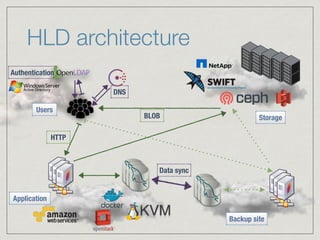
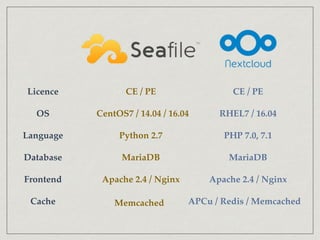
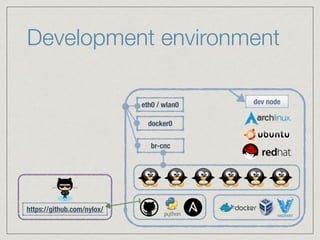
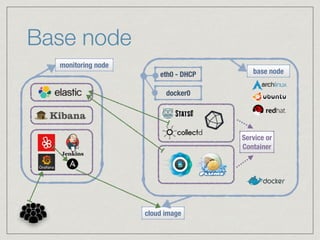
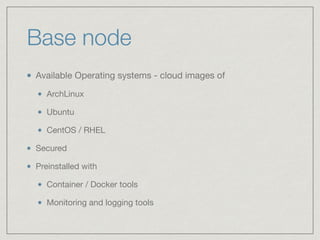
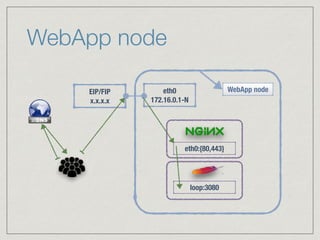
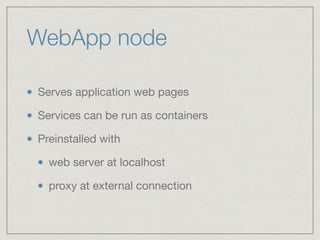
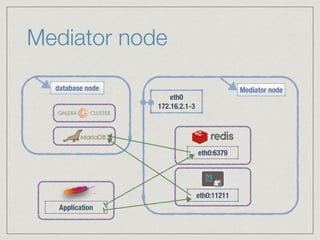
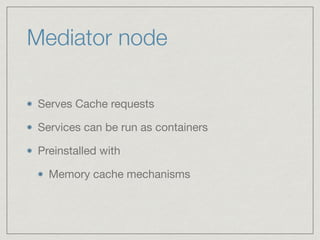
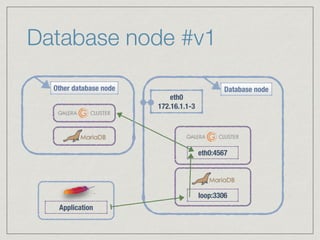
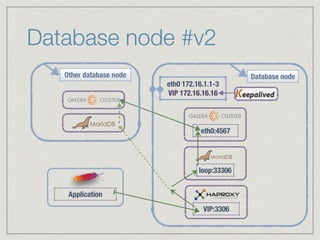
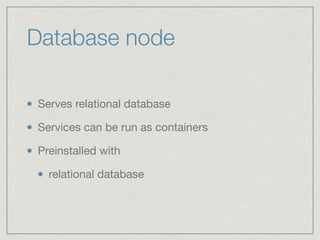
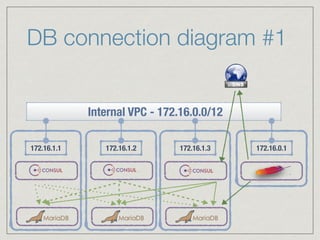
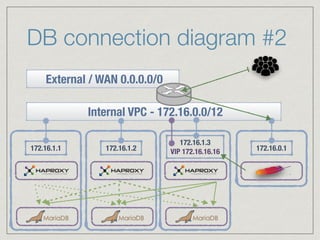
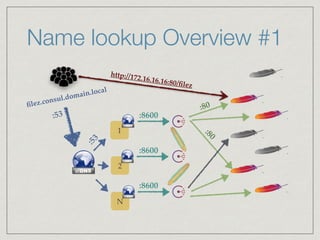
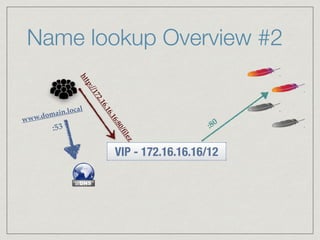
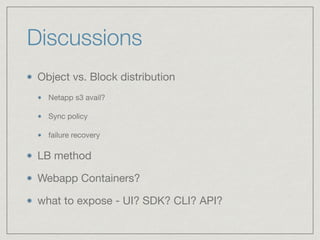
The document outlines the architecture for a remote secured storage application including various technical specifications such as required software, database configurations, and networking details. It discusses deployment environments, resiliency, security measures, and the roles of different nodes in the system. Additionally, it includes a connection diagram and addresses questions about implementation and service exposure.