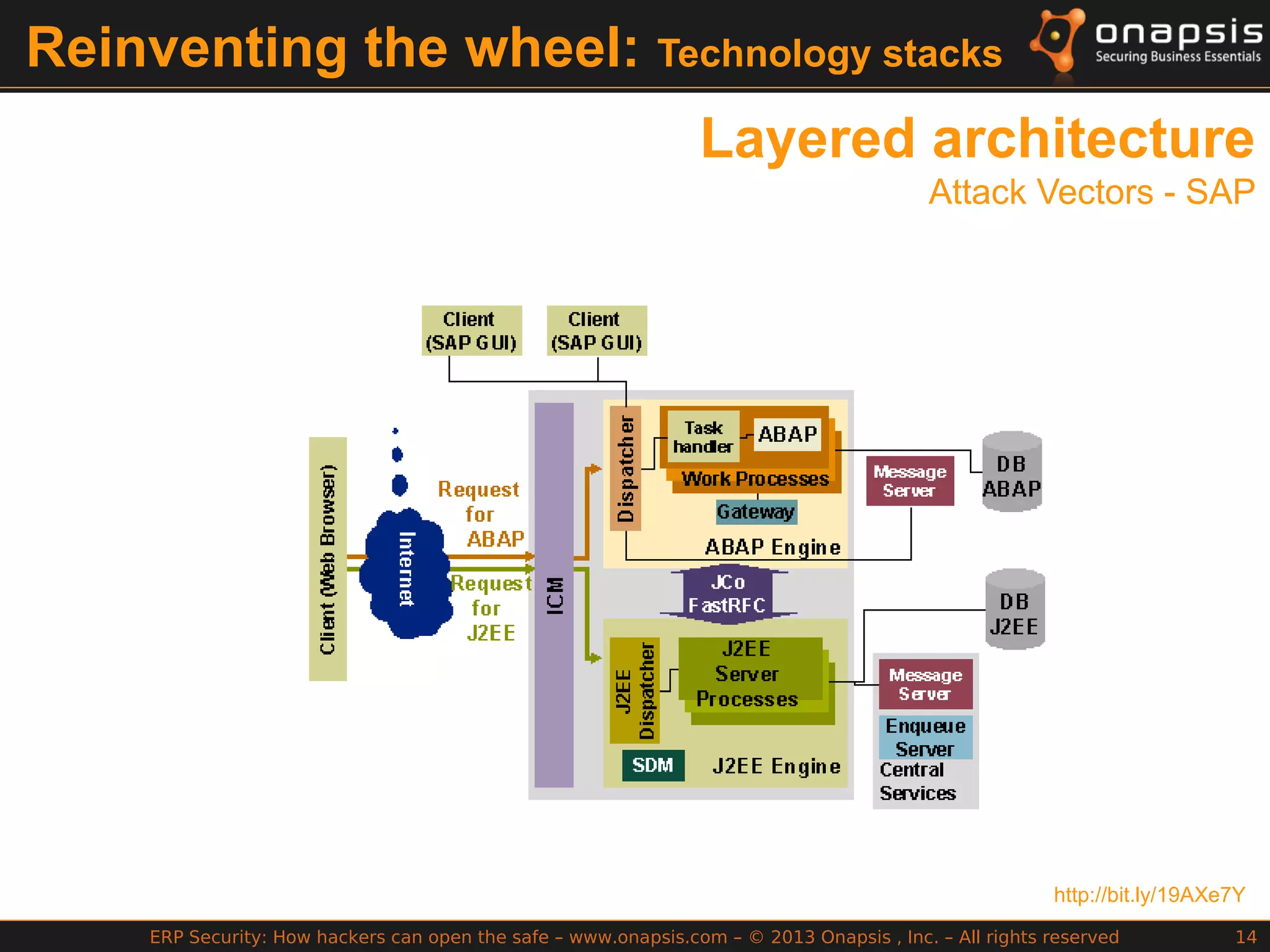
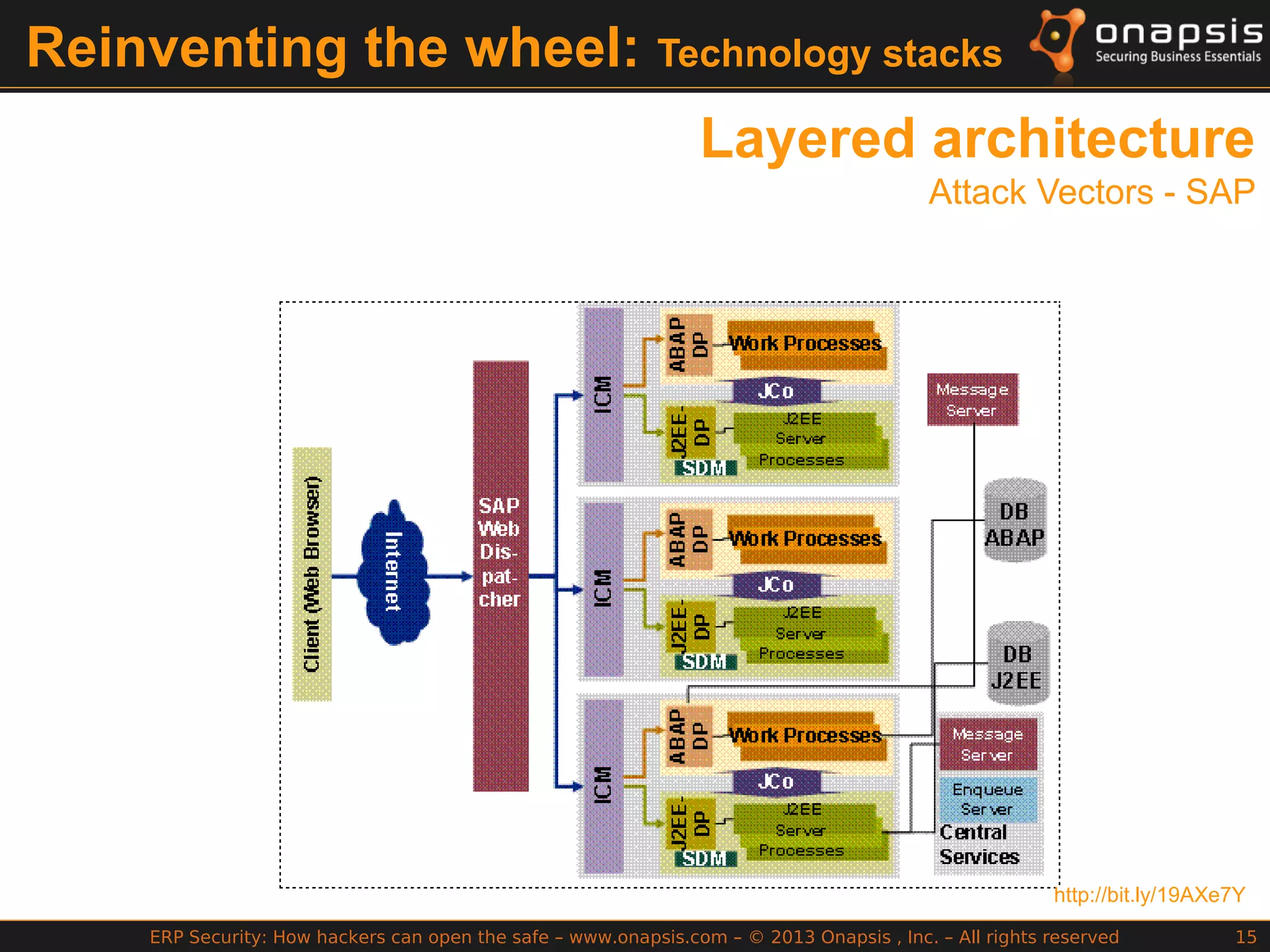
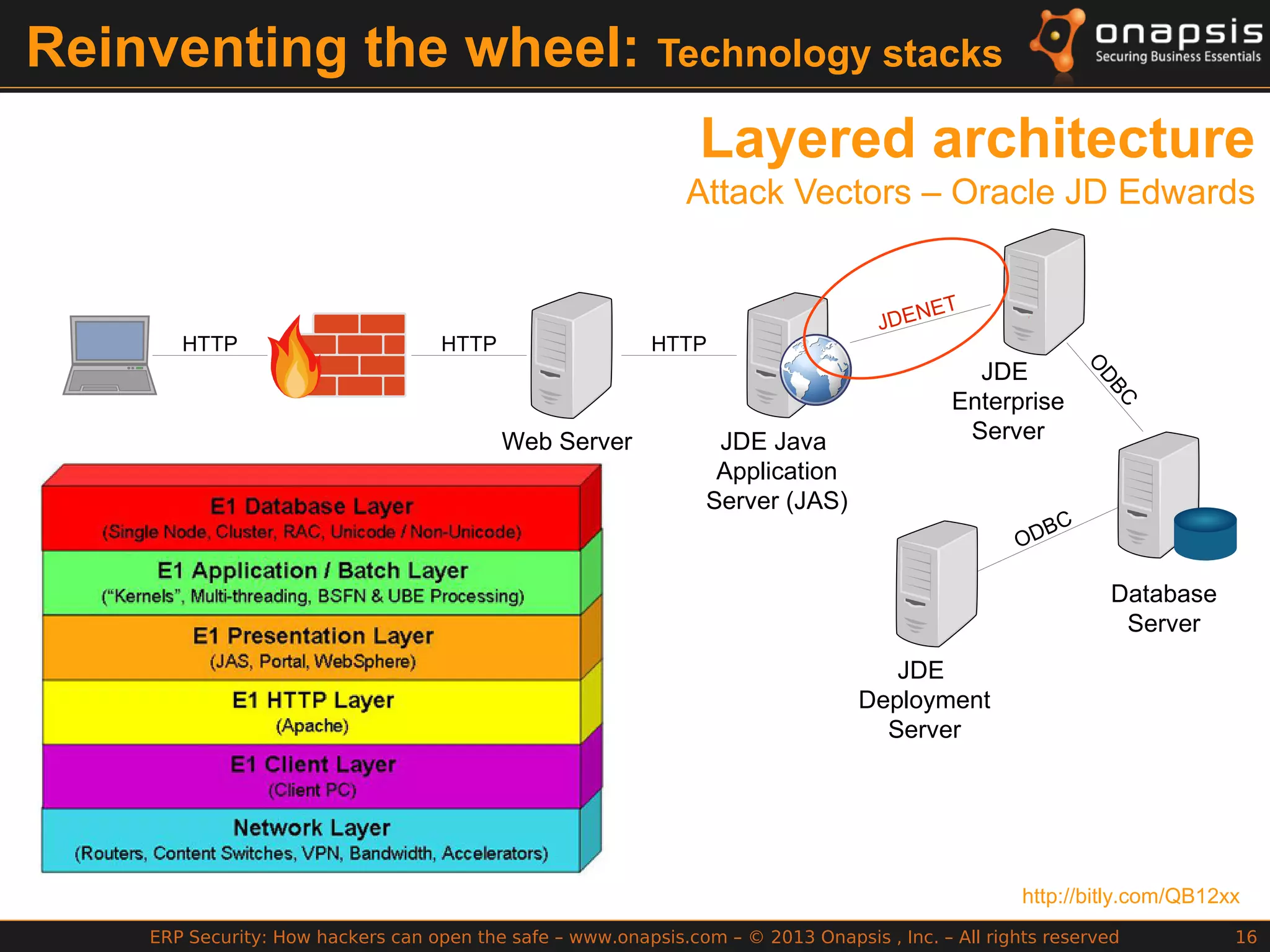
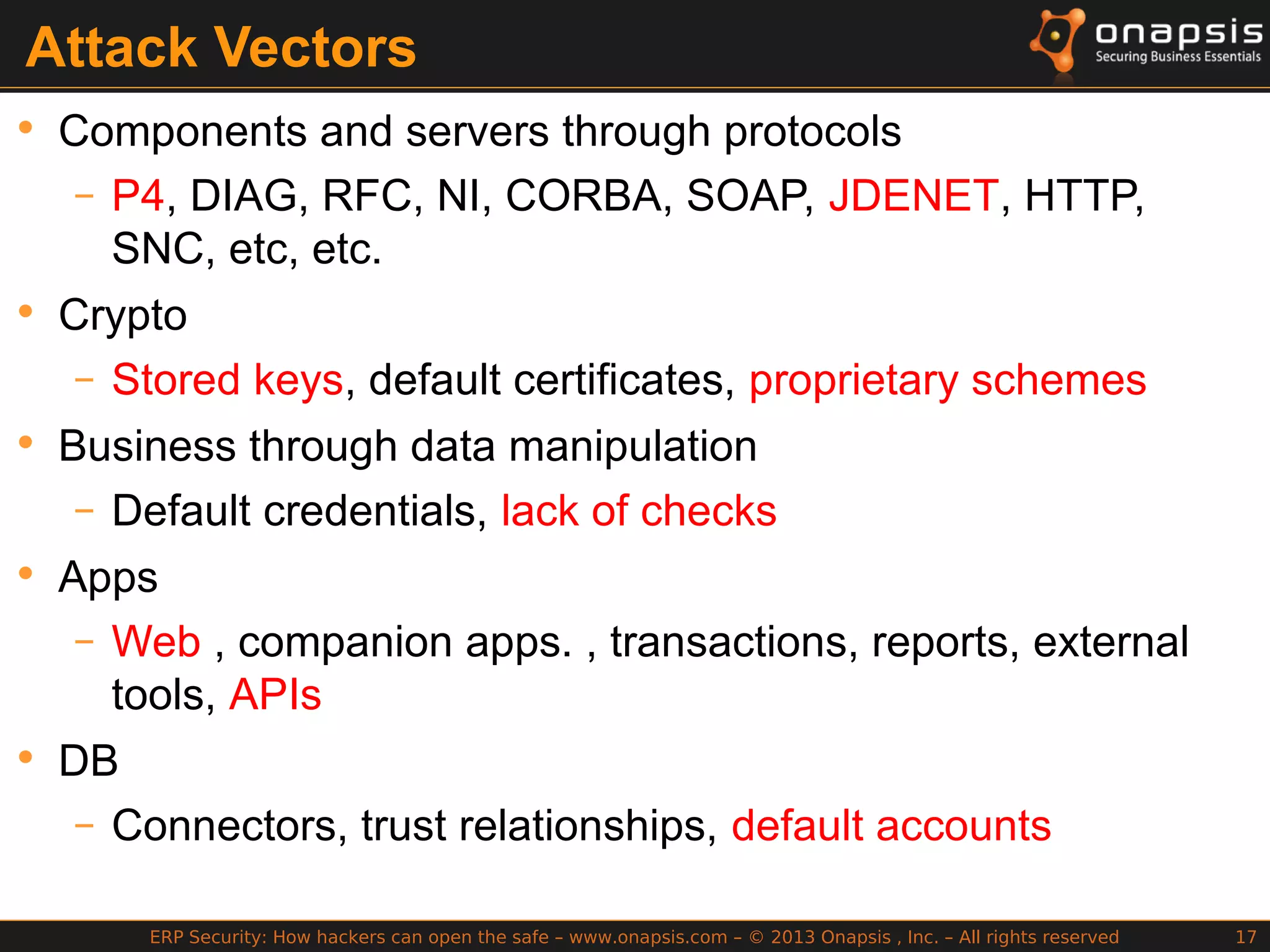
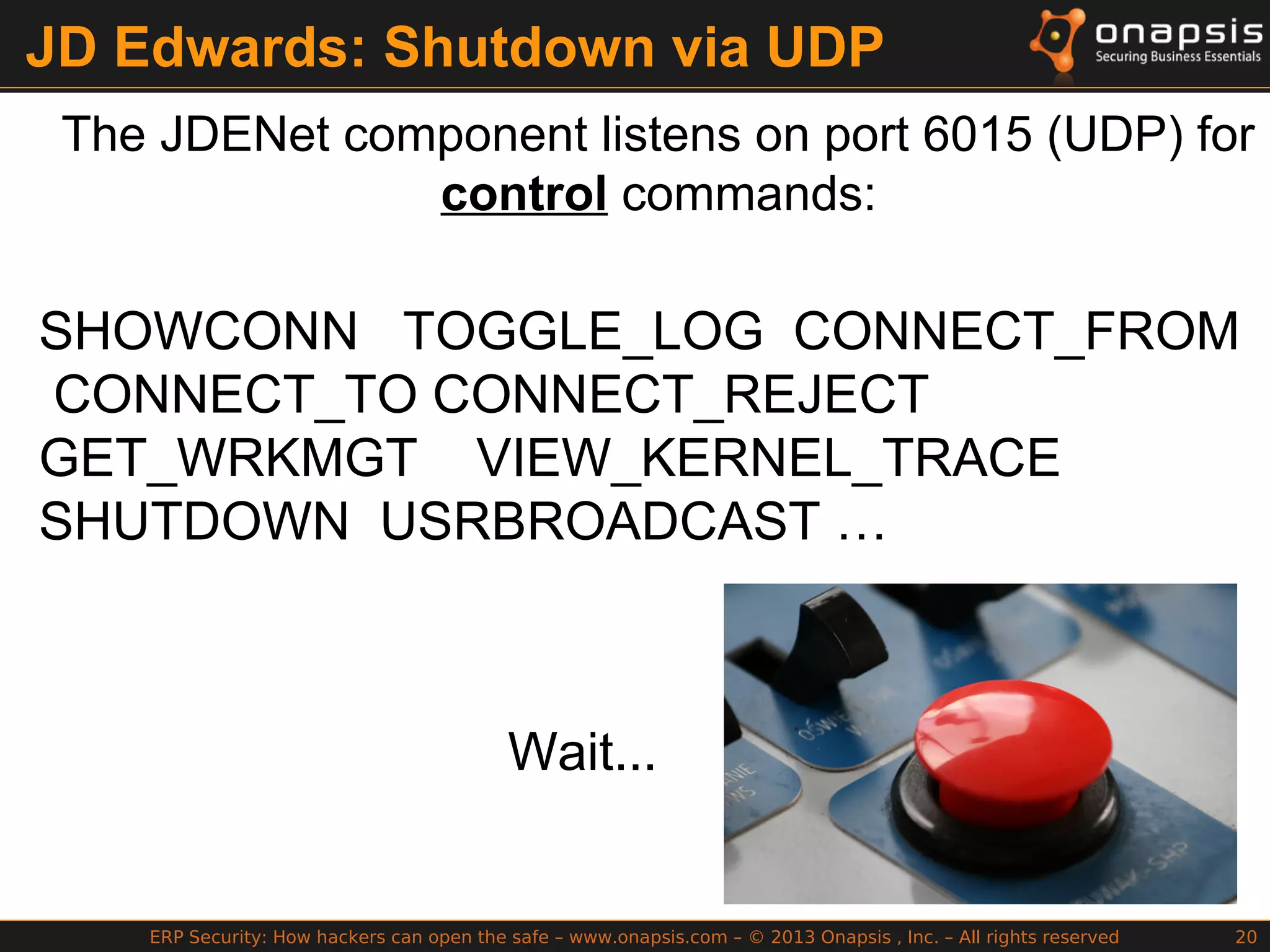
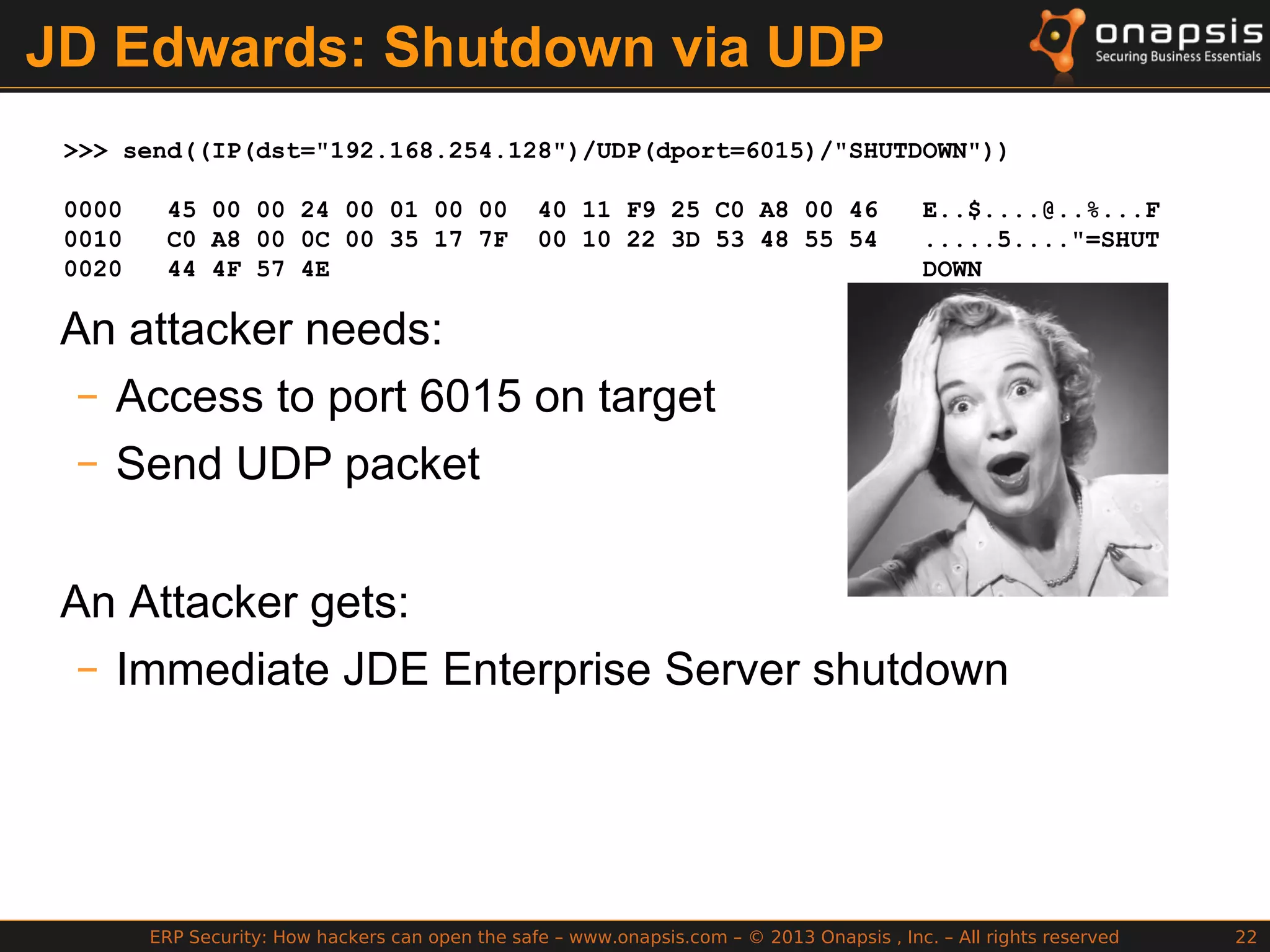
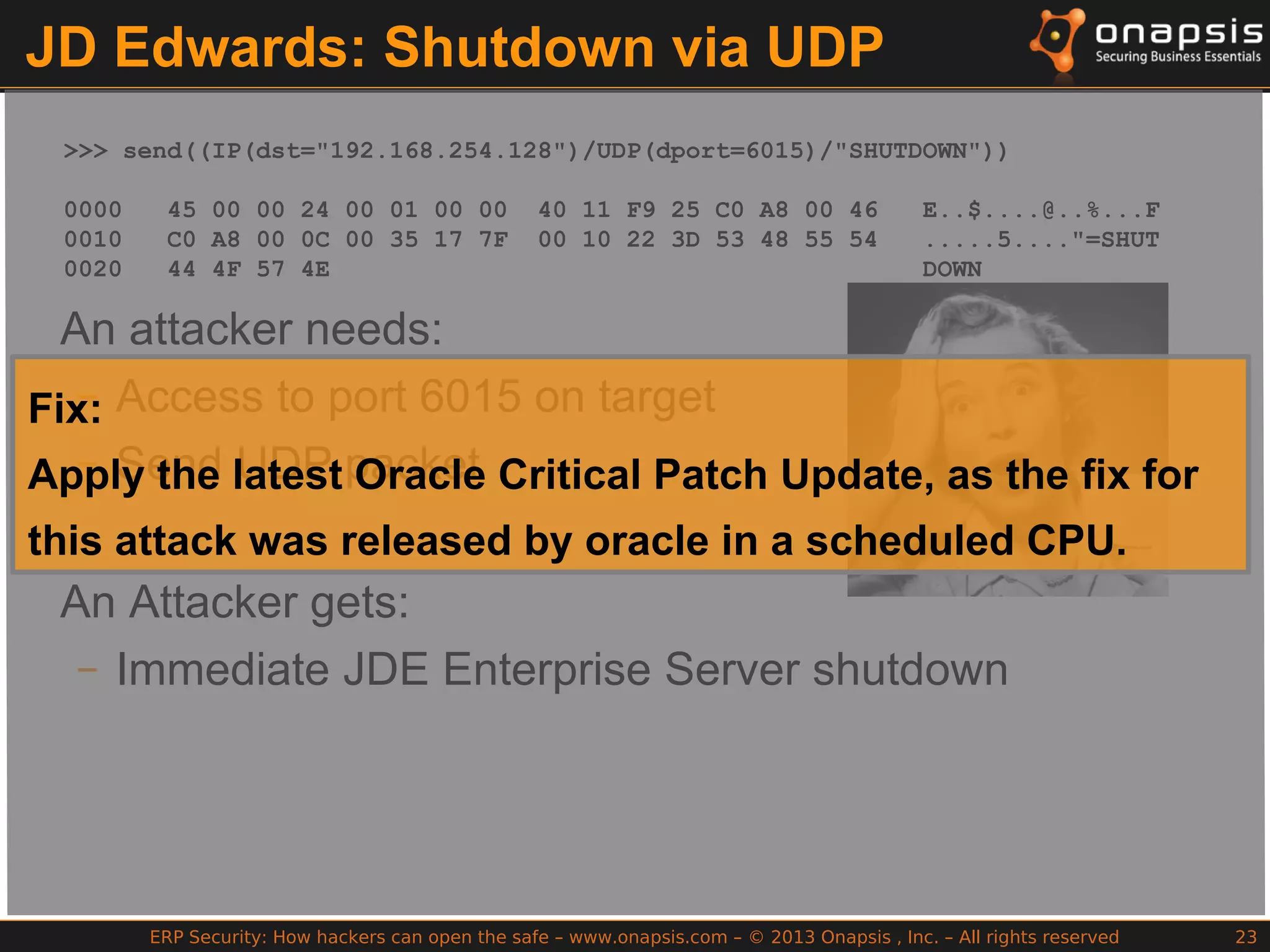
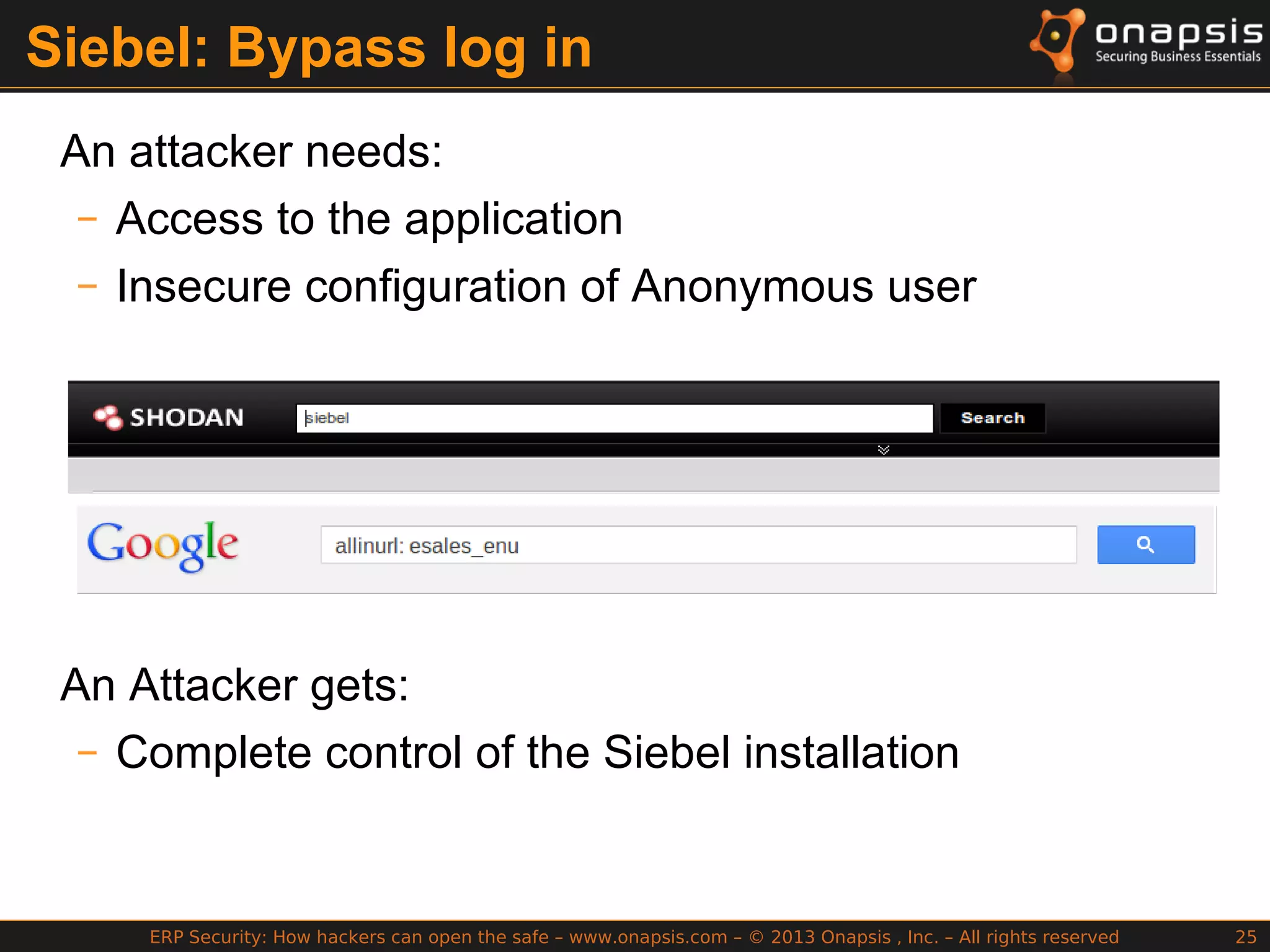
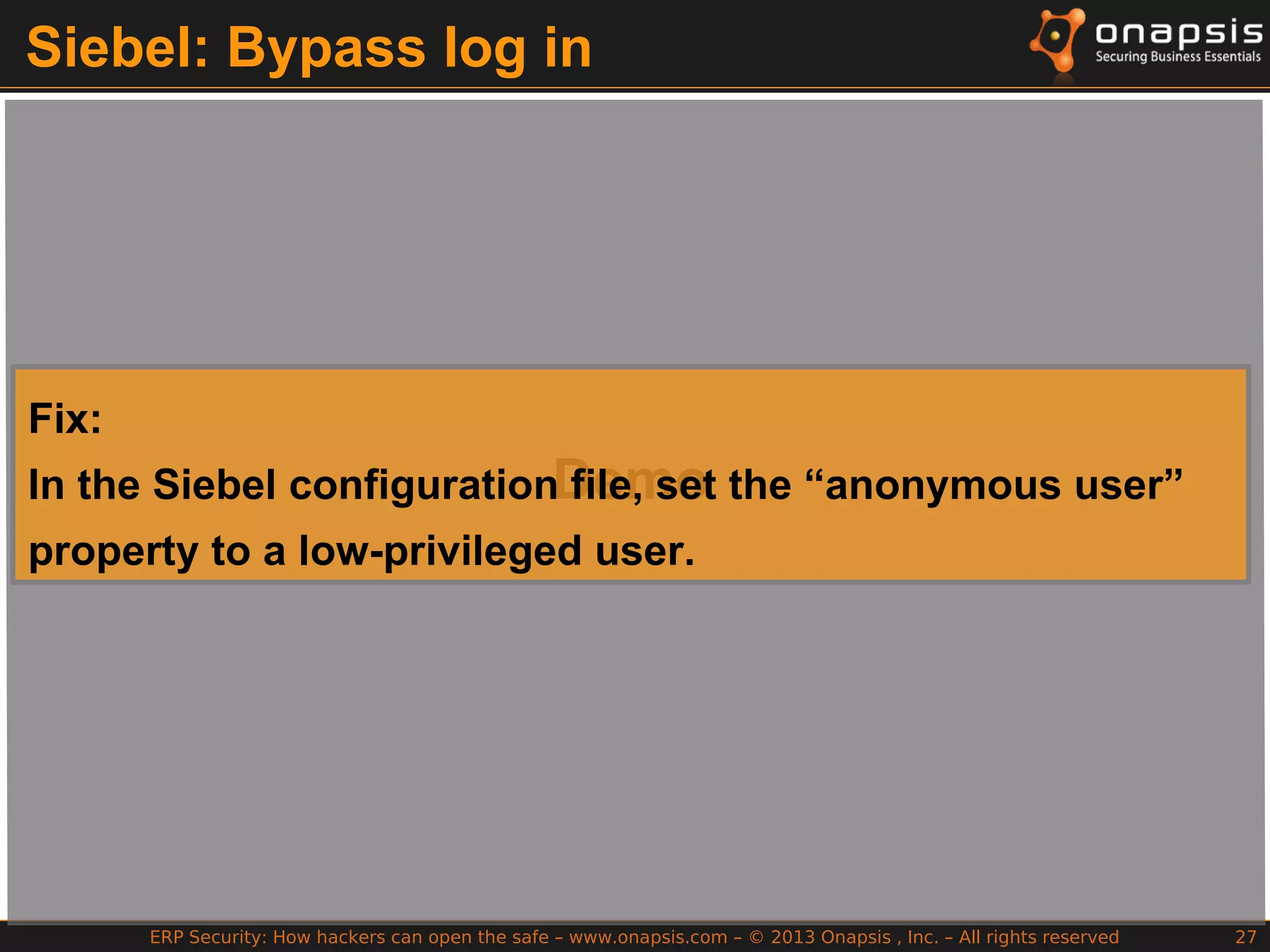
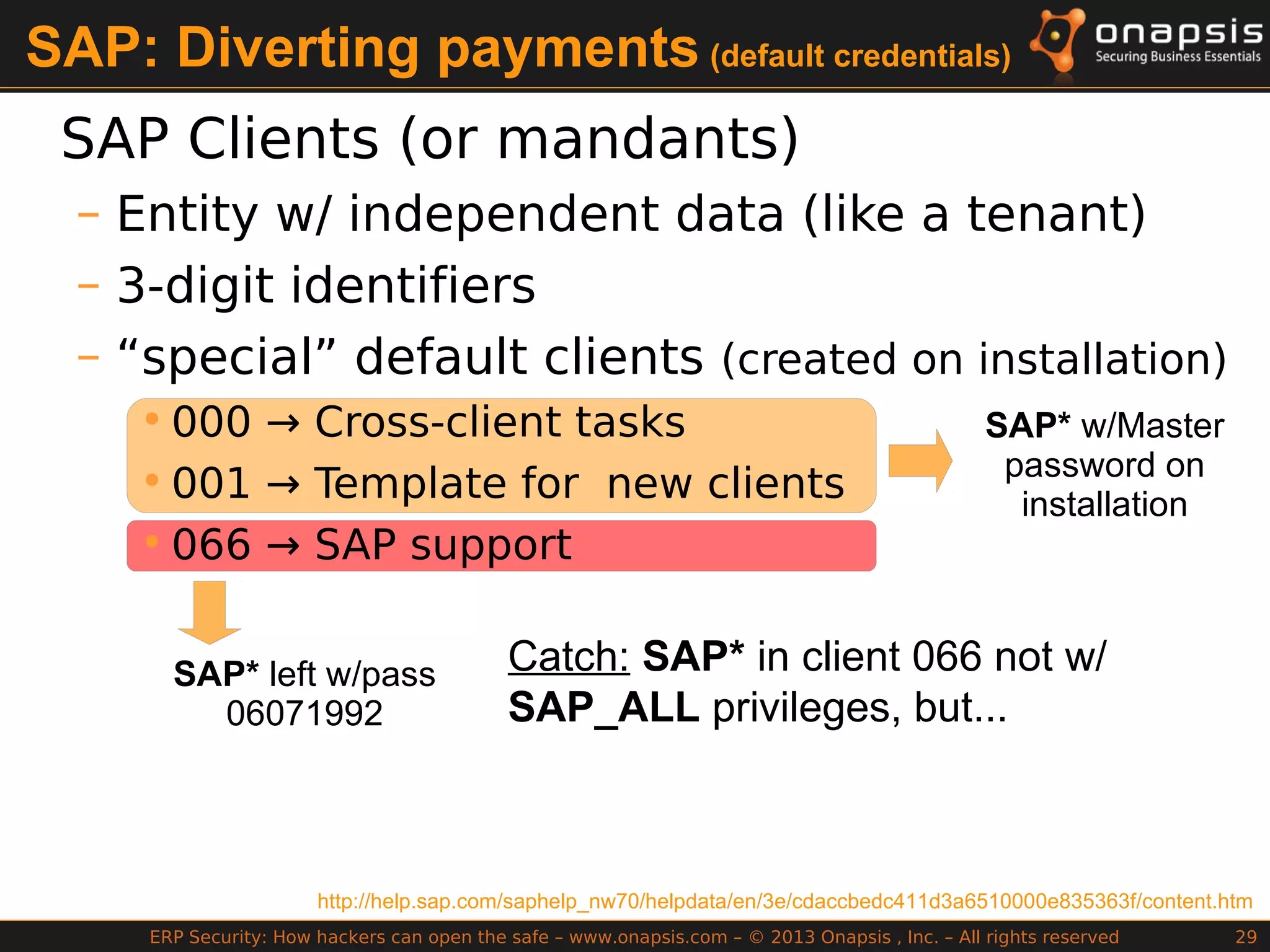
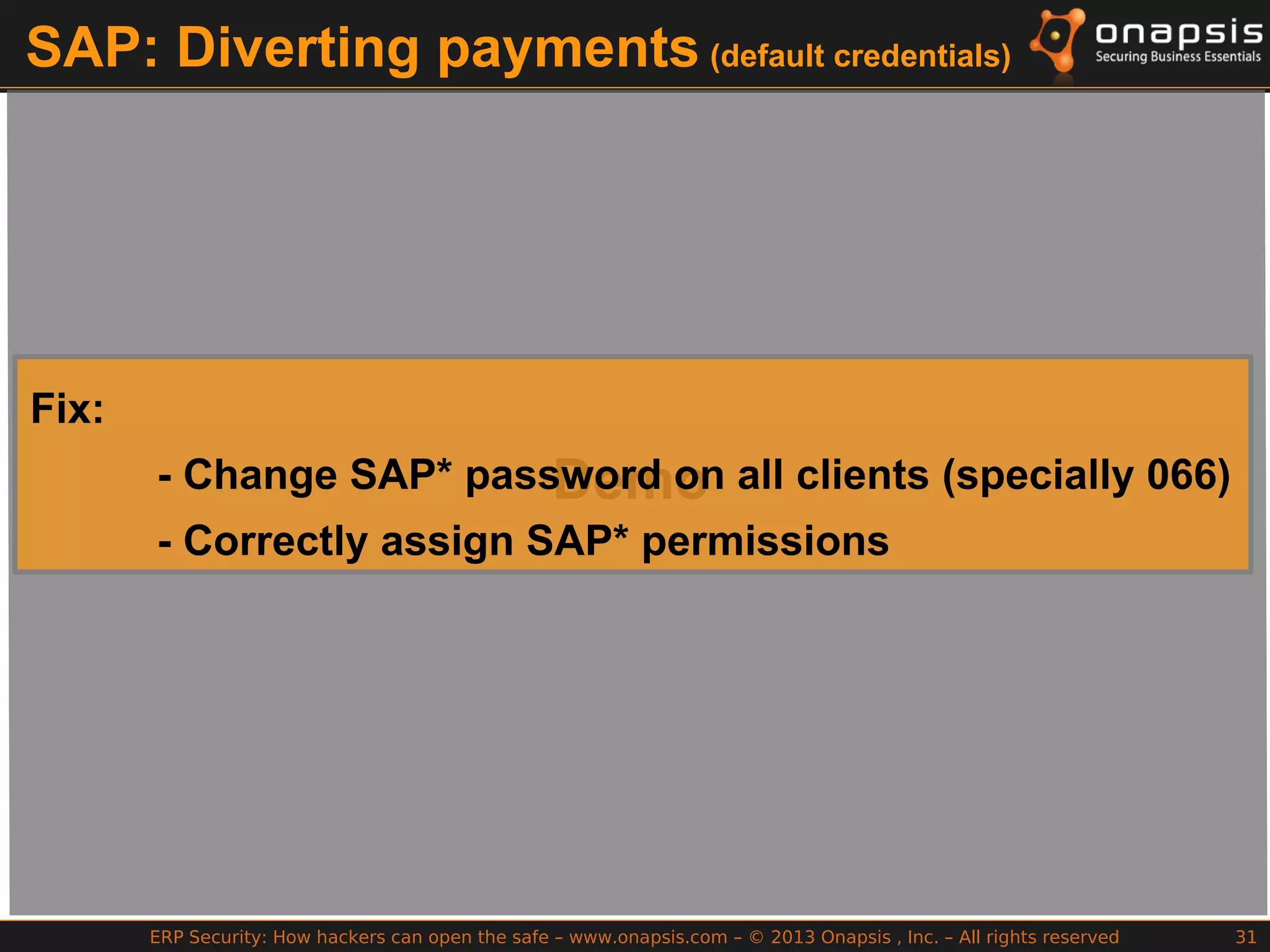
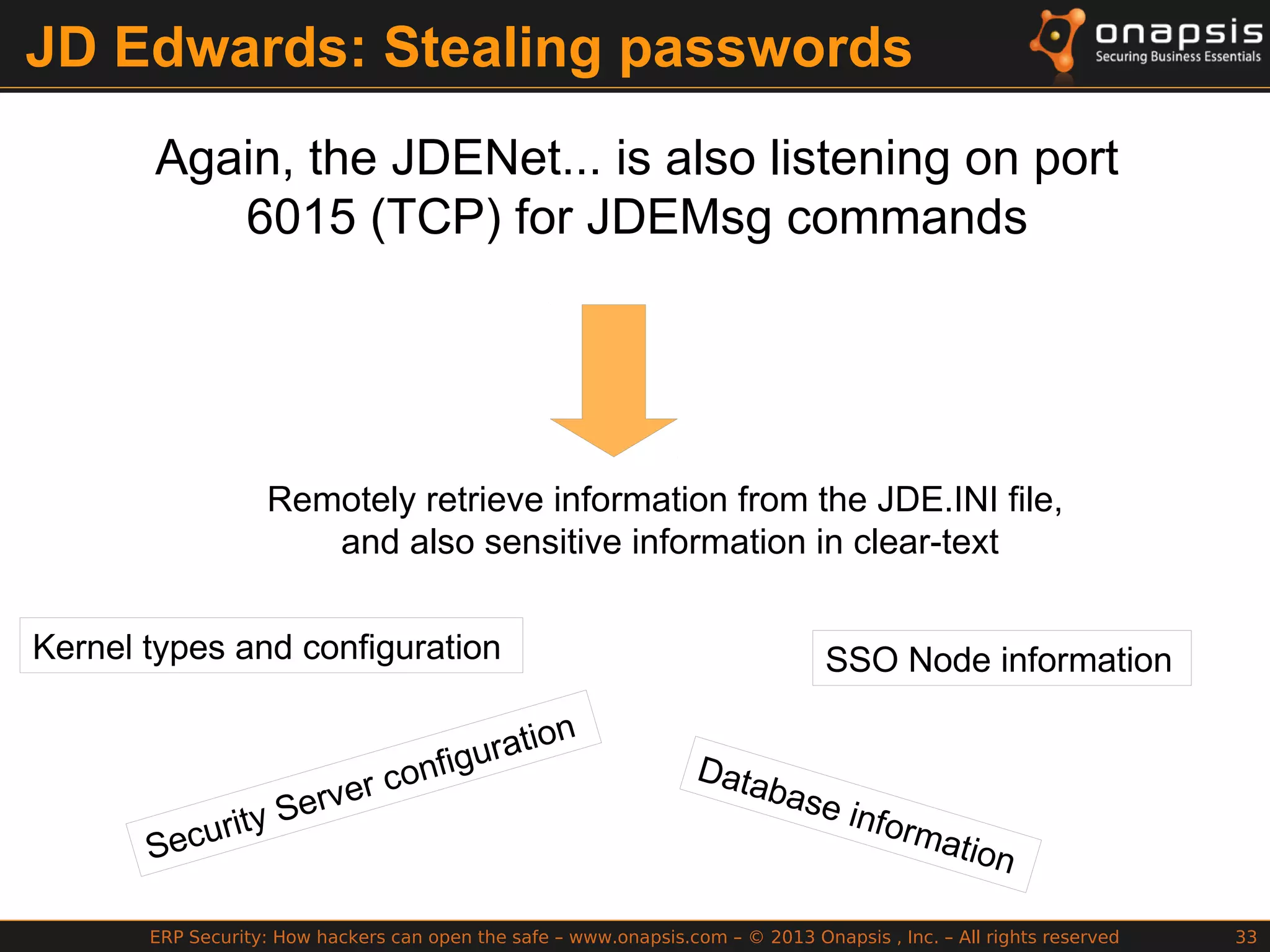
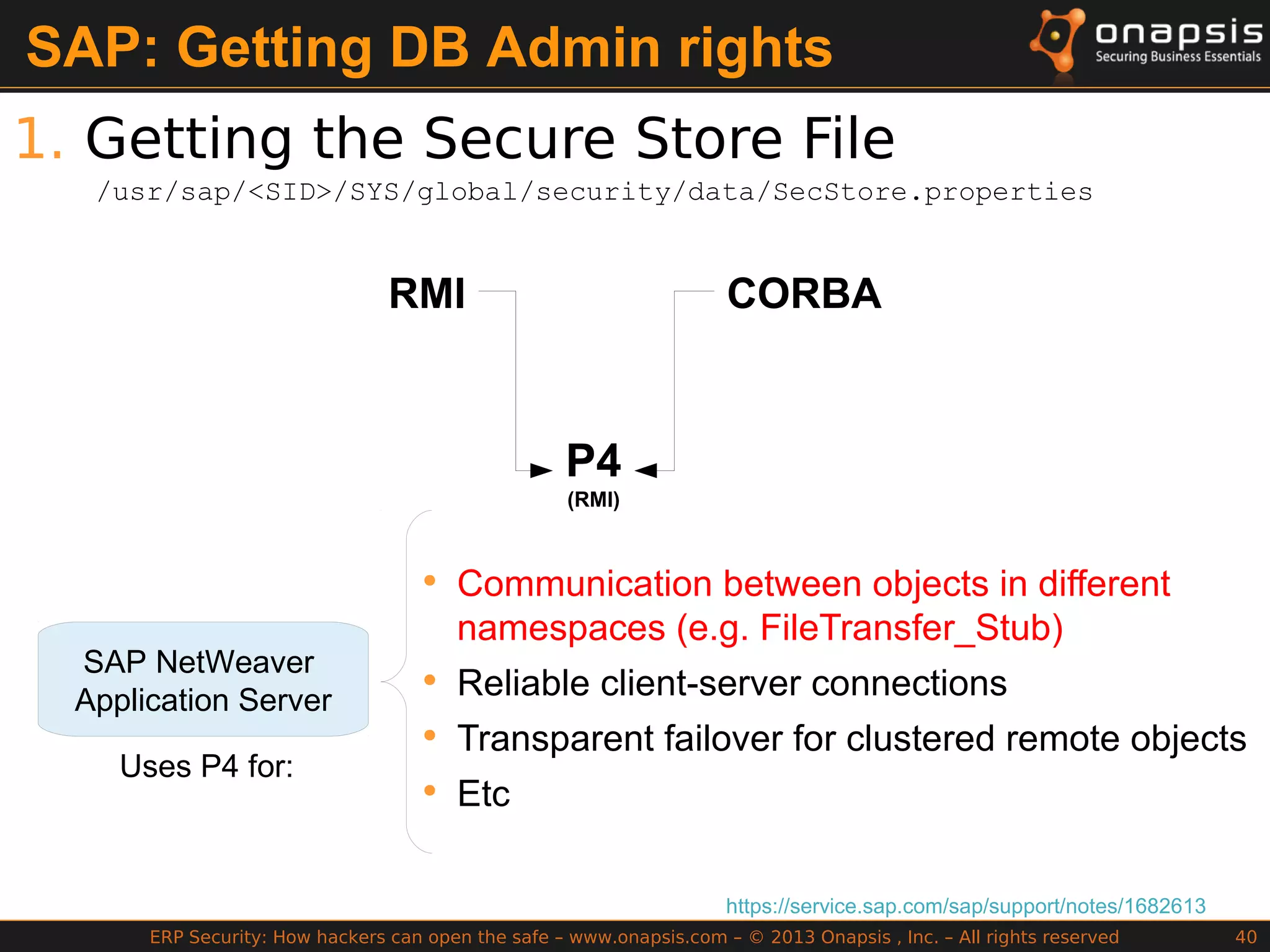
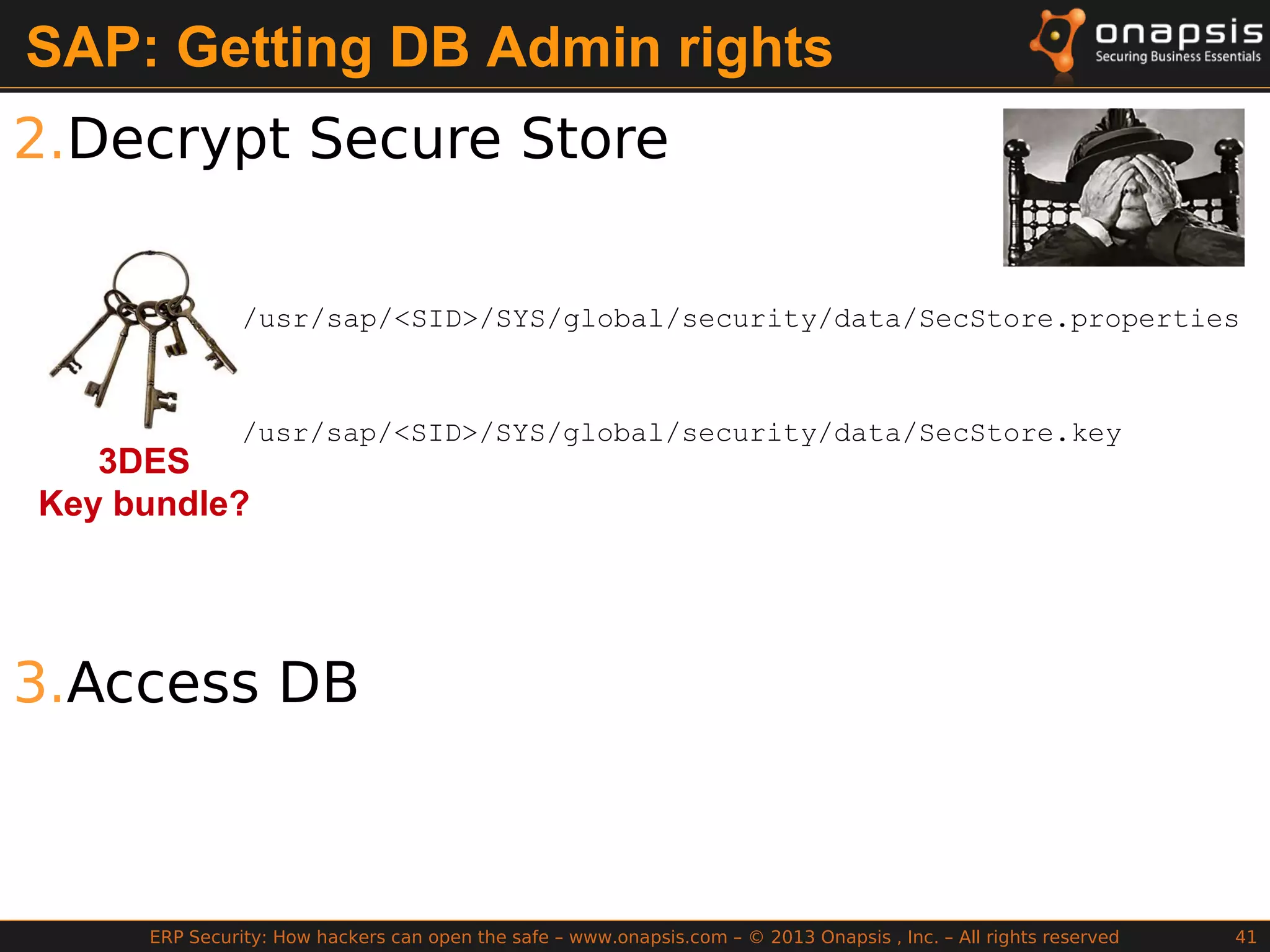
The document discusses the vulnerabilities in ERP systems that make them targets for cyberattacks, particularly focusing on methods employed by hackers to exploit these weaknesses. It outlines historical context, attack vectors, and various types of attacks such as sabotage, espionage, and fraud, highlighting their impact on business-critical processes and sensitive information. The document emphasizes the importance of improving ERP security practices due to the increasing focus on cyber threats since 2009.