This document provides an introduction to SQL Server databases including:
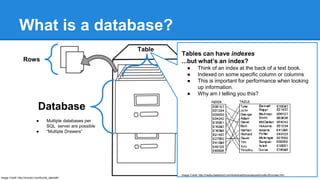
- What a database is and the key components of tables, rows, and indexes.
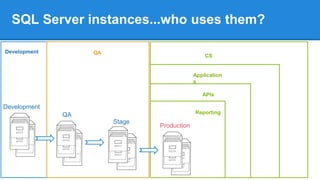
- How multiple SQL Server instances and databases can exist per server.
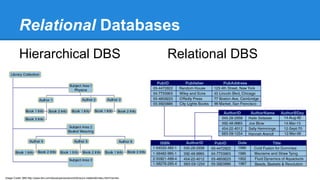
- An overview of relational databases and how they differ from hierarchical databases.
- Examples of how SQL Server instances may be used for different environments like development, QA, and production.
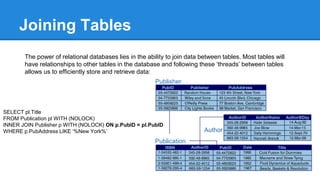
- A brief introduction to SQL including the main command categories and focusing on SELECT statements.
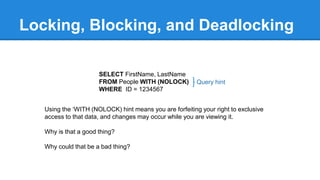
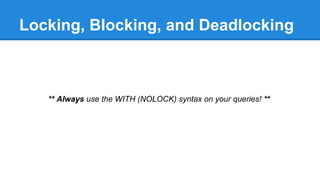
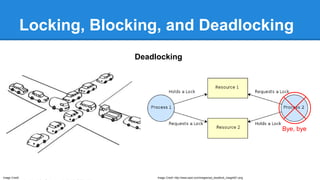
- Discussions around locking, blocking, deadlocking and how to avoid issues.
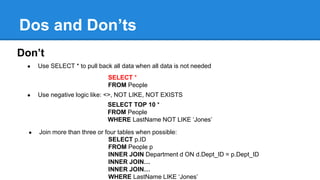
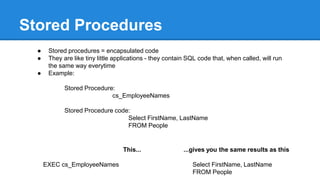
- Tips for writing efficient queries including best practices around joins, stored procedures, and data policies.