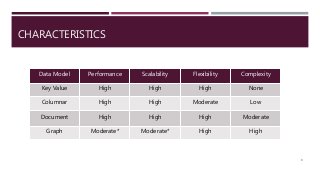
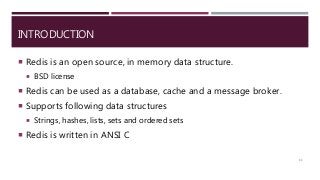
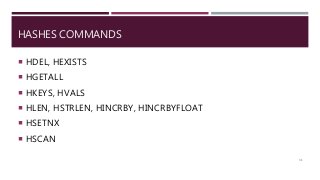
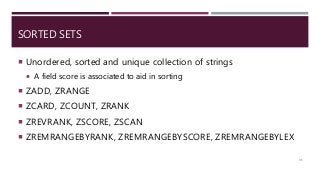
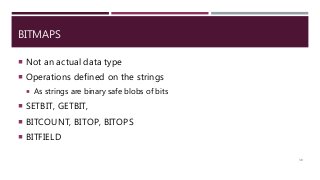
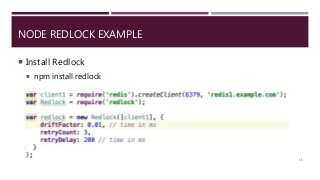
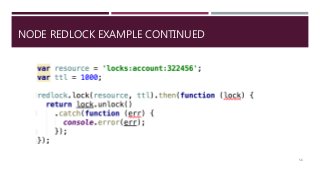
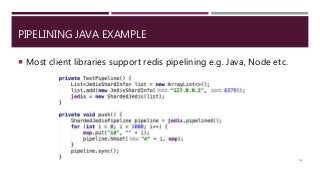
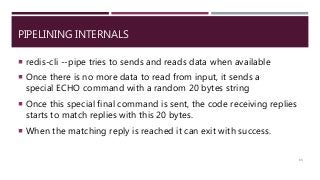
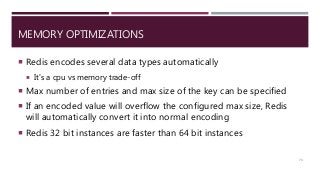
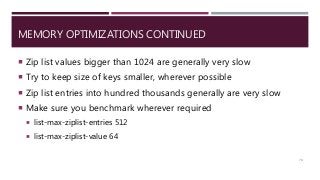
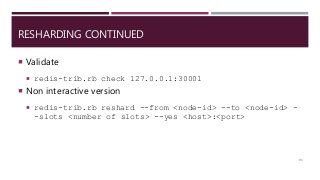
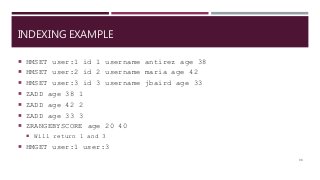
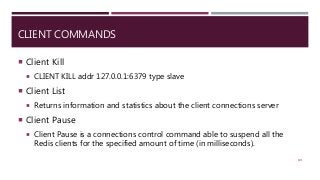
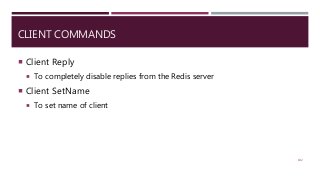
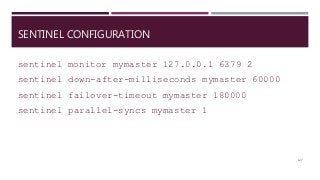
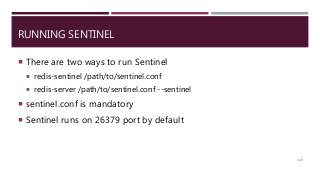
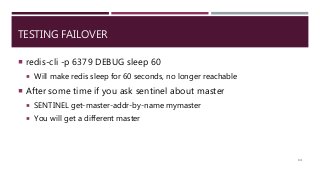
The document provides a comprehensive overview of NoSQL databases, primarily focusing on Redis, detailing its data structures, characteristics, and commands. It explains different types of NoSQL databases, key-value storage, and Redis functionality including setup, memory optimizations, transactions, and clustering. Several examples and hands-on exercises are included to help users effectively implement and utilize Redis in various scenarios.