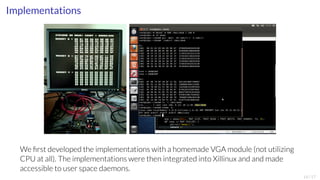
The document discusses various cryptographic advancements presented at conferences in 2014, including new authenticated encryption algorithms and their hardware implementation perspectives. It highlights the Caesar project, an international competition sponsored by NIST aimed at developing secure authenticated encryption methods. The focus is on efficient hardware designs, specifically system-on-chip implementations, and the challenges posed by integrating security in mobile devices and IoT applications.





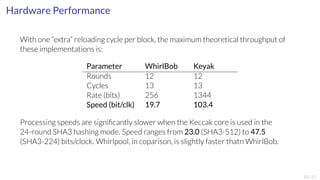
![Implementation 1: Keyak (SHA3 Keccak) Core
k1600_1
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
I0[63:0]
I1[63:0] t1[23]_i
O[63:0]
I0[63:0]
I1[63:0] t1[24]_i
O[63:0]
A[4:0] O[63:0]
k1600
clk
in[1599:0]
rnd[4:0]
out[1599:0]
keccak_rc_i
RTL_ROM
tp[0]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[0]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[0]1_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[0]2_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[1]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[1]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[1]1_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[1]2_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[2]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[2]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[2]1_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[2]2_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[3]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[3]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[3]1_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[3]2_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[4]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[4]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[4]1_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
tp[4]2_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[0]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[0]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[1]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[1]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[2]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[2]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[3]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[3]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[4]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[4]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[5]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[5]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[6]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[6]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[7]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[7]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[8]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[8]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[9]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[9]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[10]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[10]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[11]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[11]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[12]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[12]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[13]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[13]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[14]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[14]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[15]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[15]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[16]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[16]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[17]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[17]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[18]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[18]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[19]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[19]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[20]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[20]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[21]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[21]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t1[22]_i
RTL_XOR
I0[63:0]
I1[63:0]
t1[22]0_i
O[63:0]
RTL_XOR
RTL_XOR
I0[63:0]
I1[63:0]
t1[23]0_i
O[63:0]
RTL_XOR
RTL_XOR
I0[63:0]
I1[63:0]
t1[24]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t3[0]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
O[63:0]
O[63:0]
O[63:0]
O[63:0]
t3[0]0_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t3[0]0_i__0
RTL_AND
I1[63:0]
I0[63:0]
t3[1]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t3[1]0_i
RTL_AND
I1[63:0]
I0[63:0]
t3[2]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t3[2]0_i
RTL_AND
I1[63:0]
I0[63:0]
t3[3]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t3[3]0_i
RTL_AND
I1[63:0]
I0[63:0]
t3[4]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t3[4]0_i
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[5]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t3[5]0_i
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[6]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t3[6]0_i
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[7]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t3[7]0_i
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[8]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t3[8]0_i
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[9]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t3[9]0_i
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[10]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t3[10]0_i
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[11]_i
O[63:0]
RTL_XOR
I0[63:0]
t3[11]0_i I1[63:0]
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[12]_i
O[63:0]
RTL_XOR
I0[63:0]
t3[12]0_i I1[63:0]
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[13]_i
O[63:0]
RTL_XOR
I0[63:0]
t3[13]0_i I1[63:0]
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[14]_i
O[63:0]
RTL_XOR
I0[63:0]
t3[14]0_i I1[63:0]
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[15]_i
O[63:0]
RTL_XOR
I0[63:0]
t3[15]0_i I1[63:0]
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[16]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t3[16]0_i
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[17]_i
O[63:0]
RTL_XOR
I0[63:0]
t3[17]0_i I1[63:0]
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[18]_i
O[63:0]
RTL_XOR
I0[63:0]
t3[18]0_i I1[63:0]
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[19]_i
O[63:0]
RTL_XOR
I0[63:0]
t3[19]0_i I1[63:0]
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[20]_i
O[63:0]
RTL_XOR
I0[63:0]
t3[20]0_i I1[63:0]
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[21]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t3[21]0_i
I1[63:0]
O[63:0]
I0[63:0] t3[22]_i
RTL_AND
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t3[22]0_i
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[23]_i
O[63:0]
RTL_XOR
I0[63:0]
I1[63:0]
t3[23]0_i
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
t3[24]_i
O[63:0]
RTL_XOR
I0[63:0]
t3[24]0_i I1[63:0]
O[63:0]
RTL_AND
I1[63:0]
I0[63:0]
63:0
Single round of Keccak/Keyak 1600-bit
core permutation drawn with 64-bit
data paths. Mainly XORs visible.
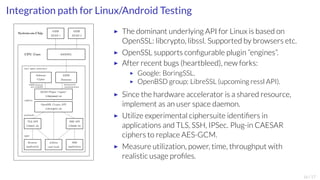
SHA3 algorithm Keccak and Keyak AEADs:
▶ Keccak is a sponge hash with a 1600-bit core
permutation, selected as SHA3 in 2012.
▶ Designed by Guido Bertoni, Joan Daemen,
Michaël Peeters, and Gilles Van Assche.
▶ Same team proposed the Keyak family of
AEADs that utilize the same permutation in the
CAESAR project.
We implemented:
▶ The 1600-bit core in Verilog for the Artix-7
FPGA core of Zynq 7000.
▶ The module can be utilized for both hashing and
authenticated encryption.
8/17](https://image.slidesharecdn.com/saehitalk-141031073345-conversion-gate02/85/Simple-AEAD-Hardware-Interface-SAEHI-in-a-SoC-Implementing-an-On-Chip-Keyak-WhirlBob-Coprocessor-8-320.jpg)