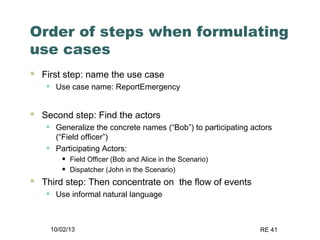
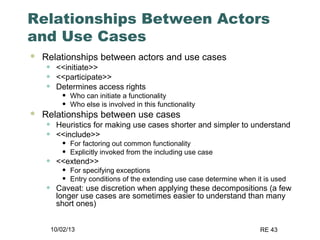
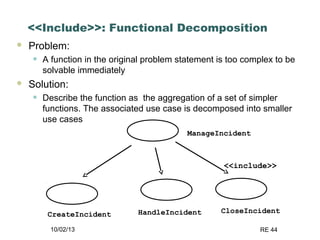
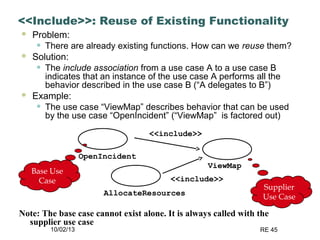
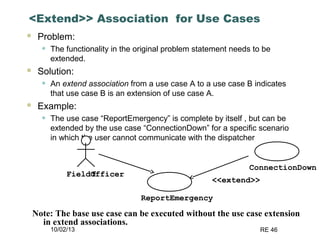
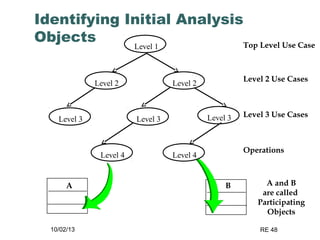
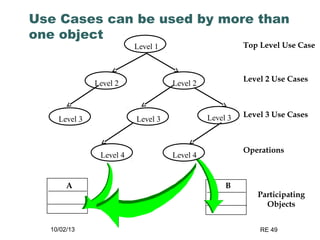
The document discusses requirements elicitation techniques. It describes requirements elicitation as identifying the needs of users and stakeholders to communicate to developers. Effective techniques include interviews, requirements workshops, brainstorming, storyboards, use cases, role playing and prototyping. Requirements elicitation faces problems of scope, understanding, and volatility. Scope issues include unclear boundaries and unnecessary design data. Understanding challenges involve incomplete user needs, communication gaps between users and analysts, and differing views. Requirements also tend to change over time.






























![10/02/13 RE 37
Identifying Scenarios
Scenario
• “A narrative description of what people do and experience as they
try to make use of computer systems and applications” [Carrol,
Scenario-based Design, 1995]
• Informal description of a single feature from the viewpoint of a
single actor
Types of Scenarios
• As-is scenarios – describes current situation
• Visionary scenarios – describes future system
• Evaluation scenarios – describes user tasks for evaluating the
system (acceptance criteria)
• Training scenarios – introduces new users to the system](https://image.slidesharecdn.com/requirementselicitation-131001224904-phpapp02/85/Requirements-elicitation-37-320.jpg)