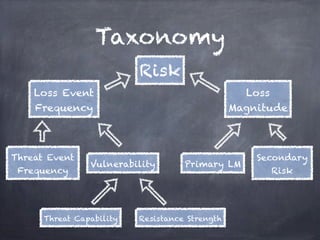
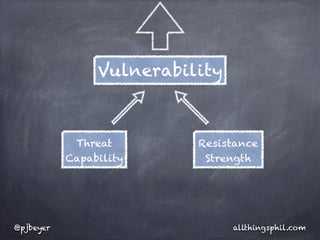
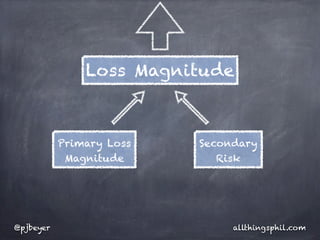
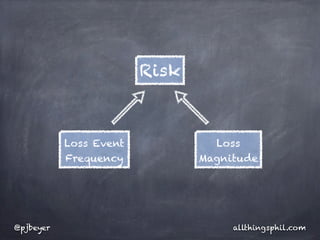
The document discusses risk analysis in the context of information security, emphasizing the components of threats, vulnerabilities, and risks. It highlights the importance of understanding asset risk and deriving risk values based on probability, frequency, and magnitude. Additionally, it critiques approaches to risk assessment that rely solely on best practices without a repeatable framework.