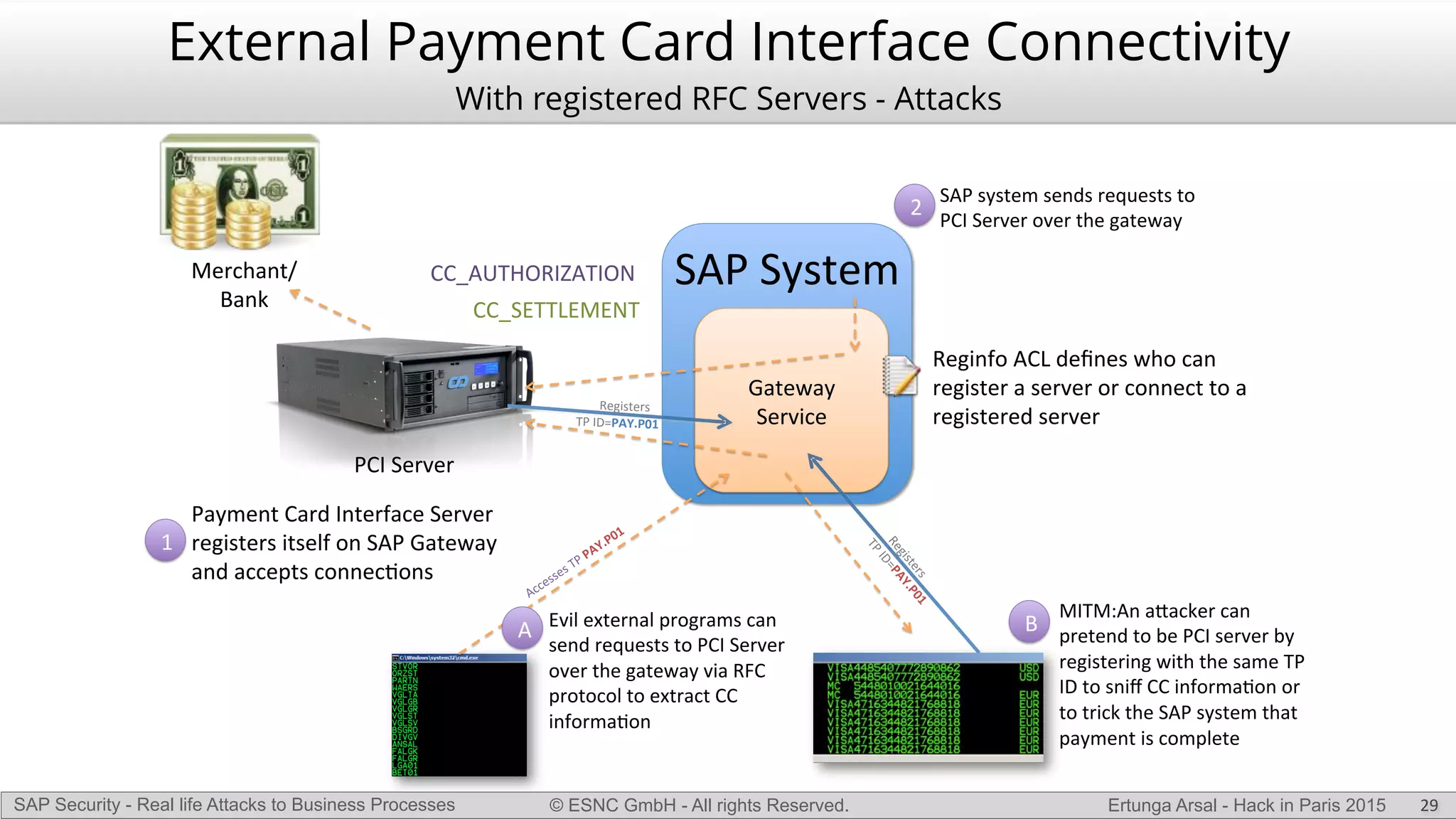
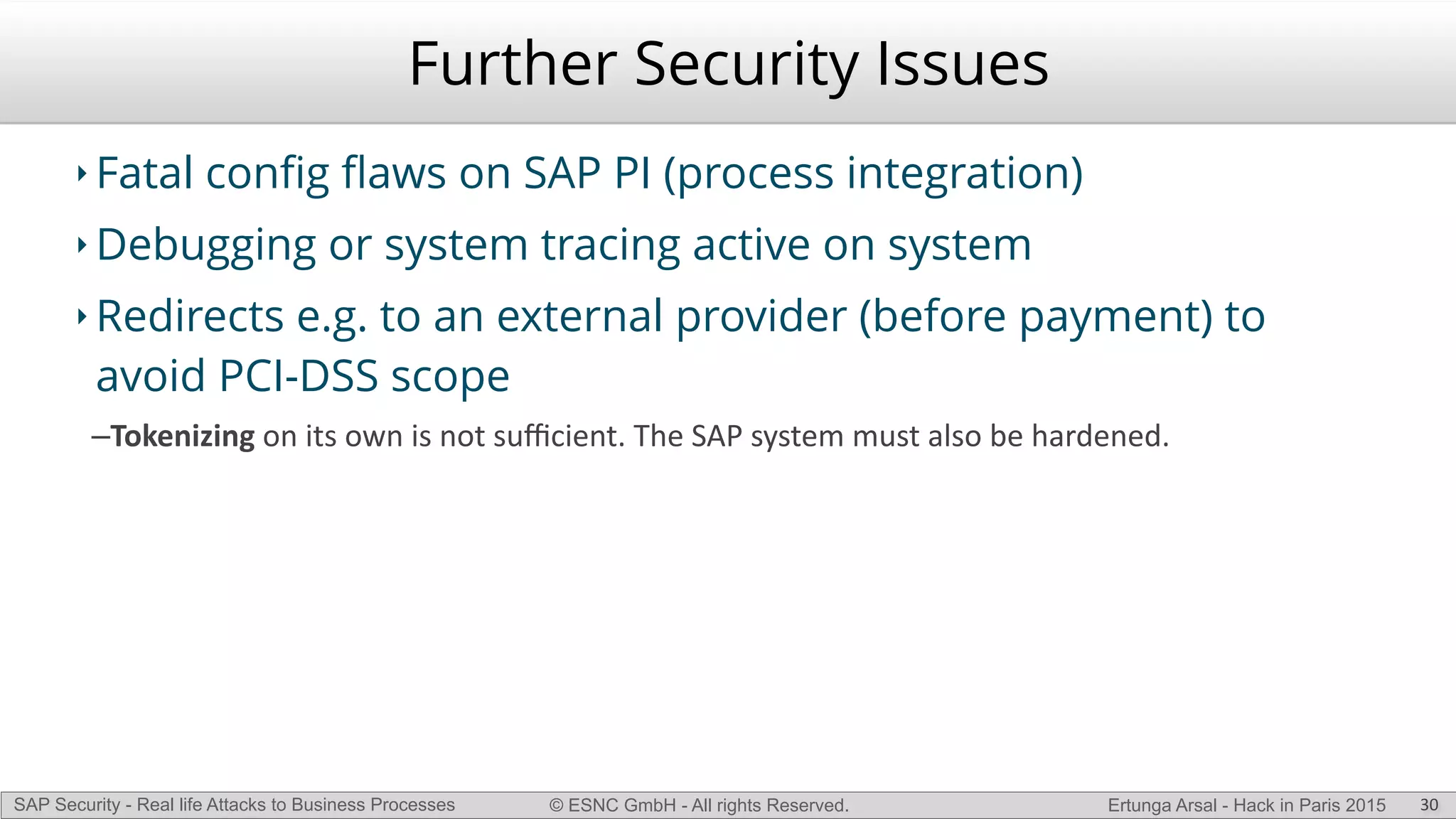
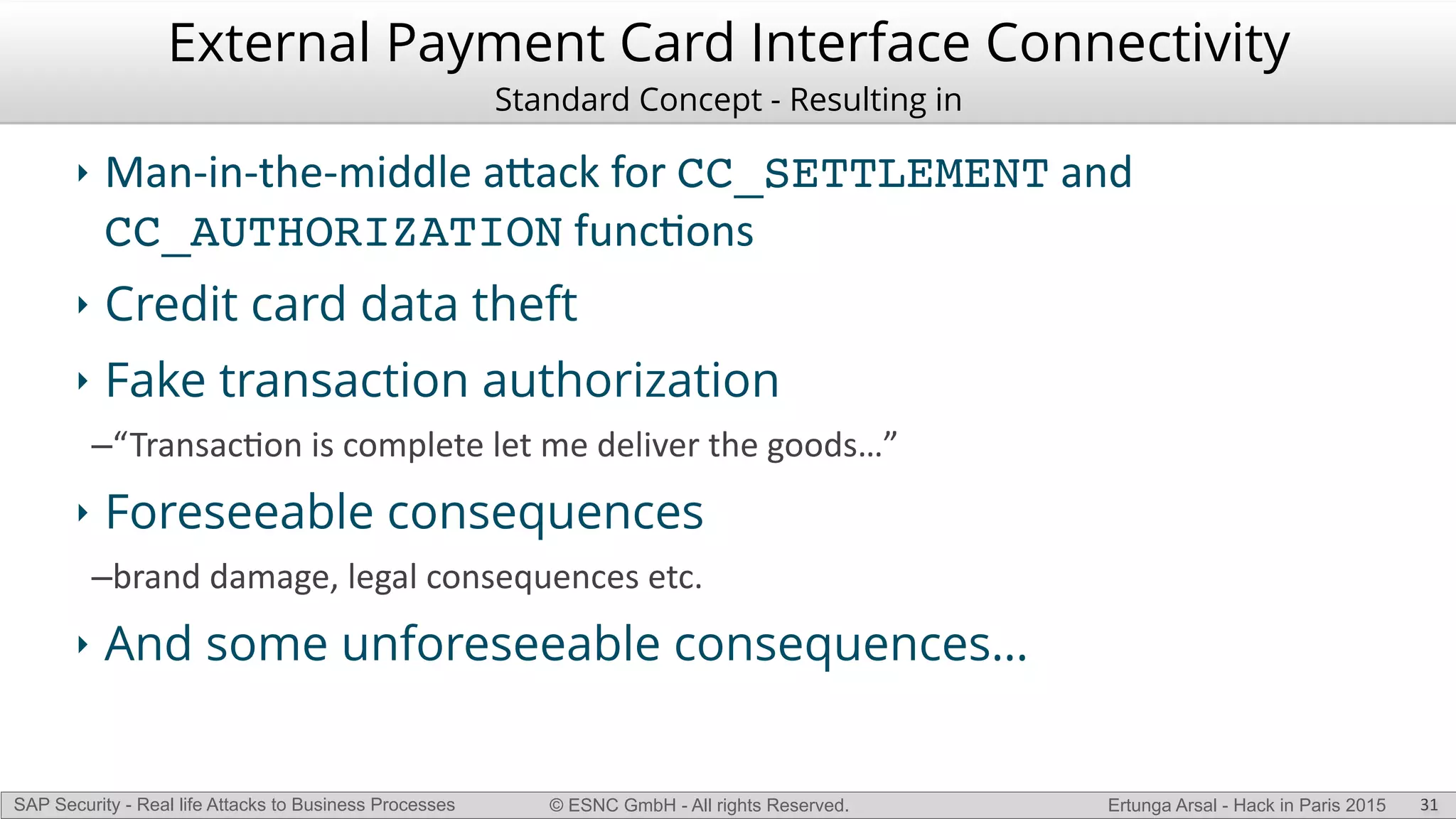
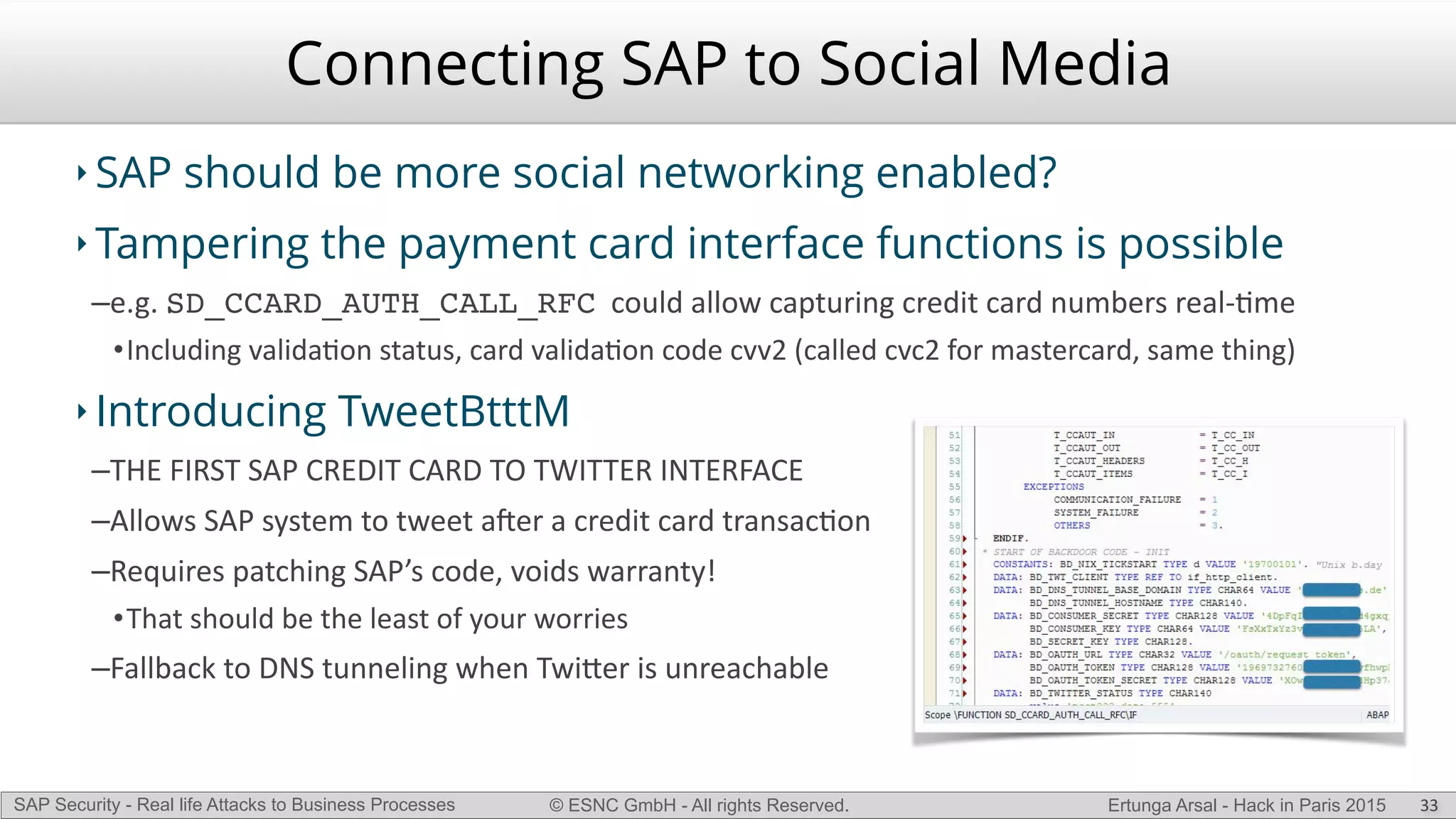
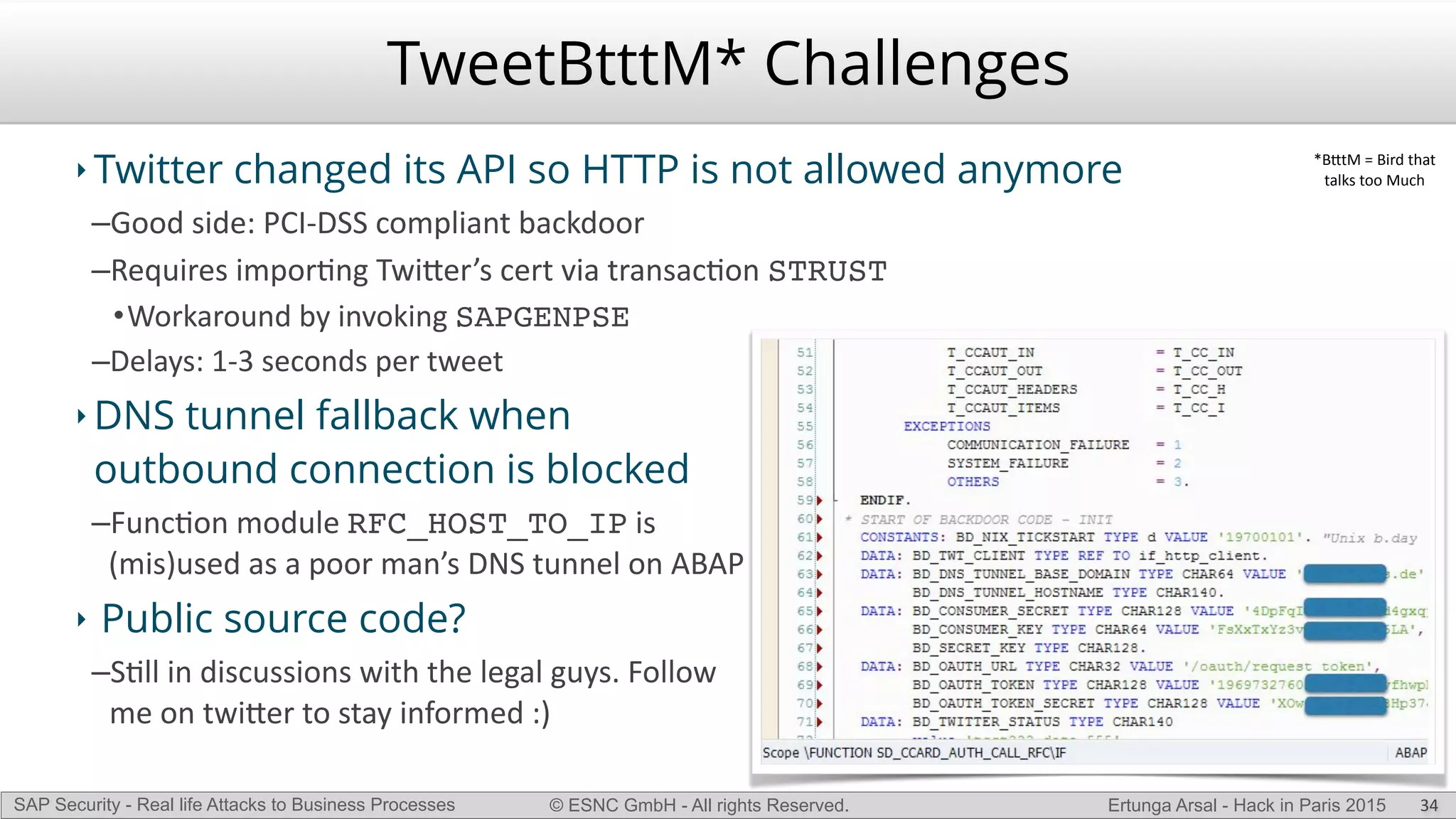
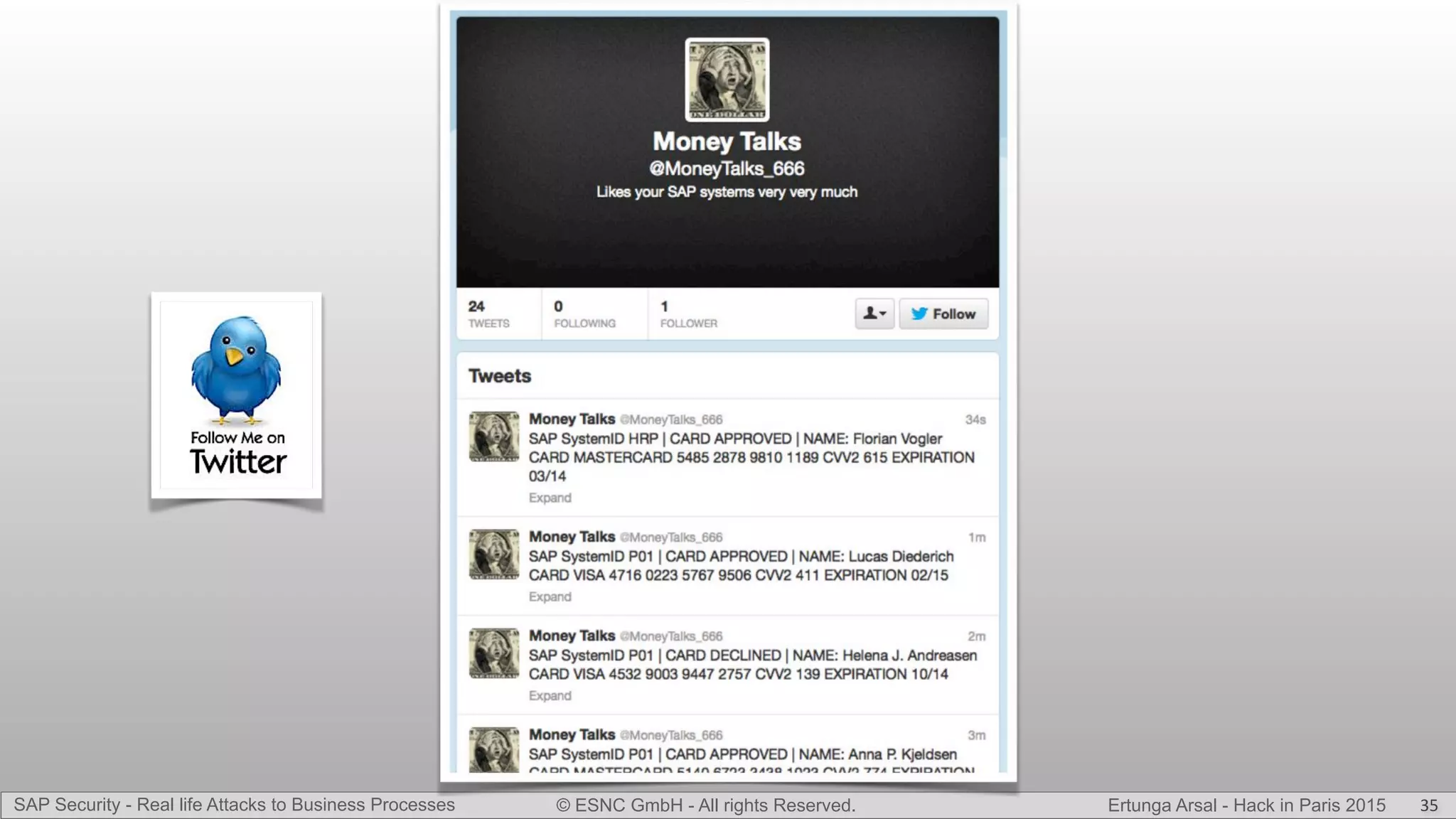
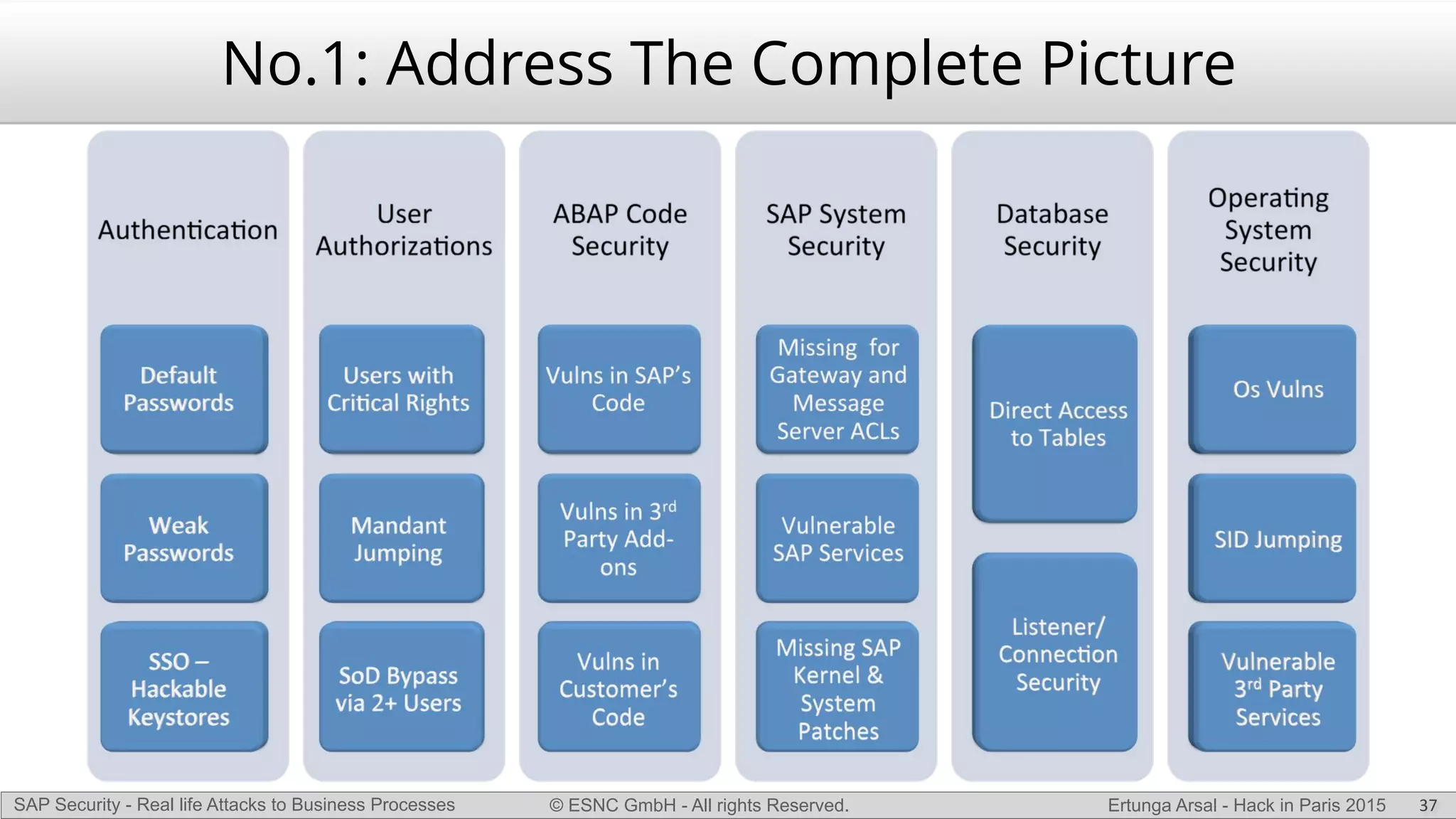
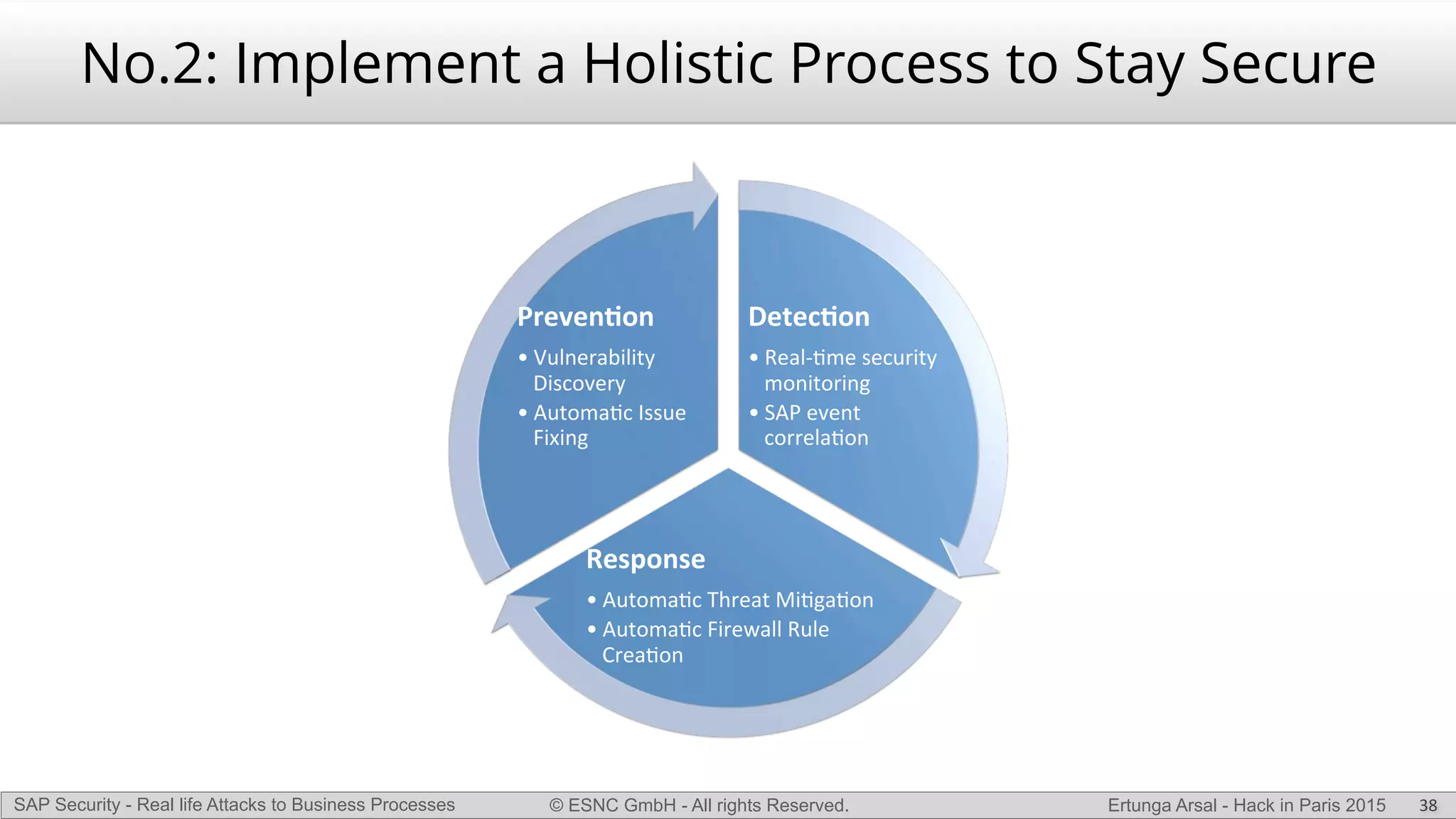
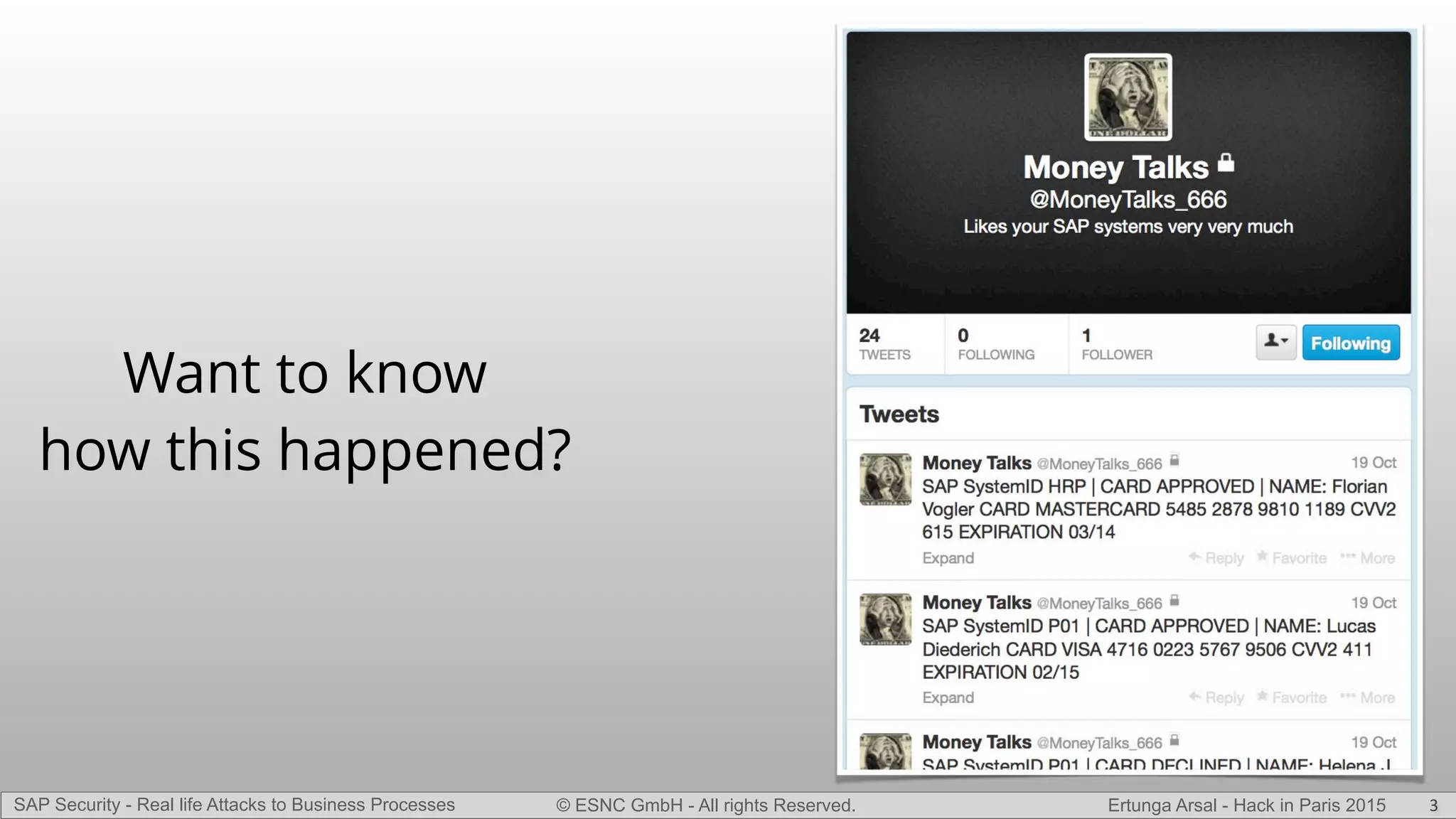
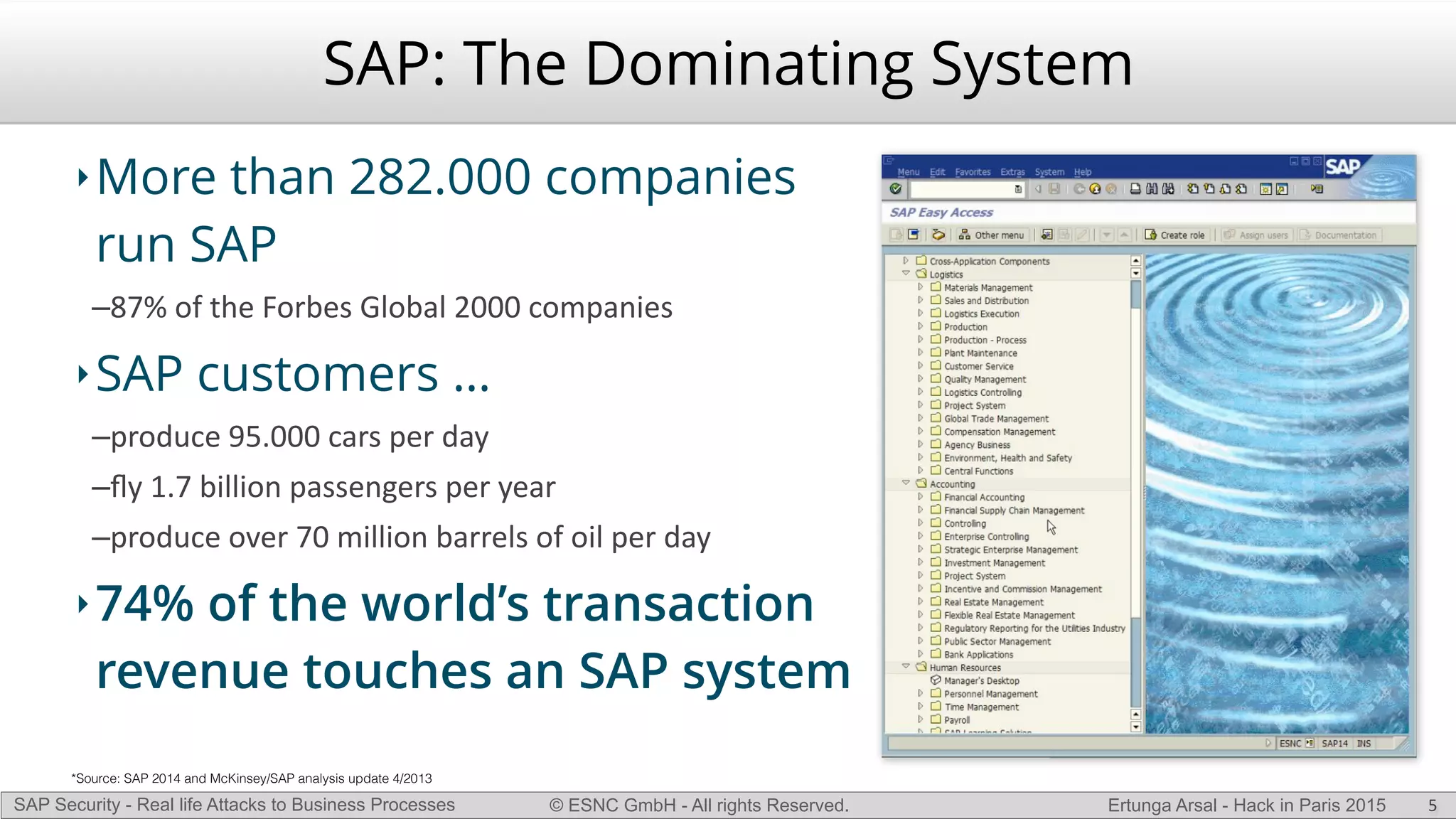
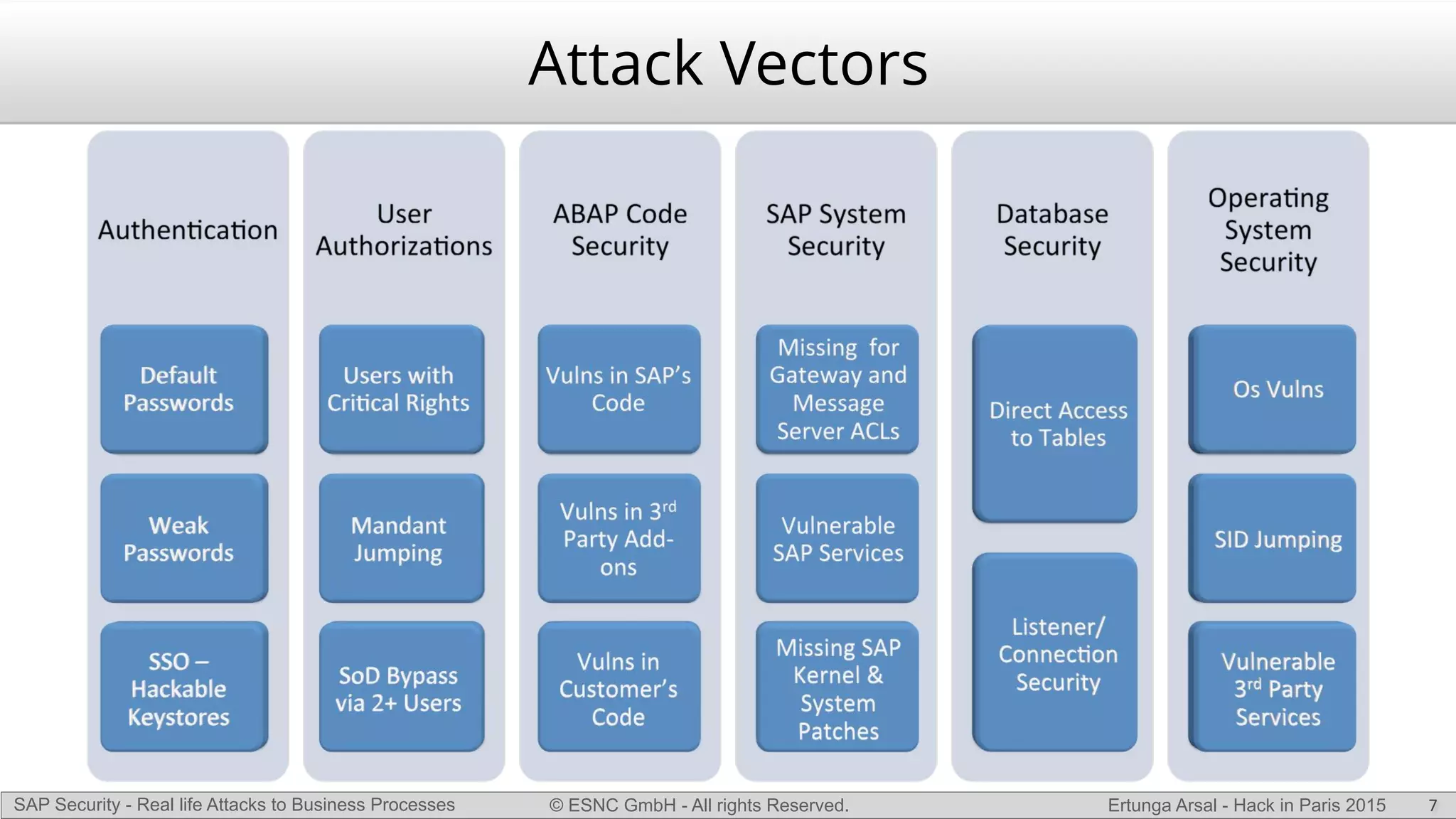
The document discusses security vulnerabilities in SAP systems that can allow attackers to compromise business processes. It begins by explaining how SAP systems are complex with numerous components and third-party additions that are often unpatched. It then demonstrates how exploiting vulnerabilities in third-party components and core SAP services can allow an attacker to gain admin privileges on the system. With access, the attacker can manipulate business processes like vendor payments to divert funds to their own bank account. The document also examines how payment card data may be stored unencrypted in SAP tables and accessed remotely to steal card details.


(
‣ We were able to bypass the patch’s protection
–Second(patch(came(a(couple(of(months(later([SAP(Note(1826162](
–This(Kme(CVSS(v2(score(is:(7.5$(High$Risk)$
‣ Same vulnerability higher CVSS score
9](https://image.slidesharecdn.com/f00dc98a-33fe-4d49-93e9-e14dd5aedaaf-150729043330-lva1-app6892/75/SAP-Security-Real-life-Attacks-to-Business-Processes-Hack-in-Paris-2015-9-2048.jpg)