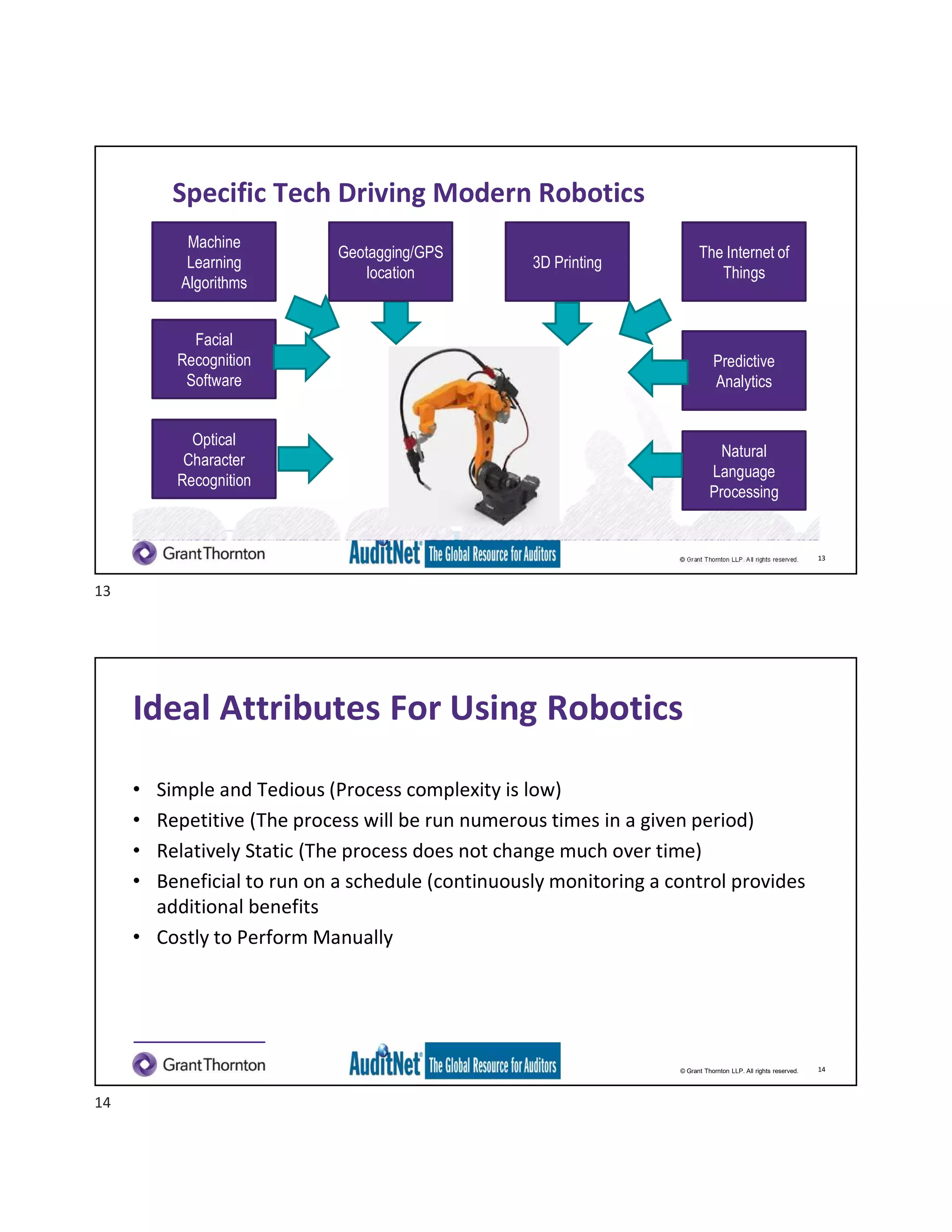
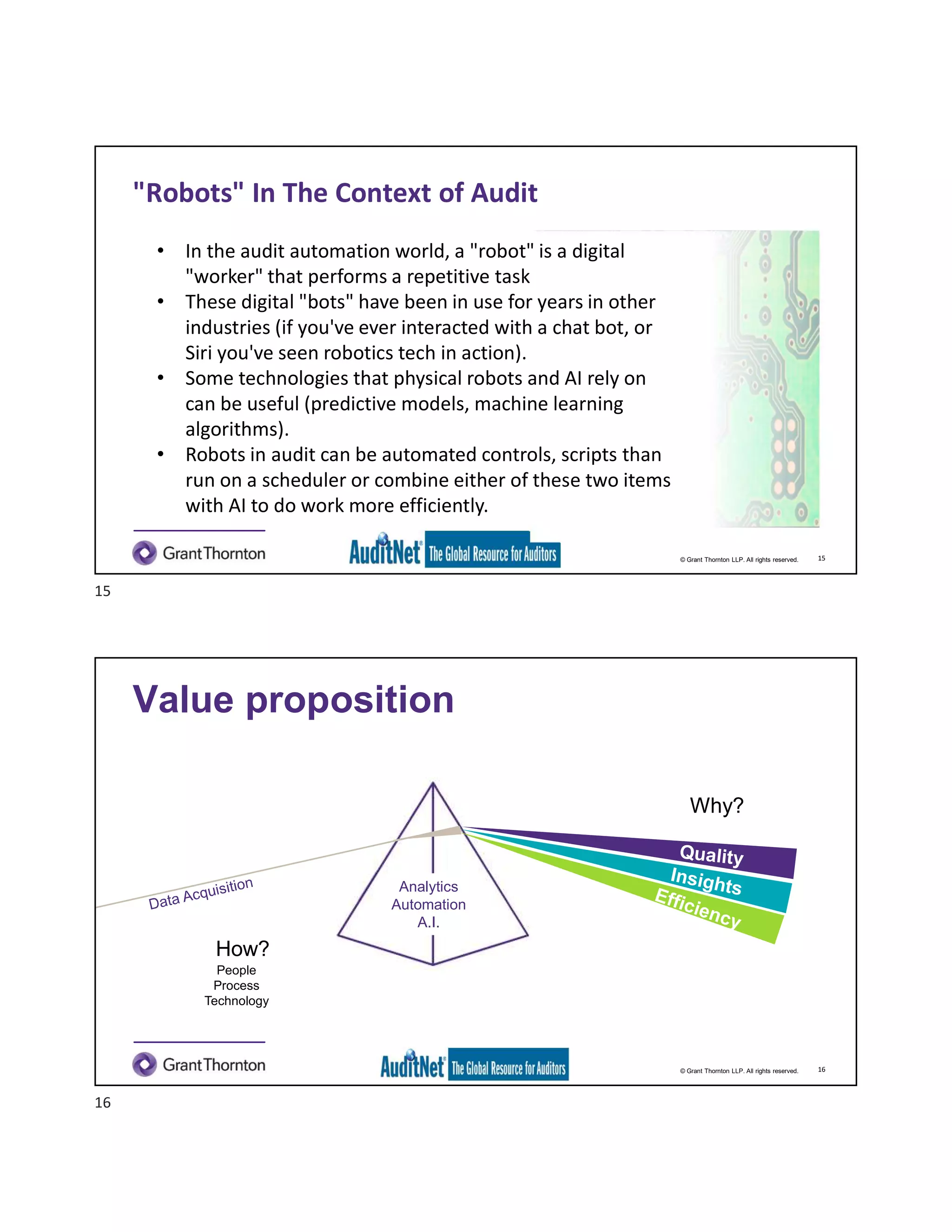
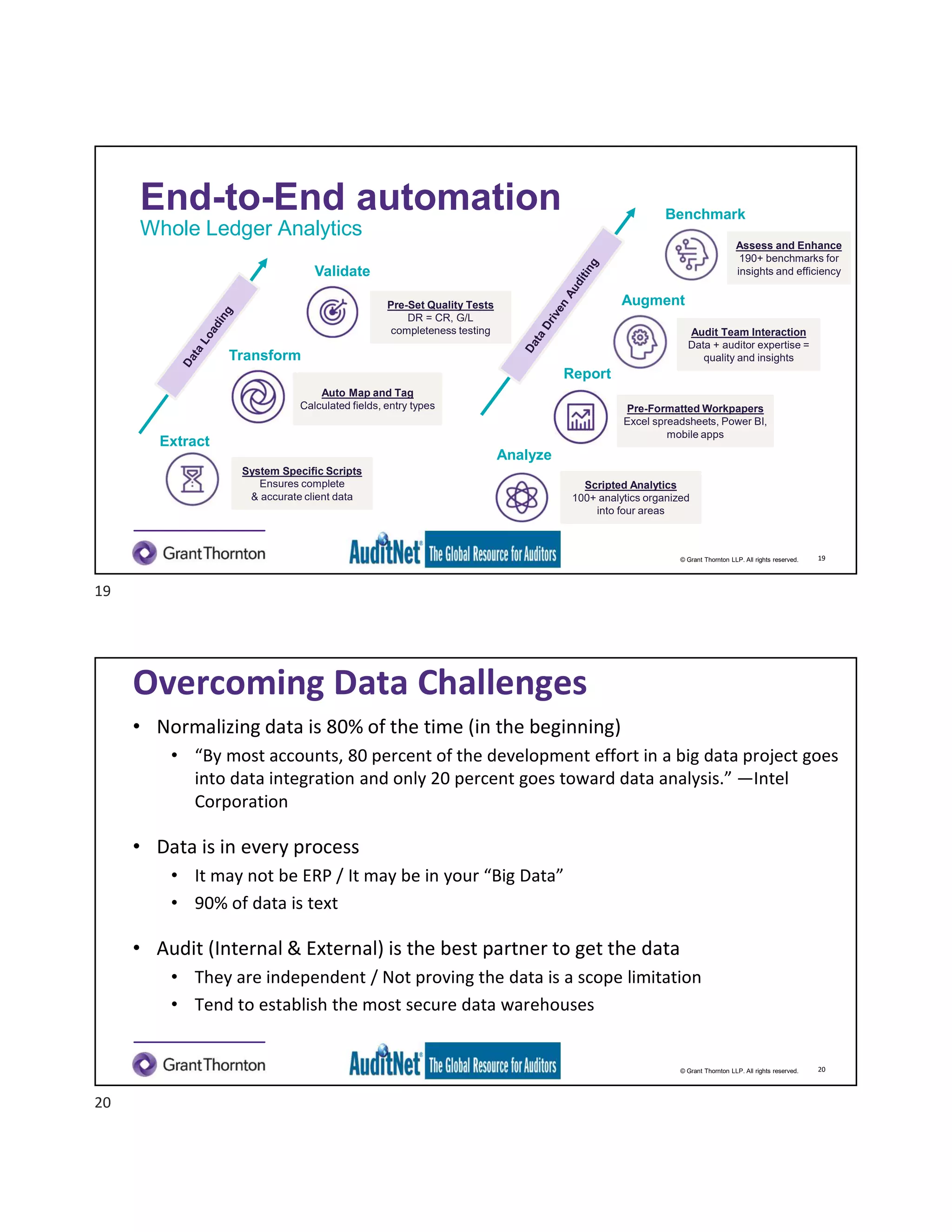
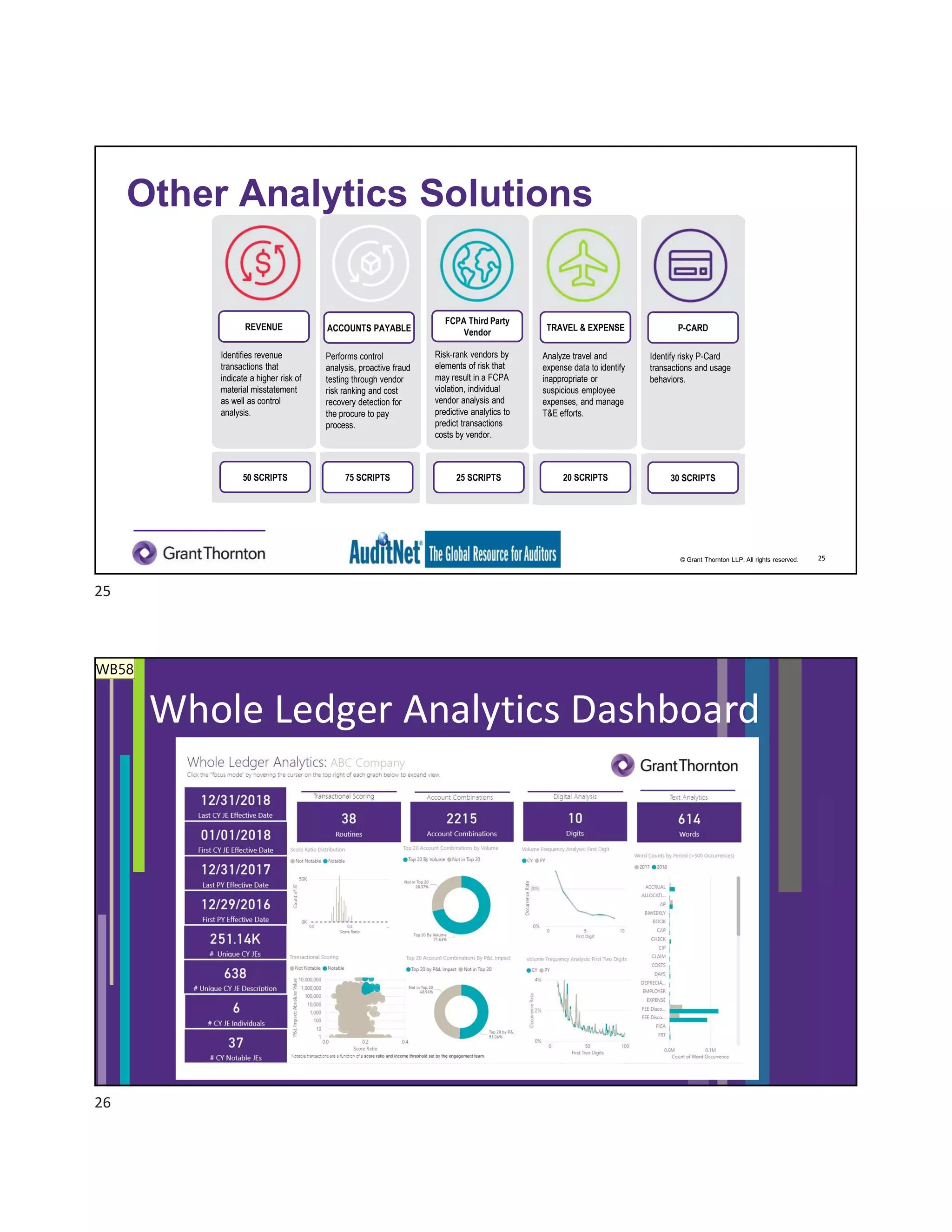
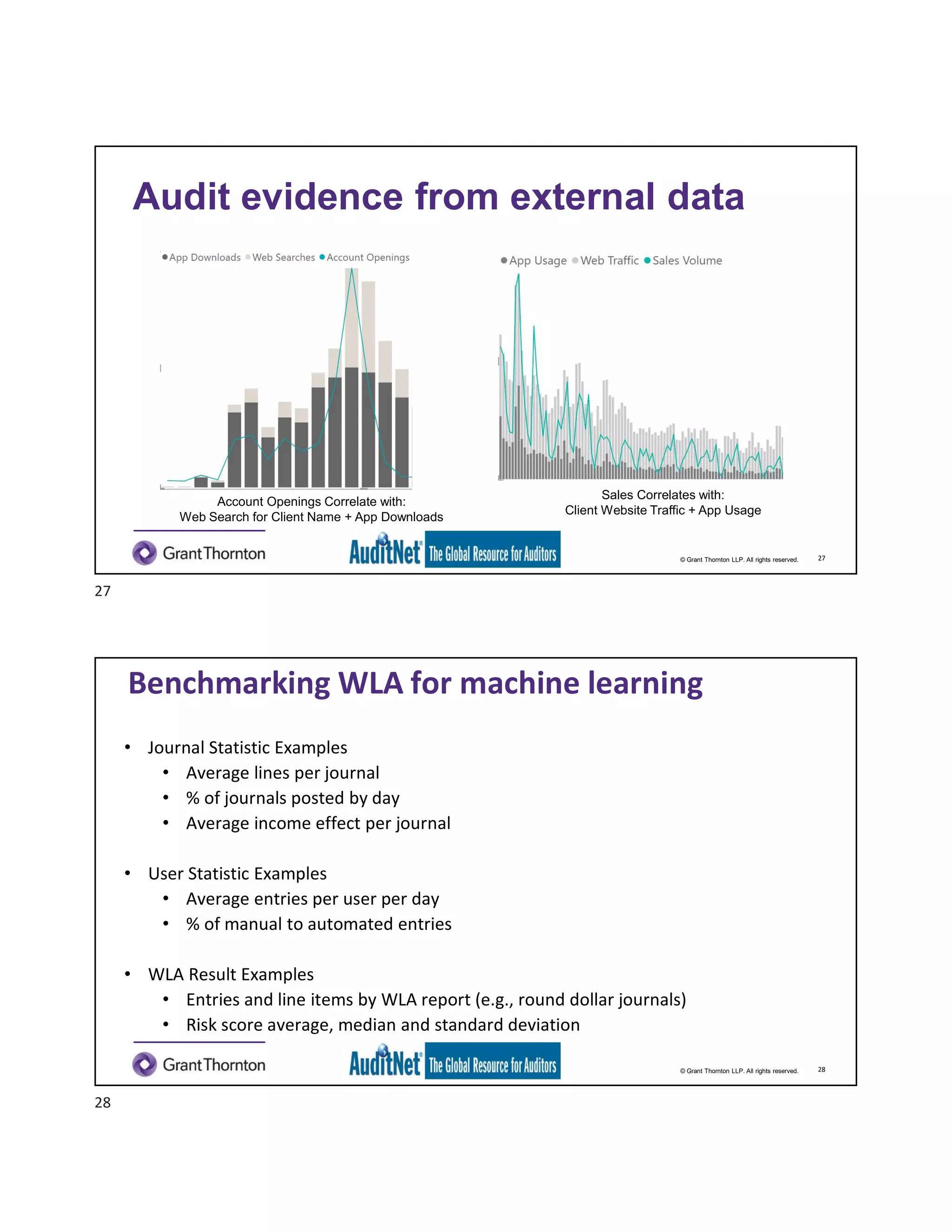
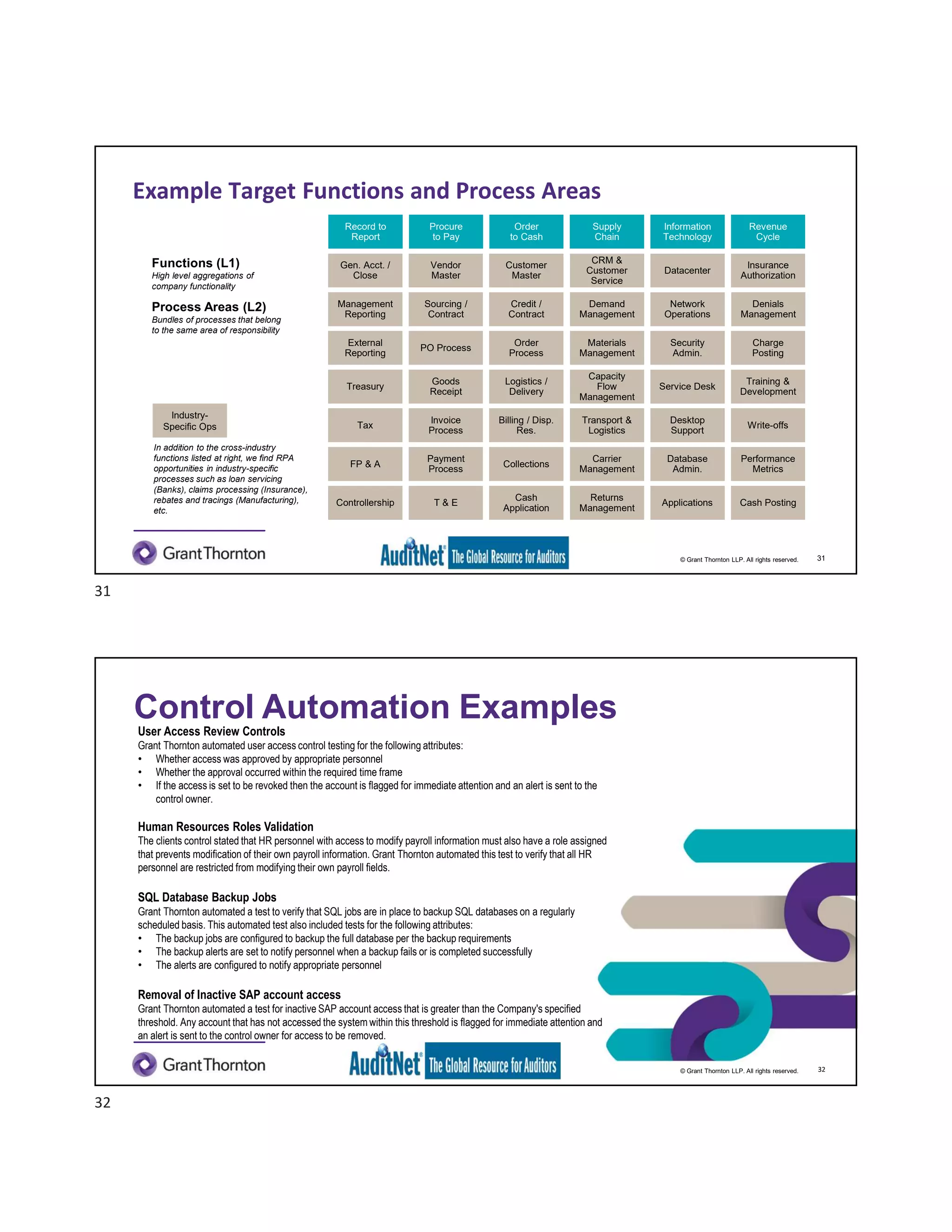
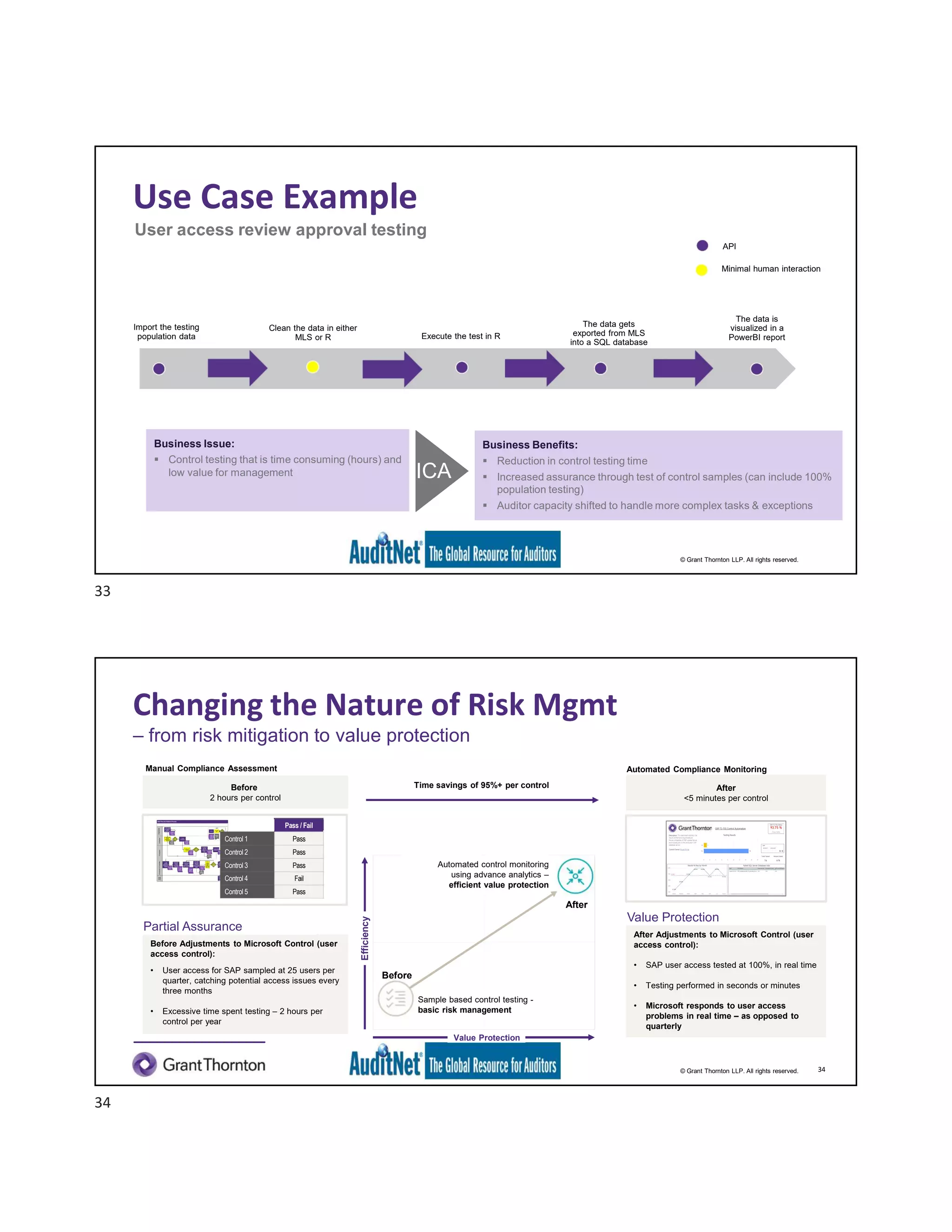
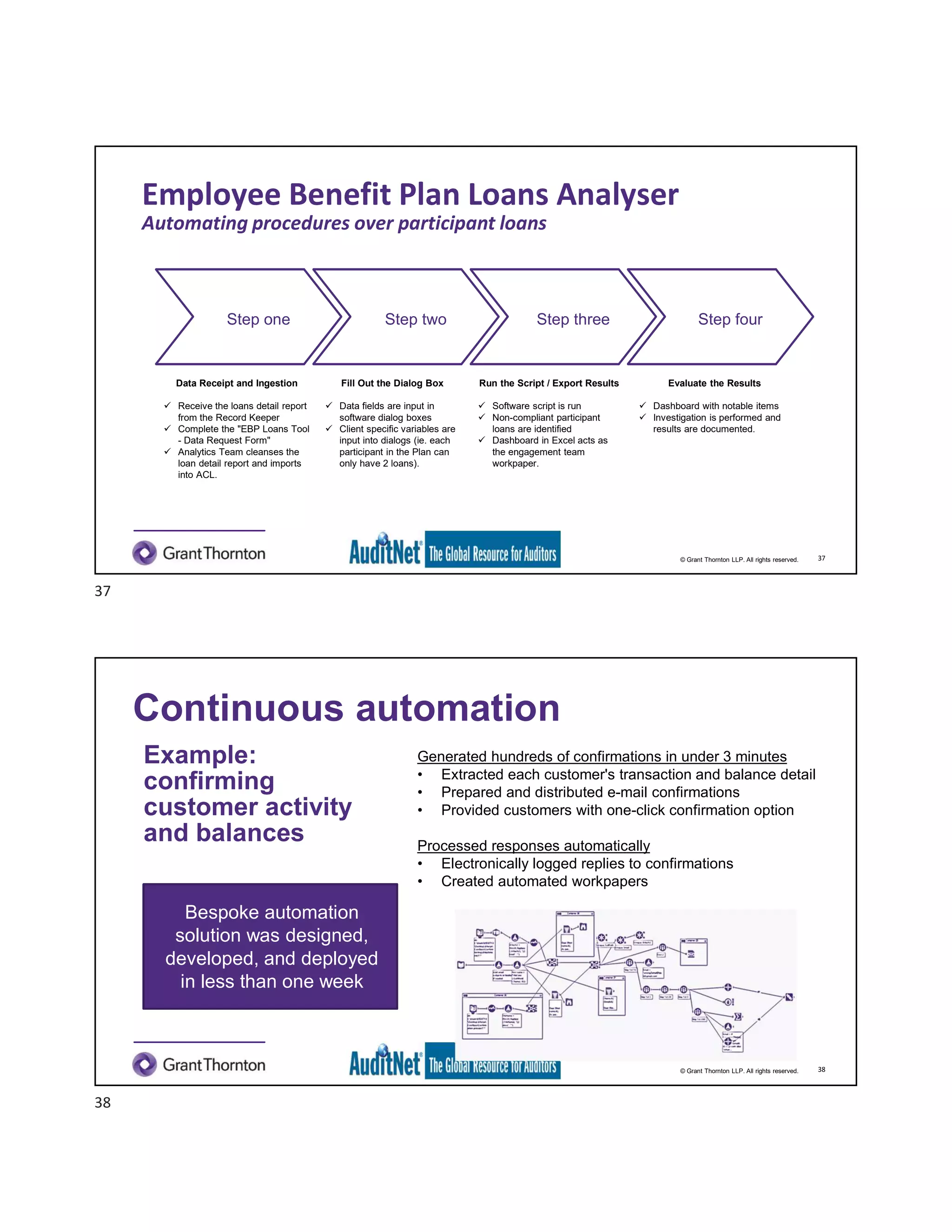
The document discusses the role of robotic process automation (RPA) in auditing, emphasizing its potential to enhance efficiency and accuracy in audit processes. It highlights the features of AuditNet, a global resource for auditors, and outlines training and certification opportunities related to RPA. Additionally, it provides insights into the practical applications of RPA in various auditing functions, alongside the benefits and challenges of integrating technology into auditing tasks.