Right-sized security for IoT - ARM
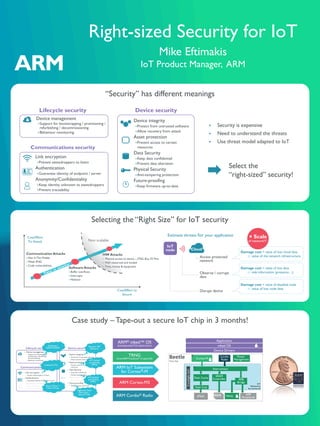
- 1. Right-sized Security for IoT Mike Eftimakis IoT Product Manager, ARM Case study – Tape-out a secure IoT chip in 3 months! Selecting the “Right Size” for IoT security HW Attacks Physical access to device – JTAG, Bus, IO Pins Well resourced and funded Time, money & equipmentSoftware Attacks Buffer overflows Interrupts Malware Communication Attacks Man In The Middle Weak RNG Code vulnerabilities Cost/Effort To Attack Cost/Effort to Secure Non scalable IoT Subsystem for Cortex-M eFlash Interconnect Flash Cache eFlash Flash Cntl SRAM Controller APB PeripheralsSRAMSRAMSRAMSRAM ProcessorCortex-M CoreSightSoC mbed OS Device Drivers Application Beetle Test chip Power Management TRNG APB Bridge Cordio Radio ARM® mbed™ OS (including mbedTLS, mbed uVisor) TRNG (from ARM TrustZone® CryptoCell) ARM IoT Subsystem for Cortex®-M ARM Cortex-M3 ARM Cordio® Radio Device management Support for bootstrapping / provisioning / refurbishing / decommissioning Behaviour monitoring Device integrity Protect from untrusted software Allow recovery from attack Asset protection Prevent access to certain resources Data Security Keep data confidential Prevent data alteration Physical Security Anti-tampering protection Future-proofing Keep firmware up-to-date Device security Communications security Lifecycle security Link encryption Prevent eavesdroppers to listen Authentication Guarantee identity of endpoint / server Anonymity/Confidentiality Keep identity unknown to eavesdroppers Prevent traceability Implement OMA LWM2M ImplementTLS Root of Trust + Chain ofTrust HW backed partitioning (MPU) Implement Dual Flash bank + Secure FoTA HW backed partitioning (MPU) Partition SW Resource IoT node Cloud Disrupt device Observe / corrupt data Access protected network Damage cost = value of lost data or side information (presence…) Damage cost = value of lost cloud data or value of the network infrastructure Damage cost = value of disabled node or value of lost node data × Scale of network!!! Estimate threats for your application “Security” has different meanings Device management Support for bootstrapping / provisioning / refurbishing / decommissioning Behaviour monitoring Device integrity Protect from untrusted software Allow recovery from attack Asset protection Prevent access to certain resources Data Security Keep data confidential Prevent data alteration Physical Security Anti-tampering protection Future-proofing Keep firmware up-to-date Device security Communications security Lifecycle security Link encryption Prevent eavesdroppers to listen Authentication Guarantee identity of endpoint / server Anonymity/Confidentiality Keep identity unknown to eavesdroppers Prevent traceability Select the “right-sized” security! Security is expensive Need to understand the threats Use threat model adapted to IoT