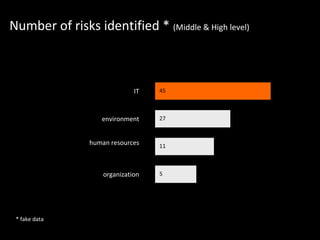
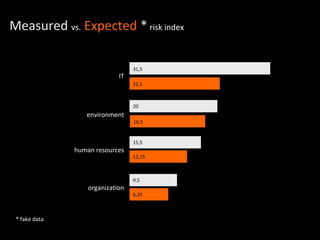
The document discusses performing a risk assessment on information security. The goals are to identify risk factors in sensitive IT processes, organizational structure, human resources, and the environment. Risks are then classified and assigned information values related to data integrity, confidentiality, and availability. The document outlines estimating the probability and potential damages of bad events, and determining risk levels. It recommends establishing mitigation actions to reduce risk levels.