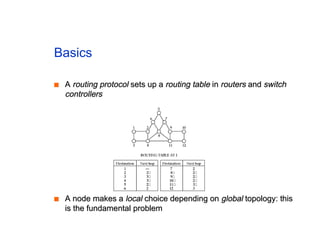
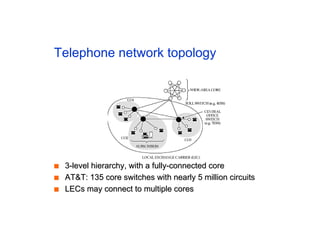
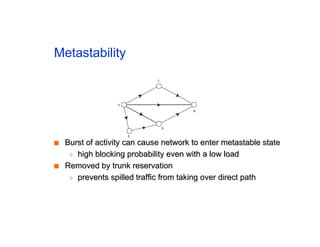
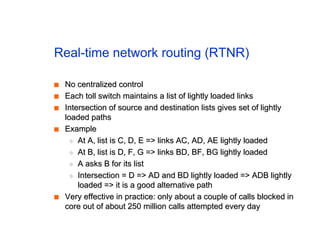
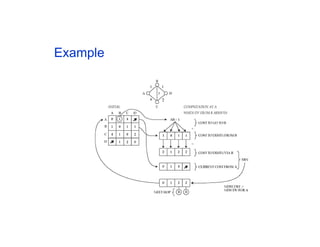
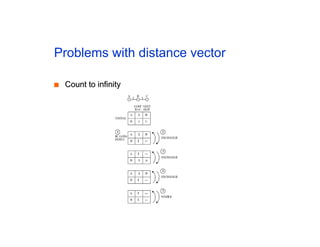
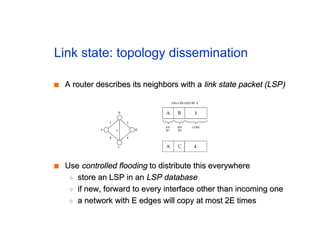
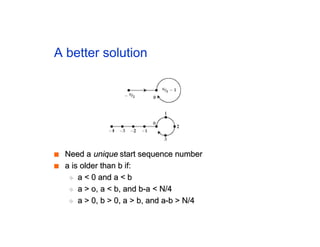
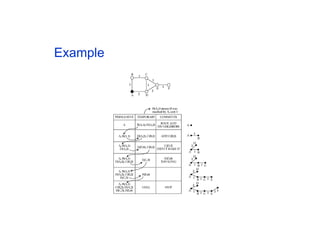
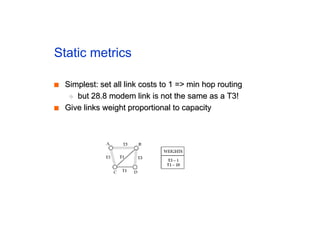
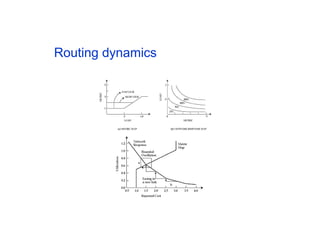
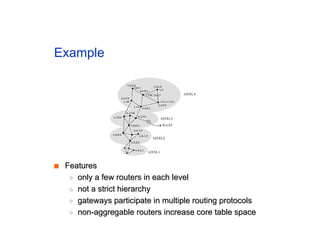
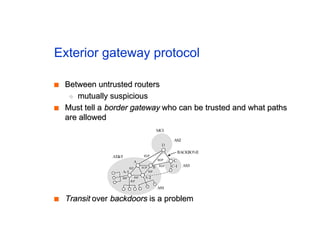
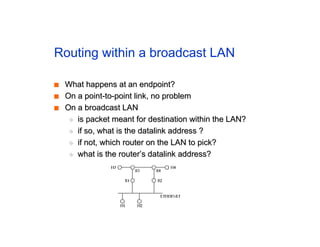
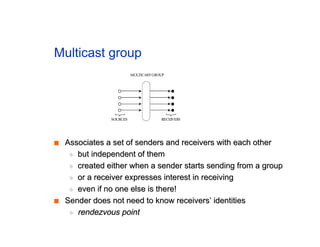
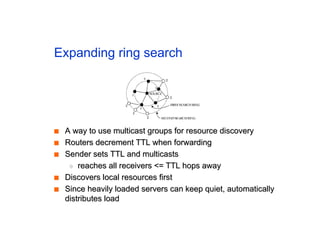
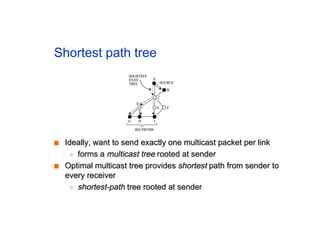
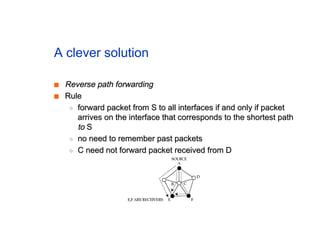
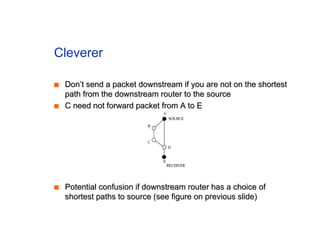
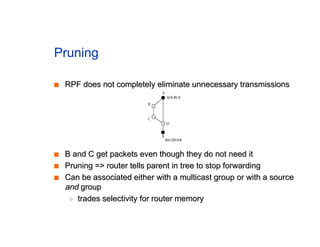
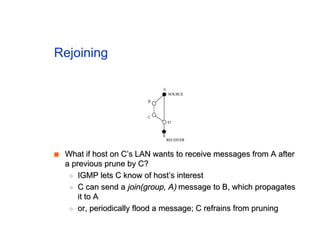
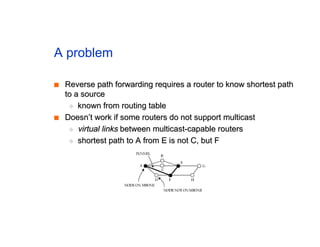
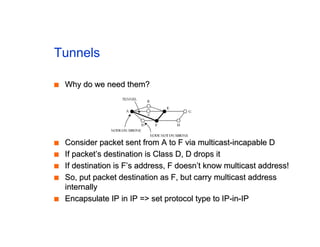
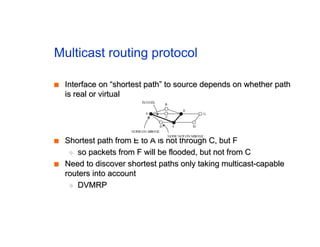
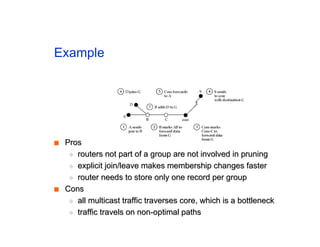
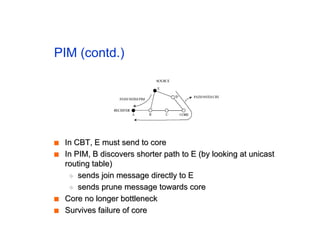
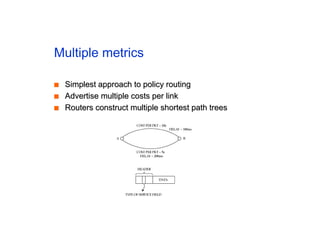
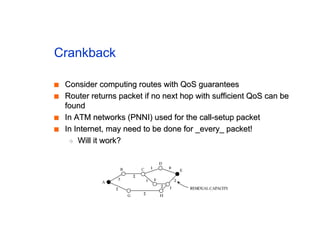
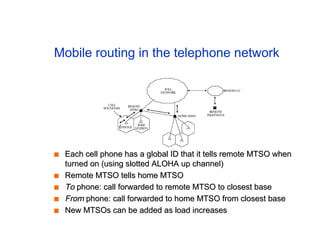
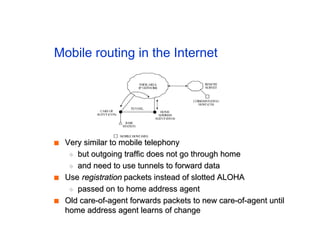
The document discusses the process of routing in computer networking, explaining how a routing protocol sets up routing tables in routers to determine the best paths between network nodes. It highlights key concepts such as centralized vs. distributed routing, distance-vector vs. link-state routing, and dynamic non-hierarchical routing. Additionally, it addresses challenges like network failures, load balancing, and the importance of maintaining accurate topology information for effective routing.