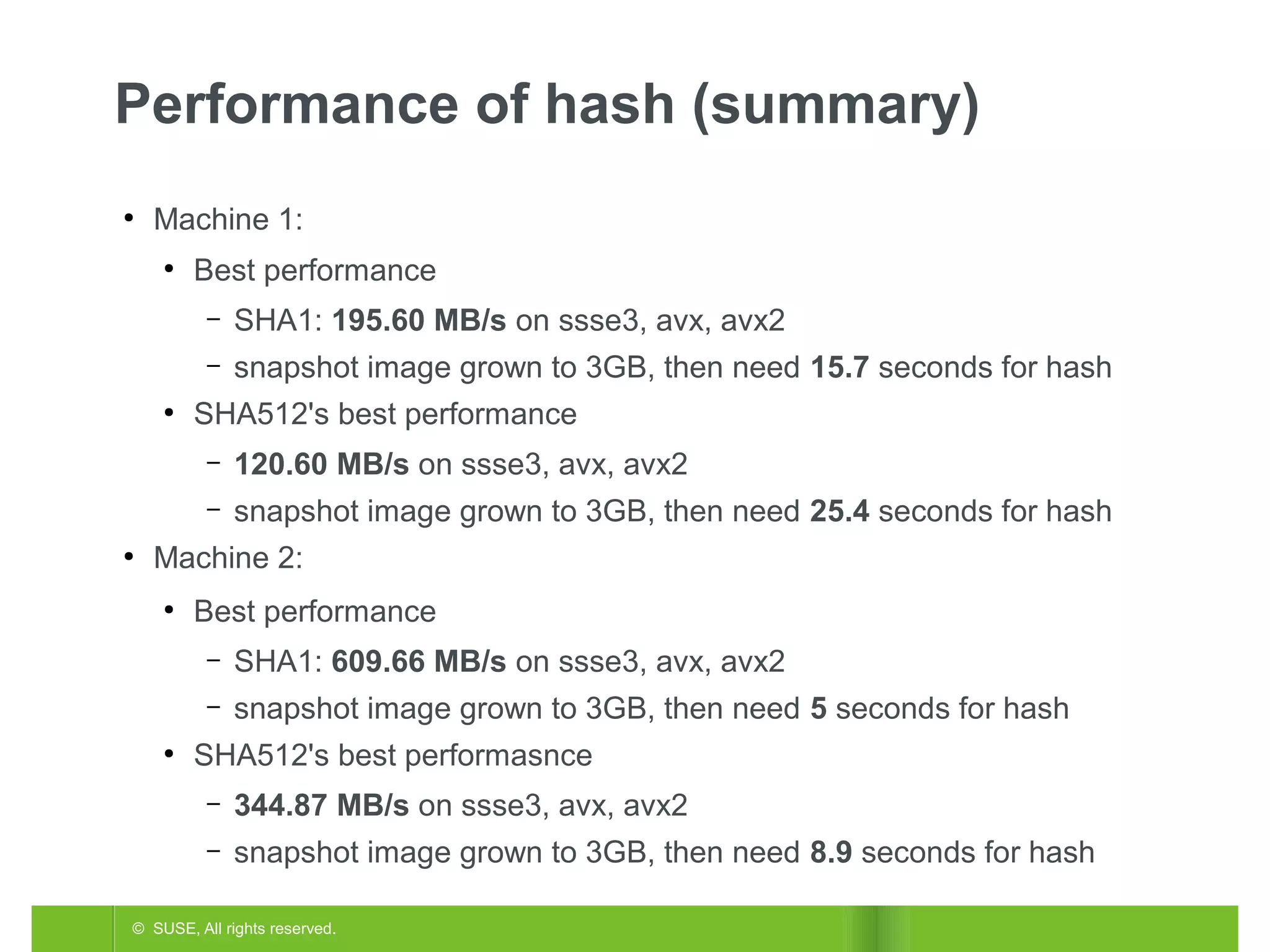
The document discusses securing hibernation snapshots on machines with UEFI secure boot enabled. It proposes using the shim bootloader to generate a key pair, with the private key stored in an EFI variable and passed to the kernel to sign hibernation snapshots. When restoring from hibernation, the kernel would verify the signature using the public key. Performance tests on hash algorithms like SHA-1 and SHA-512 are also presented.



![EFI variable name and GUID
●
GUID:
●
●
S4SignKey [BT][NV]→ private key
●
●
fe141863-c070-478e-b8a3-878a5dc9ef21
PKCS#8 _uncompressed_ private key format
S4WakeKey [RT][V] → public key
●
X.509 format
© SUSE, All rights reserved.](https://image.slidesharecdn.com/s4-sig-check-lpc-20130918-131226003618-phpapp02/75/S4-sig-check-lpc-20130918-7-2048.jpg)
![When shim should generate keys?
●
●
When system boot, and shim didn't find key-pair
When shim found GenS4Key EFI variable from
kernel:
●
●
●
GenS4Key-fe141863-c070-478e-b8a3878a5dc9ef21
[RT][NV]
Kernel or userspace write GenS4Key
variable to '1' when hibernate launched.
Kernel will delete GenS4Key in system boot.
© SUSE, All rights reserved.](https://image.slidesharecdn.com/s4-sig-check-lpc-20130918-131226003618-phpapp02/75/S4-sig-check-lpc-20130918-8-2048.jpg)
![Patch status
●
V4 RFC patches sent to kernel upstream and openSUSE kernel for
reviewing:
●
●
●
[RFC V4 PATCH 00/15] Signature verification of hibernate snapshot
https://lkml.org/lkml/2013/9/14/183
Following kernel experts gave suggestions:
●
Hibernate
●
Matt Fleming <matt@console-pimps.org>
EFI
●
●
Pavel Machek <pavel@ucw.cz>
Dmitry Kasatkin <dmitry.kasatkin@gmail.com>
Asymmetric keys
Followed Pavel and Matt's suggestions, already fix in V2, V3 patches
© SUSE, All rights reserved.](https://image.slidesharecdn.com/s4-sig-check-lpc-20130918-131226003618-phpapp02/75/S4-sig-check-lpc-20130918-14-2048.jpg)